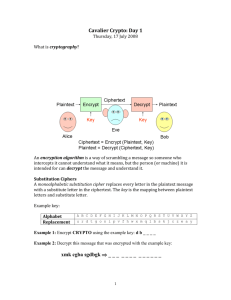
exam3
advertisement

Question 1: Saltzer & Schroeder describe 8 principles for design and implementation of security mechanisms. For each one of the following cases, what security design principles dose it violate and/or implement? a) Psychological Acceptability. b) Least Privilege. c) Fail-Safe Defaults. d) Economy of Mechanism. e) Complete Mediation. f) Separation of Privilege. g) Least Common Mechanism. h) Open Design. 1) Disable user-account after 3 wrong password attempts violate principle … . [ ] 2) Your web servers shared the same Internet connection violate principle … . [ ] 3) Make your encryption algorithm base on obscurity violate principle …. [ ] 4) File access is only checked when the application opens the file violate principle … . [ ] 5) Special version of UNIX su command checks password, if ok grants access. If it cannot access password file (for some reason) grants access anyway to allow user to fix the problem. This UNIX version violate principle… . [ ] Question 2: In Scanning Tool, the scanning engine collects various hardware and software information from the scanned targets. How can you use the following information to improve your computer protection? 1) Windows registry information can be used to identify: a) Trojans. b) open ports. c) shares. d) logged users. 2) Upgrading the service packs of your computer used to: a) remove bugs. b) close open ports. c) remove spywares. d) eliminate shares. 3) One of the most vulnerabilities that can be used from back-doors: a) Administrator account. b) Guest account. c) Any limited account. d) Any administrator account. Question 3: A Pub (A) , Prv(A) B Pub (B) , Prv(B) A and B are participate in a secure communication. The secure communication components include RSA Encryption and SHA1 algorithm. How you can use these components to perform the following operation? 1) A sending a message (M) to B with assurance that message only seen by B. a) A encrypt M using Prv(A) and B decrypt it using Pub(A). b) A encrypt M using Pub(B) and B decrypt it using Prv(B). c) A sign M using Prv(A) and B decrypt it using Pub(A). d) A sign M using Pub(B) and B decrypt it using Prv(B). 2) B receive a message from A with assurance that message are not tampered with. a) b) c) d) A encrypt M using Prv(A) and B decrypt it using Pub(A). A encrypt M using Pub(B) and B decrypt it using Prv(B). A sign M using Prv(A) and B decrypt it using Pub(A). A sign M using Pub(B) and B decrypt it using Prv(B). 3) A sign a message with the minimum cost if: a) A sign M using Prv(A), and then compute the hash of the signed M. b) A sign M using Pub(A), and then compute the hash of the signed M. c) A compute the hash of M, and then sign the hash value using Pub(A). d) A compute the hash of M, and then sign the hash value using Prv(A). Question 4: For the following statements, indicate whether there are True [T] or False [F]. 1) To minimize number of bugs is your computer, use the most complex security algorithms. [ ] 2) Word documents owned by a user use mandatory access control method. [ ] 3) Zone alarm firewall protects your computer from dangerous traffic. Almost it has two zones one for internet zone, and the other for trusted zone. [ ] 4) Zone alarm allows Sharing in the trusted zone and denies it in the internet zone. [ ] 5) A patch is an update which is released by a software company to address a technical/security issue. [ ] 6) MD5 is message-digest algorithm, which its output is a stream of hexadecimal digit and the output length depend on the message length. [ ] 7) Two stations with the same MAC address can't be connected to one AP. [ ] Question 5: Complete the following statements by selecting the correct choice: 1) A __________ is a software program that corrects a set of known bugs or adds new features to operating systems and applications. a) Service Pack. b) Anti-spay ware. c) GFI security scanner. d) Anti-virus. 2) You should give your Public Key to everyone you know. They will use it to __________ and to __________. a) send you encrypted data. b) verify your signature. c) decrypt messages that received from you. d) signed the messages that sent to you. 3) In web security, the automated scan consists of tow phases, __________ and __________: a) Structuring. b) Spanning. c) Scanning. d) Crawling. 4) __________ is the practice of obscuring the message so that it can not be seen. a) Cryptography. b) Hashing. c) Steganography. d) Signature. 5) To crack the WEP, we depend on __________. a) SSID. b) MAC. c) IP. d) IV.