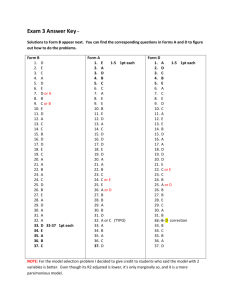
2 pt - Karlstads universitet
advertisement

Karlstads universitet
HT-08
Datavetenskap
Exam for Computer Security DVG C04, 7,5hp, 2009-01-12 kl 8:15 - 13:15
Responsible teachers: Hans Hedbom, Leonardo Martucci and Simone Fischer-Hübner
Aids allowed: none.
Maximum number of points: 60. For grade 3 30-39 p are required, for grade 4 40-49 p
are required and for grade 5 at least 50 p are required. The results are published within 3
weeks after the exam.
1)
Introduction (2 pts)
a) Name 3 basic security services (0.3 pt) and explain their meaning (0.6 pt).
b) Where do threats come from (0.3 pt)? Threats are usually classified in 3 groups;
name those groups (0.3 pt).
c) What are vulnerabilities? (0.5 pt)
2) Evaluation Criteria (2 pt)
Provide 4 different reasons for the need of security evaluation criteria (2.0pt)
3) Message Authentication Code(2 pt)
a) MAC is the acronym for Message Authentication Code. What is the purpose of a
MAC? (0.5 pt)
b) Assuming the following scenario: a message M needs to be sent from A to B.
Public keys PA and PB are known by all communicating parties. The message M
is to be encrypted with secret key K that is chosen by A. A hash function H is
known by both parties. Draw a diagram that illustrates how is the message sent
from A to B in a secure way, i.e., that prevents an attacker E to read or modify M.
(1.5 pts)
4) Buffer Overflow Attacks (6 pt)
a) What is a buffer overflow attack? (0.5 pt)
b) What are the 3 main requirements to deploy a buffer overflow attack? (1.5 pts)
c) There are 3 possible strategies to deal with buffer overflows: fixing the code,
conceding the overflow or using runtime techniques. What type of protection is
used when the overflow is conceded? Explain the technique. (1.0 pt)
d) What is a “return-to-libc” attack? (1.0 pt) This attack is used to bypass which type
of buffer overflow protection? (0.5 pt)
e) What type of protection is used against a “return-to-libc attack”? (0.5 pt) Explain
how does it work (1.0)?
DVGC01
-1-
Karlstads universitet
HT-08
Datavetenskap
Exam for Computer Security DVG C04, 7,5hp, 2009-01-12 kl 8:15 - 13:15
5) Race Condition (2 pt)
Explain what a race condition is and why does race conditions happen? (2.0 pts)
6) Pseudo Random Number Generators (2 pt)
a) Draw a diagram representing a general PRNG, illustrating the inputs and outputs
(i.e. assume that the PRNG algorithm is a block – the internals of this block are
not of particular interest for answering this question). (0.5 pt)
b) Explain why seeds have to be carefully selected. (0.5 pt). Name 2 possible
practical sources for obtaining a good seed? (0.5 pt)
c) What type of tests is used to verify if the output of a PRNG is apparently random?
(note that you don’t need to name any test suite, but just answer what type of test
is used in those suites). (0.5 pt)
7) IEEE 802.11 Network Security (4.5 pt)
a) What are the risks in IEEE 802.11 networks? Name 3 sources of those risks. (1 pt)
b) The IEEE 802.11 standard defines security mechanisms that are applied which
layer (according to the TCP/IP network model)? (0.5 pt)
c) The WPA (Wi-Fi Protected Access) specifies 2 authentication modes, the SoHo
(small office, home office) mode and the enterprise mode. Explain how does the
SoHo mode work? (0.5pt). What are the main the main components used in the
enterprise mode (0.5 pt) Explain how does the enterprise mode work (1.0 pt).
d) What does the RSNA (Robust Secure Network Association) of the IEEE 802.11
standard define? Name 4 items (1.0 pt)
8) GPG Keys (2 pt* bonus)
Have you send an encrypted email to your teacher and published your public key into
a repository? Answer yes or no.
9)
Operating system security (5pt)
a) In Linux PAM might be used in the authentication process. What is PAM?
Describe how PAM is structured and explain broadly how it works. (3p)
b) Windows uses ACL to handle access control to files while standard Linux uses
another mechanism. Describe and compare the two mechanisms.(2p)
DVGC01
-2-
Karlstads universitet
HT-08
Datavetenskap
Exam for Computer Security DVG C04, 7,5hp, 2009-01-12 kl 8:15 - 13:15
10) Authentication (5pt).
a) Describe and explain the relation between access control and authentication.
b) In connection with Authentication the terms Claim and Credential is used explain
these terms and give examples.
c) In the course we have discussed Biometrics. What is a biometric? Biometrics can
be divided into two broad categories. Which are these and what characterize
biometrics belonging to the different categories. What are the pros and cons of
using biometrics?
11) Firewalls (4.5pt)
a) Describe the firewall architecture known as screened subnet and explain how it
works. (1.5p)
b) One of the transport protocols are a bit tricky to handle in Firewall rules. Which
transport protocol is it and why is it tricky? What is required to reliably filter
it?(3p)
12) Malicious code (5pt)
a) What is the difference between a virus, a worm and a Trojan Horse? Explain how
they work.(2 pt)
b) What do we mean by a Blended threat? Give an example of a Trojan horse.(1pt)
c) Explain broadly how 4:th generation virus protection works.(2pt)
13) Security Models & Access Control (6pt)
a) What kind of access can a process with the current security level (secret, {NATO,
CRYPTO}) have to documents classified in each of the following ways under the
Bell LaPadula Model (2pt):
1. (unclassified, { })
2. (unclassified, {CRYPTO, NUCLEAR})
3. (top secret, {NATO, NUCLEAR})
4. (top secret, {NUCLEAR, CRYPTO, NATO})
b) Describe the difference between discretionary access control (DAC) and
mandatory access control (MAC). How can DAC be compromised by a Trojan
Horse?(2pt)
c) What is XACML? What are the XACML components and how do they work
together to decide about access control requests?(2pt)
DVGC01
-3-
Karlstads universitet
HT-08
Datavetenskap
Exam for Computer Security DVG C04, 7,5hp, 2009-01-12 kl 8:15 - 13:15
14) Database Security (7pt)
a) What is polyinstantiation and how does it arise ? Give an example (3pt).
b) What is the difference between a general and an individual tracker attack to a
statistical database (1pt)?
c) Consider the statistical database with N = 14 students
Name
Sex
Major
Class
Course
Grade
Annicka
Female
CS
2001
2
Katrin
Female
Bio
2001
5
Jonas
Male
Bio
1999
3
Anette
Female
CS
1999
4
Johannes
Male
EE
2000
2
Per
Male
Bio
2002
4
Alfredo
Male
CS
2000
2
Lotta
Female
Psy
1999
5
Rickard
Male
CS
2001
4
Anna
Female
EE
1999
3
Helena
Female
Psy
2001
5
Peter
Male
Bio
1998
2
Paul
Male
CS
1999
5
Marianne
Female
CS
1997
5
Show how Annicka’s course grade can be compromised under a query-set-size restriction
of n=2 using
a. an individual tracker attack (1pt)
b. l a general tracker attack (1pt)
d) What are technical means to protect against tracker attacks? (1pt)
15) Legal Aspects (privacy) (4pt)
a) Explain the “purpose binding” and the “data minimization” privacy principles and
explain why they are important.(2pt)
b) Discuss privacy risks of RFID applications (2pt)
16) Intrusion Detection (IDS) (3pt)
a) What is the difference between Misuse Detection and Anomaly Detection? What
are the pros and cons of both IDS methods?(2pt)
b) Give an example how Misuse and Anomaly detection would be used to detect
computer viruses or buffer overflow attacks. (1pt)
DVGC01
-4-