Digital Signatures
advertisement

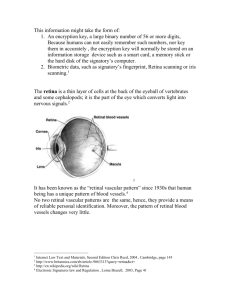
Digital Signatures In society, probably the most often used form of proof that an individual did in fact agree to a contract is the handwritten signature. Obviously, there is no way of handwriting your signature on an electronic message. This is the function of the digital signature. Digital Signatures are intended to serve at least two purposes: It can be used by the receiver to verify that the sender of the message is who he or she claims to be. This has to do with authentication. It can be used by the receiver to later prove that the message was initiated by the sender. This is at the heart of non-repudiation. Of course for this to be truly a useful tool, the digital signature must be devised in such a manner as to make it impossible for the receiver to have created the message himself. To achieve these purposes, cryptography is used for digital signatures and just as there is in encryption algorithms, there are symmetric-key signatures and asymmetrickey, or public-key signatures. Like symmetric-key encryption, symmetric-key signatures involve the use of identical keys at the sending and receiving ends. Public-key signatures are of course implemented using public-key encryption. Thus, one key is used to encrypt while a different key is used to decrypt. In both cases, the end goal is that the digital signatures include encrypted information that could only have been encrypted by the sending party or by a trusted central authority. One digital signature scheme that works in public-key cryptosystems and is based on one-way hash functions is called a message digest. The two most widely used message digest algorithms are MD5 and SHA-1.