CS241 Final - Course Website Directory
advertisement

Take-Home Review Exam
(cs423)
Problem 1: Multiple Choice Questions
1) (1 Point) What two advantages do threads have over multiple processes?
A.
a. Threads have separate memory space;
b. Threads don't destroy shared data;
B.
a. Threads are inexpensive to create and destroy;
b. Threads use very little resources while they exist;
C.
a. Threads don't have to {\em trust} each other;
b. Threads don't have separate memory space;
Write your answer here:____
2) (1 Point) A rendezvous requires
A.
B.
C.
D.
no buffering
double buffering
a buffer queue
none of the above
Write your answer here:____
3) (1 Point) Assume that there are four queues in a multilevel queue scheduling system:
one first-come first-served queue and three round-robin queues with quantum = 8, 16, and 32
milliseconds respectively. What is the quantum of the first-come first-served queue?
A.
B.
C.
D.
8 milliseconds
64 milliseconds
32 milliseconds
none of the above
Write your answer here:____
4) (1 Point) What is convoy effect?
A. Having one IO-bound process and {\it n} CPU-bound process
B. Having mixed balance between IO bound and CPU bound processes
C. Having {\it n} IO-bound processes and one CPU-bound process
Write your answer here:____
5) (1 Point) A signal handler is useful for
A. catching SIGKILL
B. specifying action to be taken for a specific signal
C. changing signal from UNBLOCKED to BLOCKED signal
Write your answer here:____
6) (1 Point) Let us assume an event (job) arriving with the constant arrival rate of 20 processes
per second. Let us assume two processors with the constant service rates 20 processes per second
each. What is the overall system utilization under these assumptions?
A. 100%
B. 50%
C. 20%
Write your answer here:____
7) (2 Point) Consider the 2-process solution to the critical section problem
(i refers to the current process and j is the other one)
repeat
flag[i] := true ;
while (flag[j]) do no-op ;
<critical-section>
flag[i] := false ;
<remainder-section>
until false ;
This solution does NOT satisfy :
A
B
C
D
E
Mutual Exclusion
Progress
Bounded Wait
both (b) and (c)
none of the above
Write your answer here:____
8) Consider the reader-writer problem below:
semaphore mutex, wrt;
int readcount = 0;
mutex = 1; wrt = 1;
Writer:
Reader:
Down(&wrt);
write document
Up(&wrt);
Down(&mutex);
readcount++;
if (readcount == 1) Down(&wrt);
Read Document
readcount--;
if (readcount == 0) Up(&wrt);
Up(&mutex);
Which statement is TRUE based on the above code?
A. Multiple readers are satisfying mutual exclusion among each other when reading a
shared document
B. Writer and multiple readers are simultaneously reading and writing into the document
C. The first reader signals the entry of the writer to the critical region
D. The last reader blocks the writer to enter the critical region
Write your answer here:____
9) (1 Point) Which one of the following describes which allocation schemes (Contiguous,
Indexed, Linked) suffer(s) from external fragmentation?
A. Contiguous only
B. Indexed only
C. Linked only
D. Contiguous and Indexed
E. Indexed and Contiguous
Write your answer here:____
10) (1 Point) Which of the following file descriptor statements is NOT correct?
A. File descriptors are local to each process.
B. When a process is forked, its children can inherit open file descriptors.
C. Each process can have many file descriptors.
D. Open file descriptors are unique for each process.
E. Valid file descriptors are specific for each thread.
Write your answer here:____
11) (1 Point) A UNIX file system has 4-KB blocks and 4-byte disk addresses. The inode of file
‘X’ requires 8 direct entries and an indirect block which is half full. How large is the file in
blocks?
A. 16
B. 264
C. 520
D. 1032
E. 5004
Write your answer here:____
12) (1 Point) How many disk operations are needed to fetch the first data block of the file /a/b/c?
Assume that the inode of ‘/a’ is already in memory, but not the contents of ‘a’ and there are no
other mount points. Assume all directory listings use one disk block.
A. 2
B. 3
C. 4
D. 5
E. More than 5
Write your answer here:____
13) (1 Point) “Only one process may use a resource at a time” best describes which one of the
following?
A. Mutual Exclusion
B. Hold and wait
C. No preemption
D. Circular wait
E. Starvation
Write your answer here:____
14) (1 Point) “A process may hold allocated resources while awaiting assignment of other
resources” best describes which one of the following conditions?
A. Mutual Exclusion
B. Hold and wait
C. No preemption
D. Circular wait
E. Starvation
Write your answer here:____
15) (1 Point) “No resource can be forcibly removed from a process holding it” best describes
which one of the following conditions?
A. Mutual Exclusion
B. Hold and wait
C. No preemption
D. Circular wait
E. Starvation
Write your answer here:____
16) (1 Point) Which problem is avoided by defining a linear ordering of resource types that is
followed by all processes?
A. Mutual Exclusion
B. Hold and wait
C. No preemption
D. Circular wait
E. Starvation
Write your answer here:____
17) (1 Point) Which one of the statements about the linker is TRUE?
A. The linker fixes code and data cross-references of multiple compilation units
B. The linker processes conditional compilation directives (#if #else #endif)
C. The linker chains together multiple CPU cache lines for better performance
D. The linker is executed before the C preprocessor in modern POSIX systems
E. The linker requires super-user privileges to execute on modern POSIX systems
Write your answer here:____
18) (1 Point) Which one of the following is NOT true for the File Descriptor table?
A.
B.
C.
D.
E.
Entries 0,1,2 are used for standard in, out and error.
Shared by multiple threads of the same process.
Shared by multiple processes on the same system.
Is cloned when a process is forked.
File descriptors are small integers.
Write your answer here:____
19) (1 Point) Which one of the following is NOT true for an entry in the System File table?
A.
B.
C.
D.
More than one entry may point to the same file
Contains file offset for each entry
Contains access mode for each entry
Contains a count of the number of file descriptors using it
E. Is only used to securely map system library files.
Write your answer here:____
20) (1 Point) Which one of the following allocation schemes is the best choice if fast random
read access of a large file is the only concern?
A.
B.
C.
D.
Contiguous allocation.
Linked allocation.
Indexed allocation.
Multi-level indexed allocation.
Write your answer here:____
21) (1 Point) Which two schemes are commonly used to manage disk free-space?
A.
B.
C.
D.
E.
Hash and linked list.
Hash and bit-vector.
FIFO and bit-vector.
FIFO and linked list.
Bit vector and linked list.
Write your answer here:____
22) (1 Point) Which one of the following is NOT stored in a disk partition?
A.
B.
C.
D.
E.
Master boot record.
Super block.
Free-space management information.
inode data.
Directory names.
Write your answer here:____
23) (1 Point) Which one of following best describes the seek time of a disk?
A.
B.
C.
D.
Latency of moving the disk head
Time required to access one block from the disk
Latency of moving the disk head plus the average rotational delay
Latency of moving the disk head plus the maximal rotational delay
Write your answer here:____
24) (1 Point) A 512KB file is stored contiguously on one disk track. Each track contains 1024
sectors, each sector is 512 bytes. Average seek time=1ms and rotational speed is 15,000 RPM
(Rotations Per Minute) . What is the average access time to read the entire file, in milliseconds?
Hint: 60,000 RPM = 1 rotation per 1ms.
A.
B.
C.
D.
E.
Between 0 and 1.9 ms
Between 2.0 and 2.4 ms
Between 2.5 and 2.9 ms
Between 3.0 and 4.9 ms
Between 5.0 and 10.0 ms
Write your answer here:____
25) TCP opens what kind of connection between the client and server?
A.
B.
C.
D.
one-way asymmetric connection
one-way symmetric connection
two-way symmetric connection
two-way asymmetric connection
Write your answer here:___
END OF MULTIPLE CHOICE
SHORT ANSWER QUESTIONS FOLLOW ON THE NEXT PAGE
CS 241
Netid:__________________
Problem 2. Memory Allocation [10 Points]
2A) In most systems, a process can allocate and de-allocate memory from its heap using malloc()
and free(). A heap is just a chunk of memory. Suppose the heap is managed with linked list. Each
node in the list is either allocated or free. The list is sorted by address. When malloc() is called,
the list is searched for a free segment that is big enough (depending on the allocation algorithm),
that segment is divided into an allocated segment (at the beginning) and a free segment. When
free() is called, the segment should merge with its neighboring segments, if they are also free.
Consider a process with a heap of 14MB, which is initially unused and empty. During its
execution, the process issues the following memory allocation/de-allocation calls
void* p1 = malloc(4MB)
void* p2 = malloc(3MB)
void* p3 = malloc(2MB)
free(p2)
void* p4 = malloc(2MB)
free(p1)
void* p5 = malloc(2MB)
Show the heap allocation after the above calls, using best-fit, worst-fit and next-fit algorithms.
Assume heap memory begins at address 0, and ignore memory used by the linked list itself. The
tables below are included for your convenience and will not be graded.
* Identify the starting address of p4 and p5 (e.g. p5=13 MB).
* Determine the size of the largest available contiguous free space available at the end.
[9 points]
BEST:
0
1
2
3
p4= ______ MB
WORST:
0
1
2
0
1
2
p4= ______ MB
5
6
p5= ______ MB
3
p4= ______ MB
NEXT:
4
4
5
6
p5= ______ MB
3
4
5
6
p5= ______ MB
7
8
9
10
11
12
13
largest contiguous space= ______ MB
7
8
9
10
11
12
13
largest contiguous space= ______ MB
7
8
9
10
11
12
13
largest contiguous space= ______ MB
2B) Briefly describe one problem with the Worst-Fit allocation algorithm. [1 point]
Problem 3. Networking
3A) List and briefly explain 2 features that TCP provides that UDP does not [4 points].
CS 241
Netid:__________________
i)
ii)
3B) Briefly explain one advantage of using TCP instead of UDP to perform a file transfer [1
Point]
3C) Briefly explain one advantage of using UDP instead of TCP to stream video content. [1
Point]
3D) Briefly explain the purpose of the TTL field in the IP header. [1 Point]
3E) An application creates a UDP packet with a ”TTL” number of 5. Under what conditions
would this packet arrive at the destination? [1 Point]
Problem 4. Deadlock A
5A) What is the difference between a preemptible and a non-preemptible resource? [1 point]
CS 241
Netid:__________________
5B) Briefly explain why preemption of the CPU resource requires interrupts and timers. [1
point]
5C) Consider the following resource requests. Process 1 requests exclusive use of both the CPU
and the display. Process 2 requests exclusive use of both the display and the disk. Process 3
requests exclusive use of both the disk and the network. Process 4 requests exclusive use of both
the network and the display. Resources are assigned in process request order (Process 1 is first).
The disk, display and network resources are non-preemptible. Determine if deadlock is possible
by constructing a Resource Allocation Graph and a Wait-For graph. [4 points]
i) Resource Allocation Graph:
ii) Wait-for-Graph:
5D) Consider the following.
Each philosopher has completed CS241, and they go for lunch. If a philosopher
notices that the group is about to deadlock, he/she will release the utensil
(fork/chopstick) they are currently holding and put it back on the table.
Determine if each of the four requirements for deadlock are satisfied in the above variation of the
Dining Philosophers problem. [2 points]
i)
CS 241
Netid:__________________
ii)
iii)
iv)
5E) At the end of the meal, one philosopher complains of not eating. Explain the difference
between deadlock and starvation and why starvation is possible. [2 points]
CS 241
Netid:__________________
Problem 5. Deadlock B
6A) Consider the following three threads executing different paths of execution. Determine if
and where deadlock can occur for each thread. For example, “Thread 1 can deadlock on Line 2”
would mean that Thread 1 can deadlock and wait forever to acquire mutex_e. [3 points]
Line
1
2
3
4
5
Thread 1
lock(mutex_d)
lock(mutex_e)
e=d*2
unlock(mutex_e)
unlock(mutex_d)
Thread 2
lock(mutex_e)
lock(mutex_f)
f=f+e
unlock(mutex_f)
unlock(mutex_e)
Thread 3
lock(mutex_f)
lock(mutex_d)
d=d*f
unlock(mutex_d)
unlock(mutex_f)
Complete the following, or write “deadlock cannot occur”
Thread 1 can deadlock on line ___
Thread 2 can deadlock on line ___
Thread 3 can deadlock on line ___
6B) Determine if and where deadlock can occur. [2 points]
1
2
3
4
5
6
7
8
9
10
Thread 1
lock(mutex_h)
lock(mutex_i)
lock(mutex_j)
j=i+h
unlock(mutex_j)
unlock(mutex_h)
lock(mutex_g)
g=g+i
unlock(mutex_g)
unlock(mutex_i)
Thread 2
lock(mutex_g)
lock(mutex_i)
i=g+g
unlock(mutex_i)
unlock(mutex_g)
Complete the following, or write “deadlock cannot occur”
Thread 1 can deadlock on line ___
Thread 2 can deadlock on line ___
CS 241
Netid:__________________
Problem 6. File system
7A.) Determine the reference count of the disk inode associated with file ‘f1’ and ‘f2’ after the
following set of shell commands. Files do not exist prior to the execution of the following
commands. The commands complete successfully (without errors). [2 Points]
1> echo “hello CS241” > f1
2> ln –s f1 f2
3> ln f2 f3
4> ln f1 f4
5> rm f4
final reference count for f1 = ____
final reference count for f2 = ____
7B.) In the above example, which is the last line that modifies the inode update time for f1?
[1 point]
Give the line number: ________
7C.) A process reads all bytes of a 2^20 byte file '/tmp/s/g1' . g1 is a soft link to file g2 in the
same directory. If reading the directory entries of /tmp is the first block read, how many blocks in
total must be read?
Assume each directory’s listing fits into one block , a block size is 2^12 bytes and we deal with
a standard inode-based file-system where the first 10 blocks are referenced directly and a block
pointer requires 4 bytes. Assume after the first time a block is read or written, its contents are
cached in memory. [2 points]
CS 241
Netid:__________________
Problem 7. File I/O Implementation
The following functions and structure may or may not be useful in this problem.
struct stat {
dev_t st_dev; /* device inode resides on */
ino_t st_ino; /* inode's number */
mode_t st_mode; /* inode protection mode */
nlink_t st_nlink; /* number or hard links to the file */
uid_t st_uid; /* user-id of owner */
gid_t st_gid; /* group-id of owner */
dev_t st_rdev; /* device type, for special file inode */
…
};
int stat(const char *path, struct stat *sb); //returns 0(success) or -1
Assume a standard inode-based file system. Complete the C function ‘is_same_physical_file’ to
return the integer result ‘1’,’2’ or ‘3’.
Return value
Condition
1
Two given strings f1 and f2 refer to the same physical file, i.e., refer to the same
physical data blocks on the disk
2
Either of the given files does not exist (errno==ENOENT)
3
All other conditions, including other error conditions
Assume f1 and f2 are valid null-terminated C strings: Each refers to a regular data file that
currently exists or has been recently removed. Assume f1, f2 ultimately refer to files on the same
mounted file-system. Include error handling for the condition that the file(s) cannot be found.
Ensure “==”, “=” etc. are clearly legible.
int is_same_physical_file(char*f1, char*f2) {
//write your code here
}
CS 241
Netid:__________________
Problem 8. Network Implementation
Complete the C code below to set up a TCP server socket with a backlog of 8 connections, and
wait for a connection. Store the connection socket in the variable 'conn_sock'. The following
constants and functions may be useful. The server socket address is provided as an argument
‘addr’. You do not need to include error handling or use any fields of any structures. Assume that
there is additional code after your block of code that uses 'conn_sock'.
// constants: AF_INET, PF_INET, SOCK_DGRAM, SOCK_STREAM
int accept(int s, struct sockaddr *addr, socklen_t *addrlen);
int bind(int sockfd, struct sockaddr *my_addr, socklen_t addrlen);
int connect(int sockfd, const struct sockaddr *serv_addr, socklen_t addrlen);
int listen(int s, int backlog);
int socket(int domain, int type, int protocol);
void server(struct sockaddr_in *addr)
{
int conn_sock;
// write your code here
}
CS 241
Netid:__________________
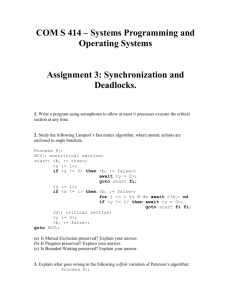
Problem 9. Synchronization
Consider the following code:
Lock mutex;
mutex.acquire();
shared variable accessed
mutex.release();
1) (14 Points) Write a pseudo-code to define Lock structure and the procedures acquire,
release, applying swap hardware synchronization mechanism. Note that the swap
routine is defined as follows:
void swap(char *x, *y)
{ char temp;
temp=*x;
*x = *y;
*y = temp; }
2) (6 Points) Explain why your implementation enforces mutual exclusion.
END OF EXAM
Check your answers.
Check your Netid is on every sheet.
Check your Problem 1 responses are written on the Right
Hand Side.
You can use this sheet for scratch paper, or for overflow.