Chapter 3
advertisement

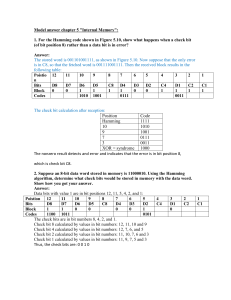
Codes Chapter 3 Purposes: How to use binary combinations to represent code characters? How to detect or correct an error (errors) generated when information bits are transmitted over a communications channel? Codes can represent digits, letters, punctuation marks, control characters, words, strings, pictures, etc. What we are going to study: BCD code and other weighted/unweighted codes for the ten decimal digits; ASCII code; Error detecting and correcting codes; Binary Coded Decimal (BCD) Characters BCD code 0 1 2 3 4 5 6 7 8 9 0000 (0) 0001 (1) 0010 (2) 0011 (3) 0100 (4) 0101 (5) 0110 (6) 0111 (7) 1000 (8) 1001 (9) 1010 (A) 1011 (B) 1100 (C) 1101 (D) 1110 (E) 1111 (F) 2421 code 0 1 2 3 4 5 6 7 8 9 The number of total possible codes to represent the ten decimal characters is 16 15 14 9 8 7 , since the first character has 16 choices, the second one has 15 choices, … and the last one has 16 9 7 choices. Example: The decimal number 9872 is represented in BCD as Weighted Codes: There exists a fixed weight associated with each bit position in the binary representation of the code character. Weighted code character can be represented by N b3 w3 b2 w2 b1 w1 b0 w0 , where b j is the bit and w j is the weight at position j . Weight can be positive and negative. For example, weights 8,4,-2,-1 define one mapping (coding) for decimal numbers For each group of weight, there may exist multiple codes. For example, there are 36 different codes that can use weights 3,3,2,1 There are only 70 weighted-code groups that represent decimal digits, among which 17 are positive. Examples: All codes within group 3,3,2,1 and group 8,4,-2,-1 Unweighted Codes: Excess-3 code (XS3): adds binary 3 to each character of the BCD code. It is selfcomplementing and used in the early Univac I computer. Gray code: only a single bit changes between any two consecutive code characters. Properties of Codes: Self-complementing codes: 9’s complement in decimal is the 1’s complement in binary. Example: the 2,4,2,1 code, the XS3. If a weighted code is self-complementing, the total weight must be 9. Reflective codes: a code that reflects the bit pattern of its characters about its mid point. Example: the gray code. Algorithm: to compute the corresponding Gray code character for the binary number and vice versa. Let bn 1 , bn 2 b1 , b0 be the binary numbers, and let g n1 , g n2 g1 , g 0 be the corresponding Gray code characters, then bn 1 g n 1 g n 1 bn1 n 1 b g j (mod 2), k n 1, 0 g j b j b j 1 , j (n 2), ,1,0 k j k Example: For the binary number 101101, compute the Gray code character. Alphanumeric Code ASCII: 7 bits per character EBCDIC: introduced by IBM. 8 bits per character. Latin-1: Can support characters with accent marks in Spanish and French. 8 bits per character. Unicode: 16 bits character. Can represent non-Latin characters. Read the text yourself for more. Note: Your hello.c is stored in a file as a sequence of bytes. Each byte has an integer value corresponding to some character. This value is the ASCII code of the character. Control of Transmission Errors Sources of transmission errors: electrical noise, inter-symbol interference, electrical echo, crosstalk, environmental interference, etc. Transmission errors can not be completely avoided but can be detected and/or corrected. Error Detecting Codes Definition: The Hamming Distance of two code characters is the number of bit positions in which the two code characters differ. The Distance of a code is the minimum distance between any pair of the code characters. Example: What is the distance of the BCD code? Remark: To detect d errors, we need a distance of d 1 code; To correct d errors, we need a distance of 2d 1 code. Justification: One bit error detection: use a parity bit to detect a one-bit error: even or odd parity. Question: why the one bit parity makes the code distance to become two? Practice Problem: Fill the blanks of the table. Decimal BCD Odd Parity Odd Parity Code Even Parity Even Parity Code 0 1 2 3 4 5 6 7 8 9 Probability of detecting an error with parity: Using one parity bit can detect that an odd number of bits have changed! Error detection probability analysis Error Correcting Codes (Hamming Codes) We know to correct d errors, we need a distance of 2d 1 code. Consider the case of d 1 . For a code containing m -bit code characters, how many check bits do we need in order to change the distance of the code from 1 to 3? Let k be the number of check bits. Example: compute k for m 4 . By adding 3 check bits, we obtain the Hamming (7,4) code, which indicates that in each code character, there are 4 bits data and 3 bits for error correction. Questions: How to build the one-bit error correcting code after computing the number of check bits? How to detect the one bit error if it occurs? In 1950, Hamming proposed a method to answer the above questions. The resultant error correction code is called a Hamming Code. Idea: let 1,2,3,,2mk denote the bit positions in the resultant hamming code, among which 2i , i 0,1, k 1 , are check bit positions and others are data bit positions. The check bit at position j checks the data bit at position i if j and i 0 . Here and is a logic (bit-wise) and operation. The xor of each check bit and all its checked data bits must be zero if no errors occur. Let ( yk 1 , yk 2 , y0 ) be the xor results. yk 1 yk 2 y0 represents the data bit position that an error occur. If yk 1 yk 2 y0 is 0, then no errors occur. Example: Construct the Hamming code for the BCD code. Decimal 0 1 2 3 4 5 6 7 8 9 BCD (7,4) Hamming Code Notes Example: If bit position 3 has an error for decimal 6, what is the received code character? How this error is corrected? Remarks: 1. Hamming codes can correct only one-bit errors 2. By adding one additional parity bit to each Hamming code character, we obtain a single-error correcting, double-error detecting code. Polynomial Codes Polynomial codes are used to compute the CRC (Circular Redundancy Check) checksum widely used in computer networks for error detection. It is called polynomial codes because a polynomial is used to represent the bits in the code word. A code polynomial is the polynomial to represent the code b n 1 bn2 b2 b1b0 , which can be written as P( x ) b0 x 0 b1 x1 bn 2 x n 2 bn 1 x n 1 , where coefficients bi 0,1, i 0,1, n 1 . For a n bit polynomial code, its code polynomial has order (degree) n 1 . Example: The polynomial code 11001011 can be written as P( x) x 7 x 6 x 3 x 1 . Arithmetic Operations on Code Polynomials: Addition, Subtraction, Multiplication, and Division are defined as in ordinary algebra, except that in modulo-two arithmetic is used to compute coefficients. In modulo-two arithmetic, both addition and subtraction are equivalent to xor operation. Example: P( x) x 7 x 6 x 3 x 1 and J ( x ) x 6 x 3 x 2 x 1 . Then P( x ) J ( x ) P( x ) J ( x ) P( x ) J ( x ) P( x ) J ( x ) Example: W ( x ) x13 x12 x 9 x 8 x 7 x 6 x 5 x 4 x 3 x 2 x , D( x ) x 5 x 3 x . Compute W ( x ) D( x ) . The quotient Q (x ) is The Remainder R (x ) is Question: How to compute the CRC checksum given the code polynomial M (x ) for the data bits? We need a generating polynomial G (x ) , which contains the term 1 , and has degree g , where g is the required number of bits in the CRC checksum. Compute x g M ( x ) G( x ) , which results in Q (x ) and R (x ) . The checksum contains the coefficients of R (x ) . Sender transmit T ( x ) x g M ( x ) R( x ) ; Receiver check whether the remainder of T ( x ) G ( x ) is 0 or not. If the remainder is not a 0, then errors occur. Standardized generating polynomial used in computer networks: CRC-5: CRC-12: CRC-16: CRC-CCITT: CRC-32: CRC-16, CRC-CCITT, and CRC-32 are the most popular ones in data link layer and network layer of the protocol stack. Error Detecting Capabilities of Polynomial Codes: Strong. Special requirement for the generating polynomial. Hamming codes are a subset of polynomial codes!