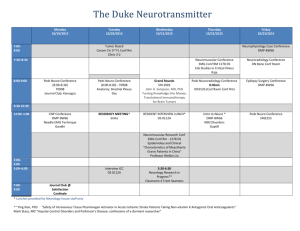
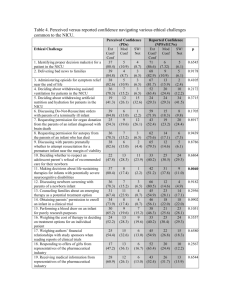
3818-11-sitet - Cisco Support Community
advertisement

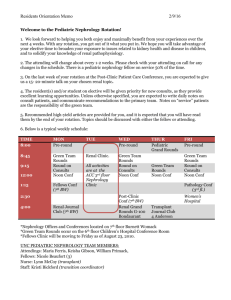
Site to Site VPN
Objective: To configure a site to site VPN between two Cisco PIX firewalls
Topology and Basic Setup:
Connect the PIX firewalls as shown in the figure.
Connect the PIX to the COM port of the PC using the console cable and bring up
HyperTerminal
Assign IP addresses as shown in the figure and also set up a static route to the
Internet Gateway on both the firewalls.
Configuration: The same configuration is required on both firewalls, with only the
IP addresses changing
Access the configuration mode
o Pixfirewall # configure terminal
Enable ISAKMP on the outside interface
o Pixfirewall(conf)# isakmp enable outside
Specify that authentication will be through a pre-shared secret.
o Pixfirewall(conf)# isakmp policy 10 authentication preshare
Specify DES as the encryption algorithm for ISAKMP (IKE Phase 1 SA)
o Pixfirewall(conf)# isakmp policy 10 encryption des
Specify MD5 as the hash algorithm for ISAKMP (IKE Phase 1 SA)
o Pixfirewall(conf)# isakmp policy 10 hash md5
Specify that the peer firewall will be identified by its IP address.
o Pixfirewall(conf)# isakmp identity address
Configure the Pre shared secret as “zoom123”. For the peer IP address, fill in the
public IP address of the other firewall.
o Pixfirewall(conf)# isakmp key zoom123 address <peer ip address>
Identify traffic to be encrypted using access-lists. Refer fig. for the addresses.
Remote network refers to the inside network of the other firewall.
o Pixfirewall(conf)#access-list 1 permit ip < inside n/w address> < mask>
< remote n/w address> <mask>
Configure IPSec Transform set suite, with the name “myset”, and encryption
DES, hash MD5 with ESP header
o Pixfirewall(conf)# crypto ipsec transform-set myset esp-des esp-hmacmd5
Configure a crypto map, “mymap”, and specify that key exchange will be
through ISAKMP
o Pixfirewall(conf)# crypto map mymap 10 ipsec-isakmp
Specify the traffic to be matched to trigger IPSEC negotiations
o Pixfirewall(conf)# crypto map mymap 10 match address 1
Specify the IP address of the IP sec peer. This is the public IP address of the other
firewall. Refer fig. for the addresses.
o Pixfirewall(conf)# crypto map mymap 10 set peer <ip address>
Set the lifetime of the IPSEC SA to 3600 seconds
o Pixfirewall(conf)# crypto map mymap 10 set security-association
lifetime seconds 3600
Set the IPSEC transform set to “myset”.
o Pixfirewall(conf)# crypto map mymap 10 set transform-set myset
Apply the crypto map to the outside interface
o Pixfirewall(conf)# crypto map mymap interface outside
Configure No NAT for the traffic to be encrypted
o Pixfirewall(conf)# nat (inside) 0 access-list 1
Allow the firewall to accept IKE traffic
o Pixfirewall(conf)# sysopt connections permit-ipsec
Save the configuration
o Pixfirewall(conf)# write memory
Verification:
Check the configuration using “show config”.
From the LAN, try to access a private HTTP server on the remote firewall’s
inside network. Access will be allowed because of the site-to-site VPN.
Command Syntax: Pixfirewall(conf)# isakmp enable <if-name>
Pixfirewall(conf)# isakmp policy <priority> authentication { preshare | rsasig}
Pixfirewall(conf)# isakmp policy <priority> encryption {des | 3des}
Pixfirewall(conf)# isakmp policy <priority> hash {md5 | sha}
Pixfirewall(conf)# isakmp identity { name | address}
Pixfirewall(conf)# isakmp key <key> address <peer ip address> [netmask
<mask>]
Pixfirewall(conf)#access-list <acl ID> [iline <line no>] {deny| permit}
<protocol> < source address> <mask> [<operator> <port>] <destination
address> <mask> [<operator> <port>]
Pixfirewall(conf)# crypto ipsec transform-set < transform-set name> {
<transform-1> [ transform-2] [transform-3] }
Pixfirewall(conf)# crypto map <map name> <seq no> { ipsec-isakmp | ipsecmanual}
Pixfirewall(conf)# crypto map <map name> <seq no> match address <acl id>
Pixfirewall(conf)# crypto map <map name> <seq no> set peer {<host name >
| <ip address>}
Pixfirewall(conf)# crypto map <map name> <seq no> set security-association
lifetime { seconds <seconds> | kilobytes <kilobytes>}
Pixfirewall(conf)# crypto map <map name> <seq no> set transform-set
<transform set name –1> [… <transform-set name 6>]
Pixfirewall(conf)# crypto map <map name> interface <if-name>
Pixfirewall(conf)#nat [(if_name)] 0 [access-list acl_id ]
Pixfirewall(conf)# sysyopt connections permit-ipsec
Show commands
Pixfirewall(conf)# show crypto ipsec sa
Pixfirewall(conf)# show crypto isakmp sa
Pixfirewall(conf)# debug crypto ipsec
Pixfirewall(conf)# debug crypto isakmp