RSA_Project Description
advertisement

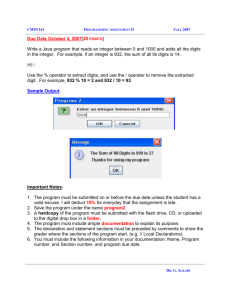
Peter Burnett MAT 7305 Technology in the Teaching of Mathematics Klaus Volpert December 8, 2004 Project Overview: This purpose of this project is to introduce methods of encryption to the students. It will cover a brief history but will concentrate on the RSA method. Through this lesson the student will learn the method of RSA encryption and demonstrate understanding of how the RSA method works. The students will be expected to have pervious knowledge of prime numbers, exponents, number bases other than 10, very basic modular arithmetic, and some programming background. The students will also be introduced to the computer algebra system Maple and some of its basic functions. They will work through a few given examples, produce their own encryption keys and try to use what they have learned to attempt to break other encryptions. Grading will be based on the student’s ability to encrypt and decrypt information. They will discover their grade is as they go along. The students will be turning in answers to the questions in this project and their output from Maple. Brief Definition and History: Cryptology (from the Greek Kryptos 'hidden' and logos 'word') is the science of secure communications. Cryptology is split into two subdivisions: cryptography and cryptoanalysis. The cryptographer (soon to be you) seeks to find methods to ensure the secrecy, integrity, and/or authenticity of messages. The cryptoanalyst seeks to undo the former's work by breaking the cryptographer's cyphertext/cryptogram (encrypted plaintext) or by encrypting signals that will be accepted as authentic by the receiver. It is easy to think of an example of when someone would want to send secret messages such as credit information, secret strategies, etc. There have been many different methods used over time, all of which rely on a key of some sort to encrypt and decrypt messages. These keys can either be private, only the sender and receiver know, or public, where everyone knows at least part of the key. Private key cryptography is perhaps the most traditional method of cryptography. One user would use a key that only he knew to encrypt a message using some function. The Greek historian Polybios developed one of the earliest systems. He used a grid of letters where each letter of the message was replaced by the two letters indicating the row and column in which the original letter lies. Below is an example of a Polybios square with the English alphabet excluding the letter J. SYDWZ R I P U L HC A X F TNO G E BKM Q V Here RD would replace P, and G would be replaced by TW. Another system used was the CAESAR system. In this system, the kth letter beyond it replaces each letter, where k is the key. For example, say the message were the word "PRIVATE" and we use the private key k=4. Under the CAESAR system this would yield TVMZEXI. The user could then send this message to the recipient who also knew the algorithm and the key. This is a very simple example of a private key algorithm. These are two fairly basic systems. Another very famous system, used by the Germans during WW2, utilized a series of keys to encrypt information. The machine that would apply this system was called the Enigma Machine. It used a code wheel (alphabetic) and numerical key. The letter on the code wheel would correspond to a number in the key. This number would correspond to a shift in the alphabet to choose the cipher text. Below is an example: Key: Shift By: Plain Text: Cyfer Text: G 7 T A E 5 H M R M 19 13 E B W P A 1 O P N Y 14 25 A T O S G 7 L S E 5 A F R M 19 13 N D F Q A 1 S T N Y 14 25 T O H N G 7 N U E 5 I N R M 19 13 G H Y U A 1 T U N Y 14 25 X X L W The main idea behind public key cryptography is that not only can one make his algorithm public, but one can make his key public as well. A person might publish their public key in a directory, and anyone who wishes to send that person secure information can encrypt that information using the public key and send it over insecure channels. Then when the cryptotext/cyfertext gets to the receiver he can decrypt it using their private key. This way, anyone can encrypt information, but only the person with the private key can decrypt it. Here the key that encrypts the message does not decrypt it. Calculating the decryption key from the encryption key requires solving a difficult mathematical problem, likely impossible. We will be looking in depth at the RSA (Rivest, Shamir, and Adelman in1978) method which relies on the fact that it is easy to check if numbers are prime and it is also easy to multiply numbers but it is very difficult to factor numbers. The RSA method relies on Fermat’s Little Theorem: For any prime number p and any number a 0 a p1 1 mod p The RSA method uses the following function encrypt: fi ,n ( x) xi (mod n) Where i, n and x are large integers, typically over 100 digits. For our purposes we will use smaller values for examples. If you know i, n and x it is relatively easy to compute fi ,n ( x) , but not necessarily the reverse. The numbers i, and n form the public key (i, n). The secret key, (j, n), is n and another large number j such that xij x (mod n) . The three numbers (i, j, n) form the key pair. This number j can also be found using the Extended Euclidian Algorithm, which says if i and (p-1)(q-1) are relatively prime then we have the linear combination: i * s ( p 1)(q 1) * t 1 This equation will have integer solutions. Once you have found integer solutions to this the number j = s forms the final part of our secret key. This gives the following function used to decrypt: g jn ( y) y j mod n Interesting note: In 1996, a team of many mathematicians made the headlines (in the science section) because they factored a number of 129 digits, after months of computation. Here is that factorization: 114381625757888867669235779976146612010218296721242362562561842935706935 245733897830597123563958705058989075147599290026879543541 = 3490529510847650949147849619903898133417764638493387843990820577 x 32769132993266709549961988190834461413177642967992942539798288533 Once they found the factorization, they could decrypt a message that Rivest, Shamir, and Adelson had given as a challenge. The decrypted message was The magic words are squeamish ossifrage; this sentence was hidden in a 128-digit ciphertext. In this case, n had “only” 129 digits. With every digit that you add, the problem becomes much harder. In practical RSA schemes, n has 200 or 300 digits. Maple: Getting Started First thing we need to do is open the program called Maple. This is a very powerful computer algebra system that is going to help all of us become experts in cryptography. Before we get started with that, we need to learn a few basics about using this program. If at any time you have a question, try to use the Help menu to figure it out. It can be very helpful. Let’s try a few things. Input the following into Maple: 2+3 then press enter… Did you get an error? That was because every line needs to end in a semicolon ( ; ) if you want to see the output, and a colon ( : ) if you want to suppress the output. Let’s try that again. 2 + 3; You should get 5. then press enter Try a few things on your own using the following operations: +, -, *, /, and ^. Now we will look at a few built in functions. If we need a prime number we can use the function: ithprime(5); This will give us the 5th prime number. We can also check if a number is prime by using: isprime(25); This will return true or false. Another interesting tool is the factoring function. If we want in the integer factors of a number we can use: ifactor(24); 3 This would return ( 2 ) ( 3 ) Just for fun choose a number 30-35 digits long and see how long it takes Maple to factor that number. We can define functions and variables to aid us in our calculations. Say we want to define the function f ( x) 3x 2 6 x 2 We would enter: f:=x->3*x^2-6*x+2; To define a variable we can simply write the equality: p:=13; This would set the value of p to 13 so for all future uses of p it would be 13 unless we change it. We could then evaluate f(p); This would return 431 Lastly if we have two numbers we can easily set up a linear equation using the two numbers and its Greatest Common Divisor. We will want that to be one thus the numbers are relatively prime. If given the numbers 13 and 3000 their GCD = 1. Therefore there exist integer solutions to the equation 13s 3000t 1. Why those numbers? We will get to that later. Question: Will there be integer solutions to this equation if it were 13s 3000t 2 ? If we want to find solutions to the original equation we can use the function igcdex(13,3000,'s','t'); This will set the values s and t to one possible solution to the equation. Type s,t; to see what those values are. Question: How can you get other solutions to this equation? Use the following are to make some notes about things you might want to remember about Maple or had trouble with. They may help you in the future. Review of Modular Arithmetic: The number X (mod Y) is the remainder when X is divided by Y. (Remember X (mod Y) stands for X modulo Y.) For example: 7 modulo 3 is 1 Because: 7–2*3+1 So when you divide 7 by 3, You get a remainder of 1. The “modulo Y” terminology can also be used in the following way: Z=X (mod Y) (This stands for Z equals X modulo Y, which means that Z and X have the same remainder when divided by Y.) For example: 7 = 25 (mod 3) Because: 7=2*3+1 25 = 8 * 3 + 1 so when you divide 7 or 25 by 3, you get a remainder of 1. We will mainly concern ourselves with the first type of example. Try the following by hand: 1. 5 (mod 2) = 2. 38 (mod 5) = 3. 51 (mod 12) = 4. 1254935 (mod 100) = 5. 8246 (mod 143) = 6. 4^3 (mod 7) = These can all be done using Maple using the following notation: 38 mod 5; 3 After you have done these my hand, confirm your answers using Maple. The RSA Method Finally!!! Lets get started. Exercise 1: How the basic structure works. For these exercise you may work with a partner, this to help each other, not an opportunity to just copy off your partner. To get started we need to choose our prime numbers to work with. We will choose our two secret prime numbers to be p 31 and q 37 so n pq 1147 . Next we will use i 43 . This gives a public key of 43,1147 . This is enough to encrypt information but not enough to decrypt it so we need to figure out our secret key. I guess it is a good thing we know what p and q are. Using the Extended Euclidian Algorithm we need to find integer solutions to the equation: 43s (31 1)(37 1)t 1 43s 1080t 1 This is where Maple is going to really help us. First let’s set up our parameters (variables) in Maple. (Look back to Maple: Getting Started) 1. Set variables equal to all our values we have chosen so far. 2. Get an integer solution to 43s 1080t 1 , this will give us the final part to the secret key. 3. Let j equal s. Question: What value did you get for s and t? Question: What is your public key? What is your secret key? We now have everything we need to encrypt and decrypt. Say you wanted to purchase that perfect gift for your teacher from a website on the internet. You would need to send them your credit card information. If your card number is 1029 1120 0864 0099 we can encrypt this number and send it over insecure lines and not worry about someone steeling our information. 1. Split the credit card number into four separate numbers. 2. Define the function fi ,n ( x) xi (mod n) in Maple. 3. Using Maple encrypt each separately using f(1029); f(1120); f(0864); f(0099); What numbers did you get? 4. Now decrypt those numbers and make sure you did it correctly. Define the function g jn ( y) y j mod n What numbers did you get? Were they the same that you encoded? Now that you have successfully completed an encryption and decryption take a minute and answer the following questions. Question: Could this public key have been broken? Why/Why not? If so what could have been done to make it harder or impossible? Question: Would our values have worked if the credit card numbers were larger, say 9263? Why/Why not? Question: Could we have looked at the series of sixteen digits as one number? Why/Why not? Question: What could we do to avoid all the problems in the previous three questions? Exercise 2: Encoding Text For exercise you may continue to work with a partner. In this example we will explore the possibility of sending messages that include text. To do this we will need decide what characters will be used and assign all of them a numerical equivalent. We can then encrypt and decrypt those numbers as in exercise one. For this we will use 30 characters. Roman letters ‘A’ to ‘Z’ are numbered 0 to 25, blank space ( ) = 26, period (.) = 27, comma (,) = 28, and the question mark (?) = 29. In this exercise you will be using new values of p, q, n, i, and j. Be sure to use Maple as we did in exercise one. 1. Choose new primes p and q (not too big yet). 2. Calculate n. 3. Choose and appropriate value for i. 4. Calculate s and t and therefore j. 5. Note your public key. 6. Note your private key. 7. Write your public key on the board along with your name in the class directory. 8. Choose another public key and check it off so it will not be used again. 9. Write out a short phrase or sentence (I will be watching). 10. Convert those characters to numbers using the method above. 11. Encrypt your message using the encryption function. This will give you a series of numbers. Write them out with commas to separate them. (34, 153, …) 12. Give your encrypted message to the appropriate group for them to decode. You should receive one to work on yourself. 13. Decrypt the message someone sent you using your private key. Exercise 3: Code Breaking For exercise you may continue to work with a partner. Now try breaking and decoding mine: Public pair: (31, 3149). Cyfertext: 341,2378,517,2442,1339,2378,2841,2442,0,2442,1,849 Question: What were p, q, n, i, j? Question: What was the private key? Question: What was the original text? This is little more than a cryptogram in the Sunday newspaper. If you notice a pattern you could figure out to which letter each number corresponds. What could we do to make it harder to find patterns in our encrypted message? Question: Could we just erase the commas so an interceptor can’t see the individual letters(341237851724421339237828412442024421849)? Why/Why not? Question: What could we do so we could avoid using commas or any separation device and still be able to accurately decode the message? Exercise 4: Text to Text Encryption For exercise you may continue to work with a partner. You may have noticed in the last example, after we encoded our numbers (0-30) they may have gotten very large. Question: How large can the number be after encoding? In this exercise we will encrypt blocks of text to other blocks of text. Now along with the public key and secret keys the sender and receiver will have to know what size the blocks of text are to be used. For example the code: “THE RAVEN FLIES AT MIDNIGHT.” could be broken into block of two letters such as: TH|E |RA|VE|N |FL|IE|S |AT| M|ID|NI|GH|T.| This would give us blocks of numbers: 19 7 | 4 26 | 17 0| … What we can then do is convert these integer digits into a number in base 10 as if it were in base 30 in the following manner: 19*30 7 557 The 19 is in the 30’s column and the 7 is in the 1’s column. 1. Finish converting the letters to integer digits. 19 7| 4 26|… 2. Finish converting the integer digits to base 10. Question: Why are we assuming the number was in base 30? Why not use base 10 in the first place or base 40 or 15? Question: What is the largest number you can get after converting one of these integer digits to base 10? 3. 4. 5. 6. 7. 8. 9. Use primes p = 97 and q = 71. Calculate n. Use i = 59. Calculate s and t and therefore j. Note your public key. Note your private key. Encrypt your blocks of numbers using the encryption function. Question: How large are your encrypted values compared to your non-encrypted values? We now need to reverse the process of converting between base 10 and integer digits in base 30. For example 2787 base 10 converts to 3 2 27 in integer digits in base 30. 2787 / 900 = 3.0966 2787 – (30^2 * 3) = 87 87 / 30 = 2.9 87 – (30 * 2) = 27 10. Now finish converting all your encrypted numbers to integer digits. Question: What is the largest number any of these integer digits can be? Why? 11. Convert those integer digits back to characters. Question: What size are your new blocks of text? Question: What additional information will the sender and receiver need other than the public key and private key to encrypt and decrypt messages? Exercise 5: Code Breaking (Again) For exercise you may continue to work with a partner. This is you final exercise to prove you are now an expert in the RSA method of public key encryption. Given the following information break the code and discover your grade on this project. Sender block size: 2 Receiver block size: 3 Public Key: (43, 16241) Remember you are the receiver trying to decode the message without the private key. LHMIQIMEALCEPEKE. HHZQJORJFKPECVIEODGVRCXPPI.MOC Exercise 6: Maple Programming For exercise you may continue to work with a partner. Through all of these exercises there have been many repeated calculations. With a little programming we can have Maple do all of that for us in a fraction of the time. Now that you have already figured out what the encryption in exercise 5 means we can use it again in this exercise so we will always know if the calculations are correct. When programming it is always best to make an outline of the process we are trying to complete. Here is a list the major steps we used in exercises four and five: 1. Convert text blocks to integer digit blocks 2. Make a list of those blocks (integer digit pairs) 3. Convert integer digits from base 30 to base 10 4. Encrypt those numbers 5. Convert encrypted numbers from base 10 to base 30 (integer digits) 6. List new blocks (integer digit triples) 7. Convert integer digit blocks to text blocks We will use maple to do all the calculations in steps 3 through 6. As we work through this there will be tips on how to use Maple. Lists: You can define a list, L, of elements very much like defining a variable: L:=[[1,2],[2,3],[3,4]]; This list contains the ordered pairs (1, 2), (2, 3) and (3, 4). You can count the number of elements in list L by using: nops(L); To replace the k-th element in list L with x use: L:=subop(k=x,L); Procedures / Functions To define a procedure/function we name it and define what it will be accepting: base:=proc(L,k) end; This procedure “base” will accept two things, L and k. In our uses L will be a list and k will be a constant. To send values to a procedure use: value:=base(integers,k) This will send the list “integers” and constant “k” to the procedure where they will be referred to as L and k respectively because of the was we defined it earlier. The variable “value” will be set equal to whatever value is returned from the procedure. Loops: To write a loop that will run 10 times we can use a “for” loop: for k from 1 to 10 do end do; This will do whatever is between the “do” and “end do” 10 times with the value of k incrementing from 1 to 10. Arrays: An array is a block of variables (matrix) that all have the same name other than an index to differentiate between values. The array does not have to be defined before using. To set the k-th value in the array “conv” equal to m use: conv[k]:=m; Section and subsections: To keep our work neat we will put each portion of our program in to subsections within an overall section with the title of our program. To create a section: 1. Click “Insert” 2. Click “Section” This will give you a place to type the title of the section in plain text, notice no > at the beginning of the line. Once you have titled the section you can press enter to go to the next line and you should type an explanation of what is contained in the section. Now you may want to create a subsection: 1. Click “Insert” 2. Click “Subsection” Again you can title the subsection then press enter to type an explanation of the subsection. To change back to a math input (>) press “ctrl j”. If you ever want to add text press “ctrl t”. Let’s get started with programming. 1. 2. 3. 4. Open a new page in Maple. Create a new section and title it “Encoding Program”. Type a description of what the program is going to do. Create a new subsection and title it “Entering Constants”. In this section you will be entering p, q, and i. 5. Set variables p, q, i, and n equal to appropriate values from exercise 5. 6. Create a new subsection and title it entering digits. In this section you will enter the integer digit blocks, which you have calculated by hand, into a list. 7. Set a list “integers” equal to the list of integer digit blocks (size 2). 8. Set a variable equal to the number of elements in list “integers”. 9. Set another list “integersencrypted” equal to the same set of integer digit blocks. These will be changes later. You just need placeholders. 10. Set a variable equal to the number of elements in list “integersencrypted”. 11. Create a new subsection and title it “Converting integer digits to base 10”. In this section the integer digit blocks will be converted to base 10 from base 30. 12. Enter the following procedure named “base”: Accepts two variables and names them L and k. L base:= proc(L,k) will be our list and k a counter op removes the [ ] local T, x, y: from list L T:= op(L): Defines three local variables x:=T[k,1]: y:=T[k,2]: x = the 1st value of the k-th element in list L Converts to base 10 x*30+y: y = the 2nd value of k-th element in list L and returns that value end; This procedure will convert only the k-th element in the list from base 30 to base 10. We will need a loop to apply this to all elements in the list. 13. Define a for loop that will run enough times to send every element in list “integers” to the procedure “base”. Use the following to set the array value “conv[k]” to the value returned from procedure “base”. conv[k]:=base(integers,k): The converted values are now stored in the array. 14. Create a new subsection and title it “Encryption”. In this subsection you will be encrypting all the converted values. 15. Define a function, h, to encrypt your values. 16. Have you saved your program yet? It would be a good idea to do now and then. 17. Define a for loop that will run enough times to encrypt all your converted values. 18. In the loop set the array value “encry[k]” equal to the function evaluates at “conv[k]”. The encrypted values are now stored in the array encry[k]. 19. Create a new subsection and title it “Converting back to integer digits”. In this subsection you will be converting the base 10 numbers to base 30 and thus our encrypted integer digits. These will be blocks of three integer digits. 20. Define a for loop that will run enough times to convert all the encrypted values to blocks of integer digits. trunc(n) takes the integer part of n 21. In this loop use: x1:=trunc(encry[k]/30^2): x1,x2, and x3 are the x2:=trunc((encry[k]-(x1*30^2))/30): converted x3:=encry[k] mod 30: integer digits integersencrypted:=subsop(k=[x1,x2,x3],integersencrypt ed): The new integer digits are now stored into the list “integersencrypted”!!!! If you have been ending your lines with a colon Maple didn’t output the values. Renames the elements in the list integersencrypted to the new integer blocks 22. To see the list of encrypted integer digits type: integersencrypted; This will give you a nice neat list of all your new integer digits which you can then translate to text (cyfertext). Does this match the encoded message in exercise 5? Now that we have a nice program to encrypt information can we use the same framework to write a program to decrypt a message? Yes!!! See exercise 7. Exercise 7: Maple Programming (Again) For exercise you may continue to work with a partner. Try to use the framework in exercise 6 to write a program to decode the message you just encrypted. Open a new page in Maple for this program. Major differences: Need private key. Starting with blocks of size 3. Converting blocks of size 3 to base 10 Converting decrypted values to blocks of size 2 in base 30 Ending with blocks of size 2