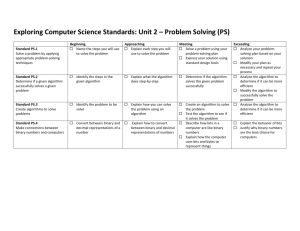
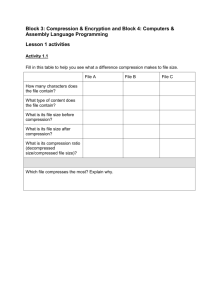
AS91371-lesson-plan-draft-v1-16Jan2012
advertisement

A Guide for Teaching Digital Technologies Achievement Standard AS91371 (2.44): Demonstrate understanding of advanced concepts from computer science Heidi Newton University of Canterbury Tim Bell tim.bell@canterbury.ac.nz University of Canterbury DRAFT v1 16 January 2012 1 This lesson plan has been prepared as a suggested way to teach this standard, but please be aware that it is in draft form, and we are sharing it in the hope that it gives ideas for teaching. However, it has no official status. You are welcome to modify it, and we encourage you to share new versions, or send suggestions (including minor corrections or clarifications) to tim.bell@canterbury.ac.nz This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 3.0 License. We encourage you to improve and share this document. It is licensed under a Creative Commons Attribution-Noncommercial-ShareAlike 3.0 License: You may use this document, alter it, and share new versions, as long as you retain the credits on this page, and license a new version under the identical terms. 2 Introduction This lesson plan explains one possible way that Digital Technologies Achievement Standard 2.44 can be taught and assessed. For this achievement standard, students need to demonstrate an understanding of advanced concepts in computer science, i.e. representations using bits, methods of encoding, and using heuristics to perform a usability evaluation. Note that not everything in this lesson plan needs to be taught. Options are given in some sections so that teachers and/or students can decide which topics are best for them. The main topics covered for bits and representations are: Binary numbers Representing text with bits (ASCII and Unicode) Representing colours with bits For this section of the achievement standard, students need to pick at least two different types of data and discuss at least two different representations for those data types. Therefore, we recommend that binary numbers are covered for all classes (numbers are a type of data), in addition to one other type of data. This could be either of the other two covered here (text or colours) or an alternative type that the teacher is knowledgeable about (some ideas are given at the end of the bits and representations section). If the colours activity is chosen, this can then be extended further in the compression section for encoding, how to do this is discussed in the compression section. Encoding is split into three sub sections; encryption, error control coding, and compression. For this section of the achievement standard, students need to know the basics of all three for achieved, and then be able to show a more in-depth understanding of an application of at least one of these three kinds of encoding for merit/excellence. Therefore, the basics of each of these three topics should be taught to all students, although only one of these topics needs to be covered in depth. Encryption and error control coding both have a simple activity suitable for the purpose of giving a basic introduction. We don’t provide a basic introduction for compression, although one of the more in depth activities can easily be simplified. How to do this is explained in that section. The examples used to introduce the basics of the encoding methods are: Encryption: Breaking Caesar Cipher Error Control Coding: The Parity Trick Compression: Basics of image or sound compression. For the more advanced understanding, the following options are given. Students/ teachers should either pick one of these topics, or pick an alternative one that the teacher is knowledgeable about. Encryption: Choosing an encryption system and evaluating it. [Note that this activity is not explained in detail in this lesson plan and is more complex than the other topics] Error Control Coding: International Standard Book Numbers (ISBN) Compression: Images, number of bits used [Recommended if colours were used for representations using bits] Compression: Images, JPEG, GIF, or another similar image compression system 3 Other compression systems such as those used for sound or lossless compression used for text documents are good alternatives that require little domain knowledge to understand, and can easily be adapted from the JPEG image compression activity. If the algorithm used for another real world error control coding system is known, then the ISBN activity can easily be adapted for that system. Ideas for other systems are given at the ends of the relevant sections. For Human Computer Interaction, students will need to choose a portable device or interface on a computer (a portable device is recommended) to evaluate using Nielson’s heuristics. We believe that this resource covers the requirements of the standard, but if you are interested in more ideas, a comprehensive list of resources for teaching these topics including alternative examples and approaches is available at http://nzacditt.org.nz/project/programming-and-cs This lesson plan uses grey boxes for material that is intended to guide teachers rather than be taught to students. These grey boxes explain the basics of what the concepts are, contain useful links to information and resources, and give extra advice on teaching some topics. Representing Data Using Bits Binary Numbers What are binary numbers? Binary numbers are simply numbers that use only the digits 0 and 1 to represent numbers, in comparison to decimal which uses the digits 0 – 9. All numbers that can be represented in decimal have a binary equivalent. The activity recommended for teaching the students binary numbers explains how this works. The words “binary digit” are often abbreviated to “bit” (binary digit). Why do we care about binary numbers? Computer scientists care about binary numbers a lot because EVERYTHING stored on a computer is stored using binary, and many things are measured on this basis e.g. 24-bit colour, 16-bit audio, 8-bit characters, 56-bit security, 10Mbit network connection, and so on. Understanding binary numbers helps students to understand the capacity and limitations of computers. Using thousands, millions, or even billions of these individual binary digits, very complicated data can be represented. This includes text files, colour, music, videos, and pictures. The actual physical storage doesn’t use the digits “0” and “1” to represent values but instead two different states such as whether or not light is reflected on a CD, or what the direction of magnetism is on a hard disk. Binary numbers in the achievement standard Binary numbers has requirements in the standard for achieved and merit. Binary numbers are also useful for understanding encoding, which is a later section that extends binary representations. Note 4 that this part of the achievement standard covers both binary numbers and binary representations in general. For achieved, students must: “describe ways in which different types of data can be represented using bits” For merit, students must; “compare and contrast different ways in which different types of data can be represented using bits and discuss the implications” Additional resources for binary numbers Cut-out “Binary Pianos” can be downloaded from the NZACDITT page for this topic and are referred to below. http://nzacditt.org.nz/resource/level-2-computer-science-concepts-representing-data-using-bits Alternatively, binary counting cards can be printed and cut out from the Unplugged page. http://csunplugged.org/sites/default/files/activity_pdfs_full/unplugged-01-binary_numbers.pdf Web links for Binary Numbers These are suitable for background reading for teachers and/ or students if further explanations are required. http://en.wikipedia.org/wiki/Bit – Bit (Binary Digit); only read the first two paragraphs and then the section on representations. Note that the use of the word representations is NOT the same as in this standard. The standard refers to the representing of complex data such as images, sound, and numbers, whereas this article is referring to how computers can physically represent a “bit” . Both concepts however are important for students to understand. http://en.wikipedia.org/wiki/Binary_numeral_system– Binary number system; this page is only useful if you are looking at how to do math in binary, or if you need a further explanation on converting from binary to decimal. Advice for teachers Many students will have never encountered binary numbers before this lesson, so will need to start from the basics. It is possible however that they encountered binary numbers before in Year 11 computer science even though it is not a topic covered by the standards at that level, or they may have encountered it in a math class where it may have been referred to as “base 2”. Prior experience should determine how much time needs to be spent on this lesson. For ideas on teaching binary numbers, there are many videos on the Unplugged page. http://csunplugged.org/binary-numbers Like most of the unplugged videos, these are intended for the teacher rather than for being shown to a class. 5 Introducing the binary number system (Recommended for all classes) A good way to introduce the concept of binary numbers is largely based on the following Unplugged activity. While this activity is aimed at students younger than year 12, it can easily be adapted to work with year 12. http://csunplugged.org/binary-numbers However, instead of using binary cards, a “binary piano” can be used (instructions on how to obtain binary pianos are above). These instructions assume binary pianos as they are more appropriate for year 12. Start by giving each student a binary piano. Get them to cut and fold the binary piano following the instructions on it. Once the students have their binary pianos ready, briefly explain that they’re going to learn how decimal numbers can be represented using binary, which instead of using 10 digits, only uses 2 digits. Much like the explanation for the binary cards that the Unplugged page recommends, start by getting the students to show numbers such as “13” (8+4+1), “47” (32+8+4+2+1), and “130” (128+2) by getting a total adding up to those numbers (the actual numbers don’t matter, these are just examples) and reading out what the binary for the numbers is. Students should come up with a workable approach for finding these sums, but if they need a hint, start with the largest number (256 on the piano) and ask “Do you need that one?”, then asking the question for 128, 64 and so on. This is explained further in the CS Unplugged activity. Also say a few numbers in binary (or write them on the whiteboard) such as “111000011” (451 in decimal) or “100000100” (260 in decimal) and ask the students to calculate the decimal number using their piano. Do this until they are confident with converting binary to decimal and decimal to binary using their piano. Once they understand those basics, move onto the following questions. Ask the students the questions, but get them to give the answers (the answers given here are intended only for the teacher’s usage). Before asking these first questions, tell the students to try “counting” from 1 to 31 using their piano. Question: How often does the first key (with the value +1) get changed when counting? Answer: Every time. Question: Why? Answer: Because it is the only key that adds an odd number, it is needed for every odd number. [And is not needed for even numbers] Question: What value would a 10th piano key have? What is the general rule you used to determine this? Answer: 512. The general rule is that each key has a value twice as large as the previous one. Question: What is the smallest number that can be represented using the piano? Answer: 0, if all the keys are set to 0. Initially, students might say 1. If they say this, just ask them if they are sure about that until they say 0. Question: What is the highest number that can be represented using the piano? Answer: 511 (From counting, students may have noticed the pattern that having a row of “1” keys is one less than the next key; if there was a 10th key it would have been 512, so the 6 total is one less than that; the goal of the next few questions is to help students discover this rule for themselves.) Question: How many different numbers can be represented using the piano? Answer: 512 (The numbers 0 – 511) Question: How many more keys do we need to represent twice as many numbers? Answer: Students will probably either say “9” or “twice as many” or “1”. The correct answer is actually 1. If they say “9” or “twice as many”, ask them to confirm it by adding up numbers and they should realise. Question: If there were only the right most 8 keys (so pretending the “+256” key doesn’t exist), what is the highest number that could be represented? Answer: 255 Note: This is particularly significant, as computers most often store bits in groups of 8, called a byte. Thus one byte can store up to the number 255. Question: And if there were 7 keys, what is the highest number that could be represented? Answer: 127 Question: What rule could be used to determine what the highest number that can be represented is without adding numbers? Answer: The number on the next key if there was more key minus one (or twice the highest key minus one). Note: For the following questions, tell the students to write down their answers so they remember them and can answer the last question Question: What is the binary representation for “29”? Answer: 11101 Question: What is the binary representation for “58” (which is double 29)? Answer: 111010 Question: What is the binary representation for “116” (which is double 58)? Answer: 1110100 Question: What is the binary representation for “232” (which is double 116)? Answer: 11101000 Question: Can you see a binary rule for doubling a number? Answer: Insert a 0 to the right of the number. Explanation for Students: Just like multiplying a decimal number by 10 can be done by simply adding a 0 to the right of the number, multiplying a binary number by 2 can be done by adding a 0 to the right of the number. This is because binary is base 2, and decimal is base 10. At this point, the students should have a good enough understanding of binary numbers to move onto how other types of data can also be represented using bits. As an alternative, the original Unplugged activity using the cards can be used. The questions given above can easily be adapted to the cards. We do however recommend the pianos for high school students, largely for practical reasons. Students can keep their piano after this lesson for whenever they need to use binary numbers throughout working towards this achievement standard, such as in the representations lesson which 7 follows. The problem with cards is that it is several pieces of paper to try and not lose, time needs to be spent laying them out each time they are used, and they require ensuring the number of dots on each card has been correctly memorised (or counting them every time!). In addition, it is far easier to quickly (and correctly) write down a binary number from a piano than it is from cards, as the piano has it directly whereas cards require converting “black” and “white” to “0” and “1”, giving an opportunity for accidental copying mistakes. Eventually students are likely to be able to convert numbers without using these devices by simulating the process themselves, at which point they will have a good understanding of binary representation, and can apply it to the practical situations described below. As a finishing note to this introductory lesson on binary numbers… From xkcd1, “1 to 10” - http://xkcd.com/953/ And the roll-over text for the comic is “If you get an 11/100 on a CS test, but you claim it should be counted as a 'C', they'll probably decide you deserve the upgrade”. Students might like to see if they can figure out why this is so2. Optional Extras: Decimal and binary expansions Depending on the interests of the teacher, this is an optional extension of binary numbers that could be taught to the class. Note that as this is an extension topic, it is not required for the achievement standard. In math, students will have learnt about representing decimal numbers using expanded form. As an example, the expanded form of the decimal number 70,145 would be as follows. 70145 = 7*104 + 0*103 + 1*102 + 4*101 + 5*100 The digits before the multiplication signs are the digits of the original decimal number, each is multiplied by a power of 10 because 10 is the base of a decimal number, and the powers they are raised to range from 0 to one less than the number of digits, going from right to left. 1 A popular web comic, particularly enjoyed by computer scientists. Binary “11” is 3 in decimal, and binary “100” is 4 in decimal. This gives 3/4 = 75%, which is the amount for a C in (some) US schools. 2 8 This same idea can be used to represent binary numbers, and solving the equation will give the decimal number the binary number represents. As an example, consider the binary number 1100011011. 1*29 + 1*28 + 0*27 + 0*26 + 0*25 + 1*24 + 1*23 + 0*22 + 1*21 + 1*20 = 795 The digits before the multiplication sign are the digits of the original binary number, just like before, seeing as binary is base 2 the numbers are multiplied by powers of 2, and the powers are determined in the same way as before. Solving the equation reveals that this binary number is 795 in decimal. As multiplying by 1 gives the same number as that being multiplied by, and multiplying by 0 gives 0, binary expansions simplify to a sum of powers of 2. The above example would be equal to: 29 + 28 +0 +0 +0 +24 +23 +0 +21 +20 = 795 512 + 256 + 0 + 0 + 0 + 16 + 8 + 0 + 2 + 1 = 795 Which is exactly how the binary cards or binary pianos represent binary numbers. Remember that when an equation contains powers, multiplication, and addition, the order of calculations is important. Calculate all the powers first, then the multiplications, and then finally the additions. And remember that any number (except 0) to the power of 0 is 1. Using binary numbers in the achievement standard (Recommended for all classes) Binary numbers can be used as one of the two types of data that students discuss representations of. This can be done by considering different sizes for binary numbers (e.g. 8 bits and 16 bits) and looking at limitations and benefits of having different sizes. The following exercise explores this in the context of storing variables in a computer program, which will be more meaningful if students are using a programming language as part of their other work. Often when computers store variables (values that can be changed by a computer program), they have to put aside a certain amount of bytes they are able to use to represent that number. Typically integers are stored in 32 bits (although allowing for negative numbers, this is effectively 31 bits); in some languages you can declare a “short integer” which might be 16 bits. The number of bytes to use to store a number has to be sensibly chosen; if it is too big it can waste memory (especially if there are a lot of values being stored) or slow the computer down unnecessarily when it carries out calculations with the number . If it is too small there is a risk that it won’t be able to fit some input data in the allocated space. Even more importantly, being familiar with the properties of simple binary integers will help students to understand the tradeoffs that need to be made in other types of data, such as characters, images and sound. Students can do the following warm-up exercise for their reports. Note: This only considers whole numbers (positive integers including zero). You do not have to understand how numbers with decimal places are represented on a computer for this activity. The following ideas may help you if you are having trouble thinking of examples due to this limitation. o Money can be stored as the number of cents rather than dollars, in order to remove the decimal point (in fact, this is usually done on computers, because storing decimal places can introduce inaccuracies). 9 o Weights can be stored in grams or even milligrams in order to remove decimal points while keeping a high level of accuracy. Same ideas apply to other measurements. Assume a computer is able to store numbers of the following sizes; 1 byte, 2 bytes and 4 bytes. You have to decide what size is suitable for different kinds of data the computer might need to be store. Start off by working out what range of numbers each of these sizes is able to store. Think of at least 2 different things you or somebody else might store on a computer using each of these 3 sizes [think widely; related to people, money, what your school might store in its databases, what widely used websites such as Facebook or Trademe store, customer numbers, census data, unique numbers for digital devices on the internet etc.]. This should give you at least 6 examples in total of different things the computer might need to store. Explain assumptions that you made about the maximum number possible for each of your choices. Are your assumptions guaranteed to always be true? Gives specific examples of values that these numbers might be and show both the binary and decimal representations for them. In what situations might none of these 3 choices be suitable? What are some examples? What limitations are there in only being able to store numbers using these 3 sizes? [1, 2, and 4 bytes]. Consider your answer to the above question and any other problems you can think of. A related exercise would be to have students explore what the largest integer is that they can store in their favourite programming language or spreadsheet. This could be done by writing a program/formula that keeps doubling a number, and running it until an error/overflow occurs. Some languages have different lengths of integers available (int, longint etc.). Others don’t give an error message when the number gets too big, but just store wrong values. Others, like Excel and Scratch, reduce the accuracy of a number when it gets too big, but they still overflow eventually. Representing Text Using Bits Note: This section on representing text using bits are one of the options for the second data type for representations. Only one of this section, the next section (Representing Colours Using Bits), or an alternative topic decided by the teacher needs to be taught. How Unicode and ASCII work Text, also known as strings, is made up of a number of individual characters. Each unique character has a specific representation using bits, and these are put together to represent an entire text or string. Two common character representations used are ASCII and Unicode. The first representation, ASCII, uses 7 bits for each character. Students can find information about ASCII on Wikipedia. http://en.wikipedia.org/wiki/ASCII Because computers work with whole numbers of bytes (which are 8 bits), an ASCII character usually takes up 8 bits of space. The students can look at a table such as the following to see what the binary 10 representations for each character are. As a quick exercise, the students could look up each letter of their name so they can write their name in binary (in general, using personalised examples like this is a good way for students to show an understanding of the concept, since it is unlikely to be copied from a textbook or web page). Note that this only shows 7 bit binary numbers. To be technically correct, each letter should have a 0 before it. The string can be stored without separators between each character, as the computer knows that each character is exactly 8 bits long. http://en.wikipedia.org/wiki/ASCII#ASCII_printable_characters. It is important for the students to understand the following points about ASCII. That while in the (standard) version of ASCII, each character is represented using 7 bits, in practice the computer will use 8 bits for each character (1 byte), as computers store data using a full number of bytes. That the extended version of ASCII uses all 8 bits to allow for 128 extra characters to be displayable that weren’t available in the original ASCII. The first 128 characters in extended ASCII are the same as the original, as it is an extension rather than an alternative representation. The original “wasted” 1 bit in the byte required for each character is used, making this extension easily possible. Leading 0’s are stored. If they weren’t, each character wouldn’t be 1 byte, and the computer would be confused about where each character started and ended. Numbers in ASCII use different representations to normal numbers. Numbers in ASCII are treated as text with each digit being one character, and these are not able to be used for calculations. Most programming languages will however be able to convert numbers in ASCII format into numbers in a numerical format. The second representation, Unicode, uses 16 bits (2 bytes) for each character. Information about Unicode can again be found on Wikipedia. Students should largely be able to transfer their understanding of ASCII over to understanding Unicode. http://en.wikipedia.org/wiki/Unicode Using ASCII and Unicode as Examples for the Achievement Standard Students can include the following in their report for the achievement standard. (Some care needs to be taken that the report isn’t just a paraphrase of standard documents about these topics; using personalised examples will help here.) How many different characters are used in the 5-bit code used in the CS Unplugged exercises (modem exercise at http://csunplugged.org/modem, or on page 8 of the handout for http://csunplugged.org/binary-numbers)? How do ASCII codes compare with the 5-bit codes above? What is better and what is worse about each system? (Note that 5 bit codes are no longer used in practice). Demonstrate the difference with personalised examples such as representing your name using each method. How many different characters can be represented with 16 bits (as Unicode uses)? Compare the representation of your name in both Unicode and ASCII How many times more values is this than what ASCII is able to represent? What languages could be represented using Unicode but not ASCII? 11 What devices and software that you use support ASCII? Which support Unicode? Which support both? Show the representation of an Asian word (e.g. a personally chosen word in Chinese that has significance to you). Discuss the advantages and disadvantages of both ASCII and Unicode using the examples you derived above to guide the discussion. Representing Colours Using Bits Note: This section on representing colours using bits are one of the options for the second data type for representations. Only one of this section, the previous section (Representing Text Using Bits), or an alternative topic decided by the teacher needs to be taught. Hexadecimal Numbers What are Hexadecimal Numbers? Hexadecimal numbers are widely used in Computer Science as a shorthand way to write binary numbers. They represent binary in a more human readable format, but the reason for teaching them here is their relationship to colour codes, which will be explained in the next section. Like decimal is base 10, and binary is base 2, hexadecimal is base 16. Because exactly 16 numbers can be represented using 4 bits, hexadecimal can be used as a way to simplify binary numbers making them easier to read. As hexadecimal is base 16, it has 16 different digits. These are usually represented as the standard digits 0 – 9 and then the letters A – F to make up the digits 10 – 15. Advice for teachers Note that the base 4 number system (quaternary) that is initially mentioned is not important for students to know. The only reason it is taught is as a stepping stone into hexadecimal. Once the students know hexadecimal they can be told that they only need to know hexadecimal, but not this simple base 4 system (but of course it’s best not to tell them before or they may choose to not listen!) Start by asking the students following questions. A whiteboard should be handy for this activity. Question: How many different 2 bit combinations are there? (i.e., how many 2 digits long binary numbers there are?) Answer: They should answer 4; “00”, “01”, “10”, and “11”. Question: Ask them what those 4 numbers are in decimal Answer: They should answer “0”, “1”, “2”, and “3”. [Write an 8 digit binary number on the board (11001101 is the example that will be used here for the rest of the questions).] Question: Breaking the 8 bits into 4 pairs, can you rewrite this number using the digits “0”, “1”, “2”, and “3” so that it is only 4 digits long? Answer: The students should realise that they can replace each of the 4 combinations with its corresponding digit from 0 – 3. The example given above would have an answer of 12 “3031”. Ask them to explain how they arrived at their answer. A good way to do it is to draw a line between every pair of bits in the binary number that is being converted into this new form. Question: Write a 7 binary digit number such as “1001111” on the board and ask the students to translate that into this new form. Answer: This number is “1|00|11|11”, which would be “1033”. Assume a 0 has been put on the front of the leftmost piece (making it “01” rather than “1”). This addresses a problem they are likely to run into, when there isn’t an even number of digits, so one digit won’t have a pair. Confusion may result from which end this “single” digit is on. Ask the students how a decimal number such as 195 could be turned into a 4 digit number while keeping the same value. They should (hopefully!) realise that the answer is to put a 0 to the left making it 0195, and then that they can apply this same idea to a binary number with an odd number of digits to make it possible to label it using this convention. Once it has an even number of bits, it won’t matter which end was labelled from. [Write one or two more binary numbers on the board for the students to convert like this, depending on how confident they were with the previous exercises.] Question: Write a few numbers on the board of this form, such as 2113, 0130, and 0000 and ask the students to convert them to binary. Answer: The answers are 10|01|01|11, 00|01|11|00, and 00|00|00|00. Note that the bars between the digits aren’t necessary, although are good for showing working. The way the students should do this is to take each digit and replace it with the binary equivalent. Question: Binary is a base 2 system, and decimal is a base 10 system. So which base is this new number system? Answer: 4 Explain to the students that they’ve just shown you a way of representing binary numbers that takes less space to write down and is easier to remember, but is far easier to convert into binary than decimal is to convert into binary. This is the base 4 number system, known as quaternary. Just like “deci” means 10 and “bi” means 2, “quarter” means 4. http://en.wikipedia.org/wiki/Quaternary_numeral_system Once the students are able to convert binary from quaternary and quaternary to binary confidently, the idea of hexadecimal can be introduced. Explain to the students that hexadecimal is an even more compact way of representing binary numbers that can easily be converted to and from binary. Explain to the students that hexadecimal is base 16. Make sure that they understand this means that 16 different digits are required to represent hexadecimal. Explain that the digits used are 0 – 9 for the first 10, and then the letters A – F for the remaining 6, making a total of 16 digits. Ask the students the following questions (they should be able to figure these out fairly quickly from their knowledge of binary and quaternary, but it is probably best to ask them rather than tell them to ensure that they do understand). Question: How many bits are required to represent 16 different numbers? Answer: 4 bits (Which will represent the numbers 0 – 15) Question: Using these 16 digits how could the binary number 100011001010 be written? Answer: It can be broken into chunks of 4 bits, i.e 1000|1100|1010, which can then 13 essentially be converted into decimal. If the chunk is equal to 0 – 9, this is straightforward, but if the chunk is between 9 and 15, the corresponding letters will need to be used. The answer to this particular example is 8CA. The students should do this in 2 stages; breaking the number into chunks of 4 and then determining the hexadecimal digit for each chunk. Explanation: Tell the students that a “chunk” of 4 digits is actually called a nibble (or nybble) in computer science terms. (A nibble is half the number of bits of a byte, which shouldn’t be too hard to remember given a somewhat obvious analogy). Hexadecimal essentially assigns a single digit to each nibble, and seeing as there are 16 different possible nibbles, hexadecimal requires 16 digits to represent all possible nibbles. Note that hexadecimal is just a quick way to write large binary numbers; computers still store the value in binary, but it makes it quicker for humans to read the numbers. For example, network devices have a unique “MAC address” [http://en.wikipedia.org/wiki/MAC_address] which is at least 48 bits long; rather than write down the 48 bits for a device, people write them in Hexadecimal using just 12 digits. Task: Get the students to make a quick conversion chart of each possible nibble (there are 16 of them) and its corresponding hexadecimal digit. This shouldn’t take them to long. This conversion chart will be useful to them, as converting 4 bit binary numbers into their corresponding hexadecimal digit can take a bit of practice to be able to do without thinking about it. Note that 0 would be 0000, 1 would be 0001, etc, A is equal to decimal 10 which would be binary 1010, B is equal to decimal 11 which would be binary 1011, up to F which is equal to decimal 15, which would be binary 1111. Wikipedia has useful information on the hexadecimal number system if further explanation is required. http://en.wikipedia.org/wiki/Hexadecimal Colour codes (Hexadecimal notation) Colours are often represented using a hexadecimal notation. Students may have encountered this when selecting colours for a webpage they were writing in HTML. Briefly explain the following points to the students before moving onto the activity that follows. Each pixel on a computer screen shows a colour by adjusting the amount of red, green, and blue light coming from it. With varying proportions of each light colour, all colours can be displayed. Because of this, it makes sense for a computer to store colours using three values; one displaying the amount of red, one displaying the amount of green, and one displaying the amount of blue in the colour. This is exactly what hexadecimal colour codes represent (the students may or may not have seen these; it doesn’t matter if they haven’t). Tell the students to go to the following webpage, which allows them to experiment with mixing red, green, and blue to make various colours (or they might use a similar “colour picker” in software that they are familiar with). The amount of each colour is represented by an integer between 0 and 255. (Students should know the significance of the number “255”!) http://www.cosc.canterbury.ac.nz/mukundan/cogr/RGB.html. It will probably seem quite magical that every colour can be obtained with various combinations of 14 these 3 basic colours of light. Among allowing the students to experiment with this tool themselves, the following questions can be asked to get them thinking about how various colours are represented using this system. [These first questions are largely to illustrate the way to obtain shades of grey as this might not immediately be obvious. Ask the students this after they’ve had awhile to experiment] Question: How can black be represented? Answer: Setting all colours to 0 Question: How can white be represented? Answer: Setting all colours to 255 Question: How can colours on the grey scale be represented? Answer: By having all three values the same [These next questions are to get students thinking about how colours can be represented by a computer] Question: What is significant about the number range that each colour can be set to? Answer: The students should easily be able to see that each of the 3 colours can be set to a value from 0 – 255. It is the range of numbers that can be represented using 8 bits (1 byte) Question: So how many colours can be represented in total using this system? Answer: The students should answer something like 24 bits, or perhaps 16,777,216 (224 or 256*256*256) which is the exact number in decimal. Make sure they realise that it is 24 bits because each colour has 8 bits, and the number of bits for each colour should be added to get the total. Don’t forget that “0” counts as a colour as well. Question: How many bytes is this per colour? Answer: 1 Question: And how many nibbles per colour? Answer: 2 Question: So how could you represent a colour using hexadecimal? Answer: By using 2 hexadecimal digits for the amount of each of red, blue, and green. Explain that this is the system that hexadecimal colour codes use. Internally, the computer would store the colour using binary (in this example, 24 bits), although the codes are written using hexadecimal as this is more human readable (only 6 digits are required). Using Hexadecimal Colour Codes for the Achievement Standard Tell the students to use the colour mixer to make a shade of a colour they like. As not all colours will work well with the following activity, ensure students don’t pick colours that fit into any of the following categories. A good way to check the colours all the students have chosen would be to record the three numbers of the colour for each student. Avoid colours that have two or more of the bars set to “0” or “255” Avoid colours that have all three bars set to values outside of the range 10 – 245 Avoid the exact same colour (same numbers) as anybody else in the class (as each student’s work needs to be personalised) Once the students have chosen a colour (and all colours have been verified as suitable for the standard), give the students the following instructions. Note that students should retain all working 15 as they will need to include this in their reports as evidence that they understand the binary number system (for achieved). At the end of the activity, a brief example is included as a guide to clear up any possible confusion. Take a screenshot of your colour being displayed in the colour mixer and save it For each of the three decimal colour values, convert them into binary and then into hexadecimal. Once you think you have the three hexadecimal values correct, put them into the format <red hexadecimal value><green hexadecimal value><blue hexadecimal value>, so that you have a 6 digit hexadecimal number, e.g. the decimal numbers 175 red, 1 green and 181 blue would convert to 1010 1111 0000 0001 1011 0101 in binary, which is AF01B5 in hexadecimal. Enter the hexadecimal into the specified box on the following page and click “calculate”. The colour should be the same. http://drpeterjones.com/colorcalc/ The next task is to see what happens when the number of bits used to represent colours is reduced. To do this, go back to the binary of the colour that was obtained while converting from decimal to hexadecimal. Choose at least four different numbers of bits to experiment with for each colour. Each colour should be allocated the same number of bits (so the total number of bits must be a multiple of three), and all choices should be 7 or fewer bits per colour (so smaller than the original number of bits). One of the choices should be 1 or 2 bits per colour. As an example, students might choose “8 bits”, “7 bits”, “4 bits”, “2 bits” and “1 bits”. To see the effect of reducing the number of bits used to represent a colour, we need to remove some of the accuracy from the numbers (a worked example of this activity is given below). In order to convert the colour to the chosen numbers of bits, replace the right-most bits of each colour with zeros. So if for example the colour had to be converted to 6 bits, replace the rightmost 2 bits of each colour with 0’s (if they aren’t already 0’s). i.e 10001001 would become 10001000. Convert the resulting binary separately into decimal (so you have 3 numbers like at the start) and into the merged hexadecimal form. Enter the results into the corresponding tools introduced previously in this exercise. Both should be giving the same colour, although not necessarily the same colour as you chose at the start of the activity. Take screenshots of the colour in each of the tools and save them. Note: While it is possible to complete the exercise by only converting into decimal OR hexadecimal, it is strongly recommended to do both conversions for double checking and for practice of converting numbers to different number systems. By now, you should have at least 5 different colours (including the original) that were all obtained by removing bits from the original colour. Assuming a suitable choice was made, the first colour should be noticeably different from the last colour, and it is likely the colours in between will be as well. If the difference between the first and last colour is barely noticeable and your smallest chosen value was 2 or more bits per colour, add an extra size using 1 bit per colour as this is likely to cause a very noticeable difference as long as the original colour choice was suitable. If a computer was to store these colour values, it would not need to store the 0’s at the end beyond the number of bits as it would already know those values will always be 0’s. Write an explanation of your results, discussing how the colour quality changes as the number of bits used to represent it is reduced. Consider how many different colours can be 16 represented using each of the sizes you chose, what kinds of colours would be more or less affected by removing bits, and what impact this will have on images that are saved using these numbers of colours (include both the advantages and disadvantages). Assume that an image is represented by a red, green, blue value for each pixel in it, and assume that a colour doesn’t have to use a full number of bytes (as opposed to 7 bit ASCII that wastes the 8th bit in a byte). For example, if a pixel uses 12 bits, then two pixels are typically stored in 3 bytes (24 bits) instead of using two bytes for each pixel. Your report for the standard should contain screenshots showing your colours in the tools, all working required to convert from decimal <-> binary <-> hexadecimal, and your explanation of the results. An example of this activity Showing this example to the students is not recommended. Instead it should be used as an example for the teacher to ensure she or he understands what the activity requires. Students would likely show more working than what is shown here. Discussion question answers are not included as they may give too much guidance to students should they see them. The colour I chose is the shade of purple represented by red=186, green=0, and blue=151. <Show screen shot of the colour> This converts into binary as follows. Red = 186 = 10111010 <Students should show working of this calculation> Green = 0 = 00000000 <Students should show working of this calculation> Blue = 151 = 10010111 <Students should show working of this calculation> The values can then be converted into hexadecimal using the technique discussed earlier. <Students should include the nibble -> hexadecimal chart they made earlier in their report> Red = 1011|1010 = BA Green = 0000|0000 = 00 Blue = 1001|0111 = 97 So my colour in hexadecimal is BA0097 <Show screenshot of colour in second tool> I have decided to see how the colour appears when only 6 bits are used to represent each colour. This requires removing the last 2 bits of each colour representation Red = 10111000 Green = 00000000 Blue = 10010100 These values converted into decimal give Red = 184 <Students should show working of this calculation> Green = 0 <Students should show working of this calculation> Blue = 148 <Students should show working of this calculation> 17 And these values converted into hexadecimal give Red = B8 <Students should show working of this calculation> Green = 00 <Students should show working of this calculation> Blue = 94 Which means my colour in hexadecimal is now B80094 <Show screenshot showing this colour> <Show a few more different number of bits for the colour> <Discussion should now follow here> Optional extras or alternatives for the achievement standard. Depending on the interests and strengths of students and teachers, similar contrasting representations can be discussed using: Sound – compare the quality and size of 16-bit and 8-bit WAV files Variable types in programming languages – compare the relative merits of integers and long integers if you are using a programming language that distinguishes these IP addresses – discuss the relative costs and benefits of IPv4 and IPv6 MAC addresses – compare the range of values that can be represented by MAC-48, EUI-48, and EUI-64 The address spaces of 16-bit, 32-bit and 64-bit computers MIDI representation of music – consider the number of bits used for notes, programme changes and channels, explain the limitations these impose and how they can be worked around. As long as at least two different representations (usually two different numbers of bits) for the chosen data type are considered, and the results are compared and contrasted as required by the standard, any of these topics are suitable to cover instead of text or colour. We do recommend however that the binary numbers activity is covered by all classes as it is unlikely to take very long, and binary numbers are a very important concept for the students to grasp. 18 Encoding What is encoding? In this context, encoding means changing the representation of a file so that it is more suitable for the purpose it is being used for, usually by introducing a compromise in an area that isn’t a big concern for the user. For example, an mp3 coded file takes a lot less space than a Wav file, but the sound is lower quality. There are three common kinds of encoding, and each is covered by this standard: Compression: making a file smaller to save space (e.g. jpeg, mp3, zip) Encryption: changing the representation of a file so that it can’t be read unless you have the password (key) Error control: adding extra information to data so that it is possible to detect and even correct errors if the data is corrupted (e.g. a check digit on a credit card number so that simple typing errors can be detected quickly, or parity bits in a RAID disk setup so that if a disk drive fails its contents can be recreated from the rest of the data. Encoding in the Achievement Standard Encoding has requirements in the standard for achieved, merit, and excellence. All requirements consider three different types of encoding; compression, error control coding, and encryption. To fulfil the requirement for achieved, students will need to have a basic understanding of each of these three encoding types, and to fulfil the requirement for merit and excellence, they will need to investigate an application of at least one of them. To cover this, the lesson plan recommends a simple activity for each of the three encoding topics, and then gives a few ideas for applications that can be investigated for merit and excellence. For achieved, students must; “Describe the concept of encoding information using compression coding, error control coding, and encryption; and the typical uses of encoded information” For merit, students must; “Discuss how a widely used technology is enabled by one or more of compression coding, error control coding, and encryption” For excellence, students must; “Evaluate a widely used system for compression coding, error control coding, or encryption” Advice to Teachers It is good to cover the section on binary representation before covering encoding. Not all the material in this section needs to be taught, so if there is limited time available, some of the applications of encoding can be skipped out, as only one real world application is required for the achievement standard. 19 For background reading on this topic, the book Nine Algorithms That Changed the Future: The Ingenious Ideas That Drive Today's Computers by John MacCormick includes examples of all three coding methods (Cryptography, Error-Correcting Codes, and Data Compression) as three of the nine algorithms. It’s written for non-expert readers, and although it doesn’t match the topics in this plan exactly, it gives a broad and approachable view of these areas, as well as explaining why they are important. Encryption What is Encryption? Encryption is a form of encoding that involves storing a message in a different way so that if anybody reads the message that is encrypted, they will not be able to understand what it says. Why do we care about Encryption? Encryption is important in the digital world that we live in, as information sent through the internet (such as web browsing, banking or credit card information, or other person information) is vulnerable to being read by eavesdroppers. Encryption prevents unauthorised people from being able to do this. Everybody should have a basic understanding of encryption rather than relying on security experts, as not everything is encrypted that should be, and not all encryption is as effective as is necessary. An example of insufficient encryption relevant to many people is router wireless keys. Many routers by default use WEP, which is very easily attacked (students could choose to investigate this for their application in encoding for merit/excellence) Encryption in the Achievement Standard Encryption is one of the three encoding topics in the standard. Students should have a basic understanding of encryption, along with a more in-depth understanding of an application of at least one of encryption, error control, and compression. See the box on encoding in general for further information on how this relates to the achievement standard. The activities on Caesar cipher are recommended for giving the students a basic overview of encryption. The section of breaking substitution ciphers is not necessary, although is potentially fun for students, and will reinforce the concepts. Additional Resources for Encryption There is a terminology sheet. This should be given to students at the start of the second section Note for Teachers While encryption is a very interesting topic, it is more complicated than the others to focus on in the achievement standard. For this reason, only the basics are covered, and ideas are given for possible applications for merit and excellence, but are not explained in this document. For most classes, an 20 application of error control coding or compression instead will be easier to work on for merit/ excellence. Caesar cipher and breaking substitution ciphers is insufficient for merit and excellence in the achievement standard as they are not used in real world, as required by the standard. Introducing Encryption with Caesar Cipher (Recommended for all classes) A good way to introduce encryption is with an example. In order to do this, a message encoded with Caesar Cipher will be required. The students will not need to use their computers for this exercise. Note that a Caesar Cipher is not a good encryption method, but it is an excellent example for introducing the main terminology and issues surrounding encryption. Either the Caesar cipher example below can be used, or another example can be generated by using http://web.forret.com/tools/rot13.asp. Make sure to remember the key (rotation) you used to encrypt the message. “DRO BOCMEO WSCCSYX GSVV ECO K ROVSMYZDOB, KBBSFSXQ KD XYYX DYWYBBYG. LO BOKNI DY LBOKU YED KC CYYX KC IYE ROKB DRBOO LVKCDC YX K GRSCDVO. S'VV LO GOKBSXQ K BON KBWLKXN.” This message has been encrypted with a key (rotation) of 10. This means that every letter in the original message has been replaced with the letter 10 places forward in the alphabet. If the end of the alphabet is reached, it wraps back around to the start of the alphabet. Some tips on creating a good message for this activity Type the message entirely in capitals to prevent confusion about case Include the words “A” and/or “I” at least once in the message (these will be good clues for attacking the code) Include words that contain apostrophes to give more clues Include common 2 or 3 letter words such as “and”, “the” or “it”, and try and include them more than once in the message. Write the message on the whiteboard or show it on a projector, and ask the students what it says. Don’t tell the class yet what Caesar cipher is, or even that the message is using Caesar cipher. Depending on the class, they might start trying to figure it out, or they might just say it is too hard. If they say it is too hard, use the following questions to encourage them to have a class discussion and figure it out. Possible answers that the class should come up with are given in italics below each question. [While pointing at a one letter word in the encrypted message] What letters could this one letter word be? In English, “I” and “A” are the only common one letter words, so one letter words in the message are likely to be these. 21 Are all letters in the English alphabet equally frequent? Which are the most common letters? This page might also be helpful if unsure or if a disagreement results from this question, but note that there are exceptions to every rule – for fun students could look at the novel “Gadsby” (http://en.wikipedia.org/wiki/Gadsby_%28novel%29), which doesn’t contain a single letter “e”! http://en.wikipedia.org/wiki/Letter_frequency#Relative_frequencies_of_letters_in_the_Engli sh_language How can letter frequencies be used to determine what this message is? Letters that appear the most frequently in the encrypted message are likely to correspond to the most frequent letters in the English alphabet. [While pointing at an apostrophe in the message] What word could this be? They should consider common contractions in English, and if the word is a longish word with an apostrophe before the last letter, the last letter is likely to be “S”. If the apostrophe is at the end of the word, the last letter is definitely “S”. Look at the two and three letter words. What might they be? Are any words repeated more than once in the message? Depends on the actual message of course, although they should be considering common two or three letter words in English. Avoid giving the students too much information and instead just focus on asking them questions that will point them towards a solution. Each student should have a pen and paper in front of them for this activity so that they can experiment and write down ideas and observations. A good approach is to double space the message, and start filling in the decoded version on either the line above or the line below each line of the cipher. This should be done on both the whiteboard version and the individual versions on the students’ own pieces of paper. As students figure out letters and agree on them, put them on the whiteboard version in each place the letter occurs. A bit of trial and error may be necessary. Note that the students are unlikely to and unexpected to notice the rotation pattern of Caesar cipher at this stage, so will not be able to take advantage of it. Don’t worry about this, just leave them to figure out what each letter is one by one. Once the students have figured out the message, carry on to the next section. Using the Caesar Cipher Example to Illustrate Terminology (Recommended for all classes) The terminology used in encryption can be introduced using the activity in the previous section as a basis. Give the students the handout on “big words in encryption”. Explain the following concepts and terminology to the students (you can use these words in the class exercises to reinforce their meaning). All the terminology can be found on the handout. The original message you gave them is in a form known as cipher text. The English message they managed to obtain (the original message) is called the plain text. The way that the message has been encrypted is called Caesar cipher Caesar Cipher works by using a rotation, i.e., replacing each letter in the plain text with the letter a certain number of places forwards (or backwards) in the alphabet The number of places forward in the alphabet to replace each letter with is the same for each letter, and is known as the key. 22 Now ask the students what the key was for the example that was used. Ask them to justify why. If they are unsure, go over the information in the last two bullet points in the above list. The way they should figure it out is by looking at a letter in the plain text and its corresponding letter in the cipher text and counting how many letters are between them. For example, if “A” in the plain text was “J” in the cipher text, the number of letters would be nine. They should double check with a few other letters to ensure they are correct. Write another example (one or two words is okay this time, use the web page provided above) on the whiteboard, tell the students what the key that was used to encrypt the message is, and ask them to use the key and the encrypted text to obtain the plain text. This should be straightforward, and requires subtracting the number of letter places rather than adding. Once the students have figured out the second message using the key, finish by explaining a few more concepts. As they have just discovered for themselves, the key for a piece of cipher text can be used to easily recover the plain text. The process of converting a piece of plain text to a piece of cipher text that can easily be converted back to plain text using a key is called encryption. Caesar cipher is an encryption algorithm; i.e. an algorithm that changes a piece of plain text into cipher text using a key. There are many other encryption algorithms. Caesar cipher is a substitution cipher that substitutes each of the 26 letters in the alphabet with a different letter. The process of determining the plain text from the cipher text WITHOUT using the key is called attacking (This is what the students did in the first activity!) Attacking Simple Encryption Algorithms (Optional) Note that while this activity is optional due to being unnecessary for the standard, it is recommended for the fact that it is a very interesting and enjoyable topic, and reinforces the concepts. This activity builds on the first activity, where the students were introduced to the idea of attacking encrypted messages to recover the plain text. Start by asking the students what methods they could use to attack an encrypted message that they know is in Caesar cipher. The following bullet points are the answers they should come up with. As students get each idea, tell them the proper term used for the attack. This is partially revision from the first activity. Give them clues if they are unsure on any. Trying all the keys as there are only 25 of them [This is known as a brute force attack]. Ask them what would happen if a key of 26 was used. They should answer that the plain text would be the same as the cipher text, so wouldn’t be encrypted. Also ask them what would happen if a key of 33 was used. They should answer that it would be the same as using a key of seven, because of the wrapping around. Looking at the frequency of each letter in the cipher text [Frequency analysis attack] Looking for patterns in the cipher text [Pattern Analysis attack]. 23 Knowing the plain text and using that to calculate the key – this might seem pointless since you already know the text, but if someone is using the same key (password) for multiple encodings, you might be able to force them to send a known message and use that to work out what the key is for other messages; a related attack was used during WWII, where the allies knew of common phrases (“cribs”) such as “nothing to report” or “Heil Hitler” that could be expected to be found in a message http://www.cs4fn.org/history/bombe.php. [This is an example of a known plain text attack] Caesar cipher isn’t the only example of a substitution cipher. As it is too easy to attack it (there are only 25 possible keys, and only one character needs to be correctly decrypted to get the key), more complex substitution ciphers will be used instead for this next activity. The basic idea is still the same; each of the 26 letters in the alphabet has been replaced with one of the other 26 letters. The difference is that the key to decrypt is more complex, as it is basically a list of all 26 letters and their substitutes. Students don’t need to understand how to decrypt these ciphers using the key, only how to attack them to get the plain text without using the key. The tutorial at http://www.cryptograms.org/tutorial.php contains ways of attacking substitution ciphers using pattern and frequency analysis techniques. The webpage is easy to understand, and very interesting. Pick a few to tell the students about (whichever seem the most interesting to you as the teacher), and then give them the link so they can read the rest. This should be an extension on the attack the students did in the first activity. Frequency analysis is a common technique. This is a tool that can count the number of times each letter appears in a piece of text. http://rumkin.com/tools/cipher/frequency.php Information on the most frequent letters in English can be found on Wikipedia. http://en.wikipedia.org/wiki/Letter_frequency#Relative_frequencies_of_letters_in_the_English_lan guage Briefly show the students the tool and the Wikipedia page and give them the links. These techniques can then be applied in the game at http://www.cryptograms.org/play.php. All the puzzles are substitution ciphers. The students can do this individually or in pairs on the computers. The tutorial and frequency analysis tool should help. Give the students as much time as possible for as long as they are interested to solve these puzzles. The standard requires students to “Describe the concept of encoding information using compression coding, error control coding, and encryption”. Writing up their process with the above exercises (e.g. a statistical attack on a substitution cipher created by a classmate) would be an good way to show that they have worked with the concepts and understand the terminology. Real world applications of encryption For merit and excellence in the encoding section of the achievement standard, students might like to look at how well the following perform (the main issues with encryption will be the time taken and how hard the codes are to break. PGP, DES, AES, or methods used for HTTPS could be explored. For example, students might try encoding some files or email using PGP or derivative software, and comment on the extra effort 24 needed to use the applications, and the strength of the encryption (e.g. any known attacks or weaknesses); or they might explore where HTTPS is used by looking for online sites that they use where the URL has “https” instead of “http”, and look at the settings available in their web browser. Programming Exercises for Encryption These are not necessary for AS91371 (2.44), although may be good for improving understanding, or for linking to AS91372 (2.45)/ AS91373 (2.46). Students keen on programming can try writing a program able to code and decode messages in Caesar cipher (of a given rotation/key), including a brute force attack which shows the results of all 25 decoding. Also, instead of using the online frequency analyser, it is possible to ask the students to program their own. This is a good programming exercise for practicing the usage of string manipulation (breaking the string that needs to be analysed into the separate characters that make it up), arrays, conditional statements, loops, and meaningful/ tidy output. As an extension, students might like to make their program produce output that can easily be pasted into a spreadsheet, and then they can use this for making a graph showing the frequency of each letter, which is an interesting spreadsheet exercise. Error Control Coding What is error control coding? Error control coding is widely used on digital systems to check that data hasn’t been corrupted. Error control coding includes the processes of both detecting errors and correcting errors. Some systems are able to both detect and correct errors, others are only able to detect them. Why do we care about error control coding? If errors weren’t detected then a physical failure in data storage would mean that people just have errors in their files without knowing. It is error control coding that enables a computer to say that a file is corrupt/unreadable. The main applications that students are likely to encounter are: Storage (disks, flash drives, CD’s, etc.) where a physical problem like a scratch on a CD needs to be detected; otherwise the computer would read incorrect data from the storage and simply give the user the wrong data values, perhaps giving the wrong numbers in a spreadsheet, the wrong text in a report, or loading a program that does the wrong thing. Transmission (email, web pages, downloads, text messages etc.) where the receiver needs to be sure that the data received was the same as what was sent Check digits in places like credit card numbers and bar codes, which can be used to detect most typing/scanning errors; if these numbers were read in without detecting errors then funds might be taken from the wrong account, or the wrong product would be charged to the customer Error control coding in the achievement standard 25 Error control coding is one of the three encoding topics in the standard. Students should have a basic understanding of error control coding, along with a more in-depth understanding of an application of at least one of encryption, error control, and compression. See the box on encoding in general for further information on how this relates to the achievement standard. The parity magic trick is recommended for giving students a basic overview of error control coding. ISBN is an application of error control coding that students could use for merit/ excellence. Further applications are likely to be added in future versions of this lesson plan. Resources for error control coding - Big words terminology sheets - Parity magic trick cards (one set between every two or three students) - Error control examples spreadsheets. Introducing error control coding with a magic trick (Recommended for all classes) A good way to introduce error control coding is with an Unplugged activity which uses an error control coding technique called parity for a “magic” trick: http://csunplugged.org/error-detection. Follow the instructions given on the Unplugged page. This can be demonstrated with double sided magnetic cards on a whiteboard, although these are hard to source. As an alternative, a set of parity magic trick cards can be used, or any cards or objects with two distinct sides. Do a demonstration for the class laying the cards out on a table, and get them all to stand around watching. It is important to sound very casual when saying “I’m going to make it a bit harder by adding an extra row and column”. Practice the trick before class, as it won’t work if the extra “bits” are incorrect. Advice for teachers Students sometimes have a bit of fun trying to “derail” this activity. Two things they might try to do are to say that the person guessing the flipped card was incorrect when they were right, or try and flip more than one card! If the students say the guesser is wrong about what card was flipped, quickly double check and say that your magical powers are telling you that you are definitely correct. Make sure to sound confident, and the students will probably give up and admit that it was the correct card. To encourage the volunteer to flip only one card, ask the class “Has one card been flipped”. The tone of the response will usually let you know if your instructions have been followed. The Unplugged activity explains how to detect if more than one card has been flipped. Once students have seen the trick a few times, ask them the following questions. Don’t give them the answers; they should be able to figure them out given enough time to think. Question: Does anybody know how I knew which card was flipped without memorising all the cards? Answer: Students will typically suggest that you’ve memorised the cards, or are using a 26 binary pattern. Some may have seen the trick before; others may notice that the number of cards in each row is even, which is a starting point for the next question. Question: What do you notice about the number of cards in each row and column? Answer: The answer is that there is an even number of white and black cards in each row and column. However, it is more than likely that the example in front of them has 2 and 4 black and white cards in each row and column. The only other possibility for both to be even numbers is 6 and 0 in some rows/ columns, which is less likely because students are told to lay out the 5*5 grid randomly and don’t perceive entire rows or columns of white and black as “random” (and if the card choices are truly random, it is statistically less likely) . As a result, students will probably say that each row and column has 2 and 4 black and white cards. If they say this, guide them towards the idea of having an even number in each row and column. Explain to the students that they have been fooled, and that the extra row and column of cards was actually to make it so that there was an even number of black and white cards in each row. Question: How can I make sure there’s an even number in each row even though most of the cards were chosen by the volunteer? Answer: You only need one extra card to change from odd to even Question: So what happened when a card was flipped? Answer: The row and column the card was in then had an odd number of blacks and whites Question: So how did I know which was flipped? Answer: It was the card in the row and column with an odd number of blacks and white. Remove the “extra bits” from the grid leaving the original 5*5. Ask the students what colour card should be in each of the places and put the cards back as they get them right. After that, ask the students if they think they could identify which card was flipped. Choose a volunteer who said they could and get them to turn the other way while somebody else flips a card (at this point, the teacher should be watching to make sure only one card is flipped as the students may be tempted to flip more than one card). Once the card is flipped, get them to identify which card. If they’re having trouble, remind them to check the rows first for one that has an odd number of each colour and then the columns, and the card that was flipped is the one at the intersection of the row and column (if it is on a whiteboard, you can circle the row and column, and the flipped bit becomes obvious). Explain to the students that this is a technique called parity used by computers to detect AND correct errors. Detecting errors is called error detection and correcting errors is called error correction. Parity is therefore an example of error control coding, where extra redundant information has been added in order to allow errors to be detected and corrected. Tell the students to go in twos or threes and practice the trick a few times by themselves until they are confident with it. Students can use this parity trick for their report for 2.44 to show a basic understanding of error control coding for achieved. This can be done by either getting a friend to take photos of them doing the trick with somebody else (the student who is writing the report should take a turn at both adding the extra bits AND detecting which bit has been flipped, this may require two separate grids to be laid out) or by drawing diagrams illustrating how the parity trick works. In addition to the 27 demonstration/ illustrations, students should describe why error control coding techniques such as parity are useful. This report will be personalised because there are 33,554,432 different ways to choose the 25 random cards, so we wouldn’t expect two submissions to have the same layout! A real world error detection system – ISBN (International Standard Book Number) This exercise provides a good example of error detection in practice. A similar system is used for credit card and bank account numbers, but experimenting with these may lead to ethical issues! While this activity is interesting and useful for understanding error control, it is not essential if an application of compression or encryption is going to be used for merit and excellence. Materials required for this lesson Before this lesson, each student should be told to bring at least one book that has an ISBN (International Standard Book Number) on the back of it. The ISBN can usually be found on the back of a book, near or on its barcode, and says “ISBN” before the number. Books from home, text books from another class, or books from the library are fine. Ideally a range of different books in the class is wanted, so it is probably best to avoid using any text books for this class as their book. Every book has a unique ISBN that is used as an identifier for that book. A book’s ISBN is used in situations such as ordering a book online. Explain to the students that just like the parity trick uses extra bits to make it possible to detect and correct errors, the ISBN on the back of the book they brought also has extra information for this purpose. Most of the digits of the ISBN are the actual book identifier, but the last digit is a check digit that is used to ensure that an entered book number is correct. While ISBN’s error control system is able to detect errors, it cannot correct them. It is mainly used to give an error message if someone types in or scans an ISBN incorrectly. Note that there are two types of ISBN number, 10digit and 13-digit. The longer ones were introduced in 2007, so most recent books will use the longer system. The details of the checksum calculation can be found at http://en.wikipedia.org/wiki/Isbn. Calculating the check digit is fairly simple and can be done by hand using simple arithmetic, but it is a good exercise for students to develop a spreadsheet or program to do the calculation. The spreadsheet supplied with this lesson plan contains an ISBN checker; if your students are studying spreadsheets they should construct their own rather than just use the one supplied, as this will give them a better understanding of the system. The Unplugged activity for the magic parity trick contains an explanation of how the 10-digit system works (starting on page 4 of the pdf for the activity, page 34 of the actual Unplugged book). Show an example of using the spreadsheet to check an ISBN and then either give each student a copy of the spreadsheet (not recommended), get them to make their own spreadsheet, or get them to write a program able to check book numbers (could potentially be combined with another assessment item or be preparation for one). Students should try the spreadsheet/program on their own book’s number, and then try the book numbers of the students sitting near them to make sure that all books give a correct check sum (if entered correctly into a correct spread sheet/ program, they will). If the students have written the spreadsheet/ program themselves, then they should try a few different books to test it. 28 After trying correct ISBN’s, students should start experimenting to find out what typing errors will and will not be detected by the error control used by ISBN. Using ISBN in 2.44 for merit and excellence in encoding For the standard, ISBN can be used as an example for all of achieved, merit, and excellence. Students should be able to apply the algorithm to check a book number, experiment with it to discover what errors are and are not detected, and be able to evaluate and discuss how effective ISBN is. To successfully do this, students should consider the following points (no answers provided, as it is potentially open ended, and students need to figure this out for themselves). The approximate level of each point is given, although this is only a rough guide. Students should consider all the points and explain what they did to arrive at their answers. It is recommended to include screen shots of examples of using the spread sheet and input tried. It is easy to personalise this activity by choosing a unique book as their example. [Achieved] What are error control, error detection, and error correction? [Achieved] Why is error control used in systems? [Merit] Why is error control (error detection) used in ISBN? [Merit] How does ISBN detect errors? (Note: this does not include understanding the math behind it, just the fact that there is an algorithm and some redundant data) [Merit/ Excellence] What is the probability of a randomly entered number giving a correct checksum? (this could either be calculated, or they could enter a whole lot of random values and see how many give the correct checksum) [Merit/ Excellence] What kinds of errors are likely to be common when typing in an ISBN? The following are typical, although students shouldn’t feel restricted by this list: o Getting 1 digit wrong o Swapping 2 adjacent digits o Reversing 3 adjacent digits o Adding a digit somewhere in the number o Leaving out a digit o Getting multiple digits wrong [Merit/ Excellence] Which of these errors will always be detected because they give an incorrect check sum? (They should try variations of the above errors on their own ISBN, and see which ones go undetected. Documenting these results will provide good evidence of understanding the concepts.) [Merit/ Excellence] What kinds of errors will sometimes result in a correct checksum? (And thus possibly go undetected). [Excellence] Is it acceptable that some errors will go undetected? Consider which errors are common and which are not, and the probabilities of undetected errors. Understanding the math behind how this error control system works is NOT required for the standard, and is an advanced topic. It is sufficient to use the provided spread sheet, writing a program or own spreadsheet is optional. Note that a similar system is used for credit card and bank account numbers; for example, if an account number for a payment is mistyped then there is a very high chance that the bank will detect 29 the error without even looking up if the account exists. The answers to the above questions apply to such situations (i.e. what are the chances I’ll accidentally make a payment to the wrong person?) but doing experiments with live banking systems is likely to get undesired attention, so we recommend leaving the understanding at a theoretical level! If students have covered all this in their report, along with simple explanations and/ or examples of encryption and compression (just to an achieved level), they should have done sufficient work for excellence in the encoding section of the achievement standard. Students will NOT need to cover merit/ excellence for compression or encryption if they have done this. Compression What is compression? Wikipedia: “In computer science and information theory, data compression is the process of encoding information using fewer bits than the original representation would use.” http://en.wikipedia.org/wiki/Data_compression. The types of data that can be compressed include text, sound (music), images, and videos. While compression decreases file size, it can take time to compress data (and sometimes the data needs to be uncompressed before being used) and/or reduce the quality of the data (i.e. music might not sound as good). Why do we care about compression? The smaller a file is, the more data we can store on a hard disk, mobile device or online system. Also, it will download faster. For example, JPEG photo files are compressed to 10 or 20 times smaller than a raw bit map image; this means a camera can hold many more photos, and web pages with photos will load 10 to 20 times faster. Compression in the Achievement Standard Compression is one of the three encoding topics in the standard. Students should have a basic understanding compression, along with a more in-depth understanding of an application of at least one of encryption, error control, and compression. See the box on encoding in general for further information on how this relates to the achievement standard. The standard doesn’t require that students know how compression works (although some methods are fairly easy to understand), but that students can see the value of compression. This largely involves identifying where it is used, how much smaller the files are (this can be done by experiments), and possibly how much time is needed to compress and decompress the files. Briefly investigating the JPEG method is a good way of covering achieved. A few other image compression examples are given for possible applications for merit/ excellence, although it isn’t too hard to adapt an alternative system for this. There are several approaches to compression (different methods are used for images, audio, video, and general purpose files). We recommend choosing one to focus on in-depth if the students are to 30 do an application of compression for merit/ excellence in the achievement standard. The other topics can be briefly looked at or just skipped. Compression of Images What is compression of images? Two common approaches to image compression that are looked at in this lesson are using a smaller number of bits to represent each colour (e.g. 24-bit colour, 256 colour, and 16 colour file formats) and the JPEG image compression system. The first simply uses fewer bits to represent each pixel in the image, meaning that the number of unique colours that can be represented is reduced, and the second uses more complex methods of reducing the file size, that the students don’t need to understand but should be able to observe and describe the effects of. Note for teachers This topic carries on from the work students did on how colours are represented using bits. If the teacher and students enjoyed looking at colours for bits and representations, then doing compression of images is strongly recommended. In the students’ reports, there will be some overlap between these two sections. If a different topic was covered for bits and representations, then this lesson will have to be adapted, or one of the other topics covered instead (such as error control coding). Because students don’t need to understand how the compression method works, JPEG is easy to experiment with as long as you have software that can save pictures as JPEG files of varying quality (such software is widely used e.g. Photoshop and various free packages including Paint.NET). It is up to the teacher how many different image compression systems to talk about in class. If there is time, it would be good to cover the first one (varying the number of bits per pixel) and then another one such as JPEG or GIF. After that, the students can decide which they want to investigate in their report. Note that most of this lesson requires students to experiment with converting the formats of files to learn about them, and there is very little actual teaching material. The students should have a fairly strong understanding of the first image compression system, based on what they learnt in bits and representations. The JPEG compression system is complicated and need not be explored; as the math behind it is likely to be beyond most students (it involves summing cosine waves). The GIF system is straightforward, and uses the method described in one of the Unplugged activities (http://csunplugged.org/text-compression). Varying the number of bits per pixel Advice for teachers Depending on the software available on the school computers for working with images, the available image formats may vary. If using windows computers, Microsoft Paint is sufficient for this activity, and has 3 suitable file formats; 24 bit colour, 256 colours, and 16 colours. Microsoft Paint is the software assumed by the lesson plan for this activity. Many other image editing programs will be 31 suitable for this activity, as long as they can save files in different formats, and (ideally) show palettes/colour maps). If students are studying digital media they may already be using such programs (e.g. Photoshop). A widely used free program that is suitable (for both Mac and Windows) is GIMP. Earlier, students learnt about how colours can be represented using 3 bytes (24 bits), with 1 byte representing the amount of each of red, blue, and green in the image. They then went on to looking at what happens when fewer bits are used to represent colour. Tell the students that they are now going to investigate how these concepts can be used for image compression, i.e, making an image take up less space on a disk. Tell the students to open the image program they are to use (Microsoft Paint is assumed). Ask them to quickly confirm that 3 of the file formats they can save in are “24 bit colour”, “256 colours”, and “16 colours”. Ask them how many bits would be needed to represent 256 different colours (answer, 8 bits, and they should also realise that this is 1 byte). Then ask them how many bits would be needed to represent 16 colours (answer, 4 bits). They should understand that these 3 formats allow them to save images using 24 bits per pixel, 8 bits per pixel, or 4 bits per pixel. Less bits per pixel mean that less different colours can be represented. Get the students to work through the following exercises (experiments and questions) Find an image online (using Google images for example) or choose your own photo, and load it into the image program you have been told to use. Make sure it is at least 100*100 pixels, and is a photo with many colours. Shrink the image window (the white space that the image program allows you to draw on) so that it is the exact same size as the image, and then save the image using the 24 bit colour format. Look at how big your image is (for example 300 * 400 pixels), and calculate how many pixels in total that is. If each pixel was using 3 bytes to represent the colour on it, then how many bytes in total should the image be? Confirm this number by checking the size of the file on the computer. The size won’t be exact, as the file will have some other data in it along with the colour of each pixel, although should be close. [Note for teacher: To get the total number of pixels simply requires multiplying the height * length, so in the given example 300*400 = 120,000 pixels. If 24 bit colour is used, then that is 3 bytes for each pixel, so the total size of the image should be around 120,000 * 3 bytes = 360,000 bytes for the given example. A megapixel is a million pixels, so this example image is 0.12 megapixels]. Do the same for the 256 colour format. Remember that this is 8 bits in total(1 byte). Do the same for the 16 colour format. Remember that this is 4 bits in total (1 nibble). A question you may have is whether or not it matters whether this 3rd image is directly derived from the original image you had, the 24 bit colour image you have saved, or the 256 colours image you have saved. For now just choose one, and later you might want to go back and see if the image is the same if you had picked one of the other representations to derive the 16 colours image from. As an extra, you might also like to try the Monochrome bitmap format. Can you figure out how it decides what colour to make each pixel? Is it obvious that the 256 colours image is of a lower quality? 32 Are the colours in the 256 colours image and the 16 colours image the ones that you expected them to be, based on the work you did on using less bits to represent colours earlier? [Note for teacher: The answer is probably no, as while the possible colours for a certain number of bits were fixed in the colours activity (i.e for 1 bit per colour, there were 8 different colours that could be represented, and every student would have come up with the same 8 colours), these file formats attempt to optimise the colours chosen for the images] Using varying the number of bits per pixel for the achievement standard After this initial exercise, answering the following should be sufficient for the encoding section of students’ reports. Again, these can be given as instructions directly to the students. Choose a few different images, such as the one you used above, a simple drawing with a few different colours in paint (there should be 20+ different colours in the drawing), an image containing many shades of similar colours (such as a sunset or ocean, if you can, take the photo yourself), a black and white image you drew in paint, and a few photo images, with at least one containing human faces (preferably taken by yourself). [Note for teacher: It is important that all or most of the photos are taken by each individual student, and that the drawings are done by the individual students. This is so that the markers can ensure that it is their own work. Drawing/ photography ability does not matter for this standard]. Save each image in all the formats and confirm that the file sizes are around what they are expected to be. For each of the images, compare each of the different file formats for it. Discuss whether or not there is a noticeable difference in the quality. It would be good to include the Monochrome bitmap format as one of the formats you use. What would be the ideal format you’d use for each of the images? Out of all the images, which ones could be made the smallest without losing quality? Which were the ones with the most noticeable loss of quality? Why? These are the best and worst cases for this compression system. Compare this compression system to one that reduces the number of bits per colours simply by removing bits from colour codes, much like what you did in the bits and representations lesson. Is it better or worse? How is an image compression system such as this used in practice? (Wikipedia could be a good place to start if you are unsure Discussing real world applications and implications should consider how much more data or how much faster a download is as a result of the measure amounts of compression, and how slow a system would be without compression. For images, the uncompressed format is typically a bitmap (BMP) or “raw” file format on a camera. 33 The JPEG compression system (Recommended for all classes) Note for teachers As an alternative the above activity, students can instead evaluate a different compression system such as JPEG. Software that allows the amount of compression in a JPEG file to be modified is required. Do the same as what is described for the above compression system, except instead of using “24 bit colour”, “256 colours”, and “16 colours”, instead compare 4 or 5 different amounts of JPEG compression, with two being the extreme cases, and the other two or three being various cases in the middle. Using the JPEG compression system for the achievement standard For the students’ reports, again follow the above ideas, modifying them appropriately for JPEG. Do not worry about the second to last point, as it is irrelevant to JPEG (comparing to the activity in the bits and representations lesson). Students should use the same test cases as were recommended above. The reports should show clear comparisons of different types of compression. They can display the quality of the images (possibly zooming in to highlight low quality artifacts), the amount of compression (this might be a graph comparing original size with compressed size for various images and various qualities of compression), and the time taken for compression (although most systems may be too fast to notice any significant time taken). Other Image Compression Systems Any other compression system that is used in practice can be used for this standard. The main comparison to do is between a compressed file and its uncompressed original. Examples are: sound: uncompressed: WAV, AIFF files; compressed: mp3, aac, alc etc. pictures: uncompressed: BMP, raw; compressed: JPG, GIF, PNG, TIFF general files: uncompressed: ASCII or original document format; compressed: zip, compress, rar An important thing to consider if choosing a different compression system is whether or not experiments with it can be easily personalised (usually by choosing the files to use to evaluate it), and whether or not the personalisation will be clear to the markers. Human Computer Interaction What is Human Computer Interaction? According to Wikipedia, Human-Computer Interaction (HCI) “involves the study, planning, and design of the interaction between people (users) and computers. It is often regarded as the intersection of computer science, behavioral sciences, design and several other fields of study.” Why do we care about Human Computer Interaction? 34 Being skillful at HCI has become essential to developing software that is effective and popular. It goes way beyond choosing layouts and colours for an interface, as largely about the psychology of how people interact with digital devices, which means understanding many issues about how people behave, how they perceive things, and how their cognitive processes work so that they feel that a system is working to help them and not hinder them. If you ask people if they have ever been frustrated using a computer system, you’ll probably get a clear message that HCI isn’t always done well. Human Computer Interaction in the Achievement Standard Human computer interaction has requirements in the achievement standard for achieved, merit, and excellence. At this level students are using HCI principles to evaluate existing interfaces, not to design new ones. Sensitising students to weaknesses in interfaces, and especially how the general public react to interfaces (rather than computer specialists) will put them in a much stronger position for designing great interfaces in the future. The standard is based around the widely used concept of “usability heuristics” that provide a well-established benchmark for identifying weaknesses (and strengths) in interfaces. It helps if the teacher is already sensitive to these issues, and there are some approachable and enjoyable books about interface issues that provide a great background e.g. Designing with the Mind in Mind: Simple Guide to Understanding User Interface Design Rules by Jeff Johnson. The website useit.com provides a lot of information about usability and heuristics, and Nielson’s book Usability Engineering is a detailed reference that includes a description of heuristics in Chapter 5. The classic HCI book (although it isn’t really about computers) is The Design of Everyday Things by Donald A. Norman. For Achieved, students must: “provide examples from human-computer interfaces that illustrate usability heuristics” For Merit, students must: “evaluate a given human-computer interface in terms of usability heuristics” For Excellence, students must: “suggest improvements to a given human-computer interface based on an evaluation in terms of usability heuristics.” This section of work outlines the process of carrying out a usability evaluation that will enable students to gain merit for human computer interaction and then extends it to identifying possible improvements to the interface to enable them to gain excellence. The achieved level is covered implicitly by the requirements for merit. In order to carry out a usability evaluation, students will need a basic understand of human computer interaction and Nielson’s heuristics, which are covered prior to the usability evaluation. Additional Resources for Human Computer Interaction A set of Powerpoint slides accompanies this document, and can be used to introduce examples of the heuristics. 35 A glossary for the whole standard accompanies this document, and includes HCI terms The basics of HCI Some students may have already done some HCI in AS91074 (1.44) the year before, so some of this material will be revision for them. In this case, the material can be covered faster than if it is new, although it is still probably best to revise it in case the students have forgotten important details. The key ideas are covered in the first few slides of the powerpoint presentation that accompanies this plan (which includes notes on each slide for the teacher). The main points to get across are: The “system” that has to work well is the computer and the human together. Many people get frustrated with digital devices. Sometimes they will put up with it because it’s the only option, but in other cases devices and software with good interfaces sell way better or can be priced higher because they help the user get their job done. The worst person to evaluate an interface is the person who designed it. They know exactly how it should work; but if someone else tries it you’ll find out how it looks to a typical user (for this reason a student should not design an interface as a submission for this standard – it would be evidence that they don’t understand HCI evaluation!) An interface is used to do a task, so it makes the most sense to identify the tasks that a particular interface is for, and then consider how difficult those tasks are using that interface. The common mistake is to focus on features of an interface, but in the real world the question is whether or not those features can be used to achieve a task from beginning to end. Nielson’s Heuristics There are a various sets of heuristics (rules of thumb) for evaluating interfaces, but the one used in this plan are from Jakob Nielson’s http://useit.com site – this particular set is widely used. These can be introduced to the class using the powerpoint presentation that accompanies this plan. Each of the heuristics is given with examples of well-known systems that illustrate a positive or negative use of the heuristic. You or the students may identify your own examples (typically any time an interface frustrates or confuses you) that you can use as as more meaningful examples. The idea of the heuristics is that an evaluator can look at an interface and detect errors even before they get a user to try it out. This approach is only one of many that would be used for a careful evaluation in industry, but it is enough to highligh obvious problems, and illustrates ideas from HCI well. Applying Nielson’s Heuristics to HCI Evaluations Materials required for this lesson In this lesson, students will learn how to evaluate the usability of a digital device or piece of computer software using Nielson’s heuristics as a guideline. Choose a digital device to use for a class demonstration of usability, or a piece of software that can be shown on a data projector. If the chosen device/ software is very complex (like a cell phone that is able to do many different things 36 such as make calls, send texts, play music, take photos, etc.) then constrain the evaluation to a specific component of the system. In the case of a cell phone, this might be “sending text messages with the cell phone” or “playing music with the cell phone”. To make sure students’ reports are personalised, they will need to do their own exercise later on a different task and/or device to the one covered in class. Carrying out a usability evaluation with the class Start by explaining to the students that for the achievement standard, they will be carrying out a usability evaluation of a digital device that is similar to the demonstration evaluation that follows. Throughout this activity, students should be taking their own notes about the tasks, interface and the relevant heuristics. Tell the students that it is very important that they take good notes for this, as the notes will come in handy for giving them ideas for the usability evaluation they’ll be doing by themselves. Step 1 of usability evaluation – identifying common tasks The first thing to do in a usability evaluation is to identify the common tasks that will be carried out with the device/ software. Ask the students something like “what tasks are commonly carried out with this device/ software?” Word the question appropriately for the chosen device/ software and component to focus on. As the students come up with ideas, encourage class discussion and make a list on the whiteboard or data projector of the tasks the students think of. Each task on the list should be very simple, and if it is complex, then it can probably be broken down into a few simpler tasks. Students may take a while to think of all the tasks done on a device (for example, a TV remote is obviously used to change channels and volume, but an important task is switching the TV on, and in some cases that can be complicated because it’s not obvious immediately if the TV has responded, or perhaps the button to press isn’t obvious). A task that involves 3 button presses might seem trivial, but if there are 5 buttons to choose from at each step, there are 5 x 5 x 5 possible outcomes, and only one of the 125 outcomes is the desired one! Exploring the right and wrong sequences that a user can go through can become quite detailed even for small tasks. As an example, if a cell phone was the chosen device, and the focus was on text messaging, the question you might ask the students is “What tasks are commonly carried out when using a cell phone for sending text messages?” Below is a list of the kinds of tasks students might come up with. Open a new blank message Enter a few words into the message Enter a number, such as “23” Correct an error Select a person to send the message to Select more than one person to send a message to Send the completed message Just saying “Send a text message to a friend” is too general, and would be too broad to evaluate. For some devices, significant tasks might include switching the device on or opening a file. They may seem easy, but often users can struggle even with these simple tasks if the interface is confusing. 37 Step 2 of usability evaluation – applying Nielson’s heuristics to common tasks The next step to the usability evaluation is to carry out each of the identified tasks in the previous step in order to identify usability problems with the interface. To make this easier, start by reordering the tasks into an order that they might be carried out by a person using the device (the above bullet points are already in such an order). For each of the tasks, choose a volunteer in the class to try carry out the task on the device or software. It can be easier to find interface issues if each volunteer is not familiar with the specific model or software that the device uses. Get the volunteer to carry out the task in the way that they think is the right way to go about it. They should say what they are trying to do and what they are thinking about the device so that the class can hear. This includes saying if they are confused, or if they are guessing about what to do, and why they are trying what they are. It’s important to focus on any difficulty the volunteer has with the interface as a fault in the interface, not with the volunteer. Each time each of the following happens, ask the class to explain. Both good and bad points of the interface should be identified. Remind the students that they need to be taking notes about this. The volunteer was unsure what to do, but after a bit of trial and error figured it out. Discuss what the interface could have done to prevent confusion. Which heuristic(s) are relevant? The volunteer made a mistake and does something irrelevant to the task and is surprised. Discuss what might have caused the volunteer to do this. What assumptions was the volunteer making? Which heuristic(s) was the volunteer assuming was being followed? How did the device violate that heuristic(s)? The volunteer says they are doing something because it is obviously the correct thing to do. An example of this would be the volunteer saying “I’m selecting the envelope icon as it is normally associated with sending a message”. Discuss what heuristic(s) the interface was following that made this easy for the volunteer. In the example I gave, the heuristic would probably be “Consistency and standards”, as they probably knew this from other cellphones they have used before, or “Match between system and the real world” because physical envelopes are used to send messages. The volunteers should keep trying to complete their task, although with a bad interface you may harvest plenty of examples before completing it. If identifying the relevant heuristic is difficult, go slowly through each of the heuristics trying to relate them to the problem until a suitable one is identified. Often more than one heuristic will be relevant. Advice for teachers Make sure the students understand that if a task volunteer finds a task tricky with the device, it is because of the device and not the volunteer. It is best to choose volunteers who are fairly well respected in the class, unlikely to get negatively hassled by their classmates for making mistakes, and who are confident talking in front of the class as they are more likely to explain why they’re doing what they’re doing, which is an important part of the activity. 38 Once all the tasks have been completed, several usability problems with the interface should have been identified. Choose two or three of the identified problems (that a heuristic was clearly identified for), and ask the students how the interface could be changed so that it is not violating that heuristic. Encourage class discussion on different ideas. Unfortunately fixing one problem can introduce another, so once a few solutions have been identified, go through each of the heuristics and consider if the solution could violate one of them. A usability evaluation such as the one above is exactly what students need to do for the achievement standard. If they choose their own device to do a usability evaluation on, and follow the same procedure as above, they should sufficiently fulfil the requirements for Excellence in the Human Computer Interaction section of the achievement standard. Having each student choose a different device, or at least a different task for each device, will personalise their report. If the student isn’t familiar with a device they can do the evaluation on their own, otherwise they could do it in pairs, observing the difficulties that their partner has. Having a parent or grandparent try the interface can be a rich source of examples, although it requires a high level of maturity and patience from the student. Common pitfalls in usability evaluations There are several common mistakes that are made when carrying out usability evaluations or when doing the human computer interaction section of the achievement standard that should be avoided. Focussing on features instead of tasks – a camera might have clever special effects feature, but if users aren’t reminded to save the results, the overall task of adding an effect to a photo might be frustrating. Blaming a user rather than the device – if a reasonably sensible adult makes mistakes with an interface, it’s probably the interface that’s at fault, and that means there’s a market for an improved device. Evaluating an interface that you have designed yourself – the designer knows exactly how their system should work. A different user’s first action may well be to do something the designer didn’t anticipate! 39