references - Academic Science
advertisement
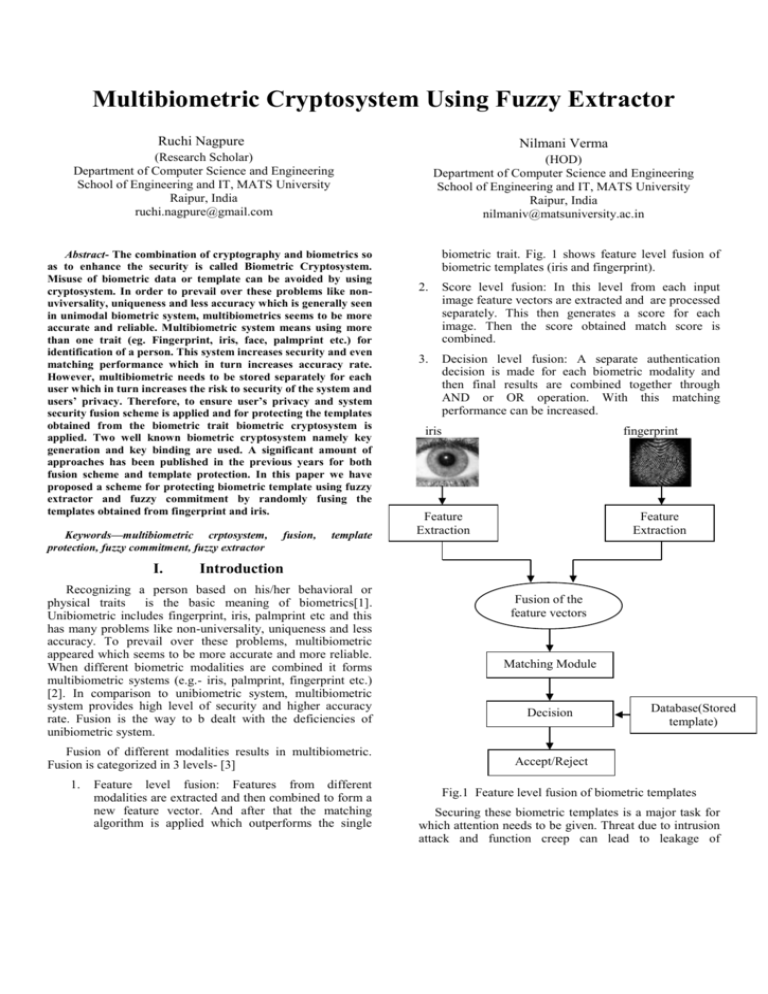
Multibiometric Cryptosystem Using Fuzzy Extractor Ruchi Nagpure Nilmani Verma (Research Scholar) Department of Computer Science and Engineering School of Engineering and IT, MATS University Raipur, India ruchi.nagpure@gmail.com (HOD) Department of Computer Science and Engineering School of Engineering and IT, MATS University Raipur, India nilmaniv@matsuniversity.ac.in Abstract- The combination of cryptography and biometrics so as to enhance the security is called Biometric Cryptosystem. Misuse of biometric data or template can be avoided by using cryptosystem. In order to prevail over these problems like nonuviversality, uniqueness and less accuracy which is generally seen in unimodal biometric system, multibiometrics seems to be more accurate and reliable. Multibiometric system means using more than one trait (eg. Fingerprint, iris, face, palmprint etc.) for identification of a person. This system increases security and even matching performance which in turn increases accuracy rate. However, multibiometric needs to be stored separately for each user which in turn increases the risk to security of the system and users’ privacy. Therefore, to ensure user’s privacy and system security fusion scheme is applied and for protecting the templates obtained from the biometric trait biometric cryptosystem is applied. Two well known biometric cryptosystem namely key generation and key binding are used. A significant amount of approaches has been published in the previous years for both fusion scheme and template protection. In this paper we have proposed a scheme for protecting biometric template using fuzzy extractor and fuzzy commitment by randomly fusing the templates obtained from fingerprint and iris. Keywords—multibiometric crptosystem, protection, fuzzy commitment, fuzzy extractor I. fusion, template biometric trait. Fig. 1 shows feature level fusion of biometric templates (iris and fingerprint). 2. Score level fusion: In this level from each input image feature vectors are extracted and are processed separately. This then generates a score for each image. Then the score obtained match score is combined. 3. Decision level fusion: A separate authentication decision is made for each biometric modality and then final results are combined together through AND or OR operation. With this matching performance can be increased. iris fingerprint Feature Extraction Feature Extraction Introduction Recognizing a person based on his/her behavioral or physical traits is the basic meaning of biometrics[1]. Unibiometric includes fingerprint, iris, palmprint etc and this has many problems like non-universality, uniqueness and less accuracy. To prevail over these problems, multibiometric appeared which seems to be more accurate and more reliable. When different biometric modalities are combined it forms multibiometric systems (e.g.- iris, palmprint, fingerprint etc.) [2]. In comparison to unibiometric system, multibiometric system provides high level of security and higher accuracy rate. Fusion is the way to b dealt with the deficiencies of unibiometric system. Matching Module Fusion of different modalities results in multibiometric. Fusion is categorized in 3 levels- [3] Accept/Reject 1. Feature level fusion: Features from different modalities are extracted and then combined to form a new feature vector. And after that the matching algorithm is applied which outperforms the single Fusion of the feature vectors Decision Database(Stored template) Fig.1 Feature level fusion of biometric templates Securing these biometric templates is a major task for which attention needs to be given. Threat due to intrusion attack and function creep can lead to leakage of information [4]. Hence, biometric cryptosystem which is combination of biometric & cryptography provides better key management & security. While designing a biometric cryptosystem security is the main challenge which has to be taken care [5]. For resolving the security purpose 3 frameworks are designed- fuzzy vault [6], fuzzy commitment [7], and fuzzy extractor [8]. In fuzzy commitment scheme a random key is generated which is of length L and is used to index a codeword c which has error tolerance. The hash value of the key is also stored. This codeword is then XORed with the template which results in a secure sketch. During authentication a biometric template is given as a input and a new codeword is formed and further key is generated. If the hash value of both the keys are identical, the person is authentic. In this the template is basically bit string. Fig. 2 shows fuzzy commitment scheme. In fuzzy vault, a polynomial is constructed and this generally secures the biometric features that are point set. Here security totally depends on the infeasibility of the polynomial reconstructions problem. In fuzzy extractor, two procedures are used namely secure sketch and fuzzy extractor. In secure sketch , a sketch is obtained when biometric is given as input. This sketch does not reveal much information about the biometric and in fuzzy extractor a random string R is extracted with any randomness and a public template is generated. During authentication this R is reconstructed with reproduce procedure and thus the template is protected. Basically template protection scheme is of two types namely biometric cryptosystem and feature transformation. For feature transformation biohashing is the example which comes under salting and salting is the classification of feature transformation. Biometric cryptosystem is again classified into Key binding and key generating systems. In both helper data is constructed. Therefore biometric cryptosystem can also be called as helper data methods. In key binding helper data is constructed with the help of random key and biometric template whereas in key generating helper data is constructed with the help of only biometric template. Key is generated rather than binding. Helper data is public that does not reveal much information about the biometric template. For key binding systems fuzzy commitment and fuzzy vault are the examples and for key generating fuzzy extractor is the example [16]. Fig 3 shows different template protection schemes. Codeword XOR Biometric Template Stored Database h(.) Sketch Hash value of key Fig. 2 shows fuzzy commitment scheme 1.1 Literature Review In [9], the author presented preprocessing of the fingerprint image which is called as image enhancement and from this how efficiently features can be extracted. Post processing is also done after minutiae extraction to validate the minutiae i.e. removing spurious minutiae (false minutiae) which is been calculated and after that matching is being performed. In [10], S. Prabhakar, A. K. Jain, and J. Wang presented a unimodal fingerprint verification and classification system. The proposed system, for the feature-extraction stage is based on feedback path. After that feature-refinement is performed so as to improve the matching performance. The Gabor filter is applied to the input image to improve its quality. In [11], iris detection is done. For finding the inner boundary, bisection method is used by the authors. To find collarette boundary histogram equalization is used. In [12], Y. Zhu, T. Tan, and Y. Wang proposed a system for identification of a person based on iris patterns. For extraction of features from iris multichannel gabor filtering is used which is based on texture analysis.. In [13], the authors have proposed a multimodal system taking features of fingerprint, palm print and hand geometry. Template Protection Feature Transformation Salting Noninvertible Transforms Biometric Cryptosystem Key binding Key generation Fig. 3 Different template protection schemes. These biometrics are taken from the identical image. Firstly fusion of fingerprint and palm print is performed at matching score level and then matching score fusion between multimodal system and unimodal system i.e. hand geometry is performed. In [14], the authors proposed a multimodal system combining finger print and iris. Decision is considered from each modality and then finally combined by “AND” operator. In [15], the authors proposed polar, surface and Cartesian folding transformations to generate cancellable finger print. In [17], author proposed a multimodal system which combines to form a binary string using fingerprint and face template as tempaltes. Further concatenation is performed to the binary strings and further fuzzy commitment scheme is applied. In [4], authors proposed a multibiometric cryptosystem that is based on feature level fusion which in turn generates a single secure sketch and for both binary string and point-set based representations practical implementation issues are considered. In [18], authors proposed a modular approach for multibiometric cryptosystem which takes two biometrics and from first biometric sketch is obtained along with the hash value of first biometric which is then used to secure second template. In [19], In this paper, the authors proposed to extract features of discriminating binary length-fixed from fingerprint images and combine them with error correction codes so that an effective fuzzy commitment scheme can be constructed. In [20], authors proposed an approach biometric templates or passwords are combined in a single secure sketch in cascaded manner. In [21], the authors proposed a methodology in which biometric template pass through cancellable transformation. Further decision is made by using individual classifiers and finally fusion is implemented at the decision level using any of unimodal and unialgorithm, unimodal and multialgorithm, multimodal and multialgorithm. This results that recognition task becomes more difficult and complex when cancellable biometrics are used. In [22], In this work the author proposed a generic feature level fusion based on iris and face of Bloom filter-based templates. The advantage of Bloom filter-based representations is that the biometric templates can be directly mapped to a set of features that are unique and that is suitable as input for cross-matching resistant cryptographic primitives. In [23], authors have proposed a hybrid template protection scheme which is carried out in 3 stages. Firstly feature level fusion is performed. In second stage random feature set is generated and in third stage template bit string is obtained. This ensures that revocable and diversified templates will be generated. In [5], authors have proposed an optional multibiometric that is based on fuzzy extractor. Fuzzy extractor extracts a stable codeword from biometric trait and a codeword set is formed. Secret share procedure generates a public template with the help of a random key. Fuzzy extractor has two procedures namely GEN and REP. Fuzzy extractor is responsible for the security. The rest of the paper is organized as follows- Section II provides brief introduction of cryptosystem. Section III provides the different methodologies used. Results are discussed in section IV. Conclusion is summarized in section V. II. Problem Definition Cryptosystem makes reference to the aggregation of cryptographic algorithms that is needed to implement a confidentiality and security service. Cryptosystem is basically used when there is a need to protect any data from the intruder or to save the data in terms of confidentiality . And it is often used when the concept of key generation is important. Biometric cryptosystems combine both cryptography and biometrics to provide better security so that the integrity and confidentiality both are maintained and take the advantage of both cryptograpy and biometric. So, biometric cryptosystem has both the advantages i.e. it provides higher accuracy rate as well as higher security. III. Proposed Framework Protection For Template We propose a framework for multibiometric cryptosystems with fusion that consists of three basic modules: (i) embedding algorithm, (ii) fusion module, and (iii) biometric cryptosystem. The generic framework of the proposed multibiometric cryptosystem is shown in fig 3. Biometric Template 1 Biometric 90 Biometric Template 2 Embedding algorithm Embedding algorithm Fusion Fuzzy commitment C1 Key (kc) C2 C3 Multibiometric Secure Sketch Database (Stored Template) Fig. 4 Proposed multibiometric cryptosystem The functionalities of the three modules are as follows: 1) Embedding algorithm : The embedding algorithm transforms a biometric feature representation into a new feature representation. In our implementation the output representation should be a binary string. In embedding algorithms conversions of the numbers to binary will be done. 2) Fusion module : To generate a fused template, the fusion module combines a set of homogeneous biometric features. As in the implementation only binary strings are considered therefore we use random permutation by using the function rand in MATLAB. 3) Biometric cryptosystem : During enrollment, a secure sketch is obtained using the fused feature vector in the biometric cryptosystem. During authentication, when given the biometric queries the biometric cryptosystem recovers. Fuzzy extractor is used to generate a codeword and this is done with the help of fuzzy extractors. Each of the above three modules play a critical role in determining the matching performance and security of the multibiometric cryptosystem. A. Methodology For Codeword Generation Fuzzy extractor is a biometric tool which is used to generate a codeword with the help of fuzzy commitment. This is generated with the help of a secure sketch. We have seen that the “fuzzy-commitment” construction of Juels and Wattenberg [7] based on error correcting codes can be viewed as a (nearly optimal) secure sketch. Then the results are applied to convert it into a nearly optimal fuzzy extractor. Hamming distance is used for the construction of fuzzy extractor. The output of the codeword extraction is the only helper data extraction. As this data is now shuffled and the intruder will not be able to detect whose data it is. Fuzzy extractor simply means designing a system which accepts randomness. In our implementation it accepts till 0.5. It is same in the commitment scheme. In this also scheme should be resilient to corruption values i.e. given any function with the input w then the should accept little variances if the input given at the time of verification i.e. w’ is close enough to w. IV. Result The proposed framework will give a satisfying result as compared to the fuzzy vault and fuzzy commitment scheme [4]. In [4], the biometric trait iris individually gives the result at GAR of 90% which is at 45 bits. For the same GAR the security is at 90 bits When face and fingerprint are involved. These results are for virtual database. For both fuzzy vault and fuzzy commitment virtual database proposed fusion gives the result of 99% of GAR. V. Conclusion The results that will be obtained by implementing the proposed method will gain higher accuracy rate and security. We have proposed a feature-level fusion framework for the design of multibiometric cryptosystems that simultaneously protects the multiple templates of a user using a single secure sketch. The feasibility of such a framework has been demonstrated using fuzzy extractor, which is a well-known biometric cryptosystem. We have also proposed random fusion for fusing biometric representations, and a mechanism to impose constraints such as minimum matching requirement for specific modalities in a multibiometric cryptosystem. decreases little. It will be seen that multibiometric cryptosystem is useful in increasing the accuracy rate. . REFERENCES [1] Ruchi Nagpure, Nilmani Verma, “Comparative Study on Biometric Template Protection Schemes” academic science 2015. [2] S.C. Dass, K. Nandakumar & A.K. Jain, Secure and Multimodal System. reliable [3] A. Ross, K. Nandakumar, and A.K. Jain, Handbook of Multibiometrics. New York: Springer, 2006. [4] Austin Hicklin, Brad Ulery, Craig Watson “A brief introduction to biometric fusion” 16 june 2006. [5] A. Nagar, A.K. Jain, K. Nandakumar “Multibiometric cryptosystems based on feature-level fusion” IEEE Transactions on Information Forensices and Security 7 (2012) 255–268. [6] Chi Chen, chaogang Wang, Iengfei Yang, Dongdai Lin, Song Wang, Jiankun Hu “Optional multibiometric cryptosystem based on fuzzy extractor”, Proceedings of IEEE 2014, 11th International Conference on Fuzzy Systems and Knowledge Discovery. 989-994. [7] A. Juels and M. Sudan, “A fuzzy vault scheme,” in Proc. IEEE Int. Symp. Information Theory, Lausanne, Switzerland, 2002, p. 408. [8] A. Juels and M. Wattenberg, “A fuzzy commitment scheme,” in Proc. Sixth ACM Conf. Computer and Communications Security, Singapore, Nov. 1999, pp. 28–36. [9] Y. Dodis, R. Ostrovsky, L. Reyzin, and A. Smith, Fuzzy Extractors: How to Generate Strong Keys from Biometrics and Other Noisy Data cryptology ePrint Archive, Tech. Rep. 235, Feb. 2006, A preliminary version of this work appeared in EUROCRYPT 2004. [10]Raymond Thai “Fingerprint Image enhancement and Minutiae Extraction” year 2003 School of Computer Science and Software Engineering, The University of Western Australia, 2003. [11] S. Prabhakar, A. K. Jain, and J.Wang, ―Minutiae verification and clas-sification,‖ presented at the Dept. Comput. Eng. Sci., Univ. Michigan State, East Lansing, MI, 1998. [12] H. Sung, J. Lim, J. Park, and Y. Lee. Iris recognition using collarette boundary localization. In 17th International Conference on PatternRecognition, volume 4, pages 857–860, 2004. [13] Y. Zhu, T. Tan, and Y. Wang, ―Biometric personaidentification on iris patterns,‖ in Proc. 15th Int. Conf. Pattern Recogn. 2000, vol. 2, pp. 805–808. [14] F. Yang, B.MA, “A new mixed mode biometrics information fusion based on fingerprint, hand geometry and palm print”. Proceedings 4th International IEEE Conf. Image Graph, 2007, pp- 689-693. [15] F. Besbes, H. Trichili, and B. Solaiman, “Multimodal biometric system based on Fingerprint identification and iris recognition” in proceedings 3rd International IEEE conf. Inf. Communication technology. ICITA 2008, pp-1-5. [16] N.K. Ratha, S.Chikkerur, J.H. Connell, R.M. Bolle, “Generating cancellable fingerprint templates”, IEEE transaction on paper analysis and machine intelligence 29, 2007. pp-561-572. [21] C. Fang, Q.Li, and C. Chang, “Secure sketch for multiple secrets” in proc. International Conference Applied Cryptography and Network Security, 2010. [17] A.K. Jain, K. Nandakumar, A. Nagar, “Biometric Template Security”. EURASIP journal on advances in signal processing, 2008. [22] Anne M.P. Canuto, F. Pintro, J.C. Xavier-jr., “Investigating fusion approaches in multibiometric cancellable recognition” Expert Systems with Applications, Elsevier, 2013. pp-1971-1980. [18] Y. sutcu, Q. Li, and N. Memon, “Secure biometric templates from fingerprint-face features” in Proc. CVPR Workshop Biometrics, june 2007. [23] Christian Rathgeb_, Marta Gomez-Barreroy, Christoph Busch_, Javier Galballyy and Julian Fierrez, “Towards Cancelable Multi Biometrics Based On Bloom Filters: A Case Study On Feature Level Fusion Of Face And Iris”. [19] S. Cimato, M. Gamassi, V. Piuri, R. Rassi, and F. Scotti, “Privacy-aware biometrics: Design and Implementation of a multimodal verification system” in proc. IEEE annual conference Computer Security Applications, 2008. [20] Peng Li, Xin Yang, Hua Qiao b, Kai Cao c, Eryun Liu c, Jie Tian “An effective biometric cryptosystem combining fingerprints with error correction codes”. Expert Systems with Applications, Elsevier, 2012, pp- 6562–6574. [24] Y. J. Chin, T.S. Ong, A.B.J. Teoh, K.O.M. Goh, “Integrated biometrics template protection technique based on fingerprint and palm print feature level fusion”. Expert Systems with Applications, Elsevier, 2014. pp-161-174.






![[CLICK HERE AND TYPE TITLE]](http://s3.studylib.net/store/data/006863514_1-b5a6a5a7ab3f658a62cd69b774b6606c-300x300.png)
