Control Number : 262 The Problem of Fingerprint Recognition
advertisement
Control Number : 262
The Problem of Fingerprint Recognition
Background
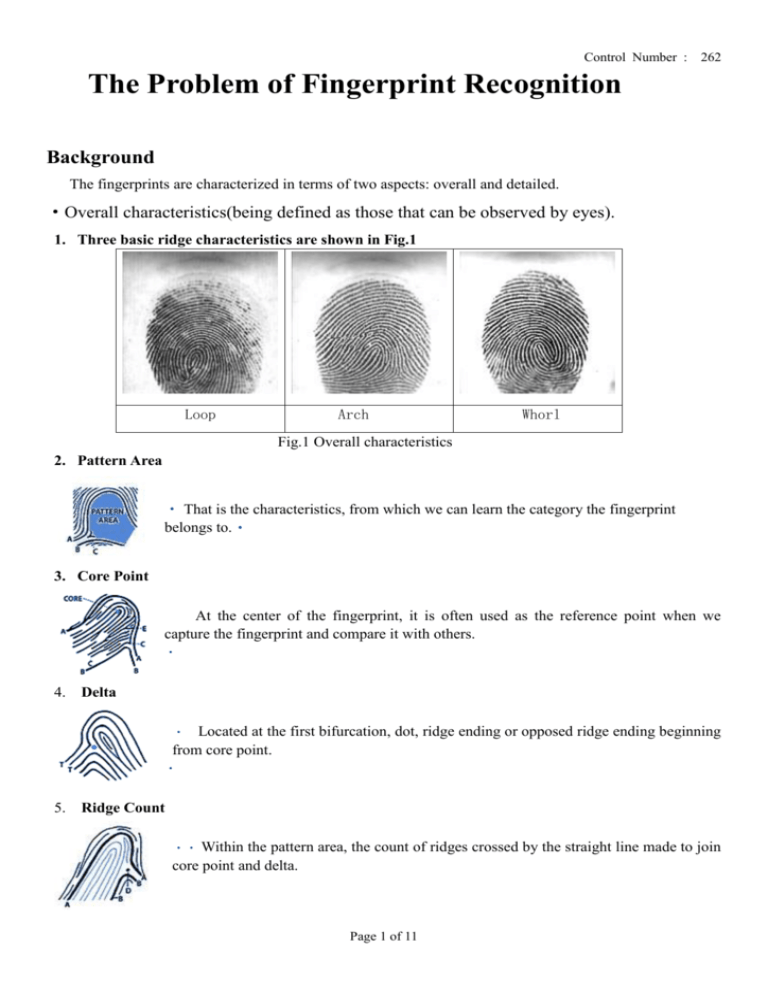
The fingerprints are characterized in terms of two aspects: overall and detailed.
·Overall characteristics(being defined as those that can be observed by eyes).
1. Three basic ridge characteristics are shown in Fig.1
Loop
Arch
Whorl
Fig.1 Overall characteristics
2. Pattern Area
That is the characteristics, from which we can learn the category the fingerprint
belongs to.
3. Core Point
At the center of the fingerprint, it is often used as the reference point when we
capture the fingerprint and compare it with others.
4.
Delta
Located at the first bifurcation, dot, ridge ending or opposed ridge ending beginning
from core point.
5.
Ridge Count
Within the pattern area, the count of ridges crossed by the straight line made to join
core point and delta.
Page 1 of 11
Control Number : 262
·Detailed
characteristics (details of fingerprints).
Minutiae points, which break the continuation and smoothing of ridge with the form of ending, bifurcation
or dot, are presented below.
1. Type
Ending ---- a ridge ends here.
Bifurcation---- a ridge changes into two or more here.
Ridge Divergence---- two parallel lines separate here.
Dot or Island ----a very short ridge which can be seen as a single point.
Enclosure---- a small circle formed as a ridge changes into two and assembles
one immediately.
Short Ridge---- a short ridge.
Orientation -- --direction the ridge trends to.
3. Curvature-- --the rate of change of ridge’s orientation.
4. Position-- --described by the Cartesian coordinate (x, y), it can be absolute, or relative.
2.
Assumptions
·The fingerprints we research are all from thumbs.
·The ridges on our thumb are equally distributed.
·Breadth between ridges is equal.
·Fingerprints are invariable all the life. Outer factors such as humidity, air bubble and the cleanness of air as
Page 2 of 11
Control Number : 262
well as the change of age can not change them.
·Fingerprints are extracted while the directions of thumbs are vertically upward and the directions agree
with the coordinate’s orientation we establish.
·The fingerprints extracted here are all integrated, not considering their mar as the result of injury.
Problem Analysis
From the Background section, we learn that minutiae offer the unique information for recognition. We can
extract the minutiae to change fingerprint image into minutiae image, based on which we establish a
minutia-coordinate model to digitize the image. So, if the fingerprint is unique for each person, the digitized
information can not be repeated. In other words, the degree of resemblance must be low. This offers
direction for our modeling and testing.
Model Design
·The minutiae
From the analysis, there are six kinds of minutiae which occupy different proportions in Fingerprint
Recognition. The data are shown in Table.1[6].
Table.1 Percentage and number of each minutia
Characteristics
Percentage (%)
Num
Ridge
68.2
238
Bifurcation
18.9
66
Orifice
1.1
4
Thorn
4.9
17
Cross
3.2
11
Bridge
3.7
13
From Table 1.we can see the proportion of the first two kinds of minutiae is about 87%, and the
proportion of the remaining four kinds of minutiae is so small that they can be ignored to simplify the
model. Among various algorithms detecting minutiae, the grads-vector algorithm gives the most accurate for
solving our problem, but puts high demands for sensors. To reduce the demands for hardware and the
complexity of algorithm, we adopt a modularized method.
First we use a template to search the location of a minutia and distinguish its category. As shown in Fig.2,
M stands for the point searched, are the neighboring points arranged clockwise, and each point presents a
pixel.
s3
s4
s5
Fig.2
s2
M
s6
s1
s8
s7
Template to capture minutiae
Page 3 of 11
Control Number : 262
where s i is defined as the value of BOOL, that is
1
si
0
if si is black
if si is white
Typical templates for ridge ending and bifurcation are given in Figs.3 and 4
Fig.3
From the Figs. above, let c s
Fig.4
7
k 0
s( k 1) s( k ) we obtain c s 2 , if M is a ridge ending, and c s 6 , if M is a
bifurcation.
·Modification
We ignore the last four kinds of minutiae in the analysis above, but the modularized method cannot meet this
requirement . In fact, the points the method searches involve many false minutiae which we want to discard.. Eight kinds of
false minutiae and their modifications are presented in Fig.5.
Fig.5
·The Coordinates
We use the core point as the origin to set up a Cartesian coordinate. As given in Fig.6, the minutiae’s
information can be represented by ( x, y, k ) , where ( x, y ) stands for the coordinates and k is the category.
Page 4 of 11
Control Number : 262
Fig.6
The coordinates of the minutiae
·Initial Analysis
Fingerprint’s characteristic consists of overall characteristics and detailed characteristics. While the former
normally remains unchanged in many fingerprints, the latter is different from each other. [Background]. A
fingerprint consists of about 40 ~ 50 minutiae, [3], from which we extract 10 minutiae with the shortest
distances from the origin to design our algorithm.
Let
p and Q be two concourses of points extracted from two different fingerprints. Then we have
P { {( x1p , y1p , k1p ), , ( x10p , y10p , k10p )}, where ( xip , y ip , k ip ) stands for three parameters of the i th point in
the
coordinates
of
x
and
y
,
and
the
minutia’s
category.
Similarly,
we
p:
have
Q {( x1q , y1q , k1q ), , ( x10q , y10q , k10q )} . Let the probability that xip xiq be 1 / a (a 1). Then the probability
that y ip y iq is also 1 / a(a 1). Among the minutiae adopted, the percentage ridge endings occupy is
68.2%
78.3% . And bifurcations occupy 1 78.3% 21.7% . Only when the minutiae in
18.9% 68.2%
p and
Q are both ridge endings or bifurcations, can we get k ip k iq . Thus the probability that k i k i
p
q
is
78.3% 78.3% 21.7% 21.7% 66.0% . From this we obtain that the probability that the i th points in
p and Q have exactly the same information is 12 66.0% , we obtain the probability when 10 minutiae
a
in
p absolutely agree with those in Q is
1 10
) (66.0%)10 a 20
(1)
2
a
From the equation above, we can see that N decreases sharply as a increases. Taking centimeter as the
unit, among the 10 minutiae with the shortest distances from the origin, the coordinates will not overflow
N (66.0%
the range [1,1] .[1]. If one digit after the decimal point are valid, the probability that there are two different
thumbs haveing the same fingerprint is M (66.0%)10 20 20 60 108 2 40 10. This value approaches
0 . In fact, if we extract 6 minutiae from each fingerprint, then the probability is 0.01 0 00 . This is sufficient
to show that the fingerprints are unique.
·Further Analysis
In the analysis above, we mainly use probability theory to tackle the problem, from which we know that
the number of minutiae chosen in one fingerprint is mainly determined by the parameter’s number of
minutiae and the digits after the decimal point of the parameter. The number of minutiae extracted is not
constant. If more parameters (such as the ridge’s orientation and curvature) or more digits (for instance, two
digits after the decimal point are valid) are adopted, the minutiae could be extracted less. But this makes a
high demand on hardware.
Page 5 of 11
Control Number : 262
From the initial analysis, we define the probability as
N (66.0%)10 a 2b
(2)
where b is the number of extracted minutiae, and b is a positive integer, b (2,50) . Supposing b remains
constant, and we study the relationship between N and a . We make b 5,6,7,,15 and get function
curves about N and a respectively. The curves can be shown as follows:
.
Function curves about N and a
Fig.7
Conclusions
In Fig.7, we find that among the curves the values of b decrease from inner to outer. That is the values of
b from the center to the outer curves correspond to 15 and 5 respectively.
From Fig.7, we learn that when N remains constant, the more minutiae we extracted, and the less precise
of each minutia’s value. While a remains constant---to require the same precision for each minutia’s value,
the more minutiae extracted, the lower rate of error exist.
Improvement
·The Function on the Degree of Resemblance.
Based on the initial analysis above, we attempt to explain why the fingerprint is unique by comparing the
fingerprints’ degree of resemblance. We set up a Cartesian coordinate for each fingerprint image in the
database from Appendix, and find out 10 minutiae with the shortest distances to the origin. Since the
category of minutiae only influence the results with a constant coefficient (for example, the " (66.0%)10 " in
the equation (2)). We discard the parameters of minutiae’s category to simplify the minutiae’s parameters as
coordinates of ( x, y ) , while constructing the resemblance function.
Matching Method
We compare different fingerprints with the 10 minutiae using two rules below:
1) Order the minutiae under the rules that the minutiae’s distance to the origin ranging from short to
long.
2) Compare the minutiae with changing from small to large. is defined in Fig.8.
Page 6 of 11
Control Number : 262
Fig.8
·Degree of Resemblance
Let b stand for the point selected in the coordinates. According to the matching method, if the distance
from b to another point b extracted from another fingerprint is no more than a certain range. We get(3)
as follows:
xb xb
'
xb
yb yb
'
or
yb
(3)
where is a certain small positive number, then we can say that the points b and b ' are resemble. Under
this condition, the distance has a normal distribution with standard deviation .So as long as 2 , that
is, the coordinates of b ' are within the range
xb 4.56% xb , yb 4.56% yb
as shown in Fig.9, the result
can meet our requirement.
Fig.9
Using the Markov-Distance function the distance between two fingerprints is defined by
10
[( xip xiq ) 2 ( y ip y iq ) 2 ]
( 4)
i 1
where ( xip , y ip ) and ( xiq , y iq ) are coordinates of minutiae from two distinct fingerprints, and i 1,2, 10 .
While computing, we use a pixel on a computer with the resolution of 1024 768 as unit.
Select 8 fingerprints’ images from database in Appendix as a concourse, which is defined as
A { A1 , A2 ,, A8 }, where Ai stands for the i th image. Then the minutiae’s information of Ai and A j
can be presented as
Page 7 of 11
Control Number : 262
Ai ( x ik , yik )
k 1,2,3...10
A j ( x jk , y jk )
We obtain the distance between the i th fingerprint and the j th as
S ij k 1 ( xik x jk ) 2 ( yik y jk ) 2
10
(5)
Now substitute the data of concourse A into equation (*) to derive the distances between the eight
fingerprints (as given in the appendix). Up till now, each fingerprint in the database has its distances with
others defined as
i ij
j 1,2. .8.
Let min min ij where j 1,2...8 . Further, let
10
Ti 4.56% xik y ik
k 0
2
2
( 6)
stands for the allowable error of distance. While computing, we enlarge Ti , let
10
Ti 10% xik y ik
k 0
2
2
(7 )
to make the computation convenient.
Compare each i min with Ti , as min represents the minimum distance between the fingerprints Ai and
other fingers and i min ij , if i min Ti , then the degree of resemblance between two fingerprints is very
low, which shows that the fingerprints cannot be repeated. The relationship between i min and Ti of the eight
fingerprints are given in Fig.10
Fig.10 Comparing i min with Ti
From the Fig.10, we can see that i min Ti , which fits well with what we obtain from the analysis above,
that is, for each person, the fingerprint is unique.
Page 8 of 11
Control Number : 262
·Testing
We enlarge the samples size to thirty, and express the relationship between i min and Ti in Fig.11 from
which we have the same conclusion as above.
Fig.11 Comparing i min with Ti
The conclusion is universal and representative because the samples are randomly adopted from the
database. Although we cannot obtain the fingerprint of every person on the earth, we still may conclude
from the existing data that min Ti is still correct with an increase in the sample size.
Comparison Between Fingerprint Recognition and Identification
·Evaluation
In our model, we use the parameters of several minutiae extracted to substitute the entire information of a
fingerprint. On one hand, this reduces the difficulty for dealing with information. As long as parameters are
adopted rationally, we can derive the results rapidly. This makes the algorithm very effective. On the other
hand, there are also some shortcomings:
. 1) While dealing with the fingerprint image, the information we obtain is limited, causing reduction
in precision.
2) Blurring and imperfection of the fingerprint’s image makes the data possessing low
precision,
impacting on the dependability of the result on the contrary, the DNA identification, as the data is external,
not obtained from the model, is based on very high precision and dependability. Take a fraction of DNA
sequence for example, as show in Fig.12.
Fig.12
At the locations of to base-pairs, the probability that each location adopt one base-pair from {A, G, C, T}
1
is . If it is compared with another fraction of DNA from another person, then the probability that the two
4
10
1
fractions are the same is . Since one chromosome contains 30 Billion base-pairs, according to the
4
Page 9 of 11
Control Number : 262
1
algorithm above, the probability that two chromosome of two persons with no pin are the same is
4
3109
,
this value would be smaller, if we consider all the chromosomes.
·Exceptions (Identical Twins)
From the analysis, DNA identification has a higher precision and dependability than using fingerprints,
but it encounters difficulty while dealing with identical twins. While the DNA from identical twins are the
same, the fingerprints are distinct. Thus, from this aspect, fingerprint has a relatively low degree of error
than using DNA identification.
Strengths and Weaknesses
·Strengths
1) While dealing with the fingerprint image, we establish a Cartesian coordinate for each fingerprint and
extract the minutiae, key factor for fingerprint recognition, as researched subjects. For further computing, we
digitize the minutiae, using its coordinates as the entire information. Simplicity and high efficiency is
sufficiently presented here.
2) To solve the model, we first use the probability theory, and then make further conclusions using the
function of resemblance.
3) The algorithm makes low demands on hardware.
·Weaknesses
1) Because of the limitation of the sample size, errors cannot be avoided.
2) When establish Cartesian coordinate for each image, we take the core point as the origin, ignoring the
possible error caused by the change of core point.
3) The precision of managing data is relatively not high.
4) In this model, we mainly research the key factor-minutiae, not considering the condition that the
fingerprint’s overall characteristics maybe different. For this reason, the results are not perfect.
References
[1] Control of Web Access Based on The Fingerprint Recognition Technology (in Chinese), Accessed February 7 2004
http://www.ahetc.gov.cn/cit/200109/05.doc
[2] Zhong yi fingerprints (in Chinese), Accessed February 7 2004
http://www.chinajoy1.com/TechDatum.htm
[3] Matching algorithm for fingerprints based on the diffused error (in Chinese), Accessed February 7 2004
http://nlpr-web.ia.ac.cn/english/irds/chinese/model.doc
[4] Fingerprint characteristics (in Chinese), Accessed February 7 2004
http://www.imagesoft.com.cn/htm/tec.htm
[5] Principle and technique of fingerprint recognition (in Chinese), Accessed February 7 2004
http://www.idsmartech.com/html/new01.htm
Page 10 of 11
Control Number : 262
[6] Yan Zhiwei. et.al. Forensics. China Inspection Press, 1997.
[7] Fingerprint identification system and its applications (in Chinese), Accessed February 8 2004
http://202.118.192.202:85/~kjqk/dnjsxx/dnjs99/dnjs9912/991203.htm
[8] Fingerprint identification based on the Morphology and configuration (in Chinese)
[9] Database of fingerprint samples(in Chinese), Accessed February 8 2004
http://202.118.192.202:85/~kjqk/jsjgcyyy/jsjg2002/0204pdf/020427.pdf
[10] FingerCell (in Chinese), Accessed February 8 2004
http://www.neurotechnologija.cn/download.html
[11] Matching algorithm for fingerprints based on the diffused error (in Chinese), Accessed February 8 2004
http://www.hotwinfiles.com/software_details.asp?r=4826#
[12] Matching algorithm for fingerprints based on the diffused error (in Chinese), Accessed February 8 2004
http://www.sinobiometrics.com/chinese/ppt/Haoying.pdf
[13] “DNA image” and Forensics (in Chinese), Accessed February 8 2004
http://bioscience.sjtu.edu.cn/General_Biology_Lab/biology/fingerprinting.htm
Page 11 of 11