final exam cmpe553 fall 2010 10012011
advertisement

Final Exam CMPE-553 06.01.2010 (120 min, 40 points)
St. Name, Surname______________________________________ St.Id#_____________
You may use one A4-sized sheet of hand-written paper for you help. Mobiles are not
allowed. Calculators may be used
Instructor Alexander Chefranov
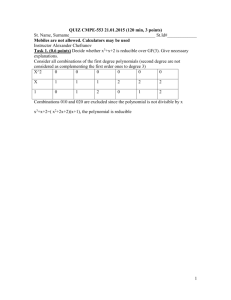
Task 1. (8 points) Decide whether x3+3x2+1 is reducible over GF(5). Give necessary
explanations.
It is reducible as divisible by x+2
1
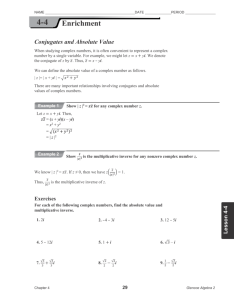
Task 2. (8 points) Decide whether multiplicative inverse of x3+ x2+x-1 mod x5- x4+ x3x2-x+1 over GF(3) exists. If exists, find it and check its correctness by multiplication. If
does not exist, explain why.
Applying Extended Euclidean algorithm, B3=2 is obtained. It means that inverse exists
and equal to B2/B3 =(x4-x3+x2)/2= 2x4-2x3+2x2= 2x4+x3+2x2
Since the next iteration gives B3=0, inverse is not existing.
2
Task 3. (8 points) Calculate a value of the element (9,3) in the AES inverse S-box (Table
5.4, b; it is 22). Show all intermediate steps of the calculation.
Hint: The S-box is constructed in the following fashion:
1. Initialize the S-box with the byte values in ascending order row by
row. Thus, the value of the byte at row x, column y is {xy}
2. Map each byte in the S-box to its multiplicative inverse in the finite
field GF(28) , with the irreducible polynomial m( x) x 8 x 4 x 3 x 1 ;
the value {00} is mapped to itself.
3
3. Consider that each byte in the S-box consists of 8 bits labeled
(b7,b6,b5,b4,b3,b2,b1,b0). Apply the following transformation to each
bit of each byte in the S-box:
(5.1)
bi bi b(i 4) mod 8 b(i 5) mod 8 b(i 6) mod 8 b(i 7 ) mod 8 c i
where ci is the i-th bit of byte c with the value {63}. The inverse S-box is
constructed by applying the inverse of the transformation in (5.1) followed
by taking the multiplicative inverse in GF(28).
The inverse transformation is
bi b(i 2) mod 8 b(i 5) mod 8 b(i 7 ) mod 8 d i
where d={05}, or 0000 0101.
Applying inverse transformation to b=(93), one gets b’=(5a), inverse of which is (22) in
GF(28)
4
Task 4. (8 points) Assume that RSA algorithm is used with the public key (N=21, e=5),
and the ciphertext is C=10. Find the plaintext M. Provide details of your work.
M=19
5
Task 5. (8 points) Consider one step of the round transformation of MD5:
a b (( a g (b, c, d ) X [k ] T [i ]) s)
where
a,b,c,d – the four words of the buffer, in a specified order that varies across steps
g – one of the primitive functions F,G,H,I
<<<s – circular left shift (rotation) of the 32-bit argument by s bits
X[k] – M[q 16+k] – k-th 32-bit word in the q-th 512-bit of the message
T[i] – the i-th 32-bit word in matrix T
+ - addition modulo 2 32 .
Assume for simplicity that a, b, c, d are two-byte words (hexa-decimal numbers):
a=0x6745, b=0xEFCD, c=0x98BA, d=0x1032, addition is made modulo 216, and
F(b,c,d)= (b c) (b d ) . Calculate a F (b, c, d ) under such assumptions.
Result is 0xFFFF
6