ABSTRACT
advertisement

ZIGBEE BASED WIRELESS WEATHER STATION
CHAPTER 1
In an industry during certain hazards is will be very difficult to monitor the
parameter through wires and analog devices such as transducers. To over come this
problem we use wireless device to monitor the parameters so that we can take certain
steps even in worst case. Few years back the use of wireless device was very less,
but due the rapid development is technology now a days we use maximum of our
data transfer through wireless like wi-fi,Bluetooth,wi max,etc.
In view of all this things, the design of wireless parameter progress helps in an
industry to monitor the parameter in real time with the use of zigbee, is an easy
installation platform, cost effective method for the low bit rate transmission, so with
the help of the ready zigbee platform by using the embedded c language we interface
the module with the pc by the help of visual basic we monitor the parameters in the
system.
The main use of this module helps in an industry during the worst cases as the
analog device may be damaged may be during the fire accidents,etc.But with the
wireless transmission we have not have an accurate data but when compared to the
analog failure the errors are very minimum so we use wireless to monitor the
parameter in an industry where their no means of human interface to monitor the
parameters
In this project we deal to monitor the parameter through wireless by using
zigbee ready platform which is based on the IEEE 802.15.4, 2.4 GHz, in this module
we use msp 430 for the voltage and other technical parameters, which has in build
RAM in it. The working of this module is simple in principle, the changes in certain
place is monitor in real time process which is very accurate in monitoring and their no
other interface and other disturbance in monitoring the parameter in this project we
monitor temperature and humidity with the help of respective sensors. The change in
the room temperature, humidity can be monitored like real time as the change is
displayed in respective interval in the visual basic screen.
This means of wireless end device is used to monitor the weather parameters
in an industry, which helps to monitor and have a clear thing to monitor it. The
1
sensors used in this module to monitor are Temperature sensor, humidity and rain fall
sensors Aare used.
MSP 430 used in the module of contains inbuilt RAM and flash memory and
also Zigbee module contains A/D converter, transmitter also.so, this can be widely
used for home automation, industrial application which helps for an easy wireless
communication for a low data rate transmission. In this following chapter we discuss
with zigbee and its importance and how it is used for the monitoring the parameters.
1.2 ZIGBEE:
ZigBee is the name of a specification for a suite of high level communication
protocols using small, low-power digital radios based on the IEEE 802.15.4 standard
for wireless personal area networks (WPANs), such as wireless headphones
connecting with cell phones via short-range radio. The technology is intended to be
simpler and cheaper than other WPANs, such as Bluetooth. ZigBee is targeted at
radio-frequency (RF) applications which require a low data rate, long battery life, and
secure networking
1.3
OVERVIEW:
ZigBee builds upon the physical layer and medium access control defined in
IEEE standard 802.15.4 (2003 version) for low-rate WPAN's. The specification goes
on to complete the standard by adding four main components: network layer,
application layer, ZigBee device objects (ZDO's) and manufacturer-defined
application objects which allow for customization and favor total integration.
Besides adding two high-level network layers to the underlying structure, the
most significant improvement is the introduction of ZDO's. These are responsible for a
number of tasks, which include keeping of device roles, management of requests to
join a network, device discovery and security.
2
(Fig 1:zigbee specifications)
At its core, ZigBee is a mesh network architecture. Its network layer natively supports
three types of topologies: both star and tree typical networks and generic mesh
networks. Every network must have one coordinator device, tasked with its creation,
the control of its parameters and basic maintenance. Within star networks, the
coordinator must be the central node. Both trees and meshes allow the use of ZigBee
routers to extend communication at the network level (they are not ZigBee
coordinators, but may act as 802.15.4 coordinators within their personal operating
space), but they differ in a few important details: communication within trees is
hierarchical and optionally utilizes frame beacons, whereas meshes allow generic
communication structures but no router beaconing.
The relationship between IEEE 802.15.4-2003 and ZigBee is similar to that
between IEEE 802.11 and the Wi-Fi Alliance. The ZigBee 1.0 specification was
ratified on December 14, 2004 and is available to members of the ZigBee Alliance. An
entry level membership called Adopter, in the ZigBee Alliance costs US$3500
annually and provides access to the specifications and permission to create products
for market using the specifications. For non-commercial purposes, the ZigBee
specification is available to the general public at the ZigBee Specification Download
Request. Most recently, the ZigBee 2006 specification was posted in December 2006.
3
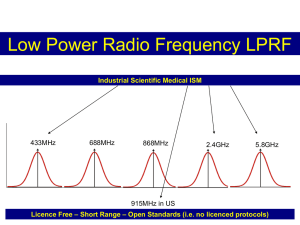
ZigBee operates in the industrial, scientific and medical (ISM) radio bands; 868
MHz in Europe, 915 MHz in countries such as USA and Australia, and 2.4 GHz in
most jurisdictions worldwide. The technology is intended to be simpler and cheaper
than other WPANs such as Bluetooth. The most capable ZigBee node type is said to
require only about 10% of the software of a typical Bluetooth or Wireless Internet
node, while the simplest nodes are about 2% However, actual code sizes are much
higher, closer to 50% of Bluetooth code size ZigBee chip vendors have announced
128-kilobyte devices.
As of 2006, the retail price of a Zigbee-compliant transceiver is approaching
$1, and the price for one radio, processor, and memory package is about $3.
Comparatively, before Bluetooth was launched (1998) it had a projected price, in high
volumes, of $4 - $6; the price of consumer-grade Bluetooth chips is now under $3.
First stack release is now called "Zigbee 2004". The 2nd stack release is called
2006, and mainly replaces the MSG/KVP structure used in 2004 with a "cluster
library". The 2004 stack is now more or less obsolete. The ZigBee Alliance has
started work on ZigBee 2007, looking to extend the ZigBee 2006 specification
capabilities; the main enhancements are optimizing certain network level functionality
(such as data aggregation). There are also some new application profiles like
Automatic Meter Reading, Commercial building automation and home automation
based on the "cluster library principle".
Zigbee 2007, now the current stack release, is sometimes called "Pro", but pro
is a stack profile, which defines certain stack settings and mandatory features.
ZigBee 2007 at the network level is not backwards-compatible with ZigBee
2004/2006, although a ZigBee 2004/2006 RFD node can join a 2007 network, and
vice-versa. It's not possible to mix 2004/2006 routers with 2007 routers/coordinator.
1.4
NETWORK LAYERS:
The main functions of the network layer are to enable the correct use of the
MAC sublayer and provide a suitable interface for use by the next upper layer, namely
4
the application layer. Its capabilities and structure are those typically associated to
such network layers, including routing.
On the one hand, the data entity creates and manages network layer data units from
the payload of the application layer and performs routing according to the current
topology. On the other hand, there is the layer control, which is used to handle
configuration of new devices and establish new networks: it can determine whether a
neighboring device belongs to the network and discovers new neighbors and routers.
The control can also detect the presence of a receiver, which allows direct
communication and MAC synchronization.
1.5
APPLICATION LAYER:
The application layer is the highest-level layer defined by the specification, and is
the effective interface of the ZigBee system to its end users. It comprises the majority
of components added by the ZigBee specification: both ZDO and its management
procedures, together with application objects defined by the manufacturer, are
considered part of this layer.
1.5.1 Main Components:
The ZDO is responsible for defining the role of a device as either coordinator or
end device, as mentioned above, but also for the discovery of new (one-hop) devices
on the network and the identification of their offered services. It may then go on to
establish secure links with external devices and reply to binding requests accordingly.
The application support sublayer (APS) is the other main standard component
of the layer, and as such it offers a well-defined interface and control services. It
works as a bridge between the network layer and the other components of the
application layer: it keeps up-to-date binding tables in the form of a database, which
can be used to find appropriate devices depending on the services that are needed
and those the different devices offer. As the union between both specified layers, it
also routes messages across the layers of the protocol stack.
5
1.5.2 Communication models:
An application may consist of communicating objects which cooperate to carry
out the desired tasks. The focus of ZigBee is to distribute work among many different
devices which reside within individual ZigBee nodes which in turn form a network
(said work will typically be largely local to each device, for instance the control of each
individual household appliance).
The collections of objects that form the network communicate using the
facilities provided by APS, supervised by ZDO interfaces. The application layer data
service follows a typical request-confirm/indication-response structure. Within a single
device, up to 240 application objects can exist, numbered in the range 1-240. 0 is
reserved for the ZDO data interface and 255 for broadcast; the 241-254 range is not
currently in use but may be in the future.
(Fig 2 :ZigBee high-level communication model)
There are two services available for application objects to use (in ZigBee 1.0):
i)the key-value pair service (KPV) is meant for configuration purposes. It enables
description, request and modification of object attributes through a simple interface
based on get/set and event primitives, some allowing a request for response.
Configuration uses compressed XML (full XML can be used) to provide an adaptable
and elegant solution.
6
ii)the message service is designed to offer a general approach to information
treatment, avoiding the necessity to adapt application protocols and potential
overhead incurred on by KPV. It allows arbitrary payloads to be transmitted over APS
frames.
Addressing is also part of the application layer. A network node consists of an
802.15.4-conformant radio transceiver and one or more device descriptions (basically
collections of attributes which can be polled or set, or which can be monitored through
events). The transceiver is the base for addressing, and devices within a node are
specified by an endpoint identifier in the range 1-240.
1.5.3 Communication and device Discovery:
In order for applications to communicate, their comprising devices must use a
common application protocol (types of messages, formats and so on); these sets of
conventions are grouped in profiles. Furthermore, binding is decided upon by
matching input and output cluster identifiers, unique within the context of a given
profile and associated to an incoming our outgoing data flow in a device. Binding
tables contain source and destination pairs.
Depending on the available information, device discovery may follow different
methods. When the network address is known, the IEEE address can be requested
using unicast communication. When it is not, petitions are broadcast (the IEEE
address being part of the response payload). End devices will simply respond with the
requested address, while a network coordinator or a router will also send the
addresses of all the devices associated with it.
This extended discovery protocol permits external devices to find out about
devices in a network and the services that they offer, which endpoints can report
when queried by the discovering device (which has previously obtained their
addresses). Matching services can also be used.
7
The use of cluster identifiers enforces the binding of complementary entities by
means of the binding tables, which are maintained by ZigBee coordinators, as the
table must be always available within a network and coordinators are most likely to
have a permanent power supply; backups may be needed by some applications,
whose
higher-level
layers
must
manage.
Binding
requires
an
established
communication link; after it exists, whether to add a new node to the network is
decided, according to the application and security policies.Communication can
happen right after the association. Direct addressing uses both radio address and
endpoint identifier, whereas indirect addressing requires every relevant field (address,
endpoint, cluster and attribute) and sends it to the network coordinator, which
maintains these associations and translates requests for communication. Indirect
addressing is particularly useful to keep some devices very simple and minimize their
need for storage. Besides these two methods, broadcast to all endpoints in a device
is available, and group addressing is used to communicate with groups of endpoints
belonging to a set of devices.
1.6 SECURITY SERVICES:
As one of its defining features, ZigBee provides facilities for carrying out secure
communications, protecting establishment and transport of cryptographic keys,
cyphering frames and controlling devices. It builds on the basic security framework
defined in IEEE 802.15.4. This part of the architecture relies on the correct
management of symmetric keys and the correct implementation of methods and
security policies.
1.6.1 Basic security model:
The basic mechanism to ensure confidentiality is the adequate protection of all
keying material. Trust must be assumed in the initial installation of the keys, as well
as in the processing of security information. In order for an implementation to globally
work, its general correctness (e.g., conformance to specified behaviors) is assumed.
Keys are the cornerstone of the security architecture; as such their protection
is of paramount importance, and keys are never supposed to be transported through
8
an insecure channel. There is a momentary exception to this rule, which occurs
during the initial phase of the addition to the network of a previously unconfigured
device. The ZigBee network model must take particular care of security
considerations, as ad hoc networks may be physically accessible to external devices
and the particular working environment cannot be foretold; likewise, different
applications running concurrently and using the same transceiver to communicate are
supposed to be mutually trustworthy: for cost reasons the model does not assume a
firewall exists between application-level entities.
Within the protocol stack, different network layers are not cryptographically separated,
so access policies are needed and correct design assumed. The open trust model
within a device allows for key sharing, which notably decreases potential cost.
Nevertheless, the layer which creates a frame is responsible for its security. If
malicious devices may exist, every network layer payload must be cyphered, so
unauthorized traffic can be immediately cut off. The exception, again, is the
transmission of the network key, which confers a unified security layer to the network,
to a new connecting device. Point-to-point encryption is also supported.
1.6.2 Security architecture:
ZigBee uses 128-bit keys to implement its security mechanisms. A key can be
associated either to a network, being usable by both ZigBee layers and the MAC
sublayer, or to a link, acquired through preinstallation, agreement or transport.
Establishment of link keys is based on a master key which controls link key
correspondence. Ultimately, at least the initial master key must be obtained through a
secure medium (transport or preinstallation), as the security of the whole network
depends on it. Link and master keys are only visible to the application layer. Different
services use different one-way variations of the link key in order to avoid leaks and
security risks.
Key distribution is one of the most important security functions of the network.
A secure network will designate one special device which other devices trust for the
distribution of security keys: the trust center. Ideally, devices will have the trust center
address and initial master key preloaded; if a momentary vulnerability is allowed, it
9
will be sent as described above. Typical applications without special security needs
will use a network key provided by the trust center (through the initially insecure
channel) to communicate.
Thus, the trust center maintains both the network key and provides point-to-point
security. Devices will only accept communications originating from a key provided by
the trust center, except for the initial master key. The security architecture is
distributed among the network layers as follows:
The MAC sublayer is capable of single-hop reliable communications. As a rule, the
security level it is to use is specified by the upper layers.
The network layer manages routing, processing received messages and being
capable of broadcasting requests. Outgoing frames will use the adequate link key
according to the routing, if it is available; otherwise, the network key will be used to
protect the payload from external devices.
The application layer offers key establishment and transport services to both ZDO
and applications. It is also responsible for the propagation across the network of
changes in devices within it, which may originate in the devices themselves (for
instance, a simple status change) or in the trust manager (which may inform the
network that a certain device is to be eliminated from it). It also routes requests from
devices to the trust center and network key renewals from the trust center to all
devices. Besides this, the ZDO maintains the security policies of the device.
1.7 PROTOCOLS:
The protocols build on recent algorithmic research (Ad-hoc On-demand
Distance Vector, neuRFon) to automatically construct a low-speed ad-hoc network of
nodes. In most large network instances, the network will be a cluster of clusters. It can
also form a mesh or a single cluster. The current profiles derived from the ZigBee
protocols support beacon and non-beacon enabled networks.
In non-beacon-enabled networks (those whose beacon order is 15), an
unslotted CSMA/CA channel access mechanism is used. In this type of network,
ZigBee Routers typically have their receivers continuously active, requiring a more
robust power supply. However, this allows for heterogeneous networks in which some
10
devices receive continuously, while others only transmit when an external stimulus is
detected. The typical example of a heterogeneous network is a wireless light switch:
the ZigBee node at the lamp may receive constantly, since it is connected to the
mains supply, while a battery-powered light switch would remain asleep until the
switch is thrown. The switch then wakes up, sends a command to the lamp, receives
an acknowledgment, and returns to sleep. In such a network the lamp node will be at
least a ZigBee Router, if not the ZigBee Coordinator; the switch node is typically a
ZigBee End Device.
In beacon-enabled networks, the special network nodes called ZigBee Routers
transmit periodic beacons to confirm their presence to other network nodes. Nodes
may sleep between beacons, thus lowering their duty cycle and extending their
battery life. Beacon intervals may range from 15.36 milliseconds to 15.36 ms * 214 =
251.65824 seconds at 250 kbit/s, from 24 milliseconds to 24 ms * 214 = 393.216
seconds at 40 kbit/s and from 48 milliseconds to 48 ms * 214 = 786.432 seconds at
20 kbit/s. However, low duty cycle operation with long beacon intervals requires
precise timing which can conflict with the need for low product cost.
In general, the ZigBee protocols minimize the time the radio is on so as to
reduce power use. In beaconing networks, nodes only need to be active while a
beacon is being transmitted. In non-beacon-enabled networks, power consumption is
decidedly asymmetrical: some devices are always active, while others spend most of
their time sleeping.
ZigBee devices are required to conform to the IEEE 802.15.4-2003 Low-Rate
Wireless Personal Area Network (WPAN) standard. The standard specifies the lower
protocol layers—the physical layer (PHY), and the medium access control (MAC)
portion of the data link layer (DLL). This standard specifies operation in the
unlicensed 2.4 GHz, 915 MHz and 868 MHz ISM bands. In the 2.4 GHz band there
are 16 ZigBee channels, with each channel requiring 5 MHz of bandwidth. The center
frequency for each channel can be calculated as, FC = (2405 + 5*(k-11)) MHz, where
k = 11, 12, ..., 26.
The radios use direct-sequence spread spectrum coding, which is managed by
the digital stream into the modulator. BPSK is used in the 868 and 915 MHz bands,
and orthogonal QPSK that transmits two bits per symbol is used in the 2.4 GHz band.
11
The raw, over-the-air data rate is 250 kbit/s per channel in the 2.4 GHz band, 40 kbit/s
per channel in the 915 MHz band, and 20 kbit/s in the 868 MHz band. Transmission
range is between 10 and 75 meters (33 and 246 feet), although it is heavily
dependent on the particular environment. The maximum output power of the radios is
generally 0 dBm (1 mW).
The basic channel access mode specified by IEEE 802.15.4-2003 is "carrier
sense, multiple access/collision avoidance" (CSMA/CA). That is, the nodes talk in the
same way that people converse; they briefly check to see that no one is talking before
they start. There are three notable exceptions to the use of CSMA. Beacons are sent
on a fixed timing schedule, and do not use CSMA. Message acknowledgements also
do not use CSMA. Finally, devices in Beacon Oriented networks that have low latency
real-time requirements may also use Guaranteed Time Slots (GTS) which by
definition does not use CSMA.
1.8 NODE TYPES:
This page describes the types of node that are used in a ZigBee network.
Reference will be made to the toplogies introduced on the previous page (Star, Tree,
Mesh), but these topologies will be described in more detail later in this module.
The ZigBee standard has the capacity to address up to 65535 nodes in a single
network. However, there are only three general types of node:
Co-ordinator
End Device
Router
These roles described below exist at the network level – a ZigBee node may also be
performing tasks at the application level independent of the role it plays in the
network. For instance, a network of ZigBee devices measuring temperature may have
a temperature sensor application in each node, irrespective of whether they are End
Devices, Routers or the Co-ordinator.
These node types are described below.
12
1.8.1 ZigBee coordinator(ZC): The most capable device, the coordinator forms the
root of the network tree and might bridge to other networks. There is exactly one
ZigBee coordinator in each network since it is the device that started the network
originally. It is able to store information about the network, including acting as the
Trust Centre & repository for security keys.
All ZigBee networks must have one (and only one) Co-ordinator, irrespective of the
network topology.
In the Star topology, the Co-ordinator is the central node in the network.
In the Tree and Mesh topologies, the Co-ordinator is the top (root) node in the
network.
This is illustrated below, where the Co-ordinator is colour-coded in dark black.
At the network level, the Co-ordinator is mainly needed at system initialisation. The
tasks of the Co-ordinator at the network layer are:
Selects the frequency channel to be used by the network (usually the one with
the least detected activity)
Starts the network
Allows other devices to connect to it (that is, to join the network)
The Co-ordinator can also provide message routing (for example, in a Star network),
security management and other services.
13
In some circumstances, the network will be able to operate normally if the Coordinator fails or is switched off. This will not be the case if the Co-coordinator
provides a routing path through the network (for instance, in a Star topology, where it
is needed to relay messages). Similarly the Co-ordinator provides services at the
Application layer and if these services are being used (for example, Co-ordinator
binding), the Co-ordinator must be able to provide them at all times.
1.8.2 ZigBee Router (ZR): As well as running an application function a router can act
as an intermediate router, passing data from other devices.
Networks with Tree or Mesh topologies need at least one Router. The main tasks of a
Router are:
Relays messages from one node to another
Allows child nodes to connect to it
In a Star topology, these functions are handled by the Co-ordinator and, therefore, a
Star network does not need Routers.
In Tree and Mesh topologies, Routers are located as follows:
In a Tree topology, Routers are normally located in network positions that allow
messages to be passed up and down the tree.
In a Mesh topology, a Router can be located anywhere that a message
passing node is required.
However, in all topologies (Star, Tree and Mesh), Router devices can be located at
the extremities of the network, if they run applications that are needed in these
locations - in this case, the Router will not perform its message relay function, unless
in a Mesh network (see above).
The possible positions of Routers in the different network topologies are illustrated
below, where the Routers are color-coded in red:
14
1.8.3 ZigBee End Device (ZED): Contains just enough functionality to talk to the
parent node (either the coordinator or a router); it cannot relay data from other
devices. This relationship allows the node to be asleep a significant amount of the
time thereby giving long battery life. A ZED requires the least amount of memory, and
therefore can be less expensive to manufacture than a ZR or ZC.
End Devices are always located at the extremities of a network:
In the Star topology, they are perimeter nodes
In the Tree and Mesh topologies, they are leaf nodes
This is illustrated below, where the End Devices are color-coded in light blue.
The main tasks of an End Device at the network level are sending and receiving
messages. Note that End Devices cannot relay messages and cannot allow other
nodes to connect to the network through them.
An End Device can often be battery-powered and, when not transmitting or receiving,
can sleep in order to conserve power.
15
1.9 SOFTWARE AND HARDWARE:
The software is designed to be easy to develop on small, cheap
microprocessors. The radio design used by ZigBee has been carefully optimized for
low cost in large scale production. It has few analog stages and uses digital circuits
wherever possible.
Even though the radios themselves are cheap, the ZigBee Qualification Process
involves a full validation of the requirements of the physical layer. This amount of
concern about the Physical Layer has multiple benefits, since all radios derived from
that semiconductor mask set would enjoy the same RF characteristics. On the other
hand, an uncertified physical layer that malfunctions could cripple the battery lifespan
of other devices on a ZigBee network. Where other protocols can mask poor
sensitivity or other esoteric problems in a fade compensation response, ZigBee radios
have very tight engineering constraints: they are both power and bandwidth
constrained. Thus, radios are tested to the ISO 17025 standard with guidance given
by Clause 6 of the 802.15.4-2003 Standard. Most vendors plan to integrate the radio
and microcontroller onto a single chip.
1.10 USES:
ZigBee protocols are intended for use in embedded applications requiring low
data rates and low power consumption. ZigBee's current focus is to define a generalpurpose, inexpensive, self-organizing mesh network that can be used for industrial
control, embedded sensing, medical data collection, smoke and intruder warning,
building automation, home automation, etc. The resulting network will use very small
amounts of power so individual devices might run for a year or two using the originally
installed battery.
Typical application areas include:
• Home Entertainment and Control - Smart Lighting, Advanced Temperature Control,
Safety & Security and Movies & Music
• Home Awareness - Water Sensors, Power Sensors, Smart Appliances and Access
sensors
16
• Mobile Services – m-payment, m-monitoring and control, m-security and access
control, m- healthcare and tele-assist
• Commercial Building– Energy Monitoring, HVAC, Lighting, Access Control
• Industrial Plant– Process Control, Asset Management, Environmental management,
Energy Management
17
CHAPTER 2
CIRCUIT DESIGN
2.1 INTRODUCTION:
This chapter mainly deals with the circuit and the requirements of the project.
Chipcon cc2420 is a basic device needed for transmit and receive the data from the
remote device with the help of computer the display of the report is done. The
transmission and receive of signal is done in the standard form of IEE
802.15.4,2.4Ghz.The program for this device is done my using msp430,this
transmitting device is interfaced with the microcontroller as it is connect to analog to
digital converters which has the digital converted signals. Now when the data to be
fed to computer is available an input port is needed, through which interfacing is
done. In this system, for interfacing com port is used as it is an inexpensive platform
for implementing low-frequency data acquisition projects. By using the visual basic
the embedding is done.
2.2 BLOCK DIAGRAM OF SENSOR CIRCUIT:
HUMIDITY
SENSOR
TEMP
SENSOR
A/D
CONVERTER
MICROCONTROLLER
MAX 232
RAIN
SENSOR
(Fig 3a: Block diagram of sensor circuit)
18
RS
232
CIRCUIT DIAGRAM:
(Fig 3 : Circuit diagram of sensor circuit)
(Fig 4: Basic model of Zigbee )
19
2.2.1 Power Supply:
This circuit IC voltage regulator as the power source. IC voltage regulators are
versatile and inexpensive and are available with features such as a programmable
output, current-voltage boosting, internal short-circuit current limiting, thermal
shutdown and floating operation for high voltage application
Regulator IC units contain the circuitry for reference source, comparator
amplifier, control devices and overload protection all in a single unit. In this circuit,
three-terminal IC voltage regulator 7805 is employed. 7805 is a fixed positive voltage
regulator whose nominal voltage output is +5v. This IC are designed with adequate
heat sinking, can deliver output currents in excess of 1A.
2.2.2 Controller circuit:
The controller used in this module is 89C52 micro-controller this used
manipulated the data accessed from the ADC converters. This micro controller linked
to the conversion circuit which contains analog sensors. This is used to for the sensor
circuit and the program for this is written I Kiel software which is then integrated by
the module.
2.2.3 Sensors:
The sensors used for the weather parameters are Lm35 for the temperature
sensing,HIH3160 series is used and a short circuit is used for the rain fall sensing is
used. The data form this is transmitted through the ADC conversion circuit where the
analog data from the parameter transducers are changed to digital form by the circuit
used.
2.2.4 Transmission circuit:
The transmission of data is done in the zigbee module on the basis of IEEE
802.15.4/2.4 GHz standard. this is integrated in the chipcon CC22420.The
transmission of data data is done in encapsulation methods like it gathers the data
and send to the receivers end at a time like a single data packet so that it can send as
many possible data packets in a minute and also the data is not lost in the
transmission .
20
2.2.5 Conversion Circuit:
The output of sample and hold is fed ADC for conversion into digital format. In
this case ADC0804 is employed for conversion of the sampled input signal into 8-bit
digital output. The ADC0804 is compatible with microprocessors. It is a 20-pin IC that
works with 5V supply. It converts the analog input voltage to 8-bit digital output. The
data bus is tri-state buffered. With eight bit, the resolution is 5V/255=19.6mv.
The in built clock generator circuit produces a frequency of about 640 KHz with
R1=10 kilo ohms and c4=150 pf, which are the externally connected timing
components. The conversion time obtained is approximately 100 us.
21
CHAPTER 3
DESCRIPTION OF CIRCUIT COMPONENTS
3.1 CC2420 2.4GHz IEEE802.15.4/ZIGBEE-READY RF TRANSCEIVER
3.1.2 Product Description:
The CC2420 is a true single-chip 2.4 GHz IEEE 802.15.4 compliant RF
transceiver designed for low-power and low-voltage wireless applications. CC2420
includes a digital direct sequence spread spectrum baseband modem providing a
spreading gain of 9 dB and an effective data rate of 250 kbps.
The CC2420 is a low-cost, highly integrated solution for robust wireless
communication in the 2.4 GHz unlicensed ISM band. It complies with worldwide
regulations covered by ETSI EN 300 328 and EN 300 440 class 2 (Europe), FCC
CFR47 Part 15 (US) and ARIB STD-T66 (Japan).
The CC2420 provides extensive hardware support for packet handling, data buffering,
burst transmissions, data encryption, data authentication, clear channel assessment,
link quality indication and packet timing information. These features reduce the load
on the host controller and allow CC2420 to interface low-cost microcontrollers. The
configuration interface and transmit / receive FIFOs of CC2420 are accessed via an
SPI interface. In a typical application CC2420 will be used together with a
microcontroller and a few external passive components. CC2420 is based on
Chipcon’s SmartRF®-03 technology in 0.18 µm CMOS.
3.1.2 Features:
2400 – 2483.5 MHz RF Transceiver
• Direct Sequence Spread Spectrum (DSSS) transceiver
• 250 kbps data rate, 2 MChip/s chip rate
• O-QPSK with half sine pulse shaping modulation
• Very low current consumption (RX: 19.7 mA, TX: 17.4 mA)
• High sensitivity (-94 dBm)
• High adjacent channel rejection (39 dB)
22
• High alternate channel rejection (55 dB)
• On-chip VCO, LNA and PA
• Low supply voltage (2.1 – 3.6 V) with on-chip voltage regulator
• Programmable output power
• I/Q low-IF soft decision receiver
• I/Q direct up-conversion transmitter
• Separate transmit and receive FIFOs
• 128 byte transmit data FIFO
• 128 byte receive data FIFO
• Very few external components
• Only reference crystal and a minimised number of passives
• No external filters needed
• Easy configuration interface
• 4-wire SPI interface
• Serial clock up to 10 MHz
• 802.15.4 MAC hardware support:
• Automatic preamble generator
• Synchronisation word insertion/detection
• CRC-16 computation and checking over the MAC payload
• Clear Channel Assessment
• Energy detection / digital RSSI
• Link Quality Indication
• Full automatic MAC security (CTR, CBC-MAC, CCM)
• 802.15.4 MAC hardware security:
• Automated security operations within the receive and transmit FIFOs.
• CTR mode encryption / decryption
• CBC-MAC authentication
• CCM encryption / decryption and authentication
• Stand-alone AES encryption
• Development tools available
• Fully equipped development kit
• Demonstration board reference design with microcontroller code
23
• Easy-to-use software for generating the CC2420 configu-ration data
• Small size QLP-48 package, 7 x 7 mm
3.1.3 Operating Conditions:
Parameter
Min
Supply voltage for on-chip voltage regulator,
VREG_IN pin 43.
2.1
Supply voltage (VDDIO) for digital I/Os, DVDD3.3,
pin 25 .
1.6
Supply voltage (VDD) on AVDD_VCO, DVDD1.8,
etc (pin no 1, 2, 3, 4, 10, 14, 15, 17, 18, 20, 26, 35,
37, 44 and 48)
1.6
Operating ambient temperature range
−40
Typ.
Max.
Units
3.6
3.6
1.8
2.0
85
3.1.4 Pin Assignment:
(Fig 5 : Pin assignment of cc2420)
24
Condition
V
V
The digital I/O voltage (DVDD3.3 pin)
must match the external interfacing
circuit (e.g. microcontroller).
V
The typical application uses regulated
1.8 V supply generated by the on-chip
voltage regulator.
°C
Pin Pin Name
Pin type
Pin Description
-
Ground
Exposed die attach pad. Must be connected to
(analog)
solid ground plane
Power
Connection of guard ring for VCO (to AVDD)
(analog)
shielding
Power
1.8 V Power supply for VCO
1
2
AGND
VCO_GUARD
AVDD_VCO
(analog)
3
AVDD_PRE
Power
1.8 V Power supply for Prescaler
(analog)
4
AVDD_RF1
Power
1.8 V Power supply for RF front-end
(analog)
5
GND
Ground
Grounded pin for RF shielding
(analog)
6
RF_P
RF I/O
Positive RF input/output signal to LNA/from PA
in receive/transmit mode
7
TXRX_SWITCH
Power
Common supply connection for integrated RF
(analog)
front-end. Must be connected to RF_P and
RF_N externally through a DC path
8
RF_N
RF I/O
Negative RF input/output signal to LNA/from
PA in receive/transmit mode
9
GND
Ground
Grounded pin for RF shielding
(analog)
10
AVDD_SW
Power
1.8 V Power supply for LNA / PA switch
(analog)
11
NC
-
Not Connect
12
NC
-
Not Connect
13
NC
-
Not Connect
14
AVDD_RF2
Power
1.8 V Power supply for receive and transmit
(analog)
mixers
Power
1.8 V Power supply for transmit / receive IF
(analog)
chain
-
Not Connect
15
16
AVDD_IF2
NC
25
17
18
19
AVDD_ADC
DVDD_ADC
DGND_GUARD
Power
1.8 V Power supply for analog parts of ADCs
(analog)
and DACs
Power
1.8 V Power supply for digital parts of receive
(digital)
ADCs
Ground
Ground connection for digital noise isolation
(digital)
20
DGUARD
Power
1.8 V Power supply connection for digital noise
(digital)
isolation
21
RESETn
Digital Input
Asynchronous, active low digital reset
22
DGND
Ground
Ground connection for digital core and pads
(digital)
23
DSUB_PADS
Ground
Substrate connection for digital pads
(digital)
24
DSUB_CORE
Ground
Substrate connection for digital modules
(digital)
25
DVDD3.3
Power
3.3 V Power supply for digital I/Os
(digital)
26
DVDD1.8
Power
1.8 V Power supply for digital core
(digital)
27
28
29
30
SFD
CCA
FIFOP
FIFO
Digital
SFD (Start of Frame Delimiter) / digital mux
output
output
Digital
CCA (Clear Channel Assessment) / digital mux
output
output
Digital
High when number of bytes in FIFO exceeds
output
threshold / serial RF clock output in test mode
Digital I/O
High when data in FIFO / serial RF data input /
output in test mode
31
CSn
Digital input
SPI Chip select, active low
32
SCLK
Digital input
SPI Clock input, up to 10 MHz
33
SI
Digital input
SPI Slave Input. Sampled on the positive edge
of SCLK
34
SO
Digital
SPI Slave Output. Updated on the negative
26
output
edge of SCLK. Tristate when CSn high.
(tristate)
35
DVDD_RAM
Power
1.8 V Power supply for digital RAM
(digital)
36
NC
-
37
AVDD_XOSC16 Power
Not Connect
1.8 V crystal oscillator power supply
(analog)
38
XOSC16_Q2
Analog I/O
16 MHz Crystal oscillator pin 2
39
XOSC16_Q1
Analog I/O
16 MHz Crystal oscillator pin 1 or external
clock input
40
NC
-
Not Connect
41
VREG_EN
Digital input
Voltage regulator enable, active high, held at
VREG_IN voltage level when active
42
VREG_OUT
Power
Voltage regulator 1.8 V power supply output
output
43
44
45
VREG_IN
AVDD_IF1
R_BIAS
Power
Voltage regulator 2.1 to 3.6 V power supply
(analog)
input
Power
1.8 V Power supply for transmit / receive IF
(analog)
chain
Analog
External precision resistor, 43 kΩ, ± 1 %
output
46
ATEST2
Analog I/O
Analog test I/O for prototype and production
testing
47
ATEST1
Analog I/O
Analog test I/O for prototype and production
testing
48
AVDD_CHP
Power
1.8 V Power supply for phase detector and
(analog)
charge pump
27
3.1.5 Circuit Description:
(Fig 5 :A simplified block diagram of CC2420)
CC2420 features a low-IF receiver. The received RF signal is amplified by the lownoise amplifier (LNA) and down-converted in quadrature (I and Q) to the intermediate
frequency (IF). At IF (2 MHz), the complex I/Q signal is filtered and amplified, and
then digitized by the ADCs. Automatic gain control, final channel filtering, despreading, symbol correlation and byte synchronisation are performed digitally.
When the SFD pin goes high, this indicates that a start of frame delimiter has been
detected. CC2420 buffers the received data in a 128 byte receive FIFO. The user
may read the FIFO through an SPI interface. CRC is verified in hardware. RSSI and
correlation values are appended to the frame. CCA is available on a pin in receive
mode. Serial (unbuffered) data modes are also available for test purposes.
The CC2420 transmitter is based on direct up-conversion. The data is buffered in a
128 byte transmit FIFO (separate from the receive FIFO). The preamble and start of
frame delimiter are generated by hardware. Each symbol (4 bits) is spread using the
28
IEEE 802.15.4 spreading sequence to 32 chips and output to the digital-to-analog
converters (DACs).
An analog lowpass filter passes the signal to the quadrature (I and Q) upconversion
mixers. The RF signal is amplified in the power amplifier (PA) and fed to the antenna.
The internal T/R switch circuitry makes the antenna interface and matching easy. The
RF connection is differential. A balun may be used for single-ended antennas. The
biasing of the PA and LNA is done by connecting TXRX_SWITCH to RF_P and RF_N
through an external DC path.
(Fig 6: cc2420 pin connections)
The frequency synthesizer includes a completely on-chip LC VCO and a 90 degrees
phase splitter for generating the I and Q LO signals to the down-conversion mixers in
receive mode and up-conversion mixers in transmit mode. The VCO operates in the
29
frequency range 4800 – 4966 MHz, and the frequency is divided by two when split in I
and Q.
A crystal must be connected to XOSC16_Q1 and XOSC16_Q2 and provides the
reference frequency for the synthesizer. A digital lock signal is available from the PLL.
The digital baseband includes support for frame handling, address recognition, data
buffering and MAC security.
The 4-wire SPI serial interface is used for configuration and data buffering.
An on-chip voltage regulator delivers the regulated 1.8 V supply voltage. The voltage
regulator may be enabled / disabled through a separate pin.
A battery monitor may optionally be used to monitor the unregulated power supply
voltage. The battery monitor is configurable through the SPI interface.
3.1.6 IEEE 802.15.4 Modulation Format:
This section is meant as an introduction to the 2.4 GHz direct sequence spread
spectrum (DSSS) RF modulation format defined in IEEE 802.15.4.
The modulation and spreading functions are illustrated at block level in Figure .Each
byte is divided into two symbols, 4 bits each. The least significant symbol is
transmitted first. For multi-byte fields, the least significant byte is transmitted first,
except for security related fields where the most significant byte it transmitted first.
Each symbol is mapped to one out of 16 pseudo-random sequences, 32 chips each.
The symbol to chip mapping is shown in Table 3. The chip sequence is then
transmitted at 2 MChips/s, with the least significant chip (C0) transmitted first for each
symbol.
(Fig 7 : Modulation and spreading functions)
30
Symbol Chip sequence (C0, C1, C2, … , C31)
0
11011001110000110101001000101110
1
11101101100111000011010100100010
2
00101110110110011100001101010010
3
00100010111011011001110000110101
4
01010010001011101101100111000011
5
00110101001000101110110110011100
6
11000011010100100010111011011001
7
10011100001101010010001011101101
8
10001100100101100000011101111011
9
10111000110010010110000001110111
10
01111011100011001001011000000111
11
01110111101110001100100101100000
12
00000111011110111000110010010110
13
01100000011101111011100011001001
14
10010110000001110111101110001100
15
11001001011000000111011110111000
(Table 1: IEEE 802.15.4 symbol-to-chip mapping)
The modulation format is Offset – Quadrature Phase Shift Keying (O-QPSK) with halfsine chip shaping. This is equivalent to MSK modulation. Each chip is shaped as a
half-sine, transmitted alternately in the I and Q channels with one half chip period
offset. This is illustrated for the zero-symbol in Figure.
31
(Fig 8 : I / Q Phases when transmitting a zero-symbol chip sequence, TC = 0.5 µs)
3.1.7 Microcontroller Interface and Pin Description:
When used in a typical system, CC2420 will interface to a microcontroller. This
microcontroller must be able to:
• Program CC2420 into different modes, read and write buffered data, and read back
status information via the 4-wire SPI-bus configuration interface (SI,
SO, SCLK
and
CSn).
• Interface to the receive and transmit FIFOs using the FIFO and FIFOP status pins.
• Interface to the CCA pin for clear channel assessment.
• Interface to the SFD pin for timing information (particularly for beaconing networks).
3.1.8 Configuration interface:
A CC2420 to microcontroller interface example is shown in Figure 11. The
microcontroller uses 4 I/O pins for the SPI configuration interface (SI, SO, SCLK and CSn).
SO
should be connected to an input at the microcontroller.
SI, SCLK
and
CSn
must be
microcontroller outputs. Preferably the microcontroller should have a hardware SPI
interface.
The microcontroller pins connected to
interface devices.
SO
SI, SO
and
SCLK
can be shared with other SPI-
is a high impedance output as long as
CSn
is not activated (active
low).
CSn should
have an external pull-up resistor or be set to a high level when the voltage
regulator is turned off in order to prevent the input from floating.
set to a defined level to prevent the inputs from floating.
32
SI and SCLK should
be
(Fig: 9 : Microcontroller interface example)
3.1.9 Receive mode :
In receive mode, the
SFD
pin goes high after the start of frame delimiter
(SFD) field has been completely received. If address recognition is disabled or is
successful, the
SFD
pin goes low again only after the last byte of the MPDU has
been received. If the received frame fails address recognition, the SFD pin goes low
immediately. This is illustrated in Figure 12.
The
FIFO
pin is high when there is one or more data bytes in the RXFIFO. The first
byte to be stored in the RXFIFO is the length field of the received frame, i.e. the
FIFO
pin is set high when the length field is written to the RXFIFO. The
FIFO
pin then
remains high until the RXFIFO is empty.
If a previously received frame is completely or partially inside the RXFIFO, the
FIFO
pin will remain high until the RXFIFO is empty.
The
FIFOP
pin is high when the number of unread bytes in the RXFIFO exceeds the
threshold programmed into
the
FIFOP
IOCFG0.FIFOP_THR.
When address recognition is enabled
pin will not go high until the incoming frame passes address recognition,
even if the number of bytes in the RXFIFO exceeds the programmed threshold.
The
FIFOP
pin will also go high when the last byte of a new packet is received, even
if the threshold is not exceeded. If so the
FIFOP pin
will go back to low once one byte
has been read out of the RXFIFO.
When address recognition is enabled, data should not be read out of the RXFIFO
before the address is completely received, since the frame may be automatically
flushed by CC2420 if it fails address recognition. This may be handled by using the
FIFOP pin, since this pin does not go high until the frame passes address
recognition.
33
Figure shows an example of pin activity when reading a packet from the RXFIFO.
In this example, the packet size is 8 bytes,
MODEMCTRL0.AUTOCRC
IOCFG0.FIFOP_THR
= 3 and
is set. The length will be 8 bytes, RSSI will contain the average
RSSI level during receiving of the packet and FCS/corr contain information of FCS
check result and the correlation levels.
3.1.10 RXFIFO overflow
The RXFIFO can only contain a maximum of 128 bytes at a given time. This
may be divided between multiple frames, as long as the total number of bytes is
128 or less. If an overflow occurs in the RXFIFO, this is signalled to the
microcontroller by setting the
FIFO
pin low while the
FIFOP
pin is high. Data already in
the RXFIFO will not be affected by the overflow, i.e. frames already received may
be read out.
A SFLUSHRX command strobe is required after a RXFIFO overflow to
enable reception of new data.For security enabled frames, the MAC layer must
read the source address of the received frame before it can decide which key to
use to decrypt or authenticate. This data must therefore not be overwritten even if
it has been read out of the RXFIFO by the microcontroller. If the
SECCTRL0.RXFIFO_PROTECTION control bit is set, CC2420 also protects the
frame header of security enabled frames until decryption has been performed. If
no MAC security is used or if it is implemented outside C2420, this bit may be
cleared
to
achieve
optimal
use
of
the
(Fig: 10 : Pin activity examples during receive )
34
RXFIFO.
(Fig 11 :Example of pin activity when reading RXFIFO)
3.1.11 Transmit mode:
During transmit, the
The
SFD
FIFO
and
FIFOP
pins are still only related to the RXFIFO.
pin is however active during transmission of a data frame, as shown in
Figure .
The SFD pin goes high when the SFD field has been completely transmitted. It goes
low again when the complete MPDU (as defined by the length field) has been
transmitted or if an underflow is detected. See the RF Data Buffering section on
page 37 for more information on TXFIFO underflow.
As can be seen from comparing Figure . and Figure , the SFD pin behaves
very similarly during reception and transmission of a data frame. If the
SFD pins
of
the transmitter and the receiver are compared during the transmission of a data
frame, a small delay of approximately 2 µs can be seen because of bandwidth
limitations in .both the transmitter and the receiver.
(Fig 12 : Pin activity example during transmit )
35
3.1.12 General control and status pins
In receive mode, the FIFOP pin can be used to interrupt the microcontroller
when a threshold has been exceeded or a complete frame has been received.
This pin should then be connected to a microcontroller interrupt pin.
In receive mode, the
FIFO
pin can be used to detect if there is data at all in the
receive FIFO.
The
SFD
pin can be used to extract the timing information of transmitted and
received data frames. The
SFD
pin will go high when a start of frame delimiter has
been completely detected / transmitted. The
SFD
pin should preferably be
connected to a timer capture pin on the microcontroller.
For debug purposes, the
signals as selected by the
SFD
and
IOCFG1
CCA
pins can be used to monitor several status
register. See Table 12 and Table 13 for available
signals.
The polarity of
FIFO, FIFOP, SFD
and
CCA
can be controlled by the
IOCFG0
register
(address 0x1C).
3.1.13 Demodulator, Symbol Synchroniser and Data Decision:
The block diagram for the CC2420 demodulator is shown in Figure .
Channel filtering and frequency offset compensation is performed digitally. The
signal level in the channel is estimated to generate the RSSI level (see the RSSI /
Energy Detection section on page 47 for more information). Data filtering is also
included for enhanced performance.
With the ±40 ppm frequency accuracy requirement from [1], a compliant receiver
must be able to compensate for up to 80 ppm or 200 kHz. The CC2420
demodulator tolerates up to 300 kHz offset without significant degradation of the
receiver performance.
Soft decision is used at the chip level, i.e. the demodulator does not make a
decision for each chip, only for each received symbol. De-spreading is performed
using over sampled symbol correlators. Symbol synchronisation is achieved by a
continuous start of frame delimiter (SFD) search.
When a SFD is detected, data is written to the RXFIFO and may be read out by
the microcontroller at a lower bit rate than the 250 kbps generated by the receiver.
The CC2420 demodulator also handles symbol rate errors in excess of 120 ppm
without performance degradation.
36
(Fig 13 : Demodulator Simplified Block Diagram)
3.2 MIXED SIGNAL CONTROLLER(MSP 430):
3.2.1 Features:
Low Supply-Voltage Range, 1.8 V . . . 3.6 V
Ultralow-Power Consumption:
Five Power-Saving Modes
Wake-Up From Standby Mode in less than 6 us
16-Bit RISC Architecture,125-ns Instruction Cycle Time
12-Bit A/D Converter With Internal Reference, Sample-and-Hold and
Autoscan Feature
16-Bit Timer_B With Seven Capture/Compare-With-Shadow Registers
16-Bit Timer_A With Three Capture/Compare Registers
On-Chip
Comparator
Serial
Onboard
Programming,No
External
Programming Voltage Needed Programmable Code Protection by
Security Fuse
Family Member Include :
MSP430F133: 8KB+256B Flash Memory,256B RAM
MSP430F135:16KB+256B Flash Memory,512B RAM
MSP430F147, MSP430F1471†:32KB+256B Flash Memory,1KB RAM
MSP430F148, MSP430F1481†:48KB+256B Flash Memory,2KB RAM
MSP430F149, MSP430F1491†:60KB+256B Flash Memory,2KB RAM
MSP Module:
37
(Fig 14 : basic core modele of mps430)
3.2.2 Description:
The Texas Instruments MSP430 family of ultralow-power microcontrollers
consist of several devices featuring different sets of peripherals targeted for
various applications. The architecture, combined with five low power modes is
optimized to achieve extended battery life in portable measurement applications.
The device featuresa powerful 16-bit RISC CPU, 16-bit registers, and constant
generators that attribute to maximum code efficiency.The digitally controlled
oscillator (DCO) allows wake-up from low-power modes to active mode in less
than 6us. The MSP430x13x and the MSP430x14x(1) series are microcontroller
configurations with two built-in 16-bit timers, a fast 12-bit A/D converter (not
implemented on the MSP430F14x1 devices), one or two universal serial
synchronous/asynchronous communication interfaces (USART), and 48 I/O pins.
Typical applications include sensor systems that capture analog signals, convert
38
them to digital values, and process and transmit the data to a host system. The
timers make the configurations ideal for industrial control applications such as
ripple counters, digital motor control, EE-meters, hand-held meters, etc. The
hardware multiplier enhances the performance and offers a broad code and
hardware-compatible family solution.
3.2.3 Pin Diagram:
(Fig 15 : functional block diagram of msp430)
3.2.4 Functional Block Diagram:
39
(Fig 16: block diagram of msp430)
3.2.5 Short-Form Description
CPU
The MSP430 CPU has a 16-bit RISC architecture that is highly transparent
to the application. All operations, other than program-flow instructions,are
performed as register operations in conjunction with seven addressing modes for
source operand and four addressing modes for destination operand. The CPU is
integrated with 16 registers that provide reduced instruction execution time. The
register-to-register operation execution time is one cycle of the CPU clock. Four of
the registers, R0 to R3, are dedicated as program counter, stack pointer, status
register, and constant generator respectively. The remaining registers are generalpurpose registers. Peripherals are connected to the CPU using data, address, and
control buses, and can be handled with all instructions.
Instruction Set:
The instruction set consists of 51 instructions with three formats and seven
address modes. Each instruction can operate on word and byte data. Table 1
shows examples of the three types of instruction formats; the address modes are
listed in Table .
40
(Table 2 :Instruction Set)
Operating Modes:
The MSP430 has one active mode and five software selectable low-power modes
of operation. An interrupt event can wake up the device from any of the five lowpower modes, service the request and restore back to the low-power mode on
return from the interrupt program.
The following six operating modes can be configured by software:
Active mode AM;
All clocks are active
Low-power mode 0 (LPM0);
CPU is disabled
ACLK and SMCLK remain active. MCLK is disabled
Low-power mode 1 (LPM1);
CPU is disabled
ACLK and SMCLK remain active. MCLK is disabled
DCO’s dc-generator is disabled if DCO not used in active mode
Low-power mode 2 (LPM2);
CPU is disabled
MCLK and SMCLK are disabled
DCO’s dc-generator remains enabled
ACLK remains active
Low-power mode 3 (LPM3);
CPU is disabled
MCLK and SMCLK are disabled
DCO’s dc-generator is disabled
ACLK remains active
41
Low-power mode 4 (LPM4);
CPU is disabled
ACLK is disabled
MCLK and SMCLK are disabled
DCO’s dc-generator is disabled
Crystal oscillator is stopped
Flash Memory:
The flash memory can be programmed via the JTAG port, the bootstrap
loader, or in-system by the CPU. The CPU can perform single-byte and singleword writes to the flash memory. Features of the flash memory include:
Flash memory has n segments of main memory and two segments of
information memory
(A and B) of 128 bytes each. Each segment in
main memory is 512 bytes in size.
Segments 0 to n may be erased in one step, or each segment may
be individually erased.
Segments A and B can be erased individually, or as a group with
segments 0−n.Segments A and B are also called information memory.
New devices may have some bytes programmed in the information
memory (needed for test during manufacturing). The user should
perform an erase of the information memory prior to the first use.
Peripherals:
Peripherals are connected to the CPU through data, address, and control
busses and can be handled using all instructions. For complete module
descriptions, see the MSP430x1xx Family User’s Guide, literature number
SLAU049.
Digital I/O:
There are six 8-bit I/O ports implemented—ports P1 through P6:
All individual I/O bits are independently programmable.
Any combination of input, output, and interrupt conditions is possible.
dge-selectable interrupt input capability for all the eight bits of ports P1 and
P2.
Read/write access to port-control registers is supported by all instructions.
42
Oscillator and System Clock:
The clock system in the MSP430x13x and MSP43x14x(1) family of devices is
supported by the basic clock module that includes support for a 32768-Hz watch
crystal oscillator, an internal digitally-controlled oscillator (DCO) and a high
frequency crystal oscillator. The basic clock module is designed to meet the
requirements of both low system cost and low-power consumption. The internal
DCO provides a fast turn-on clock source and stabilizes in less than 6 us. The
basic clock module provides the following clock signals:
Auxiliary clock (ACLK), sourced from a 32768-Hz watch crystal or a high
frequency crystal.
Main clock (MCLK), the system clock used by the CPU.
Sub-Main clock (SMCLK), the sub-system clock used by the peripheral
modules.
Watchdog Timer:
The primary function of the watchdog timer (WDT) module is to perform a
controlled system restart after a software problem occurs. If the selected time
interval expires, a system reset is generated. If the watchdog function is not
needed in an application, the module can be configured as an interval timer and
can generate interrupts at selected time intervals.
Recommended Operating conditions:
(Table 4 : operating conditions)
3.3 SENSORS:
43
To monitor parameters we sensors this type of sensors are discussed as
further in the review of each sensor
The type of sensors are as follows
3.3.1 LM 35:
LM 35 is a precision centigrade Temperature sensor. The LM35 is an integrated
circuit sensor that can be used to measure temperature with an electrical output
proportional to the temperature (in °C)
3.3.1.1General Description:
The LM35 series are precision integrated-circuit temperature sensors,
whose output voltage is linearly proportional to the Celsius (Centigrade)
temperature. The LM35 thus has an advantage over linear temperature sensors
calibrated in Kelvin, as the user is not required to subtract a large constant voltage
from its output to obtain convenient Centigrade scaling. The LM35 does not
require any external calibration or trimming to provide typical accuracies of ±1⁄4°C
at room temperature and ±3⁄4°C over a full −55 to +150°C temperature range. Low
cost is assured by trimming and calibration at the wafer level. The LM35’s low
output impedance, linear output, and precise inherent calibration make interfacing
to readout or control circuitry especially easy. It can be used with single power
supplies, or with plus and minus supplies. As it draws only 60 µA from its supply, it
has very low self-heating, less than 0.1°C in still air. The LM35 is rated to operate
over a −55° to +150°C temperature range, while the LM35C is rated for a −40° to
+110°C range (−10°with improved accuracy). The LM35 series is available
packaged in hermetic TO-46 transistor packages, while the LM35C, LM35CA, and
LM35D are also available in the plastic TO-92 transistor package. The LM35D is
also available in an 8-lead surface mount small outline package and a plastic TO220 package.
3.3.1.2Features:
Calibrated directly in ° Celsius (Centigrade)
Linear + 10.0 mV/°C scale factor
0.5°C accuracy guaranteeable (at +25°C)
Rated for full −55° to +150°C range
Suitable for remote applications
Low cost due to wafer-level trimming
44
Operates from 4 to 30 volts
Less than 60 µA current drain
Low self-heating, 0.08°C in still air
Nonlinearity only ±1⁄4°C typical
Low impedance output, 0.1 W for 1 mA load
3.3.1.3 Typical Applications:
(Fig 17 a : Basic Centigrade Temperature Sensor +2 c to +150 c)
(Fig 17: Full-Range Centigrade Temperature Sensor)
Choose R1 = −VS/50 µA
V OUT=+1,500 mV at +150°C
= +250 mV at +25°C
= −550 mV at −55°C
3.3.1.3
Maximum Ratings:
Supply Voltage +35V to −0.2V
Output Voltage +6V to −1.0V
Output Current 10 mA
Storage Temp.;
TO-46 Package, −60°C to +180°C
TO-92 Package, −60°C to +150°C
SO-8 Package, −65°C to +150°C
45
TO-220 Package, −65°C to +150°C
Lead Temp.:
TO-46 Package,
(Soldering, 10 seconds) 300°C
TO-92 and TO-220 Package,
(Soldering, 10 seconds) 260°C
SO Package (Note 12)
Vapor Phase (60 seconds) 215°C
Infrared (15 seconds) 220°C
ESD Susceptibility (Note 11) 2500V
Specified Operating Temperature Range: TMIN to T MAX
(Note 2)
LM35, LM35A −55°C to +150°C
LM35C, LM35CA −40°C to +110°C
LM35D 0°C to +100°C
Typical Performance Charecteristics:
Minimum Supply
Voltage vs Temperature
Thermal Resistance:
Junction to Air
46
Accuracy vs Temperature:
3.3.1.4
Application:
The LM35 can be applied easily in the same way as other integrated-circuit
temperature sensors. It can be glued or cemented to a surface and its temperature
will be within about 0.01§C of the surface temperature.This presumes that the
ambient air temperature is almost the same as the surface temperature; if the air
temperature were much higher or lower than the surface temperature,the actual
temperature of the LM35 die would be at an intermediate temperature between the
surface temperature and the air temperature. This is expecially true for the TO-92
plastic package, where the copper leads are the principal thermal path to carry
heat into the device, so its temperature might be closer to the air temperature than
to the surface temperature.To minimize this problem, be sure that the wiring to the
LM35, as it leaves the device, is held at the same temperature as the surface of
interest. The easiest way to do this is to cover up these wires with a bead of epoxy
which will insure that the leads and wires are all at the same temperature as the
47
surface, and that the LM35 die's temperature will not be affected by the air
temperature.
The TO-46 metal package can also be soldered to a metal surface or pipe
without damage. Of course, in that case the Vb terminal of the circuit will be
grounded to that metal. Alternatively, the LM35 can be mounted inside a sealedend metal tube, and can then be dipped into a bath or screwed into a threaded
hole in a tank. As with any IC, the LM35 and accompanying wiring and circuits
must be kept insulated and dry, to avoid leakage and corrosion. This is especially
true if the circuit may operate at cold temperatures where condensation can occur.
Printed-circuit coatings and varnishes such as Humiseal and epoxy paints or dips
are often used to insure that moisture cannot corrode the LM35 or its
connections.These devices are sometimes soldered to a small lightweight heat fin,
to decrease the thermal time constant and speed up the response in slowlymoving air. On the other hand, a small thermal mass may be added to the sensor,
to give the steadiest reading despite small deviations in the air temperature.
3.3.2
Humidity Sensor(HIH-3610):
The HIH-3610 Series humidity sensor is designed specifically for high volume
OEM (Original Equipment Manufacturer) users. Direct input to a controller or other
device is made possible by this sensor’s linear voltage output. With a typical
current draw of only 200 A, the HIH-3610 Series is ideally suited for low drain,
battery operated systems. Tight sensor interchangeability reduces or eliminates
OEM production calibration costs. Individual sensor calibration data is available.
The HIH-3610 Series delivers instrumentation-quality RH (Relative Humidity)
sensing performance in a low cost, solder able SIP (Single In-line Package).
Available in two lead spacing configurations, the RH sensor is a laser trimmed
thermo set polymer capacitive sensing element with on-chip integrated signal
conditioning. The sensing element's multilayer construction provides excellent
resistance to application hazards such as wetting, dust, dirt, oils, and common
environmental chemicals.
3.3.3 FEATURES
Molded thermoset plastic housing with cover
48
Linear voltage output vs %RH
Laser trimmed interchangeability
Low power design
High accuracy
Fast response time
Stable, low drift performance
Chemically resistant
3.3.4 TYPICAL APPLICATIONS
Refrigeration
Drying
Metrology
Battery-powered systems
OEM assemblies
3.3.5 PERFORMANCE SPECIFICATIONS
Parameter
RH Accuracy
Condition
±2% RH, 0-100% RH non-condensing, 25 °C,
Vsupply = 5 Vdc
RH Interchangeability
±5% RH, 0-60% RH; ±8% @ 90% RH typical
RH Linearity
±0.5% RH typical
RH Hysteresis
±1.2% RH span maximum
RH Repeatability
±0.5% RH
RH Response Time
1/e 15 sec in slowly moving air at 25 °C
RH Stability
±1% RH typical at 50% RH in 5 years
Power Requirements
Voltage Supply
4 Vdc to 5.8 Vdc, sensor calibrated at 5 Vdc
Current Supply
200 A at 5 Vdc
Voltage Output
Vout = Vsupply (0.0062(Sensor RH) + 0.16),
typical @ 25 C
49
(Data printout option provides a similar, but
sensor specific,
equation at 25 C.)
0.8 Vdc to 3.9 Vdc output @ 25 C typical
Vsupply = 5 Vdc
Push/pull symmetric; 50 A typical, 20 A
minimum, 100 A maximum , Turn-on 0.1 sec
Temperature Compensation
True RH = (Sensor RH)/(1.093 -0.0012T), T in
°F
True RH = (Sensor RH)/(1.0546-0.00216T), T in
C
Effect @ 0% RH
Effect @ 100% RH
±0.007 %RH/°C (negligible)
-0.22% RH/°C (<1% RH effect typical in occupied space
systems above 15 °C (59 F))
Humidity Range
Operating
0 to 100% RH, non-condensing(1
Storage
0 to 90% RH, non-condensing
Temperature Range
Operating
-40 °C to 85 °C (-40 F to 185 F)
Storage
-51 °C to 125 °C (-60 F to 257 F)
Handling
Static sensitive diode protected to 15 kV
maximum
3.4 ANALOG TO DIGITAL CONVERTER-ADC0804:
3.4.1 CONNECTION DIAGRAM:
50
ADC0804
Dual-In-Line and Small Outline (SO) Packages
(Fig. 18: Connection diagram of ADC0804)
3.4.2 GENERAL DESCRIPTION:
ADC0804 is a CMOS 8-bit successive approximation A/D converter that
uses a differential potentiometric ladder similar to the 256R products. This
converter is designed to allow operation with the NSC800 and INS8080A
derivative control bus with TRI-STATE output latches directly driving the data bus.
This A/D appear like memory location or I/O ports to the microprocessor and no
interfacing logic is needed.
Differential analog voltage inputs allow increasing the common-mode
rejection and offsetting the analog zero input voltage value. In addition, the voltage
reference input can be adjusted to allow encoding any smaller analog voltage span
to the full 8 bits of resolution.
3.4.3 KEY SPECIFICATIONS:
Resolution
: 8 bits
Total error
: ±1⁄4 LSB, ±1⁄2 LSB and ±1 LSB
Conversion time
: 100 μs
3.4.4 FEATURES:
Compatible with 8080 μP derivatives—no interfacing logic needed - access
time - 135 ns.
Easy interface to all microprocessors, or operates “stand alone”.
Differential analog voltage inputs.
51
Logic inputs and outputs meet both MOS and TTL voltage level
specifications.
Works with 2.5V (LM336) voltage reference.
On-chip clock generator.
0V to 5V analog input voltage range with single 5V supply.
No zero adjust required.
0.3" standard width 20-pin DIP package.
20-pin molded chip carrier or small outline package.
Operates ratio metrically or with 5 VDC, 2.5 VDC, or analog span adjusted
voltage reference.
3.4.5 BLOCK DIAGRAM OF ADC0804:
(Fig. 19: Block Diagram of ADC0804)
3.4.6 PARAMETRIC TABLE:
52
Min. Supply Voltage
4.5 Volt
Max. Supply Voltage
6.3 Volt
Resolution
8 bit
Conversion Time
100 us
Interface Type
Parallel
3.5 Level Converter(max 232):
3.5.1 Pin Diagram:
(Fig 20: pin diagram of max 232)
The MAX232 is a dual driver/receiver that includes a capacitive voltage generator
to supply TIA/EIA-232-F voltage levels from a single 5-V supply. Each receiver
converts TIA/EIA-232-F inputs to 5-V TTL/CMOS levels.These receivers have a
typical threshold of 1.3 V, a typica
-V
inputs. Each driver converts TTL/CMOS input levels into TIA/EIA-232-F levels. The
driver, receiver, and voltage-generator functions are available as cells in the Texas
53
3.5.2 Internal Diagram :
Sure enough, the MAX232 is the chip for you. It runs on a single chip supply
(+5 volts), and requires a few external capacitors. There is another version, the
MAX233 which requires no external parts. It is, however, a little larger physically,
and also costs about 75% more than the MAX232A.
Here is a diagram of the internals of the MAX232A. It shows a double charge
pump voltage doubler and a +10v to -10v voltage inverter. The voltages output are
used to generate the RS-232 compliant signals. The MAX232A has provisions for
two serial ports on the same physical package. Most people only connect one of
them.
(Fig 30 : intermal diagram of max 232)
3.5.3 Circuit diagram:
The picture shows the connection of rs 232 and max232 for the data
communication to the PC. Almost all digital devices which is used is at either TTL
or CMOS logic levels. Therefore the first step to connecting a device to the RS-232
port is to transform the RS-232 levels back into 0 and 5 Volts. As we have already
covered, this is done by RS-232 Level Converters.Two common S-232 Level
Converters are the 1488 RS-232 Driver and the 1489 RS-232 Receiver
Each package contains 4 inverters of the one type, either Drivers or
Receivers. The driver requires two supply rails, +7.5 to +15v and -7.5 to -15v. As
you could imagine this may pose a problem in many instances where only a single
supply of +5V is present. However the advantages of these I.C's are they are
cheap..
54
(Fig 31 : connection of rs 232 and max 232)
RS-232 Driver/Receiver:
Newer devices like MAX-232 (Maxim), ICL232 (Harris) and AD232
(Analog Devices) include a Charge Pump, which generates +10V and -10V from a
single 5 volts supply. This I.C. also includes two receivers and two transmitters in
the same package. This is handy in many cases when there is need to use both
transmit and receive data Lines. There are also many variations of these devices.
The large value of capacitors is not only bulky, but also expensive. Therefore other
devices are available which use smaller capacitors and even some with inbuilt
capacitors.Recently Analog devices have introduces a device which requires only
one cap and supports one transmit and one receive line.
CHAPTER 4
PROGRAMMING
55
4.1 INTRODUCTION:
In this chapter the code program written in visual basic and embedded c is
described below.This code is used to accept the digital bit available at the 9 pin
RS 232 port so that the input signal is converted and displayed in the VB screen.
4.2 VISUAL BASIC PROGRAMME:
Option Explicit
'int a
Dim tmpVal, humVal, pressVal As String
Private Sub Form_Load()
Call LP_Clear_Data
Label6.Caption = DateTime.Date$
MSComm1.RThreshold = 2
MSComm1.Settings = "9600,N,8,1"
MSComm1.DTREnable = False
MSComm1.CommPort = 1
MSComm1.PortOpen = True
End Sub
Private Sub LP_Clear_Data()
Label6.Caption = ""
Label7.Caption = ""
Label8.Caption = ""
Label9.Caption = ""
'Label10.Caption = ""
End Sub
Private Sub MSComm1_OnComm()
Dim sData As String
Dim lHighByte As Long
Dim lLowByte As Long
Dim lByte As Long
Dim Prs As String ' Pressure
Dim Temp As String ' Temperature
Dim Hum As String ' Humidity
Label8.Caption = "" 'Humidity
Label9.Caption = "" ' temperature
'Label10.Caption = "" 'Pressure
56
If MSComm1.CommEvent = comEvReceive Then
sData = MSComm1.Input
On Error Resume Next
If Mid(sData, 1, 1) = "T" Then
tmpVal = Mid(sData, 2, 5)
End If
If Mid(sData, 1, 1) = "H" Then
humVal = Mid(sData, 2, 5)
End If
If Mid(sData, 1, 5) = "RRRRR" Then
Me.Label16.Caption = "NO RAIN FALL"
End If
If Mid(sData, 1, 5) = "RFFFF" Then
Me.Label16.Caption = "RAIN FALL"
End If
Label8.Caption = humVal
Label9.Caption = tmpVal
'Label10.Caption = pressVal
End If
End Sub
Private Sub Timer1_Timer()
Call MSComm1_OnComm
End Sub
Private Sub Timer2_Timer()
Label7.Caption = Time
End Sub
4.2 C PROGRAM FOR RECIVEING :
#include<stdio.h>
#include<reg52.h>
57
void DELAY(unsigned int);
void SER_SET();
void CONVERSION();
void TEMPE();
void HUMIDITY();
void GAS_DEDUCT();
void RAIN_FALL();
sbit GAS_SENS=P3^6;
sbit RAIN_SENS=P3^7;
unsigned int temp,humi,l,k,i,h;
unsigned char TEM[6],HUM[6];
//unsigned char GAS1[10]="SSSS";
//unsigned char GAS2[10]="NNNN";
unsigned char RAIN1[10]="RRRR";
unsigned char RAIN2[10]="FFFF";
void main()
{
P2=0XFF;
P1=0XFF;
P3=0XFF;
SER_SET();
GAS_SENS=0;
RAIN_SENS=1;
while(1)
{
l=P2;
TEMPE();
DELAY(50);
l=P1+30;
HUMIDITY();
DELAY(50);
//GAS_DEDUCT();
//DELAY(50);
RAIN_FALL();
DELAY(50);
TI=0;
SBUF=0X0D;
while(TI==0);
TI=0;
DELAY(500);
}
}
/*--------->TEMPERATURE CALC and TXION FUNCTION<-----------------*/
void TEMPE()
58
{
k=0;
while(l>0)
{
k=(l%10)+(k*10);
l=l/10;
}
temp=k;
i=0;
if(temp>=100&&temp<1000)
{
TEM[0]='0';
i=1;
}
if(temp<100)
{
TEM[0]='0';
TEM[1]='0';
i=2;
}
while(temp>0)
{
TEM[i]=(temp%10)+0X30;
temp=temp/10;
i++;
}
if(k<10)
{
TEM[3]='0';
i=4;
}
TEM[i]='\0';
TI=0;
SBUF='T';
while(TI==0);
TI=0;
i=0;
while(TEM[i]!='\0')
{
TI=0;
SBUF=TEM[i];
while(TI==0);
TI=0;
i++;
}
}
/*--------->HUMIDITY CALC and TXION FUNCTION<-----------------*/
void HUMIDITY()
{
k=0;
while(l>0)
{
59
k=(l%10)+(k*10);
l=l/10;
}
humi=k;
i=0;
if(humi<100)
{
HUM[0]='0';
HUM[1]='0';
i=2;
}
if(humi>=100&&humi<1000)
{
HUM[0]='0';
i=1;
}
while(humi>0)
{
HUM[i]=(humi%10)+0X30;
humi=humi/10;
i++;
}
if(k<10)
{
HUM[3]='0';
i=4;
}
HUM[i]='\0';
TI=0;
SBUF='H';
while(TI==0);
TI=0;
i=0;
while(HUM[i]!='\0')
{
TI=0;
SBUF=HUM[i];
while(TI==0);
TI=0;
i++;
}
}
/*--------->RAIN FALL DETECTION and TXION FUNCTION<-----------------*/
/*void GAS_DEDUCT()
{
TI=0;
SBUF='G';
while(TI==0);
TI=0;
i=0;
if(GAS_SENS==1) //IF RAIN FALL FOUND
{
60
while(GAS1[i]!='\0')
{
TI=0;
SBUF=GAS1[i];
while(TI==0);
TI=0;
DELAY(20);
i++;
}
}
else if(GAS_SENS==0)
//IF GAS LEAK NOT FOUND
{
while(GAS2[i]!='\0')
{
TI=0;
SBUF=GAS2[i];
while(TI==0);
TI=0;
DELAY(20);
i++;
}
}
}
*/
/*--------->RAIN FALL DETECTION and TXION FUNCTION<-----------------*/
void RAIN_FALL()
{
TI=0;
SBUF='R';
while(TI==0);
TI=0;
i=0;
if(RAIN_SENS==1) //IF RAIN FALL NOT FOUND
{
while(RAIN1[i]!='\0')
{
TI=0;
SBUF=RAIN1[i];
while(TI==0);
TI=0;
//DELAY(20);
i++;
}
}
else if(RAIN_SENS==0) //IF RAIN FALL FOUND
{
while(RAIN2[i]!='\0')
{
TI=0;
SBUF=RAIN2[i];
while(TI==0);
TI=0;
//
DELAY(20);
61
i++;
}
}
}
/*--------->DELAY FUNCTION<-----------------*/
void DELAY(unsigned int count)
{ // mSec Delay 11.0592 Mhz
unsigned int j;
// Keil v7.5a
while(count)
{
j = 115;
while(j>0)
j--;
count--;
}
}
/*--------->SERIAL INITIALIZING FUNCTION<-----------------*/
void SER_SET()
{
TMOD=0X20;
TH1=0XFD;
TL1=0XFD;
SCON=0X50;
TR1=1;
}
CHAPTER 5
5.1 CONCLUSION
62
The fundamental aim of this project is to design a wireless weather system
which enables to monitor the weather parameter in an industry by using zigbee
technology and display the parameter on the PC’s screen using visual basic. The
components used in the circuit are readily available. The individual sub-circuits
have been designed on PCB and tested for functioning in the laboratory. The test
has been performed by placing the sensor board both in an indoor and outdoor
and the parameters are noted and checked with the analog transducers for errors
and the errors are very minimum. ZigBee targets applications not addressable by
Bluetooth or any other wireless standard.
The Zigbee based wireless weather station is essentially a design and
implementation project of wireless technology. To approach a project like this a
parallel path has to be taken in regards to the theory and the practical circuitry, for
a successful conclusion in any project the paths must meet, and this only happens
when they are fully understood. This is why a good grounding in the basics of
Digital, Computer interfacing ports & programming in micro controller ,visual
basic6.0 language must be achieved before ever approaching a project like this.
To start off looking at basic of wireless device was must. This is what made the
overall project challenging and rewarding.
The design use for this project is essentially quite a simple one, and it is this
simplicity which partly brings it down when it comes to the overall reliable
performance.
5.2 FUTURE SCOPE:
The zigbee technology can be wide used for home and industrial
automation.It lead to the cheap wireless technology, so that it can be widely used
for low rate data transfer. It can also be used for the remote control unit like
toys,etc. We got a proposed zigbee universal remote controller. It requires only
200us of latency and high efficient use of power. Zigbee is the best for where the
battery is replaced very rarely.
REFERENCES
63
1. www.zigbeealliance.com
2. www.wikipedia.org
3. Wireless Communication System by Roody Coolen
4. Communication Electronics by Freznel
64