EC310 Lecture 13
advertisement

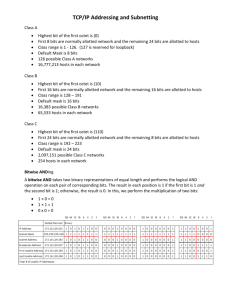
EC312 Lesson 26: Internet Protocol Objectives: (a) Summarize the principles behind the design of the Internet Protocol. (b) Define the structure of an IP address and define the purpose of network masking. (c) Determine the address space available given an IP address and mask. (d) Identify and explain the basic fields of the IP header. (e) Understand the current use of the IP address space. I. The Problem and the Solution 1. The Problem. As computer networking took off in the 1970's, many different competing companies developed many different network architectures, each using different protocols at each layer. Each company advertised its own approach as "the best." This explosion of different approaches was beneficial in that it fostered competition, with each company vying to make their own network architecture better. But, all the while, this presented a problem when people on different networks wanted to connect to each other. Originally, computers could only talk to other computers on the same network—but, at the same time, there was a strong desire to allow any two computers on any two networks to be able to communicate. This seemed infeasible: Different networks have different frame formats at the data link layer, different physical layer characteristics, different addressing schemes, etc. Consider the internet shown below, which consists of a token ring (RIP), an Ethernet network and an IBM network (RIP) connected together. Each of these networks uses different frame formats, as shown. Could we just plop an Ethernet frame on a token ring network or an SNA network and have it work? 1 Token Frame Format Data Frame Format 1 1 1 SD AC 2 or 6 Destination Address FC Starting delimiter SD 4 2 or 6 Source Address J K 0 J K 0 ED AC Information FCS 0 1 ED 1 FS IBM(line SNA J, K non-data symbols code) 0 Ethernet Access control Frame control PPP T M PPP Priority; T Token bit R R R Ring M Monitor bit; RRR Reservation Token FF frame type ZZZZZZ control bit Z Z Z Z Z Z FF High-Level Data Link Control Ending delimiter Figure 13.4 802.3 MAC frame Frame status J K 1 J K 1 A Copyright ©2000 The McGraw Hill Companies C xx A I C I E E x x intermediate-frame bit error-detection bit A address-recognized bit xx undefined C frame-copied bit Leon-Garcia & Widjaja: Communication Networks Figure 6.61 The answer is, of course: No. The frame formats on one network will be completely unrecognizable on a Frame format for bit-oriented protocols. different network! 13.7 For example, with Ethernet, the destination address occurs starting on the 9th byte into the frame. In token ring, the destination address starts with the 4th byte into the frame. In SNA, the destination address occurs on the 2nd byte into the frame. As another example, in Ethernet the data starts 23 bytes into the frame, in token ring the data starts either 7 or 15 bytes into the frame, and for SNA the data starts 3 bytes into the frame. A frame from one network will look like garbage on a different network. Note that, aside from the frame format, different networks have “structural” differences also. For example, Ethernet has a maximum frame size of 1500 bytes, token ring has a maximum frame size of 5000 bytes and SNA has no maximum frame size. Consider also: Ethernet addresses are always 6 bytes. Token ring addresses can be 2 or 6 bytes, and SNA addresses are 1 byte. And, furthermore, we’ve shown only three networks connected above. Throw in an ATM network, a Token Bus network, some Novell and AppleTalk crap, an FDDI optical network and a couple of wireless LANs and things go to hell in a handbasket. To summarize, then, we need protocols that can implement internetworking, i.e., we need protocols that can overcome the differences in networks. These protocols should "conceal" the underlying network differences so that users are unaware that different networks even exist. From the user's perspective, everyone should be on one monolithic network. 2 2. The Solution: The Kahn/Cerf Protocols A revolutionary solution to the internetworking problem was proposed in the early 70's by Vinton Cerf and Robert Kahn. The two protocols they proposed, later christened the Internet Protocol (IP) and the Transmission Control Protocol (TCP) quickly became the most popular suite of protocols for internetworking and were subsequently adopted as the protocols used by the Internet. Vinton Cerf Robert Kahn Cerf and Kahn with President Bush If the award of the Presidential Medal of Freedom does not convince you of the importance of these protocols, perhaps this will: These protocols are so damn famous that one of the authors was once invited to give a talk to sleeping midshipmen: These two protocols—IP and TCP—are truly a work of genius. These protocols were intended to allow internetworking for small networks (in 1975 the Internet had a mere 61 nodes). These protocols have successfully scaled to support networks of billions of users. It is estimated that two billion videos are watched on YouTube each day. Trillions of emails are sent each year. Think about all the things you use the Internet for—and then think that it all works because of protocols that were designed in 1975 for a small system, and never intended to scale to large networks. Stated another way: It is amazing that the Internet actually works at all! However, the fact that the Internet uses protocols originally designed to be used on a small network of nerdy academics means that security was never baked into the cake. Security was not needed on a network of 61 nodes, all of whom were friends. With one billion nodes on the network today, well… things are different. 3 3. The Premises. Kahn and Cerf reasoned that to internetwork efficiently, everyone must agree on three things: A standard for service A global addressing scheme A uniform packet format Regarding the first item above—the standard for service—IP provides connectionless unreliable best-effort packet delivery. Connectionless: Every packet is an independent entity, possibly traveling over different paths from source to destination. Stated another way, there is no network connection that is set up in advance along which all packets will subsequently flow from source to destination. Unreliable: Packets can be lost, delivered out of order, or delivered multiple times; IP will not detect this. Best-effort: There are no guarantees packet delivery will be successful. Basically, IP says: "I'll try, but no guarantees." The standard of service provided by IP can be likened to the Post Office, but without the shootings. To see this, suppose that you mail three letters to your family back in Los Angeles, California. Each letter is mailed from the same location in Bancroft Hall. You mail Letter #1 on Monday, Letter #2 on Tuesday and Letter #3 on Wednesday. It is quite possible that the letters follow different routes from Annapolis to Los Angeles. For instance, two of the letters might be delivered on a direct flight, while the third might be placed in a bag that has to change planes in Chicago. Letter delivery is connectionless. It is quite possible that your family receives the letters out of order, perhaps receiving Letter 3 before Letter 2. One of your letters might never be delivered—the Post Office estimates that slightly over 1% of all mail is never delivered to the destination (for varying reasons). Letter delivery is unreliable. Unless you pay a premium, there are no guarantees that a letter you place in the mail will actually be delivered. Letter delivery is provided on a best-effort basis. We now address the other two requirements for internetworking. The global addressing scheme will be discussed in Section II below, and the uniform packet format will be discussed in Section III. II. The IP Address 1. A Software Address: To make a group of networks "appear" to be a single network, we must use a single global addressing scheme for all hosts on all networks. IP assigns to each computer a unique 32-bit IP address. This is a "software address"; it is not a hardware address. To send a packet over a TCP/IP network, we must use the destination's IP address. IP addresses have two parts: a Network ID, which is the same for all hosts on particular network, and Host ID, which is a unique suffix for each individual host on this particular network. Network ID Same for all computers on a particular network Host ID Unique suffix for each individual computer on this particular network 4 2. Dotted Decimal Notation for Reading IP addresses. Let's momentarily gloss over the separation of the IP address into a Network ID and a Host ID, and simply focus on how the 32-bit address is represented. For historical reasons, IP addresses are expressed as decimal numbers (as opposed to a more sensible hexadecimal scheme). The 32-bit IP address is separated into 8-bit chunks (octets). Each octet is then expressed as a decimal value, separated by periods. This is termed the dotted-decimal notation for IP addresses. For example, to express the IP address 10000001000010010100000111001111 in dotted decimal notation, it is first split into four octets: 10000001 00001001 01000001 11001111 and the four octets are each individually converted to a decimal (base-10) number: 10000001 00001001 129 9 01000001 65 11001111 207 We then write the four decimal numbers separated by periods: the IP address is 129.9.65.207. Example 1 Express each of the following IP addresses in dotted-decimal notation. (a) 00001011 00000010 00000000 00100111 (b) 10000000 10000000 11111111 00000000 Solution: (a) (b) Every computer on the Internet must have a unique IP address. That is, no two devices on the Internet cannot have the same IP address at the same time. In theory, since IP addresses are 32 bits, we have 232 (more than 4 billion) IP addresses available. Thus, in theory, more than 4 billion devices could be simultaneously connected to the Internet. 3. The Network Mask Now, let's revisit the notion that the 32 bits in an IP address are divided into a Network ID and a Host ID. To view the Network ID portion of an IP address, we use a network mask. A network mask (which we will just call a mask, since the context is understood) is a 32-bit number consisting of a string of contiguous 1’s followed by contiguous 0’s. Example 2 Which of the following can serve as masks? (a) (b) (c) (d) 255.2.0.0 255.255.0.0 255.255.0.23 255.255.64.0 Solution: (a) (b) (c) (d) 5 Example 3 Show that the address 255.240.0.0 is a mask by writing out the address as 32 bits. Solution: Example 4 Write the following masks in slash notation. (a) 255.0.0.0. (b) 255.255.255.0 (c) 255.240.0.0 Solution: (a) (b) (c) Example 5 Write the following masks in dotted decimal notation. (a) /16 (b) /9 Solution: (a) 4. Use of Masks (b) Recall that IP addresses have two parts. Network ID Host ID We design masks so that if we bitwise AND the mask with an IP address, we extract the network ID. For example, suppose we are examining a Navy site that is using a mask of /17. Suppose we see that a host on this network has the IP address: 131.122.220.30. What is the network ID? To solve this problem, we first express the mask as a 32-bit IP address: 1 1 1 1 1 1 1 1 . 1 1 1 1 1 1 1 1 . 1 0 0 0 0 0 0 0 . 0 0 0 0 0 0 0 0 We then express the IP address as a 32-bit quantity: 1 0 0 0 0 0 1 1 . 0 1 1 1 1 0 1 0 . 1 1 0 1 1 1 0 0 . 0 0 0 1 1 1 1 0 We then bitwise AND the mask with the IP address. Recall the table for the bitwise AND operation: A 0 0 1 1 B 0 1 0 1 A AND B 0 0 0 1 6 1 1 1 1 1 1 1 1 . 1 1 1 1 1 1 1 1 . 1 0 0 0 0 0 0 0 . 0 0 0 0 0 0 0 0 1 0 0 0 0 0 1 1 . 0 1 1 1 1 0 1 0 . 1 1 0 1 1 1 0 0 . 0 0 0 1 1 1 1 0 - - - - - - - - - - - - - - - . - - - - - - - - . - - - - - - - 1 1 1 1 1 1 1 1 . 1 1 1 1 1 1 1 1 . 1 0 0 0 0 0 0 0 . 0 0 0 0 0 0 0 0 Now, converting the result to dotted decimal notation, we have the network ID: 131.122.128.0 Recall the significance of this network address and the mask: Since the mask was given as /17, every host on this network will have the same first 17 bits in common. The network ID—131.122.128.0—specifies the exact values of these first 17 bits. Thus, every host on this network has an IP address that begins: 1 0 0 0 0 0 1 1 . 0 1 1 1 1 0 1 0 . 1 ... The remaining bits (shown as the three dots above) are used to constitute the host ID. Example 6 Suppose an organization has been given a mask /24. One of its machines has IP address 200.137.34.56. What is the network ID? Solution: Example 7 Suppose an organization has been given a mask /13. One of its machines has IP address 200.137.34.56. What is the network ID? Solution: 5. Obtaining an IP Address Each host on the Internet must have a unique IP address. It would be very bad for two (or more) people to have the same IP address. This latter (bad) event is termed an address conflict. So, we must ensure there are no address conflicts. When an organization needs IP addresses, it is given a block of addresses. So… how does an organization get a block of IP addresses to dole out to its hosts? To ensure there are no address conflicts, (i.e., to ensure uniqueness) an organization—the Internet Assigned Numbers Authority (IANA)—gives out network addresses. IANA has authorized five sub-organizations, termed Regional Address Registries, to control large blocks of addresses and distribute them to organizations in different geographic regions of the world. The Regional Address Registry covering the United States and Canada is ARIN (which stands for American Registry for Internet Numbers). 7 Generally, ordinary organizations do not interact with ARIN. Usually, ISPs get a large number of addresses from ARIN, and organizations, in turn, get blocks of addresses from their ISP. So, the authority is: ICANN IANA Ultimately controls all IP addresses 5 Regional Address 5 address Registries thatRegistries IANA has that ICANN authorized to administer has authorized blocks of addresses to administer RIPE APNIC ARIN LATNIC AFRINIC blocks of addresses ISP 1 … ISP 2 Joe’s Hardware Sal’s Pizza ISP 16 … … USNA … So…bottom line…when an organization needs IP addresses, it is given a network address (usually from an ISP). The organization then uses the remaining bits in the IP address (corresponding to the host bits) to distribute unique IP addresses to its hosts. An Aside Believe it or not, from the inception of the Internet until late 1998, a single individual manually assigned all IP addresses. The individual, Jon Postel, was termed by many as the God of the Internet. He formed the Internet Assigned Numbers Authority (see picture above) and served as its head until his death at age 55. He was the guiding force behind a number of Internet protocols. On the ten-year anniversary of his passing, Vint Cerf offered the toast: Here's to Jonathan B. Postel, a man who went about his work diligently and humbly, who served all who wished to partake of the Internet and to contribute to it, and who did so asking nothing in return but the satisfaction of a job well done and a world open to new ideas. 8 6. IP Address Blocks When an organization is given a network ID, it is given an IP address and a mask. For example, an organization might be given the block of IP addresses: 205.16.37.32/28 In this case, the first 28 bits determine the Network ID, and the final 4 bits are used for the Host ID. Thus, all hosts on this network will have the first 28 bits in common: 205.16.37. 0 0 1 0 _ _ _ _ All hosts on this network will have the same first 28 bits—the Network ID. Figure 19.3 The organization can play with the last four bits to dole out unique IP addresses to all of its hosts. A block of 16 addresses granted to a small organization So, the organization can choose to make the host ID 0001, or 0101, or 1011, etc. It can use the last four bits to assign unique IP address to all of its hosts. The organization has 24 = 16 different ways it can assign these last four bits. From Forouzan, Data Communications and Networking, 2007 Any host on this network can have its address represented in CIDR notation by following the address with the mask. For example, an individual host on the above network might have its IP address expressed as 205.16.37.39/28 More generally, a block of IP addresses is defined using the notation 19.19 W.X.Y.Z/n where W.X.Y.Z defines any address in the block and /n defines the mask, i.e. the n leftmost bits are 1. 9 Example 8 You know that one of your organization’s IP addresses is 205.16.37.39 / 28. (a) Describe the mask qualitatively. Solution: (b) What is the mask in binary? Solution: (c) What is the mask in dotted decimal notation? Solution: (d) Now, the mask bits with a 1 correspond to the “network-ID” and the mask bits with a zero correspond to the bits that you can play with to assign IP addresses to your hosts. If that is the case, how many addresses have you been given? Solution: Now, we have to further complicate matters (slightly). First complication: The first address in a block is termed the network address, and is normally not assigned to a host. That is, the first address in your block, where the host bits all have a value of zero, is used to define your network to the rest of the world. In the foregoing example, we said that “we will have to revise this answer shortly.” Here is the revision: We have 16 addresses, but the first is our network address, which is not available to assign to a host. Second complication: The last address in a block is termed the broadcast address, and is normally not assigned to a host. That is, the last address in your block, where the host bits all have a value of one, is used to indicate "all hosts on this network", and this address is thus not available to assign to a host. Bottom line: When you calculate the number of IP addresses you have to play with, you first determine the number of bits in the host-ID portion, and then use the formula: Number of addresses available for assignment to hosts = 2number of bits in the host-ID portion 2 Example 9 You own a small organization that needs (and is given) 14 IP addresses for assignment to individual hosts. What is your mask in dotted decimal notation? Solution: 10 Example 10 As in the example above, you know that one of your organization’s IP addresses is 205.16.37.39 / 28. What is the network address assigned to your organization? Solution: Last byte: MASK: Address: Result: This is a major point of confusion for students. If I know that one of my machines has an IP address of 205.16.37.39 how can I tell that the network address I own is 205.16.37.32 The answer: by using the mask as we have shown. Example 11 What is the network address of a network that has a host assigned the IP address: 182.44.82.16 / 26 Solution: Example 12 What is the network address of a network that has a host assigned the IP address: 182.44.82.80 / 26 Solution: So, as you can see, there is the potential for things to get very tricky here. If you knew a host had IP address 182.44.82.80 is it obvious that the host is on a network with network address 182.44.82.64? Here is an alternate way to find the network address (i.e., the first address in your block): If the IP address of a host is W.X.Y.Z/n set the 32 n rightmost bits to zero. Example 13 Using the technique above, determine the network address of a network that has a host assigned the IP address: 182.44.82.16 / 26 Solution: 11 Example 14 Using the technique above, determine the network address of a network that has a host assigned the IP address: 182.44.82.80 / 26. Solution: Example 15 Suppose one of you machines has the IP address 180.34.64.64 / 30. (a) How many addresses do you have available for assignment to hosts? (b) What is your network address? Solution: (a) (b) So much for the first address in your block. How do you find the last address (i.e., the broadcast address) in your block? Here is a way to find the last address in your block: If the IP address of a host is W.X.Y.Z/n set the 32 n rightmost bits to one. Example 16 Suppose you know that one of your organization’s IP addresses is 205.16.37.39/28. What is the last address (the broadcast address) in the block assigned to your organization? Solution: Summary of what you need to know: Given that you have a host with address W.X.Y.Z / n determine the number of addresses you have in your block, as well as the first address (i.e., the network address) and last address (i.e., the broadcast address). 7. Special IP Addresses. We already mentioned that an IP address with the network ID bits are set to the proper value, but the host bits are all zero refers to the network itself. Similarly, IP address with the network ID bits set to the proper value but with the host bits all set to one is the broadcast address for that network. 12 IP Addresses (2) Here are more special IP addresses. The all zeroes address (32 zeroes) means: “me”. This address is used by a host that does not know its IP address. The all ones address (32 ones): all hosts on this network Why would this ever be used? A host may not know its own IP address (and hence does not know its network ID). A host that just starts up and doesn't know who or where it is uses the all zeroes address to refer to itself and the all ones address to refer to "anyone else out there." The reserved address 127.0.0.0 is used for “loopback.” This address is used for testing on the local computer. When 127.0.0.0 is used as a destination address, the computer does not send the packet to the network. Special Special IP IP addresses. addresses. 8. Private IP Addresses Table IANA 19.3 has reserved the following addresses for private use: Addresses for privateIPnetworks 3/24/2007 Tanenbaum Chapter 5 Network 3/24/2007 Tanenbaum Chapter 5 Network 71 71 From Forouzan, Data Communications and Networking, 2007 You are allowed to use any of these addresses at will without permission from anyone. Note that this equates to almost 18 million addresses (almost ½ of 1% of the potential IP addresses). Example 17 (a) Can more than one organization assign the number 172.18.3.1 to one of its machines? 19.43 (b) If no, why not? If yes, does this violate the cardinal rule: No two machines on the Internet can have the same IP address at the same time? (c) What happens if I try to launch a packet with the destination address 172.18.3.1 onto the Internet? Solution: (a) (b) (c) 13 II. The Uniform Packet Format We mentioned that IP was developed with the idea that to internetwork efficiently, we must have an agreed upon packet format. The Internet Protocol defines a hardware-independent packet format. The IP packet has the basic structure: Header Data The size of the header can vary from 20 to 60 bytes. The maximum allowed total size of an IP packet (header + data) is: 64 KB = 65,535 bytes. Figure 20.5 IPv4 datagram format The IP packet format: Forouzan, Data Communications and Networking, McGraw Hill, 2007 We offer a brief explanation for the various fields: 20.11 Version: Current version IP version 4 HLEN: length of the header (in 4 byte increments): Minimum: 5, Maximum 15 (Note: In practice, the vast majority of IP packets contain no options and thus have the minimum header length of 5.) Type of service: This isn’t used much in practice. We'll ignore it. 14 Total length: Total number of bytes in the packet. Max is 65,535 Time to live: Hop-counter. This is a number decremented by one on each hop. When the time to live (hop-counter) reaches zero, the packet is discarded. Protocol: TCP or UDP or other? Header checksum: A checksum of the header only. Addresses. If you don't know what these are, you've been asleep for the past hour! Options: (See text if you wish; these options will not be covered in class.) Assistant Professor Patrick Vincent and LCDR Jesse Atwood Help us improve these notes! Send comments, corrections and clarifications to vincent@usna.edu Problems 1. 2. 3. Suppose you transfer a computer from the ECE Department at USNA to the EECS Department at USMA. Will its MAC address need to be changed? Will its IP address need to be changed? (a) Assume an IP packet traverses multiple routers on its way from source to destination. Which IP packet header fields change from router to router? (b) You receive an IP datagram containing 1024 bytes (assume no options). What is the value of the HLEN and TOTAL LENGTH fields? (c) What is the purpose of the Time-to-Live field in the IP packet header? (d) If an IP packet header is 32 bytes total, what value should the HLEN field contain for this packet? (e) A host has just been powered on and wishes to receive an IP address from the DHCP server. How can it send a request over a TCP/IP network if it does not have an IP address and does not know the address of the DHCP server? (f) If Time To Live (TTL) field in the header of an IP packet has the value 000000001, what will happen to this packet when it travels to the next hop? (a) What is the network address of 10.64.128.200 /28? (b) How many IP addresses are there in the block of IP addresses assigned to this network? (c) What is the first available IP address that can be assigned to a host? (d) What is the last available IP address that can be assigned to a host? (e) What is the broadcast address for this network? (f) Can the IP addresses assigned to this network be routed across the Internet? Justify your answer. 15 4. (a) Write the following masks in slash notation. (i) (ii) (b) 255.255.255.0 255.240.0.0 Write the following masks in dotted decimal notation. (i) (ii) /16 /9 5. The purpose of the header checksum field in an IP header is to: a. Provide for error checking between source and destination b. Check that the headers from previous layers have been filled out correctly c. Add up the bytes in the message and make sure it can fit in one packet d. This field is no longer used for IP communications 6. As a network administrator you notice something fishy going on in your network. In order to diagnose the problem you start sniffing packets using Wireshark and find an IP packet with the following header (shown here in hexadecimal). 45 00 00 34 60 ad 40 00 3f 06 03 5d 83 78 a8 1f 83 78 28 aa (a) (b) 7. What version of IP is this packet using? What is the source address? Consider IP address, 136.52.100.34/19. (a) What is this address’s network mask (in dotted decimal)? (b) What is this address’s network address? (c) What is this network’s broadcast address? (d) How many hosts can this network accommodate? 8. In a brief sentence, explain what is meant by the Internet Protocol principle connectionless. 9. True or False: An IP address is normally expressed in hexadecimal. 10. Write the network address for IP address 146.25.129.17/20 in dotted decimal format. 11. The purpose of the time to live field in an IP header is to: a. Show the number of hops to the destination b. Prevent a packet from endlessly traversing the internet c. Translate a packet to classless routing (CIDR) d. Amplify the network mask 16 12. Which one of the following is NOT a principle behind the design of the Internet Protocol? a. user-defined b. best-effort c. unreliable 13. Fill in the blanks: An IP address is____bits long. When expressed in dotted decimal form, every ___ bits form an octet. The integer value of a single octet can range from ____ to ____ . 14. In one sentence, state the purpose of a network mask. 15. (a) Assume you are provided the IP address 128.32.14.2 and a network mask of 255.255.254.0. What is your network ID expressed in dotted decimal notation? (b) Continuing from part (a), state the number of bits that can be used to assign host IP addresses. (c) Continuing from part (b), determine how many valid host IP addresses you can assign on your network. (d) Assume that host IP addresses are assigned sequentially from lowest to highest on your network. What is the last valid IP address that can be assigned to a host on your network expressed in dotted decimal form? Solutions to Selected Problems 5 Answer is (a) 6 (b) 83 78 a8 1f = 131.120.168.31 7 (a) (b) (c) (d) 255.255.224.0 136.52.96.0 136.52.127.255 8192 8. Every packet is an independent entity, possible traveling over different paths from source to destination 10. 146.25.128.0 13. 32 ; 8 ; 0 ; 255 14. To extract the network ID from an IP address (or to extract the network address). 15. (a) (b) (c) (d) 128.32.14.0 9 510 128.32.15.254 17