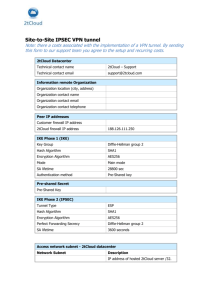
VPN Client not connected error
I setup Cisco PIX 515 in my lab to test IPSec VPN. The PIX is behind a
Linksys WRTP54G router and UDP port 500 is open. I can establish the VPN
in the LAN, but I get not connected error if I test it from a remote office that
is behind another PIX 515E. I am not sure the problem is the Linksys router
or PIX in the office. Any suggestions?
The lab PIX configuration can be found here,
http://www.howtonetworking.com/cisco/pixvpnsample.htm
Here are VPN client log.
Cisco Systems VPN Client Version 4.6.01.0019
Copyright (C) 1998-2004 Cisco Systems, Inc. All Rights Reserved.
Client Type(s): Windows, WinNT
Running on: 5.1.2600 Service Pack 2
1
09:58:38.469 05/26/06 Sev=Info/4
Begin connection process
CM/0x63100002
2
09:58:38.979 05/26/06 Sev=Info/4
CVPND/0xE3400001
Microsoft IPSec Policy Agent service stopped successfully
3
09:58:38.979 05/26/06 Sev=Info/4
Establish secure connection using Ethernet
CM/0x63100004
4
09:58:38.979 05/26/06 Sev=Info/4
CM/0x63100024
Attempt connection with server "chicagotech.net"
5
09:58:40.247 05/26/06 Sev=Info/6
IKE/0x6300003B
Attempting to establish a connection with x.x.x.246.
6
09:58:40.557 05/26/06 Sev=Info/4
IKE/0x63000013
SENDING >>> ISAKMP OAK AG (SA, KE, NON, ID, VID(Xauth), VID(dpd),
VID(Nat-T), VID(Frag), VID(Unity)) to x.x.x.246
7
09:58:40.587 05/26/06 Sev=Info/4
IPSec driver successfully started
IPSEC/0x63700008
8
09:58:40.587 05/26/06 Sev=Info/4
Deleted all keys
IPSEC/0x63700014
9
IKE/0x6300002F
09:58:40.947 05/26/06 Sev=Info/5
Received ISAKMP packet: peer = x.x.x.246
10
09:58:40.947 05/26/06 Sev=Info/4
IKE/0x63000014
RECEIVING <<< ISAKMP OAK AG (SA, VID(Xauth), VID(dpd), VID(Unity),
VID(?), KE, ID, NON, VID(?), VID(Nat-T), NAT-D, NAT-D, HASH) from
x.x.x.246
11
09:58:40.947 05/26/06 Sev=Info/5
Peer supports XAUTH
IKE/0x63000001
12
09:58:40.947 05/26/06 Sev=Info/5
Peer supports DPD
IKE/0x63000001
13
09:58:40.947 05/26/06 Sev=Info/5
Peer is a Cisco-Unity compliant peer
IKE/0x63000001
14
09:58:40.947 05/26/06 Sev=Info/5
IKE/0x63000082
Received IOS Vendor ID with unknown capabilities flag 0x000000A5
15
09:58:40.947 05/26/06 Sev=Info/5
Peer supports NAT-T
IKE/0x63000001
16
09:58:40.977 05/26/06 Sev=Info/6
IOS Vendor ID Contruction successful
IKE/0x63000001
17
09:58:40.977 05/26/06 Sev=Info/4
IKE/0x63000013
SENDING >>> ISAKMP OAK AG *(HASH,
NOTIFY:STATUS_INITIAL_CONTACT, NAT-D, NAT-D, VID(?), VID(Unity)) to
x.x.x.246
18
09:58:40.997 05/26/06 Sev=Info/6
Sent a keepalive on the IPSec SA
IKE/0x63000055
19
09:58:40.997 05/26/06 Sev=Info/4
IKE/0x63000083
IKE Port in use - Local Port = 0x1194, Remote Port = 0x1194
20
09:58:40.997 05/26/06 Sev=Info/5
Automatic NAT Detection Status:
Remote end IS behind a NAT device
This end IS behind a NAT device
IKE/0x63000072
21
09:58:40.997 05/26/06 Sev=Info/4
CM/0x6310000E
Established Phase 1 SA. 1 Crypto Active IKE SA, 0 User Authenticated IKE
SA in the system
22
09:58:40.997 05/26/06 Sev=Info/4
CM/0x6310000E
Established Phase 1 SA. 1 Crypto Active IKE SA, 1 User Authenticated IKE
SA in the system
23
09:58:41.566 05/26/06 Sev=Info/5
IKE/0x6300005E
Client sending a firewall request to concentrator
24
09:58:41.566 05/26/06 Sev=Info/5
IKE/0x6300005D
Firewall Policy: Product=Cisco Systems Integrated Client, Capability=
(Centralized Protection Policy).
25
09:58:41.566 05/26/06 Sev=Info/4
IKE/0x63000013
SENDING >>> ISAKMP OAK TRANS *(HASH, ATTR) to x.x.x.246
26
09:58:46.860 05/26/06 Sev=Info/4
Retransmitting last packet!
IKE/0x63000021
27
09:58:46.860 05/26/06 Sev=Info/4
IKE/0x63000013
SENDING >>> ISAKMP OAK TRANS *(Retransmission) to x.x.x.246
28
09:58:51.305 05/26/06 Sev=Info/6
Sent a keepalive on the IPSec SA
IKE/0x63000055
29
09:58:52.304 05/26/06 Sev=Info/4
Retransmitting last packet!
IKE/0x63000021
30
09:58:52.304 05/26/06 Sev=Info/4
IKE/0x63000013
SENDING >>> ISAKMP OAK TRANS *(Retransmission) to x.x.x.246
31
09:58:55.900 05/26/06 Sev=Info/5
Received ISAKMP packet: peer = x.x.x.246
IKE/0x6300002F
32
09:58:55.900 05/26/06 Sev=Info/4
IKE/0x63000014
RECEIVING <<< ISAKMP OAK AG (Retransmission) from x.x.x.246
33
09:58:55.900 05/26/06 Sev=Info/4
Retransmitting last packet!
IKE/0x63000021
34
09:58:55.900 05/26/06 Sev=Info/4
IKE/0x63000013
SENDING >>> ISAKMP OAK AG *(Retransmission) to x.x.x.246
35
09:58:57.798 05/26/06 Sev=Info/4
Retransmitting last packet!
IKE/0x63000021
36
09:58:57.798 05/26/06 Sev=Info/4
IKE/0x63000013
SENDING >>> ISAKMP OAK TRANS *(Retransmission) to x.x.x.246
37
09:59:01.793 05/26/06 Sev=Info/6
Sent a keepalive on the IPSec SA
IKE/0x63000055
38
09:59:03.291 05/26/06 Sev=Info/4
IKE/0x6300002D
Phase-2 retransmission count exceeded: MsgID=442F0A75
39
09:59:03.291 05/26/06 Sev=Info/4
IKE/0x63000013
SENDING >>> ISAKMP OAK INFO *(HASH, NOTIFY:DPD_REQUEST) to
x.x.x.246
40
09:59:03.291 05/26/06 Sev=Info/6
IKE/0x6300003D
Sending DPD request to x.x.x.246, our seq# = 2226793716
41
09:59:03.341 05/26/06 Sev=Info/4
IKE/0x63000017
Marking IKE SA for deletion (I_Cookie=672CDA295511818F
R_Cookie=9ADE594A69BA0090) reason = DEL_REASON_IKE_NEG_FAILED
42
09:59:03.341 05/26/06 Sev=Info/4
IKE/0x63000013
SENDING >>> ISAKMP OAK INFO *(HASH, DEL) to x.x.x.246
43
09:59:06.787 05/26/06 Sev=Info/4
IKE/0x6300004B
Discarding IKE SA negotiation (I_Cookie=672CDA295511818F
R_Cookie=9ADE594A69BA0090) reason = DEL_REASON_IKE_NEG_FAILED
44
09:59:06.787 05/26/06 Sev=Info/4
CM/0x6310000F
Phase 1 SA deleted before Mode Config is completed cause by
"DEL_REASON_IKE_NEG_FAILED". 0 Crypto Active IKE SA, 0 User
Authenticated IKE SA in the system
45
09:59:06.797 05/26/06 Sev=Info/5
Initializing CVPNDrv
CM/0x63100025
46
09:59:06.807 05/26/06 Sev=Info/4
IKE/0x63000001
IKE received signal to terminate VPN connection
47
09:59:06.937 05/26/06 Sev=Info/4
IKE/0x63000086
Microsoft IPSec Policy Agent service started successfully
48
09:59:07.297 05/26/06 Sev=Info/4
Deleted all keys
IPSEC/0x63700014
49
09:59:07.297 05/26/06 Sev=Info/4
Deleted all keys
IPSEC/0x63700014
50
09:59:07.297 05/26/06 Sev=Info/4
Deleted all keys
IPSEC/0x63700014
51
09:59:07.297 05/26/06 Sev=Info/4
IPSec driver successfully stopped
IPSEC/0x6370000A