B. In A, the encryption algorithm classified as monoalphabetic cipher
advertisement

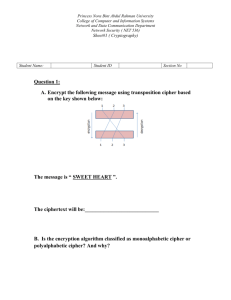
Princess Nora Bint Abdul Rahman University College of Computer and Information Systems Network and Data Communication Department Network Security ( NET 536) Sheet#1 ( Cryptography) Student Name: Student ID Section No Question 1: A. Encrypt the following message using transposition cipher based on the key shown below: The message is “ SWEET HEART ”. The ciphertext will be:____________________________ WESTHEAREZZT B. Is the encryption algorithm classified as monoalphabetic cipher or polyalphabetic cipher? And why? Polyalphabetic because 1:N Princess Nora Bint Abdul Rahman University College of Computer and Information Systems Network and Data Communication Department Network Security ( NET 536) Sheet#1 ( Cryptography) Question 2: A. Alice wants to encrypt a message to Bob by using the shift cipher algorithm “Caesar cipher” and the key= 20. The plaintext = “QUIZ”. ( Hint: you may need to use the table in previous question) Ciphertext=”KOCT” A 00 B 01 C 02 D 03 E 04 F 05 G 06 H 07 I 08 J 09 K 10 L 11 M 12 N 13 O 14 P 15 Q 16 R 17 S 18 T 19 U 20 V 21 W 22 X 23 Y 24 Z 25 B. In A, the encryption algorithm classified as monoalphabetic cipher or polyalphabetic cipher? And why? Monoalphabetic because each letter in the plain text replace by the same character in the ciphertext. Princess Nora Bint Abdul Rahman University College of Computer and Information Systems Network and Data Communication Department Network Security ( NET 536) Sheet#1 ( Cryptography) Question 3: a. In DES, if the M = 0000 2000 8000 0000 ( Hex), Find the IP(M). IP(M) Original M IP(M)=………………………………………………………………………………….. ( Hex) 0000 0000 1004 0000 b. In DEA, the S-Box3 given below, if b3= 110010, the output would be: S-Box 3 10 0 9 13 7 0 13 6 4 1 10 13 S3 =0001 14 9 9 0 6 3 8 6 3 4 15 9 15 6 3 8 5 10 0 7 1 2 11 4 13 8 1 15 12 5 2 14 7 14 12 3 11 12 5 11 4 11 10 5 2 15 14 2 8 1 7 12 Princess Nora Bint Abdul Rahman University College of Computer and Information Systems Network and Data Communication Department Network Security ( NET 536) Sheet#1 ( Cryptography) Question 5: A. Perform encryption using the RSA algorithm for the following word : Plaintext: “IF”. Where p=3; q=11; e=7; Suppose Alice sends this word to Bob by representing each alphabetic as an integer between 0 and 25 (A 0 …… Z25). Hint: Encrypt each number separately. C(I) = 2 =C C(F)=14=O A 00 B 01 C 02 D 03 E 04 F 05 G 06 H 07 I 08 J 09 K 10 L 11 M 12 N 13 O 14 P 15 Q 16 R 17 S 18 T 19 U 20 V 21 W 22 X 23 Y 24 Z 25 A. Using RSA algorithm, find the d, Where p=5; q=11; e=3. Decrypt the following word: “PRLJ” using RSA algorithm. Decrypt each character separately; then, write the plaintext that the receiver can read. ( Hint: you may need to use the table in previous question) N= 55 Q= 40 D=27 E.d mod Q =1 3 x 27 mod 80 =1 81 mod 80 =1 Plaintext= “FILE” GOOD LUCK