mandatory - University of Notre Dame
advertisement

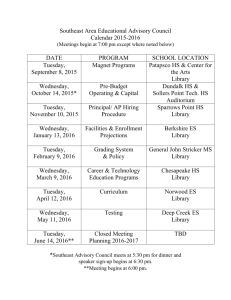
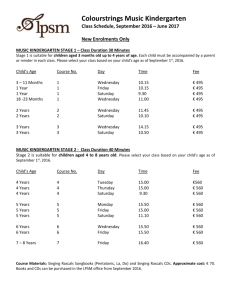
mandatory Wednesday, February 17, 2016 Slide 1 Slide notes: Text Captions: Online Information Security Training Audio: As members of the University community, we have access to many forms of sensitive data from performance reviews, student records and payroll information to research data. It's our responsibility to make sure that this data is kept secure. Information security is everybody's business. Page 1 of 42 mandatory Wednesday, February 17, 2016 Slide 2 Slide notes: Text Captions: Explanation of tutorial boxes, player bar, audio, and closed captioning Audio: This fifteen minute presentation will give you a better idea of where we may be at risk and what we can do to minimize it. You can go back or forward or pause, using the player bar. At times you will be asked to make choices to give you the information best suited to your situation. The presentation will be the same approximate length, regardless of your choices. Page 2 of 42 mandatory Wednesday, February 17, 2016 Slide 3 Slide notes: Text Captions: Slide content: Information Security isn't just about computers; it’s about how we access, process, transmit and store sensitive information in all forms. It covers laptop and desktop computers, but also includes paper records, telephone conversations and other media. Video: show snapshots of: a laptop a desktop computer cds flash drives paper notebooks hard copy of spreadsheets, paper coming out of a printer or copier someone on the phone Audio: Just what is Information Security? It isn't just about keeping our computers safe. It's about how we access, process, transmit and store sensitive information in all forms. It covers laptop and desktop computers, but also includes paper records, telephone conversations and other media. Page 3 of 42 mandatory Wednesday, February 17, 2016 Slide 4 Slide notes: Text Captions: Slide content: Myths No one wants my stuff I only surf a little The University/OIT is protecting me Audio: It can be hard to believe that the things we do put sensitive information at risk. It's not like we are reckless or oblivious to the dangers. And besides, isn't it OIT's job to keep us safe? Page 4 of 42 mandatory Wednesday, February 17, 2016 Slide 5 Slide notes: Text Captions: Slide content: Facts Do you really know what's on your computer? Going once to the wrong website can cause disaster There's only so much the University/OIT can do Audio: The fact is that all the protections OIT puts in place can't help if we visit the wrong web sites. And having a firewall in place on our computer isn't going to keep someone from seeing the printout of sensitive data on our desk. Page 5 of 42 mandatory Slide 6 Slide notes: Text Captions: Slide content: What we ask of you: Ask Is it secure? video: logo Audio: We all have to start asking ourselves Is it secure? About each file on our computer About our work area About the ways we access, process and transmit information Is it secure? Page 6 of 42 Wednesday, February 17, 2016 mandatory Wednesday, February 17, 2016 Slide 7 Slide notes: Text Captions: Slide content: University data student records employee records payroll information grades health information Audio: In the course of carrying out its mission, the University creates or maintains certain data such as student and employee data and payroll information. This data is a University resource, owned by the University. Some data that is part of life on campus is not owned by the University. This includes class notes, lesson plans, personal papers, and other materials covered in the University’s Intellectual Property Policy. video: visual representations of student records, employee records, payroll info, grades, health info, etc. Page 7 of 42 mandatory Wednesday, February 17, 2016 Slide 8 Slide notes: Text Captions: Slide content: classes of University data public internal sensitive highly sensitive Audio: University data is not all handled the same. How it must be handled depends on its classification. There are four classes of University data: public, internal, sensitive and highly sensitive Page 8 of 42 mandatory Wednesday, February 17, 2016 Slide 9 Slide notes: Text Captions: Slide content: Public data information intended for public use that, when used as intended and not altered, would have no adverse impact on University operations, University assets, or individuals. Audio: Public data is information intended for public use that, when used as intended and not altered, would have no adverse impact on University operations, University assets, or individuals. This would include press releases, articles and information on non-restricted web sites, ?????? video: pictures of public info Need more examples of public data Page 9 of 42 mandatory Wednesday, February 17, 2016 Slide 10 Slide notes: Text Captions: Slide content: internal data information not intended for parties outside the University community but, if disclosed, would have minimal or no adverse impact on University operations, University assets or individuals. Audio: Internal information is not intended for parties outside the University community but, if it is disclosed, it would have minimal or no adverse impact on University operations, University assets or individuals. Examples of internal information include ????? Need more examples of internal data video: pictures of internal info Page 10 of 42 mandatory Wednesday, February 17, 2016 Slide 11 Slide notes: Text Captions: Slide content: sensitive data Sensitive data is information whose mishandling could be expected to have a serious adverse effect on University operations, University assets or individuals. Audio: The mishandling of sensitive information could be expected to have a serious adverse effect on University operations, University assets or individuals. Examples of sensitive data would include ????? Need more examples of sensitive data video: pictures of sensitive info Page 11 of 42 mandatory Wednesday, February 17, 2016 Slide 12 Slide notes: Text Captions: Slide content: highly sensitive data Highly sensitive data is information whose mishandling could be expected to have a severe or catastrophic adverse effect on University operations, University assets or individuals. Audio: The mishandling of highly sensitive information could be expected to have a severe or catastrophic adverse effect on University operations, University assets or individuals. Examples of highly sensitive data would include ????? Need more examples of highly sensitive data video: pictures of highly sensitive info Page 12 of 42 mandatory Wednesday, February 17, 2016 Slide 13 Slide notes: Text Captions: Slide content: data stewards Data stewards are responsible for ensuring the confidentiality, integrity, and availability of the University information for which they are responsible. They define access to this information and restrictions on its use. Audio: Because of the risk involved should sensitive or highly sensitive data be mishandled, data stewards have been named to control the various types of University data. These data stewards are responsible for ensuring the confidentiality, integrity, and availability of the University information for which they are responsible. They define access to this information and restrictions on its use. Some examples of data stewards include the registrar for student records, and Human Resources for employee records. video: pictures representing data steward controlled-data Page 13 of 42 mandatory Wednesday, February 17, 2016 Slide 14 Slide notes: Text Captions: Slide content: University community Protect the privacy and security of University information, applications, computer systems, and networks under their control Adhere to all relevant data handling standards Report suspected violations of this policy to the Director of Information Security or to the appropriate Data Steward video: snapshots of people at work around campus Audio: As members of the University community, it's our responsibility to protect the privacy and security of University information, applications, computer systems, and networks under our control. We must adhere to all relevant data handling standards and report suspected violations of this policy to the Director of Information Security or to the appropriate Data Steward. If our jobs require access to or use of information owned by a data steward, we must follow their data handling regulations. Page 14 of 42 mandatory Wednesday, February 17, 2016 Slide 15 Slide notes: Text Captions: Slide content: Securing your workspace Lock your door or drawer Be aware of what people can see Be careful of leaving papers in shared spaces and printers video vignettes of actions listed Audio: Adhering to the data handling standards set in place by the data stewards will keep that data safe but there is more we need to do. We need to secure our workspace. We can do this by locking our door when we leave our office. If we share space with others, we need to lock sensitive data in a drawer. We need to be aware of what people can see when they come to our work area--what documents we have left out. And make sure we never leave documents in printers and copiers. Page 15 of 42 mandatory Wednesday, February 17, 2016 Slide 16 Slide notes: Text Captions: Slide content: Securing your workspace: storage video vignettes of actions listed Audio: Keeping data secure also involves storing it safely. Leaving it in the open in a locked office is only secure clearance if *everyone* accessing that office has the proper security to see that information. Otherwise, it should be in a locked drawer. Page 16 of 42 mandatory Wednesday, February 17, 2016 Slide 17 Slide notes: Text Captions: Slide content: Securing your workspace: disposal How to dispose of hard copies How to dispose of electronic media video vignettes of paper and cd shredding Audio: When you are finished using hard copies of sensitive data, you need to dispose of them safely. This means shredding them. Don't just throw them into the trash or the recycle bin. If you have sensitive data on electronic media such as cds or dvds, they need to be destroyed also. Many shredders will shred these also. Page 17 of 42 mandatory Wednesday, February 17, 2016 Slide 18 Slide notes: Text Captions: Slide content: Safe computing What type of computer do you use at work? mac pc do we need to include linux? video: montage of people using computers at work Audio: Besides keeping our workspace secure, we need to practice safe computing. We do this in a number of ways, some are dependent on which platform we use. Page 18 of 42 mandatory Wednesday, February 17, 2016 Slide 19 Slide notes: Text Captions: Slide content: Take Charge: What it is what it includes (antivirus, antispyware, security updates) Have you run Take Charge on your work computer? Yes No I'm not sure Audio: The TakeCharge installer helps secure your pc against viruses, malicious programs, and other security threats. It sets your firewall, sets your preferences to automatically apply security updates to your operating system and installs anti-virus software as well as two anti-spyware programs. It also installs software the Help Desk can use to diagnose problems. Page 19 of 42 mandatory Wednesday, February 17, 2016 Slide 20 Slide notes: Text Captions: Slide content: Take Charge: watch for upgrades! Audio: TakeCharge is periodically upgraded to improve the security features. Make sure you reinstall it when you see that an upgrade has been released. video: grab of OIT page showing Take Charge upgrade announcement link Page 20 of 42 mandatory Wednesday, February 17, 2016 Slide 21 Slide notes: Text Captions: Slide content: Take Charge: The link is on every OIT web page. Audio: The link to the Take Charge web page can be found on any OIT web page, on the right. It's also available from secure.nd.edu. video: grab of OIT page showing Take Charge link Page 21 of 42 mandatory Wednesday, February 17, 2016 Slide 22 Slide notes: Text Captions: Slide content: Take Charge: Check with your IT support person to find out if you should run it on your work machine. Audio: If you have an IT support person in your college, you may have Take Charge already installed on your computer. If you don't have it, ask why not. Remember, keeping your computer secure is your responsibility. Page 22 of 42 mandatory Slide 23 Slide notes: Text Captions: Slide content: Safe computing: domain membership Do you belong to the ADND domain? Yes No Not sure Audio: Belonging to the ADND domain can increase the security of your computer. How??? Page 23 of 42 Wednesday, February 17, 2016 mandatory Slide 24 Slide notes: Text Captions: Slide content: Domain membership: What does it do for you? How do you join? Audio: What does it do for you? How do they join? Page 24 of 42 Wednesday, February 17, 2016 mandatory Slide 25 Slide notes: Text Captions: Slide content: Domain membership: What is it doing for those currently belonging? Audio: What is it doing for them? Page 25 of 42 Wednesday, February 17, 2016 mandatory Slide 26 Slide notes: Text Captions: Slide content: Domain membership: How can I find out if I belong? Audio: How can I find out if I belong? Page 26 of 42 Wednesday, February 17, 2016 mandatory Wednesday, February 17, 2016 Slide 27 Slide notes: Text Captions: Slide content: Safe computing: anti-spyware Spyware is software installed on your computer without your knowledge. Its purpose is to collect personal data including logins and passwords, credit card numbers and other sensitive data, the web sites you visit, and even files you are accessing. This collected data is then sent to designers of the software. video: a spy on a computer? Audio: Spyware is a real danger when you are on a network. It can come from visiting the wrong web sites, from downloading "free" software, and in emails, text messages and shared files. Once it's on your machine, it spies on you--keeps track of where you go on the web and what you do. It can even record your logins and passwords and send them back to the software's originator. Page 27 of 42 mandatory Wednesday, February 17, 2016 Slide 28 Slide notes: Text Captions: Slide content: Safe computing: anti-spyware Ad-Aware and Spy-bot installed with TakeCharge on your PC you need to run them regularly to find and remove spyware video: show logos of anti-spyware Audio: TakeCharge installs two anti-spyware programs on your pc: Ad-Aware and Spy-Bot. Both of these programs will locate suspicious files on your computer and flag them for possible deletion upon your review. Since they work differently, it's recommended that you run both of them--and do so regularly. They aren't automatic. Page 28 of 42 mandatory Wednesday, February 17, 2016 Slide 29 Slide notes: Text Captions: Slide content: Safe computing: Antivirus software Software that scans files for known viruses. This includes auxillary drives, email and attachments, and files we download from other sources. On campus we use: McAfee VirusScan for the PC Norton's Anti-Virus for the Mac video: show logos of anti-virus Audio: Anti-virus software is only as good as the virus definitions. They are changing constantly as new viruses are being written so your software must be set for daily updates of virus definitions. TakeCharge installs McAfee VirusScan on your computer and sets the preferences for daily updates. If you install Norton's Anti-virus on your Mac, the preferences will be configured for daily updates. Don't disable the scanning! Page 29 of 42 mandatory Wednesday, February 17, 2016 Slide 30 Slide notes: Text Captions: Slide content: Safe computing: storage The most secure place to store files that contain sensitive data is your NetFile space. Audio: What's the equivalent of a locked drawer for electronic files? Your Netfile space. It's backed up daily and protected by a moat full of alligators. Page 30 of 42 mandatory Wednesday, February 17, 2016 Slide 31 Slide notes: Text Captions: Slide content: Safe computing: encryption Encryption is a process that encrypts or encodes the contents of a folder or computer so that only authorized users may obtain access. Is your work computer encrypted? Yes No Audio: Encryption offers even greater protection against unauthorized access to your files. While it's strongly recommended that all laptops be encrypted, any computer can be. Page 31 of 42 mandatory Wednesday, February 17, 2016 Slide 32 Slide notes: Text Captions: Slide content: encryption: Utimico what it does? why you should encrypt? Audio: Utimico is the encryption software used on campus. Once it is installed on your computer, all the files on your computer will be encrypted and will require a password to access them. How is this different from logging in to ADND to get to your computer? Page 32 of 42 mandatory Wednesday, February 17, 2016 Slide 33 Slide notes: Text Captions: Slide content: Encryption: Be aware that flash drives and other auxillary drives connected to your encrypted computer are not encrypted! Audio: Be aware that flash drives and other auxillary drives connected to your encrypted computer are not encrypted! Page 33 of 42 mandatory Wednesday, February 17, 2016 Slide 34 Slide notes: Text Captions: Slide content: encryption: VPN The VPN gateway is a network access service which permits remote systems to access the ND network as if they were physically located on the ND campus network. You can download the VPN software off the secure.nd.edu web page. Audio: VPN or Virtual Private Network sends data over encrypted channels to maintain security. You should use it whenever you are accessing sensitive data from off-campus. Some systems, even some on campus, require the use of VPN. video web page with VPN links Page 34 of 42 mandatory Wednesday, February 17, 2016 Slide 35 Slide notes: Text Captions: Slide content: Safe computing: Sensitive Number Finder We are no longer allowed to collect Social Security Numbers or maintain old records containing SSNs except when absolutely necessary. If your department has a legitimate business need for the use of SSNs, you may do so only with the concurrence of the University Officer or Dean responsible for your area, in consultation with the CIO and the Office of General Counsel. Credit card numbers should only be used as part of approved merchant activities coordinated through the University Credit Card Support Program (CCSP). Audio: John Affleck Graves, Executive Vice President of the University, has stated that: In today's climate, it is no longer acceptable for us to collect Social Security Numbers or maintain old records containing SSNs except when absolutely necessary. SSNs should only be used in cases where government requirements mandate such use. If your department has a legitimate business need for the use of SSNs, you may do so only with the concurrence of the University Officer or Dean responsible for your area, in consultation with the CIO and the Office of General Counsel. Credit card numbers should only be used as part of approved merchant activities coordinated through the University Credit Card Support Program (CCSP). Page 35 of 42 mandatory Wednesday, February 17, 2016 Slide 36 Slide notes: Text Captions: Slide content: Safe computing: SENF Notre Dame has created a Sensitive Number Finder to help locate files on our computers that contain sensitive numbers. Have you run the Sensitive Number Finder? Yes No Audio: Notre Dame has created a Sensitive Number Finder to locate files on our computer that may contain sensitive data. All employees have been asked to run this on their computers. Many of the files that contain sensitive numbers are ones we've forgotten about or no longer need. Keeping our computers as free of sensitive data as possible keeps us all safer. Page 36 of 42 mandatory Wednesday, February 17, 2016 Slide 37 Slide notes: Text Captions: Slide content: SENF The Sensitive Number Finder needs to be run regularly to keep your computer free of unused sensitive data. video something of SENF Audio: Running the Sensitive Number Finder should be part of your regular routine for safe computing. Page 37 of 42 mandatory Wednesday, February 17, 2016 Slide 38 Slide notes: Text Captions: Slide content: SENF The Sensitive Number Finder can be found at the secure.nd.edu Web site. All instructions for running it as well as tutorials can be found at that web site. Audio: You can download the Sensitive Number Finder from the secure.nd.edu web page. Instructions for running it can be found there also. Depending on the number of files and the locations you are scanning this process can take anywhere from fifteen minutes to an hour or more. Despite the time committment needed, it's something we all must do. Page 38 of 42 mandatory Wednesday, February 17, 2016 Slide 39 Slide notes: Text Captions: Slide content: Safe computing: removing files Files containing sensitive data can be removed through the Sensitive Number Finder or they can be electronically shredded through Spy-Bot. Audio: Spy-bot, the anti-spyware program for the pc, has the ability to electronically shred a file. To do so, change to Advanced Mode, then choose Tools and Secure Shredder. This causes Spy-Bot to overwrite the file five times so make sure you pick the right file. This is not undo-able. Page 39 of 42 mandatory Wednesday, February 17, 2016 Slide 40 Slide notes: Text Captions: Slide content: Safe computing: disposal of computers and drives Old computers, hard drives and even flash drives can be sources of sensitive information. It's important that the data be removed before they are disposed of. Audio: Disposing of computers and auxilliary drives properly is very important. Reformatting the hard drive is not enough to permanently erase the data. The secure.nd.edu web page has a link to help you permanently clean a hard drive. If you are disposing of computers through ND surplus, they will be wiped clean for you. Page 40 of 42 mandatory Wednesday, February 17, 2016 Slide 41 Slide notes: Text Captions: Slide content: secure.nd.edu is the place to go for more information about information security, to read the policies in place, and to find out who to contact with questions. secure.nd.edu Audio: For more information about the subjects covered here, to read the policies in place,or to find out who to contact with questions or concerns, visit secure.nd.edu Page 41 of 42 mandatory Slide 42 Slide notes: Text Captions: Slide content: To verify who has viewed this online presentation, please enter your NetID in the field below. Audio: Please enter your NetID in the field and click on Enter. Page 42 of 42 Wednesday, February 17, 2016