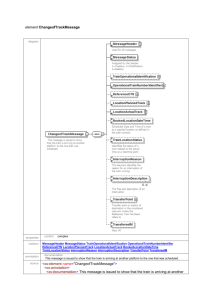
3 TIML Protocol Elements
advertisement

2 Tokens and Protocol for the Temporal Integrity Markup Language (TIML) 3 1 Introduction 4 5 6 This submission defines an XML schema for a timestamping protocol. The schema is based upon the RFC 3161 ASN.1 timestamping protocol, but uses the XML Signature standard for signature formatting. 7 2 Terminology 8 9 The key words must, must not, required, shall, shall not, should, should not, recommended, may, and optional in this document are to be interpreted as described in [RFC2119]. 1 10 3 TIML Protocol Elements 11 References to the ASN.1 protocol fields in this description refer to fields defined in [RFC3161]. 12 3.1 Schema Header and Namespace Declarations 13 14 The following schema fragment defines the XML namespaces and other header information for the timestamping schema: 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 <?xml version="1.0" encoding="UTF-8" ?> <schema xmlns="http://www.w3.org/2001/XMLSchema" targetNamespace="http://www.entrust.com/schemas/timestampprotocol-20020207" xmlns:ds="http://www.w3.org/2000/09/xmldsig#" xmlns:ts="http://www.entrust.com/schemas/timestamp-protocol20020207" xmlns:xs="http://www.w3.org/2001/XMLSchema" elementFormDefault="qualified" attributeFormDefault="unqualified" version="1.0" xml:lang="en"> <import namespace="http://www.w3.org/2000/09/xmldsig#" schemaLocation="http://www.w3.org/TR/2001/PR-xmldsig-core20010820/xmldsig-core-schema.xsd" /> 31 32 Note: The targetNamespace will have to be changed to one defined by OASIS, not one defined by Entrust. 33 3.2 Elements <StatusText> and <StatusInfo> 34 35 The <StatusText> element MAY be used to include reason text such as "Digest element is not correctly formatted". 36 The following schema fragment defines the <StatusText> element: <element name="StatusText" type="string"/> 37 38 39 The <StatusInfo> element specifies the status of the response to a timestamp request. It includes the following elements and attributes: 40 <StatusInfo> [Optional] 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 MAY be used to include reason text such as "Digest element is not correctly formatted". status [Required] Indicates the status of the response. The values correspond to the values in the ASN.1 protocol field PKIStatus, with the same semantics and restrictions. failureInfo [Optional] When the request was not fulfilled, the failureInfo attributee indicates the reason why the time-stamp request was rejected. The values correspond to the values in the ASN.1 protocol field PKIFailureInfo, with the same semantics and restrictions. The following schema fragment defines the <StatusInfo> element: <element name="StatusInfo"> <complexType> <sequence> <element ref="ts:StatusText" minOccurs="0" /> </sequence> <attribute name="status" use="required"> <simpleType> <restriction base="NMTOKEN"> <enumeration value="granted" /> <enumeration value="grantedWithModifications" /> <enumeration value="rejection" /> <enumeration value="waiting" /> <enumeration value="revocationWarning" /> <enumeration value="revocationNotification" /> </restriction> </simpleType> </attribute> <attribute name="failureInfo" use="optional"> <simpleType> <restriction base="NMTOKEN"> <enumeration value="badAlgorithm" /> <enumeration value="badRequest" /> <enumeration value="badDataFormat" /> <enumeration value="timeNotAvailable" /> <enumeration value="unacceptedPolicy" /> <enumeration value="unacceptedExtension" /> <enumeration value="additionalInformationNotAvailable" /> <enumeration value="systemFailure" /> </restriction> </simpleType> </attribute> </complexType> 2 83 </element> 84 3.3 Element <Policy> 85 86 The <Policy> element specifies the policy under which the timestamp was created. It contains the following attribute: 87 88 89 90 91 92 93 94 95 id [Required] Identifies the policy, by means of a URI. The following schema fragment defines the <Policy> element: <element name="Policy"> <complexType> <attribute name="id" type="anyURI" use="required" /> </complexType> </element> 96 3.4 Element <Digest> 97 98 The <Digest> element contains the message digest of the document that is being timestamped. It contains the following elements: 99 <Transforms> [Optional] 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 Indicates the transforms (e.g., canonicalization algorithms) that must be applied to the source before being digested. This element is imported from [XMLSig]. <DigestMethod> [Required] Indicates the digest method used to create the message digest. This element is imported from [XMLSig]. <DigestValue> [Required] Contains the output of the digest method algorithm applied to the transformed document being timestamped. This element is imported from [XMLSig]. The following schema fragment defines the <Digest> element: <element name="Digest"> <complexType> <sequence> <element ref="ds:Transforms" minOccurs="0" /> <element ref="ds:DigestMethod" /> <element ref="ds:DigestValue" /> </sequence> </complexType> </element> 118 3.5 Element <SerialNumber> 119 120 The <SerialNumber> element contains an integer serial number of the timestamp that is issued. 3 121 The following schema fragment defines the <SerialNumber> element. 122 <element name="SerialNumber" type="integer" /> 123 3.6 Element <CreationTime> 124 125 The <CreationTime> element contains the time at which the timestamp token has been created by the TSA. 126 127 128 The following schema fragment defines the <CreationTime> element. <element name="CreationTime" type="dateTime" /> 129 3.7 Element <Accuracy> 130 131 132 133 134 135 The <Accuracy> element represents the time deviation around the time contained in <CreationTime>. By adding the <accuracy> value to the <CreationTime> value, an upper limit on the time at which the timestamp token has been created by the TSA can be obtained. In the same way, by subtracting the <accuracy> value from the <CreationTime> value, a lower limit on the time at which the timestamp token has been created by the TSA can be obtained. It contains the following attributes: 136 seconds [Optional] 137 138 139 140 141 A non-negative integer representing the accuracy in seconds. milliseconds [Optional] An integer in the range [1..999] representing the accuracy in milliseconds. microseconds [Optional] An integer in the range [1..999] representing the accuracy in microseconds. 142 If any of the attributes are not present a value of 0 is assumed. 143 The following schema fragment defines the <Accuracy> element: 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 <element name="Accuracy"> <complexType> <attribute name="seconds" type="nonNegativeInteger" use="optional" /> <attribute name="milliseconds" use="optional"> <simpleType> <restriction base="positiveInteger"> <maxInclusive value="999" /> </restriction> </simpleType> </attribute> <attribute name="microseconds" use="optional"> <simpleType> <restriction base="positiveInteger"> <maxInclusive value="999" /> </restriction> </simpleType> </attribute> </complexType> </element> 4 164 3.8 Element <Ordering> 165 166 167 168 The <Ordering> element represents whether or not the timestamps issued by this TSA can be strictly ordered based upon the value in the <CreationTime> element. It’s semantics and restrictions are identical as the corresonding field in the ASN.1 protocol. The following schema fragment defines the <Ordering> element: 169 <element name="Ordering" type="boolean" /> 170 171 3.9 Element <Nonce> 172 173 The <Nonce> element contains a random value, used only once, to prevent replay attacks and to link requests and responses. The following schema fragment defines the <Nonce> element: 174 <element name="Nonce" type="integer" /> 175 3.10 Element <Extensions> 176 177 The <Extensions> element is a generic way to add additional information in the future. The following schema fragment defines the <Extensions> element: 178 179 180 181 182 183 184 185 <element name="Extensions"> <complexType> <sequence> <any namespace="##any" minOccurs="0" maxOccurs="unbounded" processContents="lax" /> </sequence> </complexType> </element> 186 187 3.11 Element <TimeStampRequest> 188 189 The <TimeStampRequest> element is used to request a timestamp on a particular document from a TSA. It contains the following elements: 190 <Policy> [Optional] 191 192 193 194 195 196 197 198 199 200 If present, it indicates the policy under which the timestamp token SHOULD be issued. <Digest> [Required] Contains the message digest of the document for which the timestamp is being requested. <Nonce> [Optional] If present, it contains a random value, used only once, to prevent replay attacks and to link requests and responses. <Extensions> [Optional] An extension point for future use. Do we want to have a version number? 5 201 202 Do we want to have a certReq field as in RFC 3161 that requests TSA certification (or more generally other TSA authentication information) be sent back in the response? 203 The following schema fragment defines the <TimeStampRequest> element: 204 205 206 207 208 209 210 211 212 213 <element name="TimeStampRequest"> <complexType> <sequence> <element ref="ts:Policy" minOccurs="0" /> <element ref="ts:Digest" /> <element ref="ts:Nonce" minOccurs="0" /> <element ref="ts:Extensions" minOccurs="0" /> </sequence> </complexType> </element> 214 3.12 Element <TimeStampInfo> 215 216 The <TimeStampInfo> element contains the data that is included within a timestamp token (<TimeStampResponse>). It contains the following elements: 217 <Policy> [Required] 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 Contains the policy under which the token was issued. If the corresponding element appears in the <TimeStampRequest> then this element MUST be identical to at least one of those elements. <Digest> [Required] Contains the message digest of the document being timestamped. This element MUST be identical to the corresponding element in the <TimeStampRequest>. <SerialNumber> [Optional] Contains a serial number for the timestamp token. If present, it MUST be unique for each token issued by a TSA. <CreationTime> [Required] The time at which the token was issued. <Accuracy> [Optional] The accuracy of the timestamp. <Ordering> [Optional] Indicates whether or not timestamps issued by this TSA can be strictly ordered according to the value in the <CreationTime> element. <Nonce> [Optional] MUST be present if and only if the corresponding element is present in the <TimeStampRequest> and MUST contain an identical value. <Extensions> [Optional] An extension point for future use. 6 239 240 Do we want to include a TSA field to identify the TSA. It doesn’t seem necessary, but RFC 3161 had one? 241 The following schema fragment defines the <TimeStampInfo> element: 242 243 244 245 246 247 248 249 250 251 252 253 254 255 <element name="TimeStampInfo"> <complexType> <sequence> <element ref="ts:Policy" /> <element ref="ts:Digest" /> <element ref="ts:SerialNumber" minOccurs="0" /> <element ref="ts:CreationTime" /> <element ref="ts:Accuracy" minOccurs="0" /> <element ref="ts:Ordering" minOccurs="0" /> <element ref="ts:Nonce" minOccurs="0" /> <element ref="ts:Extensions" minOccurs="0" /> </sequence> </complexType> </element> 256 3.13 Element <TimeStampResponse> 257 258 259 The <TimeStampResponse> element is the response to a <TimeStampRequest>. If the request is successful, then it contains the actual timestamp token produced by the TSA. It contains the following elements: 260 <StatusInfo> [Required] 261 262 263 264 265 266 267 268 269 270 271 272 273 274 275 276 277 278 279 Contains the status of the response. <Signature> [Optional] Contains the enveloping signature of the TSA over the <TimeStampInfo> element. Thus, <TimeStampInfo> is inside of this element. When the status attribute of the <StatusInfo> element contains the value granted or grantedWithModifications, this element MUST be present. When the status attribute of the <StatusInfo> element contains any other value, this element MUST NOT be present. This element is imported from [XMLSig]. The following schema fragment defines the <TimeStampResponse> element: <element name="TimeStampResponse"> <complexType> <sequence> <element ref="ts:StatusInfo" /> <!-- enveloping signature with TimeStampInfo inside --> <element ref="ds:Signature" minOccurs="0" /> <element ref="ts:Extensions" minOccurs="0" /> </sequence> </complexType> </element> 281 4 TIML and XML Signature Syntax and Processing 282 These are requirements on the relying party. 280 7 283 4.1 Token Validation 284 285 We will need to define the process whereby a Time Stamp Token (<TimeStampResponse>) is validated by a relying party. 286 4.2 Signature Validation 287 288 We will also need to define the process of verifying an XML Signature when there is a Time Stamp Token associated with it. 289 5 Time Stamp Authority Requirements 290 These are requirements on the Time Stamp Authority. 291 6 Methods of Identifying the TSA 292 293 294 We will need to think about how to identify the TSA. If X.509 certificates are being used, then the id-kp-timeStamping Extended Key Usage extension from [RFC3161] should be used. We will also need to think about how to identify a TSA when SAML is used. 295 7 References 296 7.1 Normative 297 298 [RFC2119] S. Bradner, Key words for use in RFCs to Indicate Requirement Levels, http://www.ietf.org/rfc/rfc2119.txt, IETF RFC 2119, March 1997. 299 300 301 [RFC3161] C. Adams, P. Cain, D. Pinkas, R. Zuccherato, Internet X.509 Public Key Infrastructure Time Stamp Protocols, http://www.ietf.org/rfc/rfc3161.txt, RFC 3161, August 2001. 302 303 [XMLSig] D. Eastlake et al., XML-Signature Syntax and Processing, http://www.w3.org/TR/xmldsig-core/, World Wide Web Consortium. 304 8