Creating a KMS Use Case
advertisement
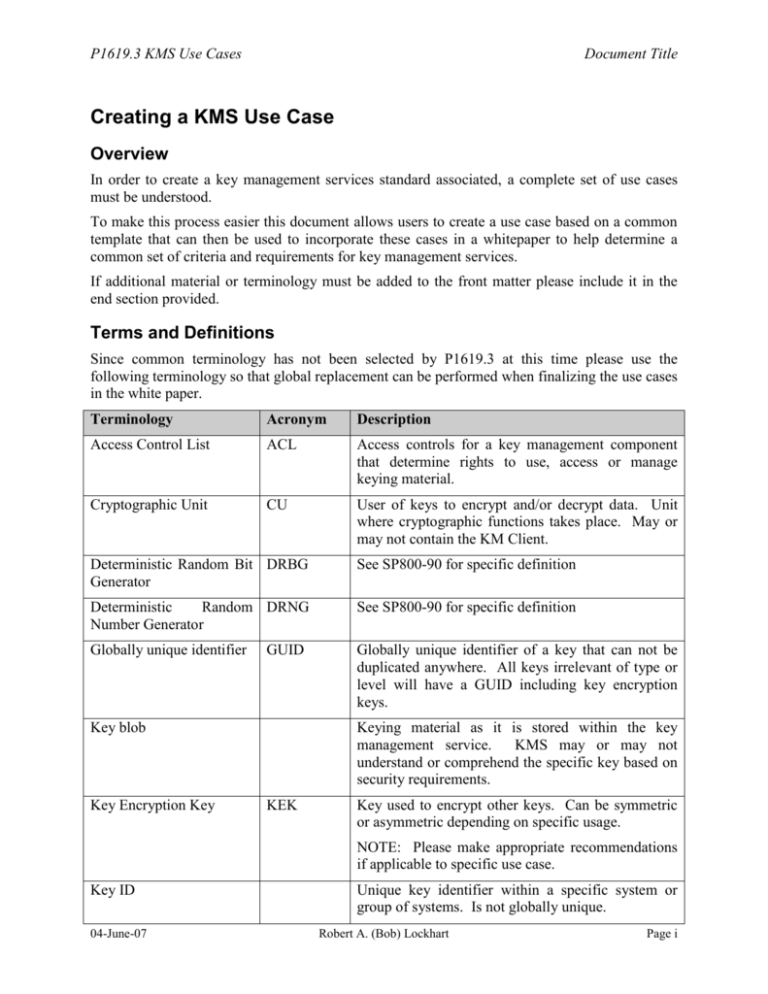
P1619.3 KMS Use Cases Document Title Creating a KMS Use Case Overview In order to create a key management services standard associated, a complete set of use cases must be understood. To make this process easier this document allows users to create a use case based on a common template that can then be used to incorporate these cases in a whitepaper to help determine a common set of criteria and requirements for key management services. If additional material or terminology must be added to the front matter please include it in the end section provided. Terms and Definitions Since common terminology has not been selected by P1619.3 at this time please use the following terminology so that global replacement can be performed when finalizing the use cases in the white paper. Terminology Acronym Description Access Control List ACL Access controls for a key management component that determine rights to use, access or manage keying material. Cryptographic Unit CU User of keys to encrypt and/or decrypt data. Unit where cryptographic functions takes place. May or may not contain the KM Client. Deterministic Random Bit DRBG Generator See SP800-90 for specific definition Deterministic Random DRNG Number Generator See SP800-90 for specific definition Globally unique identifier Globally unique identifier of a key that can not be duplicated anywhere. All keys irrelevant of type or level will have a GUID including key encryption keys. GUID Key blob Key Encryption Key Keying material as it is stored within the key management service. KMS may or may not understand or comprehend the specific key based on security requirements. KEK Key used to encrypt other keys. Can be symmetric or asymmetric depending on specific usage. NOTE: Please make appropriate recommendations if applicable to specific use case. Key ID 04-June-07 Unique key identifier within a specific system or group of systems. Is not globally unique. Robert A. (Bob) Lockhart Page i P1619.3 KMS Use Cases Document Title Terminology Acronym Description Key Management Service KMS Key management service defines all aspects of key management that includes but is not limited to the following functions: Key metadata Key Management API Key generation Key storage Key lifecycle management Policy management Audit and accounting KM User console Data associated with a specific key or group of keys KMAPI API for KM Client to KM Server and KM Server to KM Server communications. May require the development of one or more tool kits by one or more vendors. KM Client KM Policy KM Server 04-June-07 Provides communications directly or as a proxy between cryptographic unit and KM Server. KMP Policies defining various automatic controls as they relate to keys. Policy functions include but are not limited to: Generation requirements Key length and strength Re-keying and Retention Distribution and Replication Usage Auditing requirements Key granularity Access control KMS server that provides specific functions that may include one or more of the following: Key lifecycle management Policy functions Accounting and reporting functions Key storage KM User console Robert A. (Bob) Lockhart Page ii P1619.3 KMS Use Cases Terminology Document Title Acronym KM User Message Code Description Key management human or application user that must provide appropriate credentials to log in to the KMS to manage, monitor and/or maintain keys. Authentication MAC Media Encryption Key Cryptographic data integrity checking. While specific methods may be in use please use MAC as common term for where and how data or keys are verified for integrity. MEK Key used to encrypt data. Sometimes referred to as Data, Tape, Disk or other type of media encryption key. NOTE: For purposes of use cases please use generic MEK term. Non-deterministic random NRBG bit generator See SP800-90 for specific definition Non-deterministic random NRNG number generator See SP800-90 for specific definition Parent Key GUID Globally unique identifier (GUID) of a key encryption key (KEK) used to protect one or more media encryption keys (MEK) KEK GUID Requirements To create a use case a specific set of information both basic and detailed must be included. The information required in each of the sections is as follows: Section Information Provided Overview Basic concept of use case that includes description, entities involved both in cryptographic operations and normal operations. Overview should have a figure showing physical connectivity of entities involved. Application requirements Requirements of application without encryption being involved including hosts, networks and media involved. Additional considerations for operations compression, communications protocols, etc…) 04-June-07 Robert A. (Bob) Lockhart (i.e. Page iii P1619.3 KMS Use Cases Document Title Section Information Provided Encryption requirements Placement and uses of cryptographic unit or units Key management requirements (services used) Policy requirements (types and definitions) Data security requirements (mobile data, ACL’s, encryption, etc…) Key requirements This includes metadata that may apply to a specific type of key, key typing, key wrapping and other information required about the key for the described use case. Key management services requirements Services required from KMS such as key generation, storage, retrieval, archiving, auditing, etc… Communications requirements Topologies and possible protocols that may be used to transport keys (i.e. Ethernet, Fibre Channel, IP, SCSI, TLS, etc…) NOTE: where possible please include a diagram of required interaction between application and storage as well as KMS, KM Client and CU. Summary Optional section with a short review of the requirements and why this is included in the use case whitepaper. This can be written at a later date and time prior to inclusion into the whitepaper so is not required up front. Additional information may be required at a later date prior to publication of the specification. Once completed with the template please forward a copy with or without contact information to the P1619 reflector and a copy with contact information to: Matt Ball SISWG Chair Eric Hibbard SISWG Vice-chair Bob Lockhart P1619.3 Editor The following information should be entered (between the brackets []) prior to editing the below use case: Use Case Title: [Document Title] Use Case Author(s): [Author Name] Primary Contact email: [youremail@yourdomain.com] Date document submitted: [04-June-07] 04-June-07 Robert A. (Bob) Lockhart Page iv P1619.3 KMS Use Cases Document Title Please use the following pages as a template for the KMS use cases. You can modify the order the information is provided in by moving sections around. If a section does not apply to the use case please leave it blank but leave the section title. Do not include a table of contents, figures or tables. These tables will be added to final document. When finalizing your document, do not delete these first four pages if returning in Word or rich text format the above text information is required to keep some of the information updated. If additional sections are needed, add them as required prior to the appendices. 04-June-07 Robert A. (Bob) Lockhart Page v P1619.3 KMS Use Cases Document Title Document Title Use Case Introduction Operational and security requirements Basic concept of use case that includes description, entities involved both in cryptographic operations and normal operations. Overview should have a figure showing physical connectivity of entities involved. Include security requirements and reasons for encryption if applicable. Operational Entities Include all non-security and non-cryptographic related entities for this use case. Security and cryptographic entities Include all security and cryptographic related entities that participate in this use case. Operational scenario overview Describe in detail the normal data usage of the specific use case. Cryptographic usage overview Explain what and where cryptography is taking place. Algorithms, modes, authentication need only be mentioned in reference to symmetric, asymmetric, access controls, authentication mechanisms, etc… Specifics may be asked for at a later date. Key requirements Include any and all requirements for keys including generation, storage, etc… Include a table of metadata requirements for a key (time stamps, Policies, Key ID, etc…) Key Management Services use requirements Include any and all services required from KMS such as key generation, storage, retrieval, archiving, auditing, etc… NOTE: Do not feel locked in to services listed above. If additional services are required such as name services, directory services, etc… include them as part of the KMS cloud. They can be separated out later. Communications requirements List communication transports the need support such as IP, SCSI, etc… 04-June-07 Robert A. (Bob) Lockhart Page 1 P1619.3 KMS Use Cases Document Title Transport1 Rename title to appropriate topology being used. Include specific security concerns when using the transport to carry keys. Include detailed diagrams, if appropriate, of both topology and communications flow. Transport2 Rename section title or delete as needed. transport (if used) to carry keys. Include specific security concerns when using Include detailed diagrams, if appropriate, of both topology and communications flow. Summary Optional Section 04-June-07 Robert A. (Bob) Lockhart Page 2 P1619.3 KMS Use Cases Document Title Appendix 1 – Additional Terminology Terminology Acronym Description Appendix 2 – Additions Outside of P1619.3 Scope 04-June-07 Robert A. (Bob) Lockhart Page 1