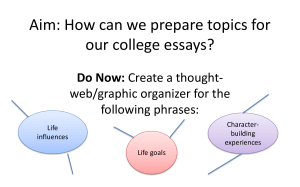
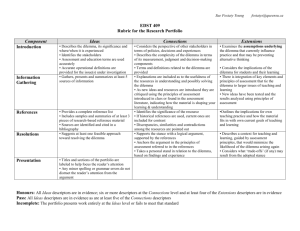
Chapter One: The Security Dilemma
advertisement

CHAPTER ONE Chapter One: The Security Dilemma Introduction There is an academic debate in the literature on the security dilemma concerning the implications of anarchy in international politics, and whether or not cooperation between states is possible under these conditions. From the perspective of offensive realism, anarchy results in an irreducible level of uncertainty in international politics. Thus, from this perspective, security-seeking states constantly view one another as threats to their own security. Anarchy inescapably leads to paradoxical security competition between defensive states (although short-term self-interested cooperation is still possible).1 In contrast, however, from the perspective of defensive realism and constructivism, long-term cooperation between defensive states in mitigating security competition under the condition of anarchy is possible. Where defensive realism and constructivism differ, however, is in how they explain the possibilities of long-term cooperation in mitigation of the security dilemma. Although defensive realist theory shares offensive realism’s assumption that anarchy is a potential source of security competition in international politics, defensive realists also argue that, under certain conditions, it may be possible for states to reduce uncertainty by signalling their defensive intentions to one another. Although uncertainty would remain in their relationship, it is nonetheless possible for both sides to mitigate the extent of security competition through long-term cooperation. 2 The constructivist perspective goes further and contends that paradoxical security competition between defensive states occurs when policymakers interact based on a socially constructed antagonistic images of one another. At the same time, however, constructivists argue that such socially constructed antagonistic relationships can be reinterpreted. Policymakers can reinterpret the meaning of the hostile images that they have assigned to one another and instead consider the possibility that the other side is driven by fear, rather than malice. Interests can thus change, leading to the possibility of a new relationship based on trust and cooperation.3 1 John Mearsheimer, The Tragedy of Great Power Politics (New York: W.W. Norton, 2001), p.35. Robert Jervis, Perception and Misperception in International Politics (Princeton: Princeton University Pres, 1976), p.81. 3 Alexander Wendt, Social Theory of International Politics (Cambridge: Cambridge University Press, 1999), pp.279-96, 326-30 2 1 CHAPTER ONE This chapter seeks to review these perspectives and begins by examining Rousseau’s ‘Stag Hunt’ and the Prisoners’ Dilemma game. From here, the chapter discusses the prospects for cooperation between actors under anarchy. The chapter then moves on to examine if security competition between status quo states is an inescapable result of uncertainty in international politics, or if cooperation can emerge between such states and thus mitigate the effects of uncertainty. This chapter thus explores the theoretical background of the differing approaches to explaining security dilemma dynamics in the academic literature.4 A review of this literature highlights an academic debate between offensive realism, defensive realism, and constructivism on the implications of uncertainty in the anarchic world of international politics. 5 An exploration of each of these theoretical approaches leads to three distinct explanations for security dilemma dynamics between defensive states. 1. Rousseau’s ‘Stag Hunt’ and The Prisoner’s Dilemma Jean-Jacques Rousseau’s ‘Stag Hunt’ begins with the assumption that, amongst a group of five hunters, all would eat well by cooperating to hunt a stag. Such cooperation, however, collapses when the men see a hare. Although the hunger of each of the hunters would be less satisfied by the hare than the stag, each of them fears that the others cannot be trusted to refrain from catching the hare first. Fearing such defection from cooperation, one of the hunters chooses instead to catch the hare The term ‘security dilemma dynamics’ has been used elsewhere in the academic literature. Alistair Iain Johnston and J.J Suh used the term in separate publications to describe the two-way, interactive nature of paradoxical security competition between defensive states; see Alistair Ian Johnston, ‘Beijing’s Security Behavior in the Asia-Pacific: Is China a Dissatisfied Power?’, in J.J Suh, P.J Katzenstein and A. Carlson (ed.), Rethinking Security in Asia (Stanford: Stanford University Press, 2004), p.75; Suh, ‘Producing Security Dilemma out of Uncertainty: The North Korean Nuclear Crisis’, Mario Einaudi Centre for International Studies (2006). Similarly, Ken Booth and Nicholas Wheeler refer to the ‘dynamics of the security dilemma’ in an effort to describe how factors such as uncertainty and fear may lead paradoxical security competition between defensive states; see Ken Booth and Nicholas Wheeler, The Security Dilemma: Fear, Cooperation and Trust in World Politics (Basingstoke: Palgrave Macmillan, 2008), pp.2-3. In this thesis, the term ‘security dilemma dynamics’ is used to describe how the dilemmas of interpretation and response identified by Booth and Wheeler, when resolved in a confrontational manner as a result of uncertainty and fear, may lead to paradoxical security competition between defensive states. It should also be noted that this paradoxical security competition, referred to as the ‘security paradox’ by Wheeler and Booth as well as in this thesis, has formed the mainstream definition of the ‘security dilemma’ in the academic literature. See Booth and Wheeler, The Security Dilemma, pp.8-9. 5 The attached table outlines in brief the key contrasting features of offensive realism, defensive realism, and constructivism as contrasting methodological approaches to understanding the security dilemma. See Appendix 1, ‘Comparison of Offensive Realist, Defensive Realist and Constructivist Approaches to Security Dilemma Dynamics’. 4 2 CHAPTER ONE and satisfy his own hunger. In so doing, however, he scares the stag away and thus deprives the other hunters of a meal.6 The Prisoners’ Dilemma game is driven by a similar logic and assumes the presence of two persons in a prison who have the choice of either cooperating (by denying involvement in a crime) or defecting (by confessing to the crime and implicating the other), without knowing if the other person will cooperate or defect.7 Their choice of action has to be decided without knowing in advance what the other side will do. At the same time, however, both sides are aware that mutual cooperation would lead to a higher benefit than mutual defection. Furthermore, as the same logic operates for both sides, they are aware that should they choose unilateral defection against a cooperating partner, the defector would benefit at the expense of the cooperative side.8 Under these circumstances, and based on the assumption that both actors are rational egoists who seek to maximise their own benefit, when the relationship between the two sides is characterised by mistrust, the likelihood is that both will believe that the other will defect. Rather than face unilateral loss, both sides will choose to defect, their preference for mutual cooperation notwithstanding.9 The notion that cooperation between actors in an anarchic environment is impossible was challenged by Robert Axelrod in The Evolution of Cooperation. Axelrod noted that, when several rounds of the Prisoners’ Dilemma game are repeated between two players – an Iterated Prisoners’ Dilemma - the choices that they undertake – cooperate, or defect – could be used by either side to signal an intent to cooperate, build trust and thus increase their resulting mutual payoff from each round of the game.10 Labelling this strategy as ‘tit-for-tat’,11 Axelrod argued that when the players value their future benefits, they stood to maximise their gains when they responded to cooperative moves by reciprocal cooperation. Conversely, the players 6 Jean-Jacques Rousseau, The Social Contrast and Discourses (London: Dent, 1973), cited in Booth and Wheeler, The Security Dilemma, p.14. 7 Robert Axelrod, The Evolution of Co-operation (New York: Basic Books, 1984), pp.7-9. 8 Axelrod, The Evolution of Cooperation, p.8. 9 Axelrod, The Evolution of Cooperation, pp.8-10. See also Robert Jervis, ‘Cooperation Under the Security Dilemma’, International Security, 30/2 (1978), pp.167-68. 10 Axelrod, The Evolution of Cooperation, pp.12-15. 11 Leon Sigal adopts Axelrod’s ‘tit-for-tat’ argument to describe the patterns of US-North Korean interaction in the case study in Chapters Four and Five. See Leon Sigal, Disarming Strangers: Nuclear Diplomacy With North Korea (Princeton: Princeton University Press, 1998), pp.125-27. 3 CHAPTER ONE minimised their losses by responding to defection by the other player with a defection of their own.12 The players in the Prisoner’s Dilemma could indicate their preferences (for cooperation or defection) and thus build a basis for cooperation even in the absence of a Hobbesian Leviathan. Even when the players in a Prisoner’s Dilemma prioritised self-interest, cooperation between rival parties was still possible as they could reciprocally signal to one another an interest in mutual cooperation rather than continued competition that neither side really wanted.13 Can such a process of cooperation and trust-building be fostered within the context of international politics? States, too, interact with one another in the absence of world government, or what may be termed ‘an anarchic setting’. In this regard, the academic literature on the security dilemma has been characterised by significant debates between offensive realism, defensive realism and critical constructivism in exploring the possibilities for trust-building and cooperation between actors in an uncertain, anarchic world. 2. The Dilemmas of Interpretation and Response In defining the security dilemma, Ken Booth and Nicholas Wheeler move away from the mainstream definition found in the academic literature that has focussed on the process of paradoxical security competition between defensive states. 14 Noting that the term ‘dilemma’ indicates a situation where one is confronted with a difficult choice between two alternatives 15 , they argued that a definition of the security dilemma also has to allow for human agency on the part of policymakers.16 In their 1992 chapter, ‘The Security Dilemma’, Booth and Wheeler defined the security dilemma as a situation when the military preparations of one state create an unresolvable uncertainty in the mind of another as to whether those preparations are for ‘defensive’ purposes only (to enhance its security in an 12 Axelrod, The Evolution of Cooperation, pp.13-14, 19-20, 31-32, 53-54. Axelrod, The Evolution of Cooperation, p.21. 14 Booth and Wheeler, The Security Dilemma, pp.8-9. 15 Booth and Wheeler, The Security Dilemma, p.29. 16 Booth and Wheeler, The Security Dilemma, pp.8-9. 13 4 CHAPTER ONE uncertain world) or whether they are for offensive purposes (to change the status quo to its advantage).17 According to this definition, the security dilemma represents the difficult choice faced by policymakers in deciding if they should interpret the military capabilities of their neighbour as offensive, and thus adopt a stronger security posture in response, or if they should view their neighbour as defensive, and thus exercise restraint to assuage their neighbour’s security fears.18 Booth and Wheeler further developed their argument in their 2008 work, The Security Dilemma: Fear, Cooperation and Trust in World Politics. They defined the security dilemma as a two level strategic predicament’ consisting of the ‘dilemma of interpretation’, and the ‘dilemma of response’. 19 Faced with the condition of existential uncertainty in an anarchic world, the dilemma of interpretation is the predicament facing decision-makers when they are confronted … with a choice between two significant and usually (but not always) undesirable alternatives about the military policies and political postures of other entities. This dilemma of interpretation is the result of the perceived need to make a decision in the existential condition of unresolvable uncertainty about the motives, intentions and capabilities of others. Those responsible have to decide whether perceived military developments are for defensive or self-protective purposes only (to enhance security in an uncertain world) or whether they are for offensive purposes (to seek to change the status quo to their advantage).20 Policymakers in this situation thus have to determine if the arms acquisitions and stronger military capabilities of another state ‘are for defensive or self-protective Wheeler and Booth, ‘The Security Dilemma’, in John Baylis and N.J. Rengger (ed.), Dilemmas of World Politics: International Issues in a Changing World (Oxford: Oxford University Press, 1992), p.30. 18 Wheeler and Booth, ‘The Security Dilemma’, p.30. 19 Booth and Wheeler, The Security Dilemma, pp.4-5. 20 Booth and Wheeler, The Security Dilemma, p.4. 17 5 CHAPTER ONE purposes only (to enhance security in an uncertain world) or whether they are for offensive purposes (to seek to change the status quo to their advantage).’21 The dilemma of response follows from the dilemma of interpretation, and defines the difficult choice faced by states in formulating policy responses to a given interpretation of another state’s intent.22 Booth and Wheeler coined the term ‘strategic challenge’ 23 to refer to a situation where policymakers interpret the intentions of another state as aggressive. They described the predicament faced by policymaker; ‘should they signal, by words and deeds, that they will react in kind, for deterrent purposes? Or should they seek to signal reassurance?’ Both courses of action carry an element of risk; if policymakers in State A adopt a confrontational response to what it believes to be a strategic challenge from State B and build up their material capabilities, its actions create a dilemma of interpretation for State B, which has to determine if State A’s arming is driven by offensive or defensive intent. If State B also resolves its dilemma of interpretation in a confrontational manner and responds by arming, State A believes that its security fears are vindicated and acquires more weapons. Repeated cycles of this confrontational resolution of the dilemma of response lead to what Booth and Wheeler refer to as a ‘security paradox’24; although States A and B are both arming to defend themselves, their actions, by contributing to the other’s security fears, lead to an arms race and escalating hostility, resulting in reduced security for both sides.25 On the other hand, if State A attempts to reassure State B through not arming itself, it will face unilateral strategic vulnerability if State B turns out to have hostile intent.26 Booth and Wheeler also coined a related concept, ‘security dilemma contagion’, that occurs when security dilemma dynamics between two states that has resulted in arms racing arouses the fears of other states in the region and causes them to arm as well, leading to a wider, regional arms race.27 Booth and Wheeler also direct our attention to the ambiguous symbolism of weapons. They cite Arnold Wolfers’ argument underlining the ambiguous symbolism 21 Booth and Wheeler, The Security Dilemma, pp.4-5. Booth and Wheeler, The Security Dilemma, pp.4-5. 23 Booth and Wheeler, The Security Dilemma, p.9. 24 Booth and Wheeler, The Security Dilemma, p.5. 25 Booth and Wheeler, The Security Dilemma , p.9. 26 Booth and Wheeler, The Security Dilemma, pp.4-5. 27 Booth and Wheeler, The Security Dilemma, p.103. 22 6 CHAPTER ONE of national security, in particular how such ‘political formulas’ mean different things for different people.28 Wolfers thus wrote that ‘policies of national security, far from being all good or all evil, may be morally praiseworthy or condemnable depending on their specific character and the particular circumstances of the case.’ 29 Booth and Wheeler developed Wolfers’ argument and note that weapons too can be seen as ambiguous. They argue that ‘weapons have meaning in relation to the context and beliefs of the relevant actors.’ 30 Similarly, the Spanish statesman Salvador de Madariaga noted that ‘a weapon is either offensive or defensive according to which end of it you are looking at.’31 Weapons can be used offensively as instruments of conquest against other states, just as they may be used by states to defend themselves from conquest. When there are high levels of ambiguous symbolism behind states’ weapons, policymakers’ efforts in resolving their dilemmas of interpretation and response are likely to be complicated. They may find themselves falling back on worst-case scenario thinking, rather than risking unilateral strategic vulnerability. If, on the other hand, states are armed with weapons that have a low level of symbolic ambiguity, it is more likely that policymakers can interpret one another’s military postures as defensive or offensive, and act accordingly.32 Booth and Wheeler argued that there are three broad ‘logics’ through which we can analyse policymakers’ understanding of the implications of uncertainty in international politics.33 They referred to these as the ‘fatalist (the idea that insecurity can never be escaped in international politics), the mitigator (the idea that insecurity can be ameliorated for a time, but not eliminated), and the transcender (the idea that human society on a global scale can become what it wants to be, and is not determined).’34 The fatalist logic of insecurity is based on the notion that ‘because the search for security is primordial, the nature of relations between states and other 28 Arnold Wolfers, Discord and Collaboration: Essays on International Politics (Baltimore: John Hopkins Press, 1962), pp.147-65, cited in Booth and Wheeler, The Security Dilemma, pp.42-43. 29 Wolfers, Discord and Collaboration, p.164. 30 Booth and Wheeler, The Security Dilemma, p.43. 31 Salvador de Madariaga, cited in Jervis, ‘Cooperation Under the Security Dilemma’, p.201. 32 Booth and Wheeler, The Security Dilemma, pp.44-45. 33 Booth and Wheeler also caution us against categorising these three logics as ‘schools’ of thought. Rather, they argue that the three logics of insecurity are ‘ideal types’ that broadly describe the ideas held by policymakers. See Booth and Wheeler, The Security Dilemma, pp.10-11. 34 Booth and Wheeler, The Security Dilemma, p.10. 7 CHAPTER ONE entities is essentially competitive.’35 This perspective suggests that, as the world is a dangerous place with aggressive enemies, insecurity is an inescapable feature of international politics. Thus, even if states are driven by defensive concerns, they invariably fear attack by other states. Rather than risk such unilateral vulnerability, states will instead act like aggressive revisionists to safeguard their own security. The mitigator logic of insecurity suggests that cooperation between states in anarchy is possible, if only on a narrowly defined basis. Booth and Wheeler argued that anarchy informed by the processes, institutions and norms of society will bring a degree of predictable order, which in turn will bring a degree of security to the political units concerned … mitigator logic accepts that human nature may be flawed, and that the anarchical international system cannot be escaped, but its proponents nevertheless argue that the most dangerous features of the struggle between nations and states – such as arms racing, crises and war – can be ameliorated.36 Nonetheless, Booth and Wheeler underlined that the mitigator logic of insecurity also shares some elements of the fatalist logic of insecurity. Although institutions and norms may rein in security competition and arms racing for a given period of time, such arrangements may collapse in the future, leading to a renewal of security competition. They write that ‘there is a widespread expectation that the competitive logic of anarchy will … overturn the aspirations of the institutions of international society. War will find a way.’37 Booth and Wheeler argued that the transcender logic is based on the notion that ‘insecurity, including that deriving from the security dilemma, can be escaped if human society reforms or re-invents the structures and processes within which it lives, 35 Booth and Wheeler, The Security Dilemma, p.12. Booth and Wheeler, The Security Dilemma, pp.14-15. 37 Booth and Wheeler, The Security Dilemma, pp.14-15. 36 8 CHAPTER ONE globally.’ 38 Although this perspective acknowledges the problems of conflict and insecurity, it also rejects the notion that conflict is the result of intrinsic characteristics of human nature that are predisposed toward aggression. Instead, the transcender logic suggests that conflict in world politics was the result of the assumptions by human beings that they exist in a world politics based on conflict and suspicion. 39 At the same time, the transcender logic allows for human agency. Human beings are capable of learning from the mistakes of history and thus reforming international politics.40 3. Offensive Realism John Mearsheimer coined the term ‘offensive realism’ to underline the irreducible nature of uncertainty in anarchy and how this led to security-seeking states engage in ‘constant security competition, where states are willing to lie, cheat, and use brute force if it helps them gain advantage over their rivals.’ 41 Because offensive realist theory assumes that uncertainty in international politics can never be reduced, it is never possible for policymakers to enter the security fears of other states. In spite of their defensive intentions, it is never possible for states to rein in paradoxical security competition. In other words, offensive realist theory suggests that states are driven by the fatalist logic of insecurity. These patterns of behaviour were identified in the early literature on the security dilemma by John Herz and Herbert Butterfield. The ‘security dilemma’ was first coined by Herz, who, in 1950, referred to a fundamental social constellation … where a plurality of otherwise interconnected groups constitute ultimate units of political life … where groups live alongside each other without being organized into a higher unity. Wherever such anarchic society has existed … there has arisen what may be called the ‘security dilemma’ … Groups or individuals living in such a constellation must be, and usually are, concerned about their 38 Booth and Wheeler, The Security Dilemma, p.16. Booth and Wheeler, The Security Dilemma, p.16. 40 Booth and Wheeler, The Security Dilemma, pp.17-18. Given that the transcender logic does not characterise US-North Korean interaction, the transcender logic will not be examined in this case study. 41 Mearsheimer, The Tragedy of Great Power Politics, pp.xii, 35. 39 9 CHAPTER ONE security from being attacked, subjected, dominated, or annihilated by other groups and individuals. Striving to attain security from such attack, they are driven to acquire more and more power in order to escape the impact of the power of others. This, in turn, renders the others more insecure and compels them to prepare for the worst. Since none can feel entirely secure in such a world of competing units, power competition ensues, and the vicious circle of security and power accumulation is on.42 Herz further developed this position in 1951 in Political Realism and Political Idealism, where he wrote because this is the realm where the ultimate power units have faced, and still are facing each other as ‘monads’ irreducible to any further, higher ruling or coordinating power, the vicious circle of the power and security dilemma works here with more drastic force than in any other field. Power relationships and the development of the means of exercising power in the brutal form of force have dominated the field here to the almost complete exclusion of the more refined ‘governmental’ relationships which prevail in ‘internal politics’.43 Writing at the same time as Herz, Butterfield highlighted the ‘Other Minds’ problem that policymakers face in interpreting the intentions of other states. Butterfield referred to how uncertainty in anarchy formed ‘the tragic element in human conflict … this condition of absolute predicament or irreducible dilemma lies in the very geometry of human conflict.’ 44 In light of the absence of a Hobbesian Leviathan in international relations, Butterfield wrote of a Hobbesian fear – that you yourself may vividly feel the terrible fear that you have of the other party, but you cannot enter into the John Herz, ‘Idealist Internationalism and the Security Dilemma’, World Politics, 2/2 (1950), p.157. Herz, Political Realism and Political Idealism: A Study in Theories and Realities (Chicago: University of Chicago Press, 1951), p.200. 44 Herbert Butterfield, History and Human Relations (London: Collins, 1951), p.20. 42 43 10 CHAPTER ONE other man’s counter-fear, or even understand why he should be particularly nervous. For you know that you yourself mean him no harm, and that you want nothing from him save guarantees for your own safety; and it is never possible for you to realise or remember properly that since he cannot see the inside of your mind, he can never have the same assurance of your intentions that you have. As this operates on both sides the Chinese puzzle is complete in all its interlockings – and neither party sees the nature of the predicament he is in, for each only imagines that the other party is being hostile and unreasonable. It is even possible for each to feel that the other is wilfully withholding the guarantees that would have enabled him to have a sense of security.45 These works on the security dilemma point to the fatalist logic of insecurity.46 Herz’s writings in 1950 and 1951 outlined how states, in seeking to defend themselves, are constantly forced to prepare for the danger of attack from other states, and thus acquire armaments. At the same time, however, the act of arming themselves also gives them the ability to threaten other states. Such arming for defense thus inadvertently contributes to the security fears of both sides, leading to a vicious cycle of escalating security competition. Furthermore, in arguing that uncertainty in anarchy was irreducible, Herz’s argument in the early 1950s suggested that the condition of international politics was one of inescapable security competition between defensive states. Butterfield’s argument highlighted the psychological conditions that explain why states seeking to defend themselves, come to fear one another. By underlining the inability of policymakers to enter into one another’s counter-fears, his argument pointed to the difficulty that policymakers face in seeing why their own defensive military postures may be seen as provocative by the other side (a phenomenon that Andrew Kydd referred to as a ‘benign self-image’). 47 Policymakers thus fail to consider the possibility that their counterparts in other states may be arming to defend 45 Butterfield, History and Human Relations, p.21. It should however be noted that Herz later revised his position and in 1959 argued that there were circumstances under which the paradoxical security competition between status quo states could be mitigated. See Herz, International Politics in the Atomic Age (New York: Columbia University Press, 1959), pp.235-39, and the discussion on defensive realism below. 47 Andrew Kydd, Trust and Mistrust in International Relations (Princeton: Princeton University Press, 2005), p.17. 46 11 CHAPTER ONE themselves, and instead believe that they are faced with a hostile state. Under these conditions, rather than face unilateral vulnerability, states thus increase their armaments to defend themselves, even if, in so doing, they increase the other side’s counter-fear, cause the other to arm as well, and in so doing, drive the vicious circle of increasing hostility and arms racing identified by Herz. Although Herz and Butterfield were writing before the term ‘offensive realism’ was coined in the field of international relations, the implications to be drawn from their works in 1950-51 arrive at the same conclusion as contemporary offensive realist theory – namely, that in the anarchic structure of international politics, policymakers must constantly adopt worst-case scenario assumptions in interpreting one another’s intentions, and are thus locked in an inescapable competition for security against one another, their own defensive intentions notwithstanding. The similarity of these arguments becomes clear when we examine Mearsheimer’s The Tragedy of Great Power Politics. Mearsheimer begins with five starting assumptions; first, states exist in an anarchic system where there is no higher authority above the sovereign state 48 ; second, states possess material capabilities that can never be distinguished as offensive or defensive, and thus they always have the potential to attack one another; third, states can never be certain about the intentions of other states; fourth, survival, and the maintenance of territorial integrity and sovereignty are the primary goals of states, which will always prioritise this as their national interest above all other goals; fifth, states are rational actors that think strategically on how best to survive.49 Based on these assumptions, Mearsheimer argued that three basic patterns of state behaviour emerge. Firstly, because of Mearsheimer’s first, second and third 48 Defensive realist theory and constructivist theory do not challenge the fact that states exist in an anarchic system where there is no higher Leviathan above the state. What differentiates defensive realism and constructivism from offensive realism, however, is that in the latter two theories, anarchy can be understood to hold different implications for security policy other than Mearsheimer’s predictions of power-maximizing behaviour. 49 Mearsheimer, The Tragedy of Great Power Politics, pp.30-31, 35. Although Mearsheimer frames his argument within the context of great power politics, he also argues that ‘all states are affected by this logic … not only do they look for opportunities to take advantage of one another, they also work to ensure that other states do not take advantage of them.’ There are thus grounds for extending this theoretical approach for the purpose of analysing interaction involving small or medium powers. See also Dale Copeland, ‘The Constructivist Challenge to Structural Realism’, International Security, 25/2 (2000), pp.200-03, for his discussion of future uncertainty and how this leads to policymakers’ adoption of worst-case thinking; this is discussed in more detail in Chapter Two. 12 CHAPTER ONE assumptions, states anticipate danger from abroad and fear one another as potential security threats. This leads to a second pattern of state behaviour, self-help, as states perceive that they have to rely on their own material capabilities to survive in a hostile world order.50 These two patterns of state behaviour, alongside Mearsheimer’s fourth and fifth assumptions, converge on the third pattern of state behaviour identified by Mearsheimer, namely, that states seek to maximize power. State will constantly seek a dominant position in international system as the surest means to achieving their own survival; furthermore, states that have already established a dominant position in the international system will seek to maintain that position of dominance against all other possible challengers to the hegemonic power’s supremacy.51 Mearsheimer argued that states ‘recognize that the best way to ensure their security is to achieve hegemony now, thus eliminating any possibility of a challenge by another … states do not become status quo powers until they completely dominate the system.’52 Thus, from an offensive realist perspective, the security dilemma can be defined as a constant state of security competition between states that cannot be mitigated or escaped. The only possible results of this process of security competition, according to Mearsheimer, are war between the competing states, an armed standoff, temporary periods of short-lived cooperation, or the collapse of either state.53 The offensive realist understanding of security dilemma dynamics suggests that because uncertainty in international politics is irreducible, it is never possible for states to signal their peaceful intentions toward one another or enter into the counter fears of the other side. States facing the security dilemma must confront worst-case assumptions in interpreting the security postures of other states. States can never reduce the symbolic ambiguity of their military postures. Under such circumstances, anarchy is seen by policymakers as a hostile, competitive world where military selfhelp is their only security guarantee. Their defensive intentions notwithstanding, states constantly resolve their dilemmas of interpretation and response in a confrontational manner by arming themselves. In so doing, however, their attempts to increase their own security, by causing increased tension and arms racing, have the 50 Mearsheimer, The Tragedy of Great Power Politics, pp.31-36. Mearsheimer, The Tragedy of Great Power Politics, pp.35-36. See also Mearsheimer, ‘The False Premise of International Institutions’, International Security, 19/3 (1994/95), pp.9-13. 52 Mearsheimer, The Tragedy of Great Power Politics, p.35. 53 Mearsheimer, The Tragedy of Great Power Politics, pp.147-52, 156-62, 164-65. 51 13 CHAPTER ONE paradoxical effect of undermining their own security. In short, the irreducible nature of uncertainty means that in the formulation of security policy, states are constantly driven by a fatalist logic of insecurity in which their defensive intentions are outweighed by their fears of attack by other states, causing them to resolve their dilemmas of interpretation and response in a confrontational manner. 4. Defensive Realism Defensive realist theorists argue that there are circumstances when paradoxical security competition can be ameliorated. In Perception and Misperception in International Politics, Robert Jervis argued that the pursuit of ‘self-defeating power’ by status quo states (which he refers to as the ‘spiral model’) occurs when policymakers ‘do not understand it or follow its prescriptions.’ 54 Security dilemma dynamics between defensive states occur when policymakers fail to acknowledge that their own military postures may be seen as threatening by the other side. 55 At the same time, however, Jervis argued that if policymakers understood the spiral model, it would be possible for them to implement policies to mitigate this security dilemma dynamic. 56 Defensive realist theory thus acknowledges the possibility that, under certain circumstances, policymakers could discern if other states were driven by aggressive or defensive intentions. Under such conditions, security-seeking states could move away from the fatalist logic of insecurity and exercise a mitigator logic by signalling their defensive intentions to one another and thus rein in paradoxical security competition.57 This approach to the security dilemma dynamic was evident when Herz revisited his argument in his 1959 work, International Politics in the Atomic Age. Acknowledging Butterfield’s work on ‘Hobbesian fear’58, Herz noted that ‘if mutual suspicion and the security dilemma thus constitute the basic underlying condition in a system of separate, independent power units, one would assume that history must 54 Jervis, Perception and Misperception in International Politics, p.81. Jervis, Perception and Misperception, pp.62-66. 56 Jervis, Perception and Misperception, pp.81-83. 57 Jervis, ‘Cooperation Under the Security Dilemma’, p.187. 58 Butterfield, History and Human Relations, p.21. 55 14 CHAPTER ONE consist of one continual race for power and armaments, an unadulterated rush into unending wars.’59 As Herz argued, however, this obviously has not been the case. There have unquestionably been periods in which units have been less suspicious of each other than at other times, periods in which they felt more secure and have been able to work out systems that gave them even a certain feeling of protection. The security dilemma … was then ‘mitigated’.60 Herz developed his argument by drawing a distinction between wars initiated by ambitious, aggressive powers that sought world domination, and wars resulting from mutual suspicion between security-seeking states.61 This distinction was to prove crucial; as Booth and Wheeler point out, Herz’s new position implied the possibility that governments were sometimes able to judge the peaceful or aggressive motives and intentions of others as a result of their words and actions. Moreover, he appreciated that knowledge of the security dilemma might enable policy-makers to construct strategies that mitigated dilemmas of interpretation and response.62 Herz thus argued that mitigation of paradoxical security competition between defensive states was possible when states were able to achieve a ‘minimum’ level of security that met their respective interests in survival, and did not simultaneously undermine the security of other states. 63 Although the continued existence of significant defensive armaments on both sides continued to give them potentially offensive military capabilities (thereby causing the security dilemma to remain an issue of concern for both sides), the limited offensive potential of those capabilities enabled them to signal their defensive intentions and thus restrain the extent of their 59 Herz, International Politics in the Atomic Age, p.235. Herz, International Politics in the Atomic Age, p.235. 61 Herz, International Politics in the Atomic Age, pp.234-35. 62 Booth and Wheeler, The Security Dilemma, p.39. 63 Herz, International Politics in the Atomic Age, pp.237-40. 60 15 CHAPTER ONE security competition. In so doing, Herz’s revised position moved away from the fatalist logic of insecurity and acknowledged the possibility of mitigator logic instead. The notion that states can achieve a sufficient level of security for themselves without undermining the security of others was further developed by Jervis during the 1970s. Noting that policymakers framed political decision-making based on their interpretations of one another’s intentions, Jervis argued that the presence of policy debates in history pointed to the existence of two differing distinct frameworks that explain interaction between states. Jervis referred to these as the ‘deterrence’ and the ‘spiral’ models. 64 Noting that the deterrence model operated on the assumption by policymakers that they were faced by a security threat posed by an aggressive foreign state, Jervis argued that the logical course of action within the assumptions of the deterrence model was to adopt a posture of firmness and willingness to go to war in order to communicate resolve to the opposite side. 65 Furthermore, as a posture of reassurance would be interpreted as a sign of weakness, policymakers should not accept any negotiated settlement involving compromise or concessions unless the other side made greater concessions or agreed to preconditions set by the first side.66 Jervis highlighted Ole Holsti’s ‘inherent bad faith model’ as a factor behind policymakers’ subscription to the deterrence model.67 Holsti argued that US Secretary of State John Forster Dulles based his interpretation of Soviet intentions on the assumption that the Soviet leadership was invariably hostile because of its politically antagonistic ideology and thus could never be trusted to uphold international agreements, regardless of actual Soviet conduct. 68 Holsti emphasised the extent to which Dulles repeatedly insisted that the USSR continued to harbour hostile intent toward the United States in spite of evidence to the contrary. Thus, for instance, Dulles attributed reduced hostility in Soviet policy toward the United States during the 1950s to Soviet economic and political weakness, rather than a shift away from Cold War confrontation following the death of Stalin. Soviet conventional arms reductions in 1956 were interpreted by Dulles as evidence of Soviet economic 64 Jervis, Perception and Misperception, p.58. Jervis, Perception and Misperception, pp.58-59. 66 Jervis, Perception and Misperception, p.60. 67 Jervis, Perception and Misperception, pp.143-44. 68 Ole Holsti, ‘Cognitive Dynamics and Images of the Enemy: Dulles and Russia’, in David Finlay, Ole Holsti and Richard Fagen, Enemies in Politics (Chicago: Rand McNally, 1967), pp.42-44, 48-52. 65 16 CHAPTER ONE weakness. Similarly, Dulles dismissed the 1958 Soviet announcement of a nuclear test ban as meaningless ‘propaganda’ statement that the Soviet leadership had no intention of actually honouring.69 Although Jervis discussed the deterrence model and Holsti’s inherent bad faith model in different chapters of Perception and Misperception, it is possible to argue that the inherent bad faith model is one of the contributing factors that underpin Jervis’s deterrence model. Policymakers may believe that other states have hostile intent, and may adhere to this perception even in the face of overwhelming evidence to the contrary. Faced with such a rigid interpretation of the other side as hostile, policymakers may advocate diplomatic and military postures of firmness to communicate resolve, even when the other side undertakes clearly cooperative actions. Jervis’s spiral model describes a situation in which the defensive postures and arming of states result in greater insecurity for other states. He argued that ‘the underlying problem lies … in a correct appreciation of the consequences of living in a Hobbesian state of nature.’70 Jervis thus wrote that a peaceful state knows that it will use its arms to protect itself, not to harm others. It further assumes that others are fully aware of this … because the state believes that its adversary understands that the state is arming because it sees the adversary as aggressive, the states does not (sic) think that strengthening its arms can be harmful.71 When policymakers have had such benign self-images, they took for granted the assumption that their military capabilities and war plans were unambiguously defensive. As Jervis noted, however, these benign self-images may not be shared by other states. Rather, and recalling Butterfield’s argument concerning the ‘other minds’ problem, policymakers in other states may fail to see the defensive intentions of the first state and believe that these postures are driven by offensive intentions. Thus, Holsti, ‘Cognitive Dynamics and Images of the Enemy’, pp.59-63, 65-69, 86; Jervis, Perception and Misperception, pp.143, 144-46. Booth and Wheeler use the term ‘ideological fundamentalism’ to describe this phenomenon; see Booth and Wheeler, The Security Dilemma, pp.64-65. 70 Jervis, Perception and Misperception, p.62. 71 Jervis, Perception and Misperception, pp.68-69. 69 17 CHAPTER ONE Jervis argued that, in attempting to communicate resolve through the adoption of firm political and security postures, policymakers may fail to acknowledge that their actions are misperceived by their counterparts in other states as evidence of hostile intent.72 Under these conditions, policymakers fail to see how their military postures and capabilities, by inadvertently contributing to the fears of other states, drive the escalating spiral of arms racing and increasing hostility that constitute Jervis’s spiral model. Jervis argued that when the deterrence and spiral models frame the perceptual framework of governments, the resulting pattern of interaction is characterised by the process of escalating security competition identified by Herz and Butterfield. 73 Because the deterrence model causes both sides in the interaction to believe that they are faced with a potentially hostile power, they engage in increased expenditure on what they believe to be upgrades to their defensive military capability. At the same time, however, because they have a benign self-image of their own military capabilities, they fail to acknowledge how or why these defensive military upgrades may be seen as offensive by the other side.74 In the absence of a global Leviathan, both sides, fearing attack from the other, find themselves compelled to undertake expansionist policies and / or arming to safeguard their own security. Even though both sides may be driven by defensive intent, it is difficult for either to rein in such security competition so long as they do not believe that their rival is arming for its own defense. As Jervis argued, Arms procured to defend can usually be used to attack … what one state regards as insurance, the adversary will see as encirclement …. when states seek the ability to defend themselves, they get too much and too little – too much because they gain the ability to carry out aggression; too little because others, being menaced, will increase their own arms and so reduce the first state’s security. Unless the requirements for offense and defense differ in kind or amount, a status quo power will desire a military posture that 72 Jervis, Perception and Misperception, pp.62-72. Jervis, Perception and Misperception, p.81. 74 Jervis, Perception and Misperception, pp.78-81. 73 18 CHAPTER ONE resembles that of an aggressor. For this reason others cannot infer from its military forces and preparations whether the state is aggressive. States therefore tend to assume the worst … so to be safe, the state should buy as many weapons as it can afford.75 Furthermore, given that both states are operating on the same assumption that their neighbour is a potential security threat, both sides, by acquiring stronger military capabilities, inadvertently feed the security fears of their neighbours. The latter, fearing for their own security, arm themselves in response. Because both sides fail to acknowledge how their arming is contributing to the other’s fears, however, they see the other’s arming as vindicating their own fears that they are facing a hostile state, and thus arm themselves even further. This leads to the escalating spiral of mutual suspicion and hostility identified by Herz and Butterfield. 76 Conversely, Jervis argued that if policymakers could appreciate that they were facing a spiral model of interaction, they could attempt to address the security fears of others through reassurance.77 In other words, policymakers can move away from the fatalist logic of insecurity and recognise the mitigator logic instead, allowing for the possibility of cooperation with other states in mitigating security dilemma dynamics. 78 This argument is briefly examined in Perception and Misperception when Jervis argued that policymakers should ‘procure the kinds and numbers of weapons that are useful for deterrence without simultaneously being as effective for aggression’. For example, in within the context of the Cold War, Jervis argued that Moscow and Washington should favour retaliatory nuclear weapons such as Submarine Launched Ballistic Missiles (SLBMs) that were likely to survive nuclear attack by the other side over counterforce Inter-Continental Ballistic Missiles (ICBMs) that could conceivably be used in a crippling nuclear first-strike.79 This argument is explored in more detail in ‘Cooperation Under the Security Dilemma’, in which Jervis developed two variables that determine the level of instability of security dilemma dynamics, which he refers 75 Jervis, Perception and Misperception, pp.64-65. Jervis, Perception and Misperception, pp.64-65. 77 Jervis, Perception and Misperception, p.82. 78 See Chapter Two for a more detailed discussion of the possibility that policymakers can attempt to rein in paradoxical security competition. 79 Jervis, Perception and Misperception, pp.111-13. 76 19 CHAPTER ONE to as ‘Offense-Defense Balance’ (ODB) and ‘Offense-Defense Differentiation’ (ODD).80 ODB determines if the military capabilities of states are strategically advantageous defensively or offensively. 81 When defensive postures are advantageous, states face little benefit in attacking. 82 Conversely, when offensive postures are advantageous, there will be an increased incentive to initiate attacks against the other side, rather than risk a potentially crippling blow from the opponent83. The second variable that Jervis examines, ODD, is the extent to which states can clearly distinguish between each others’ military postures as offensive or defensive. 84 Under certain circumstances, the technical capabilities of particular weapons, strategic terrain, fortifications, the disposition and deployment of military forces and other similar factors, can help to distinguish between offensive and defensive military capabilities.85 When military postures can be clearly distinguished as either offensive or defensive, it is possible for security seeking states to reassure one another of their peaceful intent by adopting clearly defensive military postures. Conversely, aggressor states, by adopting offensively-oriented military postures to achieve their objectives of expansion, indicate their hostile intent, thus allowing other states to respond by arming themselves.86 If, on the other hand, the problem of ODD does not allow states to clearly distinguish between offense and defense, it becomes difficult for either side to interpret each others’ intentions as peaceful or hostile.87 Jervis’s ODB and ODD variables allow for four different worlds. Jervis’s first world assumes an offence-dominant ODB and an ODD where offense cannot be distinguished from defense. This situation is particularly dangerous for status quo states. Defensive military postures are likely to be misinterpreted as preparation for Sean M. Lynn-Jones coined the term ‘Offense-Defense Theory’ based on the implications of ODB and ODD for the level of stability in a given security dilemma dynamic. See Sean M. Lynn-Jones, ‘Offense, Defense, and the Causes of War’, Security Studies, 4/4 (1995), pp.660-62. 81 Lynn-Jones used the terms ‘offense-dominance’ and ‘defense dominance’ respectively to determine if a given ODB was advantageous offensively or defensively. See Lynn-Jones, ‘’Offense-Defense Theory and its Critics’, pp.665-66. 82 Jervis, ‘Cooperation Under the Security Dilemma’, pp.190-195. 83 Jervis, ‘Cooperation Under the Security Dilemma’, p.189. 84 Jervis, ‘Cooperation Under the Security Dilemma’, p.199. 85 Jervis, ‘Cooperation Under the Security Dilemma’, pp.199-206. 86 Jervis, ‘Cooperation Under the Security Dilemma’, pp.199-206. 87 Jervis, ‘Cooperation Under the Security Dilemma’, pp.199-206. 80 20 CHAPTER ONE offensive military action. Furthermore, because such a world is offense-dominant, states view their military assets as vulnerable to preemptive attack by the other side.88 Under these circumstances, policymakers are unlikely to adopt restraint in the event of a crisis, as this would probably be a fatal mistake if the other state turned out to have hostile intent. These variables point to a high level of symbolic ambiguity behind states’ military postures. It is likely that states will have a high incentive to launch preemptive offensive attacks against one another during a crisis, rather than risk losing their key military assets to a devastating ‘first-strike’ by the other side. Status quo states in Jervis’s first world are likely to be affected by the fatalist logic of insecurity and thus adopt worst-case assumptions in interpreting one another’s intentions during a crisis. Under these circumstances, policymakers are most likely to resolve their dilemmas of interpretation and response in a confrontational manner, causing security dilemma dynamics to escalate into inadvertent conflict.89 Jervis’s second world assumes a defense-dominant ODB, but offensive weapons cannot be clearly distinguished from defensive ones. Although weapons are also characterised by ambiguous symbolism, the fatalist logic of insecurity is less strong. Because offense cannot be clearly distinguished from defense, both sides are unable to determine if the other side has hostile intent or not. As a result of defensedominance, however, policymakers may acknowledge that it is not strategically advantageous for them to attack first, and thus instead adopt a defensive military posture.90 Furthermore, policymakers may acknowledge that even if they are faced with a strategic challenger, the defense-dominant ODB would enable them to survive an initial attack by the other side. The symbolic ambiguity of weapons is less dangerous as both sides know that they have the material capabilities to survive a ‘first-strike’ by the other side and / or threaten to inflict a devastating level of ‘secondstrike’ retaliation. Jervis’s second world thus describes security dilemma dynamics that are unlikely to escalate into conflict.91 Jervis, ‘Cooperation Under the Security Dilemma’, p.211-12. Charles Glaser, ‘Why Even Good Defenses May Be Bad’, International Security, 9/2 (1984) pp.98100; Glaser, ‘When are Arms Races Dangerous: Rational versus Suboptimal Arming?’ International Security, 28/4 (2004), pp.52-55. 90 Jervis, ‘Cooperation Under the Security Dilemma’, pp.212-13. 91 Jervis,‘Cooperation Under the Security Dilemma’, pp.211-12. 88 89 21 CHAPTER ONE Jervis describes his third world as one that faces ‘security problems’ rather than security dilemmas. Such a world is offense-dominant, but states can also distinguish one another’s military postures as defensive or offensive. States can clearly interpret one another’s intention from the configuration of their military forces. If they are interested in their own security rather than expansion, it is possible for them to adopt defensive postures.92 Conversely, security-seeking states can detect an aggressive state’s intent from its offensively-oriented military capabilities and respond by developing offensive weapons of their own that may be used preemptively in the event of a crisis. 93 Under such circumstances, the ambiguous symbolism of weapons is less of a problem for policymakers in resolving their dilemmas of interpretation. At the same time, however, given that such a world is offense-dominant, status quo states are likely to remain vigilant in observing one another’s military capabilities. Status quo states in Jervis’s third world can exercise a mitigator logic of insecurity by undertaking defensive military postures to signal their defensive intentions to one another. Jervis’s fourth world is most stable and offers the strongest prospects for policymakers exercising the mitigator logic of insecurity. Because such a world is defense-dominant, status quo states can achieve a high level of security through the adoption of defensive weapons and doctrines. Furthermore, such defensive military weapons can also be clearly distinguished from offensive ones.94 Status quo states can adopt defensive military postures that safeguard their security, and simultaneously indicate their defensive intentions to the other party. 95 This allows the symbolic ambiguity of weapons to be reduced to the extent that uncertainty is no longer a source of fear. Under such circumstances, security-seeking states can mitigate security dilemma dynamics. Although defensive realist theory acknowledges that the security dilemma dynamic can be mitigated, policymakers can exercise the mitigator logic of insecurity only under limited conditions. Defensive realist approaches to mitigation closely Jervis, ‘Cooperation Under the Security Dilemma’, p.212-13. Jervis, ‘Cooperation Under the Security Dilemma’, p.212-13. 94 Jervis, ‘Cooperation Under the Security Dilemma’, p.214. This argument is explored in more detail in Chapter Two. 95 Jervis, ‘Cooperation Under the Security Dilemma’, p.214. 92 93 22 CHAPTER ONE parallel game theory’s assumption that actors are rational egoists that seek to derive more, or at least equal, benefit from cooperation. 96 As such cost—benefit calculations do not always favour cooperation between the contracting parties, the prospects for mitigation under the theoretical assumptions of defensive realism have to be qualified. In common with offensive realism, defensive realist theory assumes that states prioritise their security interests in an anarchic world. Although states can recognise a shared interest in long term security cooperation with one another (thus mitigating the security dilemma dynamic), this is based on the premise that they achieve a satisfactory level of security for themselves. The defensive realist approach thus rules out the possibility of a transcender logic of insecurity, as even in the midst of security cooperation, states prioritise their own security over that of other states. The mitigator logic of insecurity is possible only when states have an interest in cooperation. As Jervis underlines in ‘Security Regimes’, however, such a basis for security cooperation is fragile and could drift apart with time, thus causing a shift back to the fatalist logic and renewed security competition.97 Furthermore, as states continue to base their security on the possession of their material capabilities, they continue to possess weapons that they can use to inflict damage on one another (albeit with less effectiveness). 5. Constructivism The constructivist perspective suggests that security dilemma dynamics occur when socially constructed images of hostility cause policymakers to resolve their dilemmas of interpretation and response in a confrontational manner. In Social Theory of International Politics, Alexander Wendt wrote that a world of (status quo) states would only get into a Hobbesian situation in the first place if they mistakenly assumed the worst about each other’s intentions, but uncertainty and risk-aversion could lead to just that. If so, they will feel compelled to engage in deep revisionist behaviour even though they neither want to nor think it is in their self-interest, which in turn compels other states James D. Morrow, ‘The Ongoing Game Theoretic Revolution’, in Manus I Midlarsky (ed.) Handbook of War Studies II, (Ann Arbor: University of Michigan Press, 2000), pp.165-76. 97 Jervis, ‘Security Regimes’, International Organization 36/2 (1982), p.369; see also Chapter Two. 96 23 CHAPTER ONE to do so as well ... what is ultimately driving this logic is a collective representation of their condition as Hobbesian.98 This perspective is further developed by critical constructivists such as Karin Fierke, who examined the role of language in identity constitution. Fierke adopted this perspective on the grounds that language is important in understanding how and why policymakers may give a hostile meaning to the armaments of others, thereby leading to paradoxical security competition between security-seeking states. 99 The fatalist logic of insecurity can thus be seen as a socially constructed antagonistic relationship. At the same time however, the images that states have of one another can change. As examined in Chapter Two, states in a socially constructed antagonistic relationship can reinterpret one another’s intentions and enter the counter-fears of other states. Wendt noted that structural realist theory’s assumption of a separation of interests (such as security) from ideas suggests that ‘self-help and competitive power politics are simply given exogenously by the structure of the state system.’ 100 Furthermore, Wendt acknowledged the importance of a ‘rump materialism’ as an explanation for security competition between status quo states in international politics. 101 At the same time, Wendt rejected the structural realist notion that the material capabilities of states in anarchy form the underlying explanation for such security competition. Rather, the latter resulted when the structure of anarchy is conceptualised in socially antagonistic, rather than material, terms;102 as he noted in the title of his 1992 article, ‘anarchy is what states make of it’.103 Wendt argued that people act toward objects, including other actors, on the basis of the meanings that the objects have for them. States act differently toward enemies than they do toward friends because enemies are 98 Wendt, Social Theory of International Politics, p.269. Karin M. Fierke, ‘Critical Methodology and Constructivism’, in Fierke, and Knud Erik Jorgensen (ed.), Constructing International Relations: The Next Generation (New York: M.E Sharpe, 2001), p.118. 100 Wendt, ‘Anarchy is What States Make of It’, International Organization, 46/2 (1992), pp.395-96. 101 Wendt, Social Theory of International Politics, pp.109-35. 102 Wendt, Social Theory of International Politics, p.249. 103 Wendt, Social Theory of International Politics, p.249. 99 24 CHAPTER ONE threatening and friends are not … Identities are the basis of interests. Actors do not have a ‘portfolio’ of interests that they carry around independent of social context; instead, they define their interests in the process of defining situations.104 In other words, ideas and interests are mutually constitutive.105 The meaning of the one depends on the simultaneous presence and meaning of the other, and vice versa, or what Wendt referred to as an endogenous relationship.106 States cannot exist independently of ideas; rather, they construct their interests, such as security, based on the identities of themselves and of other states, even as these interests simultaneously shape their intersubjective identities.107 Seen in this light, security dilemma dynamics occur when processes of social learning cause defensive states to inadvertently believe that they are facing a hostile other. This in turn leads to increasing internalisation of an antagonistic relationship. As Wendt argued, ‘security dilemmas are not given by anarchy … if states find themselves in a self-help system, this is because their practices made it that way.’108 Thus, for instance, Wendt notes that the US is more fearful of five North Korean nuclear missiles than 500 British nuclear missiles.109 In other words, the source of US fears are to be found not in the material capabilities of Britain or North Korea per se, but rather, the US perception of Britain as friendly, and of North Korea as hostile.110 Wendt illustrates his argument with a discussion of a four stage social interaction between two agents, Alter and Ego. Initially, based on its a priori definition of the situation, Ego engages in some action.111 This constitutes a signal to Alter about the role that Ego intends to take in the interaction, and the corresponding role into which it wants to cast Alter. In this second stage, Alter ponders the meaning Wendt, 'Anarchy is what states make of it’, pp.397-98. Wendt borrowed the term ‘portfolio’ from Barry Hindess, Political Choice and Social Structure, (Aldershot: Edward Elgar, 1989), pp.2-3. 105 Wendt, ‘Anarchy is What States Make of It’, p.399; Wendt, Social Theory of International Politics, pp.104-09, 122-34.; see also Christian Reus-Smit, ‘Constructivism’, in Scott Burchill, Richard Deretak, Andrew Linklater, Matthew Paterson, Christian Reus-Smit and Jacqui True, Theories of International Relations (Basingstoke and New York: Palgrave, 2001), p.217. 106 Wendt, Social Theory of International Politics, pp.26, 113-15.; see also Reus-Smit, p.218. 107 Wendt, Social Theory of International Politics, pp.49-50, 158-71.; see also Jonathan Mercer, ‘Anarchy and Identity’, International Organization, 49/2 (1995), pp. 231, 234. 108 Wendt, ‘Anarchy is What States Make of It’, p.407. 109 Wendt, Social Theory of International Politics, p.255. 110 Wendt, Social Theory of International Politics, p.255. 111 Wendt, Social Theory of International Politics, pp.330-32. 104 25 CHAPTER ONE of Ego’s action. For Ego, there are many possible interpretations, since there are no shared understandings and behaviour does not speak for itself. Alter’s interpretation is guided by its own definition of the situation, along with additional, new information contained in Ego’s. Alter thus learns something about Ego, thereby revising his (Alter’s) own ideas. This leads to the third stage, where, based on his new definition of the situation, Alter engages in an action of his own and sends a responding signal to Ego that indicates the role that Alter wants to take and the corresponding role into which it wants to cast Ego. This brings the interaction back to Ego, who interprets Alter’s action and prepares his (Ego’s) response. Alter and Ego will then repeat this social act until one or both decide that the interaction is over. In so doing they will get to know more about one another’s identities.112 Seen in this light, Wendt argues that it is possible to see three distinct logics through which states can interpret the implications of anarchy in international politics. Wendt broadly refers to these as the Hobbesian, Lockean and Kantian cultures of anarchy.113 The Hobbesian culture occurs when states cast one another as revisionist ‘enemies’ that have hostile intent. Under these circumstances, status quo states may believe that they are faced with a hostile aggressor, and thus act like aggressor-states themselves. Furthermore, because states are convinced of the other’s hostile intent, they adopt worst-case scenario thinking and prepare themselves for attack by the other side. Believing the other side to be hostile, policymakers view military capabilities and power as the dominant variable of analysis. As Wendt noted, ‘enmity … gives capabilities a particular meaning, which derives neither from their intrinsic properties nor from anarchy as such, but from the structure of the role relationship.’114 As states in this role relationship have cast one another as enemies, they believe that their interest in security requires them to engage in power politics and arms acquisitions. Furthermore, because both sides have cast the other as enemies, their actions further internalise the other side’s belief that it is facing a hostile state. Security competition 112 Wendt, Social Theory of International Politics, pp.330-32. As the Hobbesian logic of anarchy outlines the construction of an intersubjective identity based on hostility and thus closely relates to the fatalist logic of security competition identified by Booth and Wheeler, the Hobbesian logic will be the focus of this section of Chapter One. As the Lockean logic of anarchy explores the possibility of an intersubjective identity based on cooperation between rivals, it most closely relates to the mitigator logic of insecurity and will be discussed in more detail in Chapter Two. 114 Wendt, Social Theory of International Politics, p.262. 113 26 CHAPTER ONE thus becomes a self-fulfilling prophecy resulting in a socially constructed antagonistic relationship.115 Wendt’s theoretical approach has, however, been criticised for inadequately examining how inter-subjectively shared identities lead to changing identities. As Maja Zehfuss pointed out, a social act consists in sending a signal, interpreting it and responding on the basis of the interpretation. … actors need reflexive intelligence and consciousness for this process … in order to be able to reflect and interpret, actors have to be capable of using language. Wendt does not investigate, or even mention, the role of using language in this context.116 Instead, Zehfuss argues, within Wendt’s framework, ‘behaviour is construed as the key to identity change. The interaction between ego and alter Wendt describes revolves around physical gestures. Wendt’s actors do not speak. They only signal each other.’ 117 Zehfuss hence argued that Wendt’s description of the interaction between alter and ego does not provide us with a satisfactory explanation of how shared interpretation of their relationship may arise.118 Similarly, Fierke argued that Wendt’s analysis of Mikhail Gorbachev’s adoption of New Thinking characterised the Soviet leader as a rational actor. Such a perspective suggests that Gorbachev underwent critical self-reflection that led the Soviet leadership to move away from the coercion of the Cold War toward cooperation with the West. 119 As Fierke argues, however, such a perspective contradicts the constructivist principle that ‘meanings in terms of which action is organised arise out of interaction’.120 115 Wendt, Social Theory of International Politics, pp.262-66. Maja Zehfuss, Constructivism in International Relations: The Politics of Reality (Cambridge University Press, 2002), p.48. 117 Zehfuss, Constructivism in International Relations, p.48. 118 Zehfuss, Constructivism in International Relations, p.49. 119 Karin Fierke, Changing Games, Changing Strategies: Critical Investigations in Security (Manchester: Manchester University Press, 1998), p.60. 120 Wendt, ‘Anarchy is What States Make of It’, p.403. 116 27 CHAPTER ONE Fierke sought to address this by through a critical constructivist approach by directing our attention to the importance of language. She began by citing Ludwig Wittgenstein’s argument in Philosophical Investigations that language is a form of action which gives meaning to agents. 121 Thus, a given material object, such as a firearm, may be seen as an essential tool or as a weapon, depending on the context.122 Within the context of international politics, language is important in giving meaning when there are conflicting meanings to the interactions between states. 123 When language-acts that support a given interpretation of a relationship between states are repeated over and over again, that interpretation becomes increasingly internalised. In short, repeated languages acts contribute to the identities of states.124 Moreover, given the constructivist principle that ideas and interests are mutually constitutive, the identities that emerge from these language-acts is reflected in how states come to see their interests. 125 Although Fierke does not specifically spell out what a security dilemma is in Changing Games, Changing Strategies, she developed her argument in two subsequent works. In Diplomatic Interventions, Fierke argued that there is an overlap between “more conventional definitions of the security dilemma, derived from Hobbes’ ‘state of nature’, and ‘trauma’. Fierke defined trauma as a socially constructed collective memory expressed in the form of a ‘state of hyperarousal or permanent alert, which includes an expectation that the danger may recur at any moment … positive emotion cannot find expression in war, precisely because of the continuous fear of attack by others.’126 She further developed this argument in Critical Approaches to International Security, where she suggests that the security dilemma can be seen as the ‘securitization of trauma’. 127 Fierke argued that when a state’s political discourse is dominated by trauma, the ‘experience of widespread social suffering provided the foundation for a consolidation of collective identity’ in which warfare and militarism were seen as acceptable and legitimate.128 Repeated language- 121 Fierke, Changing Games, Changing Strategies, pp.17-18; see also Ludwig Wittgenstein, Philosophical Investigations (Oxford: Basil Blackwell, 1958) 122 Fierke, Changing Games, Changing Strategies, pp.18-20; Booth and Wheeler, The Security Dilemma, p.43 123 Fierke, Changing Games, Changing Strategies, pp.12, 25-26. 124 Fierke, Changing Games, Changing Strategies, pp.18-20. 125 Fierke, Changing Games, Changing Strategies, pp.32-34. 126 Fierke, Diplomatic Interventions: Conflict and Change in a Globalizing World (Basingstoke: Palgrave Macmillan, 2005), p.139. 127 Fierke, Critical Approaches to International Security, (Cambridge, UK; Malden, MA: Polity, 2007), p.132. 128 Fierke, Critical Approaches to International Security, pp.132-35. 28 CHAPTER ONE games revolving around antagonism, by giving increased meaning to a Hobbesian intersubjective identity, caused states to interpret other states as hostile. Seen in this light, discursive analysis of language is key to understanding how and why securityseeking states may resolve their dilemmas of interpretation and response in a confrontational manner, leading to paradoxical security competition. Similar approaches to developing a constructivist perspective on security dilemma dynamics have been explored by Alastair Iain Johnston, Roland Bleiker and J.J. Suh.129 Johnston directs our attention how the ‘socialization effects’ of assertive nationalism between the US and China have led to both sides constituting one another as ‘security threats’. 130 Policymakers on both sides have thus developed conceptualisations of their security interests as incompatible, even in face of evidence to the contrary.131 Bleiker underlined how the construction of antagonistic identities, and the threat perceptions that are associated with them, have decisively shaped the domestic political atmosphere in both North and South Korea … these antagonistic forms of identity have become so deeply entrenched in social consciousness that the current politics of insecurity appears virtually inevitable. Indeed, the prevailing identity constructs have helped to legitimatize the very militarized approaches to security that gave contributed to the emergence of tension in the first place.132 Suh’s approach to the security dilemma in his 2006 paper, ‘Producing Security Dilemma out of Uncertainty: The North Korean Nuclear Crisis’ links the social construction of antagonism to the spiral model of interaction outlined by Jervis. In 129 As both Bleiker and Suh were writing in the context of US-North Korean interaction, I will focus on the theoretical part of their work on the security dilemma in this chapter to avoid confusion with my case study. 130 Johnston, ‘Beijing’s Security Behaviour in the Asia-Pacific: Is China a Dissatisfied power?’, in Suh, Katzenstein and Carlson (ed.), Rethinking Security in Asia, pp.35-36, 68-75. 131 Johnston, ‘Beijing’s Security Behaviour in the Asia-Pacific’, pp.35-49. Johnston rejects the notion that a rising China should be seen as an aggressive revisionist state to the US on the grounds that Beijing has shown increasing participation in international institutions 132 Roland Bleiker, Divided Korea: Toward a Culture of Reconciliation (Minneapolis: University of Minnesota Press, 2005), pp.10-15, 56; quote on p.15. 29 CHAPTER ONE Perception and Misperception, Jervis had argued that the spiral model occurs when policymakers fail to understand that their military postures may be seen as threatening by others. Suh breaks down the process of social construction of an antagonistic identity into three stages, which he refers to as ‘antagonistic identities’, ‘identity blaming’ and ‘malign multiplication’.133 When both sides have an identification of the other as politically or strategically antagonistic, they are more likely to interpret one another’s apparent defection from cooperation within the overall context of their antagonistic relations.134 By framing the process of interaction as antagonistic, both sides exaggerate the threat posed by the others’ material capabilities, and fail to see how or why their own actions are contributing to escalating tensions.135 The benign self-images that the states thus become further internalised. ‘Identity blaming’ may be seen as another term used to refer to the dynamics examined in Holsti’s inherent bad faith model. States thus attribute one another’s behaviour to their identification of one another as political antagonists, regardless of their actual conduct. Thus, for instance, State A links State B’s arming to B’s identity as an aggressive revisionist aiming to change the territorial status quo through force of arms. Conversely, cooperative actions by State B are either attributed to State A’s superior power, or rejected as a deliberate attempt at strategic deception by State B.136 Suh argues that when these patterns of interaction are repeated, a process of malign multiplication ensues. Because both sides are convinced that the other side is hostile and untrustworthy, they increasingly subscribe to deterrence model assumptions and believe that they should demonstrate firmness against the ‘Other’, hoping to coerce the other into backing down whilst communicating what they believe to be indications of their own resolve. Furthermore, because both sides are not sensitive to the spiral model, both downplay how their actions had contributed to the other’s suspicions and fears and simultaneously highlight the other’s apparently provocative behaviour. Their identification of one another as antagonists is further deepened. Both sides develop an increasing conviction that the other’s apparently aggressive behaviour is evidence of hostile intent. 137 At the same time, because Suh, ‘Producing Security Dilemma, pp.6-8. Suh, ‘Producing Security Dilemma’, pp.12-17. 135 Suh, ‘Producing Security Dilemma’, pp.12-17. 136 Suh, ‘Producing Security Dilemma’, pp.17-23. 137 Suh, ‘Producing Security Dilemma’, pp.24-25. 133 134 30 CHAPTER ONE neither side is sensitive to spiral model dynamics, they do not see any need to show restraint or reassure the other side.138 Both sides thus increasingly believe that further shows of firmness are necessary to communicate resolve. As this logic operates on both sides, a spiral of increasing mutual suspicion ensues, in which their actions escalate and counter-escalate the tensions in their relationship. Interaction between the two states becomes repeated on this pattern, inadvertently causing their intersubjective identity to take on an increasingly hostile meaning.139 The constructivist perspective thus indicates that security dilemma dynamics describe an antagonistic relationship between states that has arisen from their assumptions that the other is a hostile revisionist. By resolving their dilemmas of interpretation with the assumption of hostile intentions behind the material capabilities and arming of others, states believe that they are facing a security challenge. When policymakers respond with confrontational policies such as increasing their arms build-ups and placing their military forces on alert, they feed the other’s interpretation that it is facing a strategic challenge. Furthermore, because of their benign self-images, both sides fail to see how their own actions are contributing to the others’ fears. Both sides thus resolve their dilemmas of response in a confrontational manner. In spite of their defensive intentions, the belief that they are facing a hostile state leads to increasing internalisation of norms based on power politics and security competition. The Hobbesian logic of anarchy thus becomes a self-fulfilling prophecy. Conclusion This chapter has developed three differing explanations as to how and why securityseeking states interpret uncertainty in anarchy as a source of fear in international politics. Offensive realist theory suggests that uncertainty in anarchy can never be reduced; as such, policymakers will constantly adopt worst-case assumptions behind the formulation of security policy. The fatalist logic of insecurity is hence an inescapable feature of international politics. Paradoxical security competition between security-seeking states can never be avoided, except for temporary periods of cooperation. 138 139 Suh, ‘Producing Security Dilemma’, pp.10-11. Suh, ‘Producing Security Dilemma’, pp.24-28. 31 CHAPTER ONE Defensive realist theory, in contrast, indicates that security dilemma dynamics occur when policymakers are unable to see how or why their military postures may be seen as offensive by the other side. By failing to acknowledge that the other side is driven by defensive intent, such postures inadvertently feed the fears of the other side, leading to an escalating spiral of self-defeating security competition. At the same time, however, defensive realist theorists argue that there are circumstances when policymakers can acknowledge the possibility that their counterparts are driven by fear, rather than malevolence. Under such circumstances, policymakers may recognise that they have a common interest in cooperating to rein in such paradoxical security competition. Seen in this light, security dilemma dynamics occur where states are unable to signal their defensive intent to one another. The constructivist approach suggests that security dilemma dynamics occur when states resolve their dilemmas of interpretation based on a shared understanding that they are in a Hobbesian self-help world. When policymakers fail to see how their arming arouses the fears of the other side and instead formulate confrontational responses, they inadvertently contribute to the other’s security fears, causing the socially constructed antagonistic relationship to become further internalised. By adopting increasingly confrontational postures against one another, both sides further contribute to the other’s fears and thus inadvertently contributing to the vicious cycle of escalating hostility and arms racing. Seen in this light, from the constructivist perspective, the fatalist logic of insecurity is socially constructed. By outlining three distinct interpretations of uncertainty in international politics, Chapter One has highlighted three theoretical approaches to understanding how and why security-seeking states resolve their dilemmas of interpretation and response in a confrontational manner. These three differing understandings of security dilemma dynamics in turn point to an academic debate concerning the ability of states to rein in such paradoxical security competition. This debate is the focus of Chapter Two. 32