Encryption
advertisement
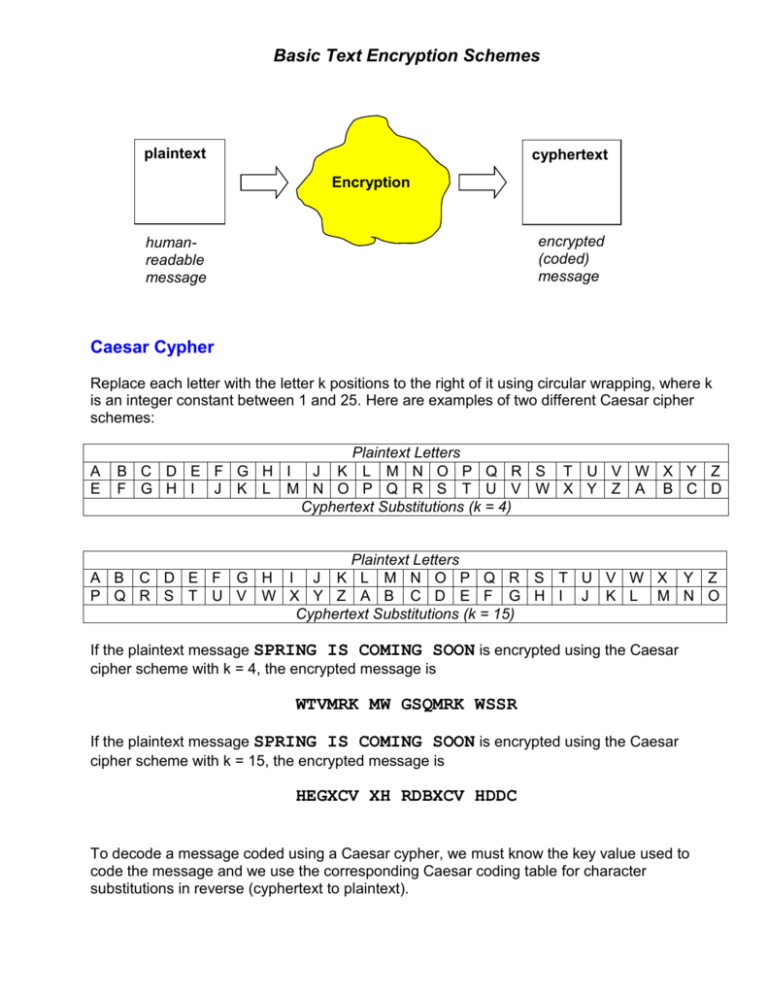
Basic Text Encryption Schemes plaintext cyphertext Encryption encrypted (coded) message humanreadable message Caesar Cypher Replace each letter with the letter k positions to the right of it using circular wrapping, where k is an integer constant between 1 and 25. Here are examples of two different Caesar cipher schemes: A E Plaintext Letters B C D E F G H I J K L M N O P Q R S T U V W X Y Z F G H I J K L M N O P Q R S T U V W X Y Z A B C D Cyphertext Substitutions (k = 4) Plaintext Letters A B C D E F G H I J K L M N O P Q R S T U V W X Y Z P Q R S T U V W X Y Z A B C D E F G H I J K L M N O Cyphertext Substitutions (k = 15) If the plaintext message SPRING IS COMING SOON is encrypted using the Caesar cipher scheme with k = 4, the encrypted message is WTVMRK MW GSQMRK WSSR If the plaintext message SPRING IS COMING SOON is encrypted using the Caesar cipher scheme with k = 15, the encrypted message is HEGXCV XH RDBXCV HDDC To decode a message coded using a Caesar cypher, we must know the key value used to code the message and we use the corresponding Caesar coding table for character substitutions in reverse (cyphertext to plaintext). Basic Text Encryption Schemes Vignere Cypher Add offsets for letters in a special keyword to plaintext letter offsets modulo 26. The keyword must contain only letters. A B C D E F G H I J K 0 1 2 3 4 5 6 7 8 9 1 0 Plaintext Letters L M N O P Q 1 1 1 1 1 1 1 2 3 4 5 6 Letter Offsets R 1 7 S 1 8 T 1 9 U 2 0 V 2 1 W X 2 2 2 3 Y 2 4 Z 2 5 Suppose the plaintext message is SPRING IS COMING SOON. This message is encrypted using the Vignere cipher scheme with keyword BEMIDJI as follows: S(18) P(15) R(17) I(8) N(13) G(6) I(8) S(18) C(2) O(14) M(12) I(8) N(13) G(6) S(18) O(14) O(14) N(13) + + + + + + + + + + + + + + + + + + B(1) E(4) M(12) I(8) D(3) J(9) I(8) B(1) E(4) M(12) I(8) D(3) J(9) I(8) B(1) E(4) M(12) I(8) = = = = = = = = = = = = = = = = = = T(19) T(19) D(3) Q(16) Q(16) P(15) Q(16) T(19) G(6) A(0) U(20) L(11) W(22) O(14) T(19) S(18) A(0) V(21) Encrypted message: TTDQQP QT GAULWO TSAV To decode a message coded using a Vignere cipher, we must have the keyword used to code the message and then we reverse the coding process by subtracting (modulo 26) the letter offset for each letter in the keyword from the offset for each matching letter in the coded message. Basic Text Encryption Schemes Permutation Cypher Divide the characters in the plaintext message into fixed length blocks and permute the letters in each block using the same permutation order. Suppose we want to encrypt the message SPRING IS COMING SOON using a permutation cipher with block size 4. The first step is to put the plaintext characters in groups of 4, padding with spaces at the end, if necessary: S P R I N G I S C O M I N G S O O N Now we pick a permutation of the numbers 1 through 4, say 3 1 4 2, and use this pattern to permute the letters in each group: 1 S 3 R 2 P 1 S 3 R 4 I 4 I 2 P 1 2 3 N G 3 1 4 N I 4 I 2 G 1 2 3 4 S C O 3 1 4 2 C S O 1 M 3 N 2 I 1 M 3 N 4 G 4 G 2 I 1 2 S 3 1 O 3 O 4 O 4 O 2 S 1 2 3 4 N 3 1 4 2 N Encrypted message: RSIP NIGCSO NMGIO OS N If we use the permutation 2 4 3 1 instead, the message has a different coding: 1 S 2 P 2 P 4 I 3 R 3 R 4 I 1 S 1 N 2 G 2 3 4 G I 4 3 1 I N 1 2 3 4 S C O 2 4 3 1 O C S 1 M 2 I 2 I 4 G Encrypted message: PIRSGI N OCSIGNMSOO 3 N 3 N 4 G 1 M 1 2 S 2 4 S O 3 4 O O 3 1 O 1 2 3 4 N 2 4 3 1 N N To decode a message coded with a permutation cipher, we must know the permutation used for the coding and then repeatedly apply it to the letters in the coded message to permute them back to their plaintext positions.







