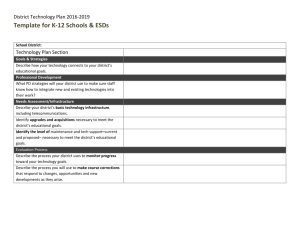
Telecommunications Sector Security Guidelines Draft Guidelines
advertisement

Contents Purpose of this guide ............................................................................................................................................. 3 Contact information ........................................................................................................................................... 4 List of acronyms ................................................................................................................................................. 4 Overview of the Security Framework .................................................................................................................... 5 Key steps to protect your networks ....................................................................................................................... 6 Part 1: General information ................................................................................................................................... 7 Implementation of the framework by Government and industry in good faith ............................................... 7 Key security principles ........................................................................................................................................ 7 What are the national security risks to telecommunications networks? .......................................................... 8 Which parts of networks are particularly vulnerable to unauthorised access and interference? .................. 10 Who has obligations under this security framework? ..................................................................................... 12 Part 2: What do you need to do to meet your security obligation?.................................................................... 15 Overview of the security obligation to protect networks and facilities .......................................................... 15 How do you meet your security obligation? .................................................................................................... 15 What are competent supervision and effective control? ............................................................................ 16 What is unauthorised access or unauthorised interference? ...................................................................... 18 What does it mean to ensure the availability and integrity of telecommunications networks and facilities? ....................................................................................................................................................... 20 What does it mean to ensure the confidentiality of communications and information? ........................... 20 Resources to help you meet your national security obligation ................................................................... 22 Does this security obligation apply to existing systems? ............................................................................. 23 Part 3: What do you need to do to meet your notification obligation? .............................................................. 25 Who needs to notify Government of changes to systems?............................................................................. 25 Are exemptions available? ............................................................................................................................... 25 What types of changes should be notified?..................................................................................................... 26 When should changes be notified? .................................................................................................................. 29 How can you notify the Government of changes? .......................................................................................... 31 Can you submit a security capability plan instead of multiple individual notifications? ................................ 31 What happens after you notify Government of proposed changes or submit a security capability plan? .... 33 Part 4: When should you engage with security agencies? .................................................................................. 34 General threat advice ....................................................................................................................................... 34 Specific threat advice ....................................................................................................................................... 34 Operational assistance ..................................................................................................................................... 35 Part 5: How will the Security Framework be administered? A step by step guide ............................................. 37 Glossary ................................................................................................................................................................ 38 Attachment A: Overview of the notification process .......................................................................................... 39 Telecommunications Sector Security Guidelines 2 Purpose of this guide The Australian Government has prepared this guide to assist industry participants to understand the obligations arising from the Telecommunications and Other Legislation Amendment Act 20xx. This is a live document and subject to periodic review in order to capture changes to related legislation and security advice. Please visit the Attorney-General’s Department website at www.ag.gov.au/telcosecurity to ensure that you have the latest version. The purpose of this document is to provide guidance to carriers, carriage service providers and intermediaries (C/CSPs) on their obligations in the Telecommunications Act 1997 (the Telecommunications Act) to: (a) protect networks and facilities from national security risks of unauthorised interference and unauthorised access; and (b) where applicable, notify government of changes to their telecommunications systems and services. This document is intended to be read by senior management and executives, as well as employees in security and regulatory roles and technical officers responsible for network design and maintenance. The guidance provided is outcomes focussed and not prescriptive. These guidelines apply to all C/CSPs. However, the measures which are appropriate for C/CSPs to implement will vary across the sector, depending on for example, the size and scope of a particular C/CSP’s operations. For this reason, C/CSPs are encouraged to adopt a risk based approach to compliance with the legislative obligations. These Guidelines provide general guidance to assist C/CSPs that may not already have mature security management practices in place, and provide targeted security advice to manage the specific national security risks of unauthorised access and unauthorised interference to networks and facilities. It is the responsibility of each C/CSP to determine whether or not it is acting in accordance with the legislative obligations. The guidance contained within this document should not be read as enforceable rules. Compliance with the Guidelines is not mandatory in order for C/CSPs to demonstrate compliance with their legislative obligations. Due to the sensitive and fluid nature of national security threats, it is not possible to comprehensively outline the threat sources and threat vectors and appropriate controls and mitigations in this document. A key element of the regulatory framework is the enhanced partnership between Government and C/CSPs and engagement processes to support increased information sharing (including classified information) and increase industry awareness of national security vulnerabilities and risks. Security agencies will supplement the advice provided in this document with tailored and general threat information. Disclaimer This document is intended as a guide and users should seek legal, technical and risk advice as to their own specific needs. The information in this document should not be relied upon as legal advice. The provision of this information does not override the need to observe laws or policies, in particular requirements to protect personal information under Australian privacy law. Telecommunications Sector Security Guidelines 3 Contact information Further information about the Telecommunications and Other Legislation Amendment Act 20xx is available on the Attorney-General’s Department website at www.ag.gov.au/telcosecurity Any questions about the security framework established by this Act (including about these guidelines) should be directed to the Attorney-General’s Department at telco.security@ag.gov.au or on [hotline to be created]. List of acronyms AGD Attorney-General’s Department ASIO Australian Security Intelligence Organisation CAC Communications Access Coordinator C/CSP Carrier, carriage service provider and carriage service intermediary C/NCSP Carrier and nominated carriage service provider CSP Carriage service provider Telecommunications Sector Security Guidelines 4 Overview of the Security Framework Legislative obligations in the Telecommunications Act Security obligation (all carriers, carriage service providers and carriage service intermediaries (C/CSPs)) Sections 313(1A) and (2A) require C/CSPs to do their best to protect telecommunications networks and facilities from unauthorised access and unauthorised interference, including by maintaining competent supervision and effective control over their networks and facilities. Notification obligation (carriers and nominated carriage service provider (C/NCSPs)) Section 314A requires C/NCSPs to notify the Commonwealth Access Co-ordinator (CAC) of proposed changes to their systems and services that could have a material adverse effect on the ability of the C/NCSP to comply with its security obligation. The CAC may exempt a C/NCSP from this requirement (314A(4)) and a C/NCSP may satisfy this requirement by submitting a security capability plan. Industry-government collaboration General guidance and engagement (for all C/CSPs) Administrative Guidance - including these guidelines and other fact sheets as required including: • Information/advice service (Attorney-General's Department website and hotline) • Unclassified and classified industry threat assessments (as appropriate) NB: C/CSPs should also continue to utilise existing fora and mechanisms to engage with Government on threat information and mitigation advice, such as CERT Australia, the Australian Cyber Security Centre (ACSC), the Trusted Information Sharing Netwo rk (TISN) etc. Targeted advice and engagement (for higher priority C/CSPs) • Tailored classified threat assessments and risk mitigation advice • Regular bilateral meetings between the C/CSP and security agencies • Enhanced information sharing between government and industry using mechanisms such as the Telecommunications Expert Group (See page 13 for a description of the factors which will contribute to whether a CSP is considered a higher priority). Compliance and enforcement Regulatory powers in the Telecommunication Act 1. Information gathering power The Secretary of the Attorney-General's Department (AGD), (or the Director-General of Security, Australian Security Intelligence Organisation (ASIO) if authorised), can request information or documents for the purpose of assessing compliance with the security obligation. 2. Power to issue directions to C/CSPs The Attorney-General can direct a C/CSP to do, or refrain from doing, a specified thing, e.g undertake certain risk mitigations, to ensure risks of unauthorised access or interference are managed. A direction can only be issued if ASIO has provided an adverse security assessment and following all reasonable efforts to negotiate an outcome cooperatively. A C/CSP will be notified of the intent to issue a direction and invited to make representations. Civil Penalty regime in the Telecommunications Act The Attorney-General can initiate proceedings in the Federal Court to seek civil remedies for non-compliance with the security obligation, a direction and/or request for information – these include penalties, enforceable undertakings and injunctions. Telecommunications Sector Security Guidelines 5 Key steps to protect your networks C/CSP’s (with the exception of high priority C/NCPs – see page 13) will generally be considered to be meeting their obligation to ‘do their best’ to protect networks and facilities from unauthorised access and interference by following these three steps. 1. Be aware of national security threats to telecommunications environments Security agencies will issue threat assessments to help inform the telecommunications community about current and emerging threats. Other helpful resources on cyber security are listed on page 22. 2. Address the risk of unauthorised interference and unauthorised access Identify valuable information that may be targeted and sensitive parts of your network and facilities that might be vulnerable to unauthorised access and interference. Assess whether you can demonstrate competent supervision and effective control and have measures in place to manage any vulnerabilities and risks. 3. Engage early with government agencies on proposed changes to networks to factor in any security risks and controls Engage with the relevant government agencies about how to manage risks from planned changes to your network, management and operational support or service delivery. Early engagement will enable you to get advice from Government on whether the types of changes you are considering making are likely to expose interference and access vulnerabilities and be of concern to national security agencies. Early engagement will minimise costs for mitigating or remediating risks. Telecommunications Sector Security Guidelines 6 Part 1: General information Implementation of the framework by Government and industry in good faith C/CSPs will be expected to implement the obligations and engage with Government co-operatively and in good faith. For example, C/CSPs required to notify of changes to networks under section 314A of the Telecommunications Act will be expected to provide sufficient information about proposed changes in any notification to allow security agencies to accurately assess any potential national security risks. Government will also work with C/CSPs co-operatively and collaboratively to identify and mitigate risks to Australia’s national security arising from the design, build or operation of telecommunications networks. The Government recognises that mitigation measures to address some security risks to networks may have a cost impact on companies. For this reason, the Government will work closely with C/CSPs through an on-going dialogue based on good faith and cooperation to ensure that the security framework operates in a pragmatic, practicable and cost-effective way for the telecommunications industry. For example, directions powers will only be used as a last resort after a period of discussion and negotiation between Government and the relevant organisation. Key security principles This security framework is based on the following four principles: 1. Protection of telecommunications networks is a shared responsibility between government and industry Owners and operators of telecommunications networks are primarily responsible for ensuring the security of their assets – this is a matter of good corporate governance and business continuity. Owners and operators are best placed to manage risks to their operations and determine the most appropriate strategies to boost resilience. However, even the most informed company is unlikely to have access to the most up to date threat information that is available to security agencies. The Australian Government is the primary source of security threat assessments. It is also a source of research, scientific and technical advice relevant to the protection and resilience of critical infrastructure. 2. Responsibility for security should start at the top of an organisation Security should be a key consideration and responsibility at the most senior management levels of any organisation. It is important that it is considered in all business decision making and that cultural change is driven from the top down – not relegated as the responsibility of the IT Department. It is important that organisations promote a risk management approach to security throughout their organisation. Promotion of a positive culture towards risk is a key measure to help ensure all parts of the organisation are considering security in their business decision making. It is also important that organisations Telecommunications Sector Security Guidelines 7 are not ‘siloed’ – effective communication between areas is important to ensure security is considered early in business decision making. Importantly, cyber risks should be considered as part of general corporate risk management. Good governance is key to management of any risks, including cyber risks. 3. Protection of telecommunications networks should be based on a risk management approach These Guidelines do not specify how telecommunications companies must protect their networks. Instead they encourage a risk-based approach to allow companies to choose the best technical and business solutions. There is no single solution to securing networks and facilities – good security is multi-layered and tailored to the risk. It is not just about particular software or hardware. Good security risk management is a holistic approach that considers people, information and assets. It recognises that cyber security is not just about technology – it is also about good governance and management of people. Good risk management is an ongoing process. It involves establishing a context, determining threats, vulnerabilities and criticality of systems and information, then analysing likelihood and consequence before evaluating and treating significant risks. Key to any risk assessment is an appreciation of how a threat or vulnerability will affect the confidentiality, integrity or availability of networks and information carried over and held on those networks. 4. Security should be built into all processes and systems – not bolted on later Well considered security measures integrated into business systems and processes from the start are ultimately more effective and less costly than security systems added on later. Good security is embedded as part of an organisation’s culture, practices and plans – not implemented as an afterthought. If security is only considered at the end of product design, it can leave systems or business arrangements exposed and add an extra layer of cost and complexity. For this reason, C/CSPs are encouraged to engage with the AttorneyGeneral’s Department (or for high priority C/CSPs engage with ASIO) early in the process of planning significant changes to systems and services which affect sensitive parts of a network and may have national security implications. C/CSPs are also encouraged to engage at any stage if they are uncertain about what parts of a network or system may be vulnerable to unauthorised access and unauthorised interference. What are the national security risks to telecommunications networks? The object of the security framework is to better manage the risk of unauthorised interference and unauthorised access to telecommunications networks and facilities to better protect Australian telecommunications infrastructure, communications and data from national security threats such as espionage, sabotage and foreign interference. Australian telecommunications networks and facilities are attractive targets for malicious actors because of the criticality of telecommunications services to Australia's economic prosperity and social well-being, and the rich source of information carried and stored on these services. Telecommunications Sector Security Guidelines 8 In some cases, national security risks will overlap with common security risks related to the running of a business. The difference lies in how that risk may be exploited by specific threat actors, and the impact it may have on Australia's critical infrastructure. In summary, national security risks relate to possible: compromise or degradation of telecommunications networks compromise of valuable data or information of a sensitive nature, such as aggregate stores of personal data or commercial or other sensitive data impairment of the availability or integrity of telecommunications networks, or the potential impact on other critical infrastructure or Government services (such as banking/finance, health or transport services). A key source of vulnerability is the ICT supply chain because Australian C/CSPs are heavily reliant on global suppliers of equipment and managed services which are located in, and operate from, a range of foreign countries. This can create challenges for implementing controls to mitigate personnel, physical and ICT security risks and therefore make networks and facilities more vulnerable to espionage, sabotage, and foreign interference through unauthorised access and unauthorised interference. Some suppliers and business delivery and operational models may present greater risks than others, due to these and other factors. The objective of the framework is to ensure that risks arising through the supply chain are appropriately identified and adequately managed by C/CSPs. The framework is designed to ensure adequate risk management, not prescribe particular business models or ban particular suppliers or service delivery solutions. Telecommunications Sector Security Guidelines 9 Under the framework C/CSPs will need to consider and manage risks associated with various business delivery and operational models (i.e. outsourcing and offshoring) and implement measures and controls to mitigate the risk of unauthorised access and interference. For this reason compliance with the national security obligation is based on the concepts of C/CSPs being able to demonstrate competent supervision and effective control over their networks, facilities and services. These concepts are described in more detail below and have specific reference to the controls and measures in place to manage the risk of interference and unauthorised access that might arise through outsourcing and offshoring arrangements. Which parts of networks are particularly vulnerable to unauthorised access and interference? Some parts of networks and facilities are generally considered to be more sensitive and at a greater risk of intrusion and interference than other parts because they either store or carry sensitive personal, government or commercial communications and information (e.g. billing systems and lawful interception systems), or because they affect the availability and integrity of the network (e.g. operations support systems). The more sensitive parts of C/CSP’s networks and facilities, which are of greater security interest include, but are not limited to: network operation centres, including infrastructure used to facilitate support of the network lawful interception equipment or operations any part of a telecommunications network that manages or stores: o o o aggregate information about customers aggregate authentication credentials of a significant number of customers administrative (privileged user) authentication credentials for the network or related systems any place in a telecommunications network where traffic belonging to a customer or end user aggregates in large volumes, being either in transit or stored data. additional areas assessed by security agencies to be more sensitive in response to changes in threat, technology and business practices. Further details about each of these areas are included below. As noted above, certain business and operational delivery models pose greater risk of unauthorised access and interference than others, for example outsourcing and offshoring. These risks may be amplified when combined with equipping, managing or providing support to sensitive parts of systems. 1. Network Operations Centres A Network Operations Centre (NOC) contains the function or functions through which network operations are controlled, either as a function distributed among business units, or as a discrete business unit itself. This includes equipment, services, locations and processes used to support the network should this occur outside a NOC. This includes Security Operations Centres (SOCs) if distinct from the NOC (since they also perform key functions of network governance and oversight). Proposals that affect the operation of the NOC or SOC, their oversight, control, and effective supervision, as well as core equipment used must be notified. Telecommunications Sector Security Guidelines 10 2. Lawful interception equipment or operations Any equipment, parts of equipment, or software designed to facilitate the lawful interception of communications on a network, which is permanently installed on the network, or able to be installed on request. For the purposes of this guidance, this also includes hardware or software which supports or facilitates this function. 3. Parts of networks that manage or store an aggregate of information These are the places where information of a sensitive nature is likely to be stored, making the systems hardware and its support/operation of specific security interest. This includes: Aggregate information about a significant number of customers or the network itself. This refers to: o o o Aggregate authentication credentials of a significant number of customers. This refers to: o o Databases which store data in bulk, such as call records or network traffic data. Operations Support Systems (OSS), or Business Support Systems (BSS) and other forms of business customer databases. Proposals affecting the equipment or systems which interact directly and modify the network. Areas of the network which store authentication credentials & encryption keys. The Evolved Packet Core (EPC) and the Home Location Register (HLR/HSS) in mobile networks. Administrative (privileged user) authentication credentials. This refers to: o Places where privileged user credentials regarding the network and support systems themselves are stored and audit and oversight controls are retained. 4. Places where traffic belonging to customers or end users is aggregated in large volumes, either in transit or at rest. Areas where data aggregates may include: Points of interconnection or intersection with other networks, and other areas over which a significant proportion of the traffic on the network travels, in each case where the volume of traffic is, in absolute terms, 15% or greater of the total traffic travelling over the network. Large databases which reside in the core of the network and customer Voice Mail Systems (VMS), large email or message systems. Box 2: Case study – Consequences from the compromise of a ‘sensitive part’ of the network Hackers in Greece infiltrated core components of the largest carrier in Greece’s network to intercept mobile phone conversations. Rogue software was illegally implanted in four of the company’s switches (the computer-controlled component of a phone network that connects two telephone lines to complete a telephone call). This created two parallel streams – one stream went to the correct recipient and the other to other stream to the hacker’s network. This allowed hackers to listen in on conversations, potentially record conversations, and track the locations of key dignitaries as well as members of other political and nonpolitical groups. As switches are at the heart of a telecommunications network, the hackers only needed to take over a few switches to carry out the attack. Telecommunications Sector Security Guidelines 11 What were the consequences? It is not known who the hackers were (including whether trusted insiders were involved or whether it was an external attack) or what conversations were intercepted and the purpose of the interception. However, the list of targets was discovered. It included the phones of the Greek Prime Minister and other high-ranking ministers, government and military officials involved in sensitive political and business discussions. How is this case study relevant to this framework? This case study highlights why the framework is focussed on the sensitive parts of networks – the consequences of a compromise of these parts can be particularly serious. In addition, this particular carrier had inadequate monitoring processes and controls to detect the unauthorised access to its lawful interception system. Under the Telecommunications Sector Security Framework, C/CSPs will need to identify vulnerabilities in their networks and implement appropriate measures and controls to manage those risks. The relationship between C/CSPs and security agencies will be strengthened to minimise the occurrence of these types of security compromises. Who has obligations under this security framework? Amendments to the Telecommunications Act have placed obligations on all C/CSPs to protect networks and facilities from unauthorised interference and unauthorised access (see Part 2). While all C/CSPs will be obliged to protect networks and facilities from unauthorised access and interference, only C/NCSPs are required to notify of changes to systems and services (classified as ‘Category A’ C/NCSPs – see below for further information). ‘Category A’ C/NCSPs will be required to notify Government of key changes to telecommunications systems and services. Security agencies may also work more closely with particularly high risk C/CSPs to assist them to manage potential vulnerabilities to their networks and facilities. This will include developing risk assessments and mitigation strategies for planned changes to networks that pose a high vulnerability to unauthorised access and interference. For those carriage service providers (CSPs) identified as posing a lower risk and classified as ‘Category B’, compliance with the framework will largely be satisfied by implementing some of the key measures outlined below and by following general security threat advice. ‘Category A’ C/NCSPs C/CSPs in this category will be treated as higher priority by government because they own and operate telecommunications infrastructure and are required to provide interception capability. C/CSPs in this category may already have a long established relationship with security and law enforcement agencies because, for example, they are required to submit annual interception plans. Your organisation is a Category A C/NCSP if: You are a carrier or nominated carriage service provider (NCSP) under the Telecommunications (Interception and Access) Act 1979 (TIA Act). Telecommunications Sector Security Guidelines 12 What this means: You will need to 'do your best' to protect networks and facilities from unauthorised access and interference (see Part 2). You will be required to notify of key changes to your telecommunications systems and services unless exempted (see Part 3). Additional engagement for high priority Category A C/NCSPs Within Category A there is a further subset of C/NCSPs that are assessed by security agencies to be an even higher priority. These C/NCSPs will be expected to engage more closely with security agencies to manage national security risks across their networks and facilities. This group is a high priority from a security perspective as they are likely to be more actively targeted and exploited by state-based actors and organised criminals and therefore have an increased risk of espionage, sabotage or foreign interference. The risk assessment will be based on: percentage of market share - the larger the number of customers, the greater the aggregate data base sensitivity of customer base - some customers will have more information of a more sensitive nature being communicated and held on networks and facilities than others - such as government and critical service providers, science and research organisations, large or significant commercial organisations, and large healthcare provider organisations (or their suppliers and business partners), and criticality of the network - for example, where the telecommunications network or service supports the delivery of other critical services, e.g., health, power, water and/or where it provides niche services, e.g. is the only service provider for a mine. Carriers and NCSPs will be contacted and advised if they fall within this higher priority group. What this means: You may have a higher level of engagement with security agencies (you will be advised if this is the case - see part 4). Note the purpose of closer engagement is to foster collaborative and proactive responses to managing national security risks. It is not a compliance monitoring mechanism. You may receive specific threat advice, security briefings and risk mitigation advice from security agencies, which will not be generally available (this will be provided by security agencies on an as needs basis - see part 4). ‘Category B’ CSPs Your organisation is a Category B CSP if: You are not a carrier or nominated carriage service provider under the TIA Act. What this means: You will need to 'do your best' to protect networks and facilities from unauthorised access and interference. You will not be required to notify of changes to your telecommunications systems and services (see section 3) You will not be expected to engage directly with security agencies (see part 4). Telecommunications Sector Security Guidelines 13 These guidelines and additional information made available on the Attorney-General's Department website at www.ag.gov.au/telcosecurity will contain information to help you to fulfil your obligations under the Telecommunications Act (see Part 4). Can a CSP change categories? Security agencies may determine that closer engagement or less engagement is required if your business circumstances change – for example, your organisation experiences a significant change in market share or customer base. CSPs will be advised if they are to be nominated under the TIA Act 1979 and will therefore move from Category B to Category A. C/NCSPs already in Category A will also be advised if additional (or less) engagement is required. Telecommunications Sector Security Guidelines 14 Part 2: What do you need to do to meet your security obligation? Security obligation - C/CSPs are required to do their best to protect telecommunications networks and facilities from unauthorised interference and unauthorised access (sections 313(1A) and (2A) of the Telecommunications Act) for the purposes of security. The legislative framework imposes a universal obligation on all C/CSPs to protect their networks and facilities from national security risks of unauthorised access and interference. A universal obligation is important to ensure all owners and operators of telecommunications networks, facilities and services are taking reasonable steps to protect against national security risks. Overview of the security obligation to protect networks and facilities The national security obligation has two elements - C/CSPs must do their best to protect their networks and facilities from unauthorised access and unauthorised interference to ensure: the confidentiality of communications carried on, and information contained on, telecommunications networks and facilities, and the availability and integrity of telecommunications networks and facilities. The obligation is not absolute and is underpinned by a 'reasonableness' test. The term 'do your best' broadly means taking all reasonable steps to protect your networks and facilities from unauthorised access and interference. What constitutes reasonable steps in a particular circumstance to secure a network or facility will differ depending on the risk factors of that network or facility (see pages 8 – 11). How do you meet your security obligation? As noted in Box 1 Vulnerabilities posed by outsourcing and offshoring arrangements, not all security risks and vulnerabilities will give rise to a national security risk and, as noted on pages 8 – 11, not all parts of networks and systems will pose national security vulnerabilities (although they may give rise to privacy or other risks). Likewise, some C/CSPs are a greater target for malicious actors. Accordingly, C/CSPs are expected to adopt a risk-managed approach to managing risks of espionage, sabotage and foreign interference to their networks and facilities. Risk management is the culture, processes and structures that underpin the effective management of potential opportunities and adverse effects. It is a structured approach to identifying, assessing and controlling risks that emerges during a program or project life cycle. The key standard for risk management is AS/NZS ISO 31000:2009 Risk management – Principles and guidelines. Telecommunications Sector Security Guidelines 15 This risk-management approach should particularly focus on risks posed by arrangements with suppliers (in particular managed service providers) and particular service delivery models (i.e. outsourcing/offshoring) will also expose the C/CSP to difference levels of risk that may need to be managed. For this reason, a key focus of the obligation is on ensuring that regardless of any outsourcing and offshoring solution, a C/CSP is able to demonstrate that it has competent supervision and effective control of its network. In other words demonstrate that is has processes, controls and arrangements in place to manage ‘who’ can access systems, networks and communications. Some parts of networks, facilities and services are more vulnerable than other parts to unauthorised access and unauthorised interference – these parts directly relate to maintaining the availability and integrity of the network and protection of information of a valuable or sensitive nature (i.e. personal, government and commercial). In meeting the national security obligation efforts should be directed towards protecting those more sensitive parts of networks from intrusion – see pages 8 – 11 for examples of sensitive parts of networks. What are competent supervision and effective control? Competent supervision refers to the ability of a C/CSP to maintain proficient oversight of its networks, data and facilities. Competent supervision may be achieved either in-house or by using an independent third party. Competent supervision could include arrangements to maintain: visibility of network and facility operations visibility of data flow and locations awareness of parties with access to network infrastructure, and the ability to detect security breaches or compromises. Telecommunications Sector Security Guidelines 16 External assessments may provide a mechanism for organisations to have their security independently reviewed. The IRAP1 is governed and administered by the Australian Government Australian Signals Directorate. Any Australian organisation (not just Government agencies) can engage an IRAP Assessor to conduct independent ICT assessments against Australian Government policies and guidelines. IRAP Assessors assist organisations to secure their ICT networks by assessing their security compliance and highlighting the information security risks facing their organisation. Penetration or vulnerability testing is another option to assess the vulnerability of a service to unauthorised access or interference. It is important that any penetration test considers both technology and human interaction. You may want to consider using a Council of Registered Ethical Security Testers (CREST) Australia2 approved company when hiring a penetration tester. The companies that CREST certified individuals work for have subjected themselves to audit and scrutiny by CREST Australia, and have signed up to the CREST code of conduct. Effective control refers to a C/CSP's ability to maintain direct authority to ensure that its network and facilities, infrastructure and information stored or transmitted, is protected from unauthorised interference and access. This would include authority over all parties with access to network infrastructure and as noted above the ability to control who has access to network systems, facilities, information and access restrictions. Effective control might include the ability to: direct actions to ensure the integrity of network operations and the security of information carried on them terminate contracts without penalty where there has been a security breach or data breach reasonably attributable to the contracted services or equipment address issues of data sovereignty direct contractors to carry out mitigation or remedial actions oblige contractors to monitor and report breaches to the C/CSP, and re-establish the integrity of data or systems where unauthorised interference or unauthorised access has occurred (for example to confirm accuracy of information or data holdings). Third party assurance may also mean implementing controls which can be tested, and, when fully effective, provide evidence that primary information security requirements have been, or are able to be, satisfied. The Protective Security Policy Framework (PSPF) administered by the Attorney-General’s Department (AGD) provides best practice guidance, in particular INFOSEC-4 and INFOSEC-5. 1 2 Further information is available at www.asd.gov.au/infosec/irap/index.htm Further information is available at http://crestaustralia.org/ Telecommunications Sector Security Guidelines 17 What is unauthorised access or unauthorised interference? For the purposes of this security framework, the obligation to protect networks and facilities from unauthorised access and unauthorised interference only relates to threats to Australia’s national security from espionage, sabotage or foreign interference. By way of example, a C/CSP would need to take reasonable steps to prevent intrusions or breaches within networks or facilities or to minimise the effect of malicious activity, demonstrable by the security controls in place. This will be particularly relevant where activity, if left unchecked, could provide opportunity to compromise the confidentiality, availability or integrity of telecommunications infrastructure or information carried by, or across it. Telecommunications Sector Security Guidelines 18 Risks to be mitigated include physical, personnel and systems. It is not reasonable or appropriate to give all personnel or contractors unfettered access to all parts of a network or facilities or information carried on it. Physical and logical controls need to be implemented along with clear access policies and the ability to track unauthorised access. The term ‘unauthorised access’ should also be understood in line with its meaning within the Privacy Act 1988 (Privacy Act), to the extent that this obligation relates to the confidentiality of communications and information. Although not defined within the Privacy Act itself, the Office of the Australian Information Commissioner has defined unauthorised access to be when personal information is accessed by someone who is not permitted to do so. This includes unauthorised access by an employee of the entity or independent contractor, as well as unauthorised access by an external third party (such as by hacking). Telecommunications Sector Security Guidelines 19 What does it mean to ensure the availability and integrity of telecommunications networks and facilities? Availability is about ensuring that authorised users have access to information, communications and telecommunications networks and facilities when required. An example where networks and facilities are not available would be a denial-of-service attack which prevents the ordinary functioning of the service, which could have serious economic, social or other consequences (particularly in an emergency). Integrity relates to the accuracy and completeness of information and communications, as well as the protection of telecommunications networks and facilities from compromise or unauthorised modification. An example of a breach of integrity would be where a C/CSP’s systems are accessed by a third party and modified to allow remote access by that party. What does it mean to ensure the confidentiality of communications and information? Many C/CSPs are already required to comply with the obligations contained in the Australian Privacy Principles (APPs) in the Privacy Act, which regulate the handling of personal information; in particular, APP 11 that requires C/CSP’s to take reasonable steps to protect the personal information it holds from misuse, interference and loss, and from unauthorised access, modification or disclosure. Additionally, C/CSPs that are covered by the data retention scheme must comply with the Privacy Act in relation to data collected and Telecommunications Sector Security Guidelines 20 retained under that scheme, even where the C/CSP would otherwise be exempt from the Privacy Act. Section 313(1A), on the other hand, creates a new security obligation, which has as its objective the protection of all information carried and stored on networks, including information about the network itself, not just personal information. The new security obligation aims to ensure the confidentiality of other categories of information that are sensitive and vulnerable to unauthorised access and exploitation, including government and business information. This includes intellectual property, information that could provide a competitive advantage, and information of a sensitive nature about a C/CSP’s network, service delivery models and customers. A C/CSP that provides services to large businesses or research organisations (such as universities) may be at a greater risk of espionage, sabotage or foreign interference because of the commercial value of the information held by their clients (such as scientific research). There are a number of controls available to assist C/CSPs maintain confidentiality, including implementing robust access controls to limit who has access to confidential communications and information. For example, access should be restricted to those who are expressly authorised to have access and who require access to do their job (i.e. provide access on a ‘need to know’ basis). Access controls are particularly important for more sensitive parts of networks (see pages 8 – 11), including to mitigate the threat of unauthorised access or interference from an insider (a trusted insider is a person such as an employee, contractor or business partner who uses insider knowledge or access to commit a malicious act to cause harm 3). The requirement to protect the confidentiality of communications and information relates to both information in transit and information being stored on telecommunications networks and facilities. Some storage solutions may present increased risk of unauthorised access and interference. Encryption is important in many circumstances to ensure that information is stored and transmitted in a form that cannot be easily accessed by unauthorised individuals or entities. Encryption methods should be reviewed regularly to ensure they continue to be relevant and effective and are used where necessary. This includes ensuring that the scope of encryption is wide enough so that attackers cannot access another unencrypted copy of your encrypted information. C/CSPs should refer to their existing obligations under the Privacy Act (particularly APP 11 – security of personal information) and the Telecommunications (Interception and Access) Act 1979. C/CSPs must have regard to those obligations in conjunction with, or in addition to, their obligations under this framework. While there may be overlap between the steps that a C/CSP might take under section 313(1A) and APP 11, the steps taken to comply with one obligation will not necessarily mean that the C/CSP has complied with the other obligation. Importantly, the steps a C/CSP will be required to take under s 313 (1A) focuses on protecting the information ‘for the purposes of security’, whereas APP 11 is focussed only on personal information but requires C/CSPs to consider broader sources of risks to that information. Existing policies and procedures to meet confidentiality and privacy obligations will also support compliance with the new security obligation in this framework. For example, the following guidance issued by the OAIC may assist you to identify practical measures you can implement to secure all categories of information: Australian Privacy Principles Guidelines4 3 Further information is available in Managing the insider threat to your business: A personnel security handbook, which is available from www.protectivesecurity.gov.au 4 www.oaic.gov.au/privacy/applying-privacy-law/app-guidelines/ Telecommunications Sector Security Guidelines 21 Guide to securing personal information5 Data breach notification — A guide to handling personal information security breaches 6 Privacy business resource 8: Sending personal information overseas 7 Privacy business resource 9: Ten tips to protect your customers’ personal information8 Privacy business resource 11: Telecommunications service providers’ obligations arising under the Privacy Act 1988 as a result of Part 5-1A of the Telecommunications (Interception and Access) Act 1979 9 The Australian Communications Media Authority has also published privacy guidance. These are the Better practice privacy tips for service providers10. Box 6: Case study – Implementation of related legislative obligations by a hypothetical company Security First Telco An Australian carrier Security First Telco enters into a commercial outsourcing arrangement where another company will provide the network management functions, including supporting critical network elements of the telecommunications company’s infrastructure where all network traffic is routed. Additionally, the company has recently put measures in place to meet data retention obligations, including controls to protect access to stored customer information and traffic data. However, controls are not in place to protect the outsourced company having access to key network transit points where traffic logs can be generated and exported. The proposed obligation to protect the confidentiality of communications and information carried across networks under this framework would also require the carrier to protect communications and information in transit and in use. Resources to help you meet your national security obligation The following Australian Government and international standards and guidelines, if implemented, would in most circumstances be considered as demonstrating reasonable steps to protect networks and information, and competent supervision and effective control of networks and facilities. AS/NZS ISO 31000:2009 Risk Management – Principles and Guidelines11 deals with risk generally. ISO 27001:2013 Information security management 12 helps organisations keep information assets secure. The International Telecommunications Union Recommendation X.1051 Information technology – Security techniques – Information security management guidelines for telecommunications 5 www.oaic.gov.au/privacy/privacy-resources/privacy-guides/guide-to-securing-personal-information www.oaic.gov.au/privacy/privacy-resources/privacy-guides/data-breach-notification-a-guide-to-handling-personal-information-securitybreaches 7 www.oaic.gov.au/privacy/privacy-resources/privacy-business-resources/privacy-business-resource-8 8 www.oaic.gov.au/privacy/privacy-resources/privacy-business-resources/privacy-business-resource-9 6 9 www.oaic.gov.au/agencies-and-organisations/business-resources/privacy-business-resource-11 10 11 12 www.acma.gov.au/theACMA/better-practice-privacy-tips-for-service-providers This standard can be purchased from Standards Australia. This standard can be purchased from Standards Australia. Telecommunications Sector Security Guidelines 22 organizations based on ISO/IEC 2700213 provides guidance on information security management in telecommunications organisations. The Australian Signals Directorate: o Information Security Manual14 is the standard for the security of government ICT systems o Cloud Computing Security15 can help businesses perform a risk assessment and use cloud services securely o Strategies to Mitigate Targeted Cyber Intrusions16 provides information about how organisations can select the best mitigation strategies for their requirements. The Trusted Information Sharing Network (TISN) is Australia’s primary national engagement mechanism for business-government information sharing and resilience building on critical infrastructure resilience. The TISN website includes resources for businesses on protection of critical infrastructure. Information can be found at www.tisn.gov.au The Protective Security Policy Framework (particularly INFOSEC-4 and INFOSEC-5) outlines a range of information to effectively managing protective security risk, including controls. Information can be found at www.protectivesecurity.gov.au. CERT Australia is the primary point of contact within the Australian Cyber Security Centre for cybersecurity incidents affecting major Australian business; it collaborates with over 500 entities to provide them with advice and support. Information about CERT Australia can be found at www.cert.gov.au The Australian Cyber Security Centre is the hub for private and public sector collaboration and information sharing to combat cyber security threats. Information can be found at www.acsc.gov.au The Australian Communications and Media Authority publishes information about legal obligations on C/CSPs. This information can be accessed at www.acma.gov.au under ‘law enforcement’. The United Kingdom Cyber Essentials Scheme: Requirements for basic technical protection from cyber attacks17 is an accessible guide for organisations of all sizes to mitigating the most common internet based threats to cyber security. The United States National Institute of Standards and Technology Framework for Improving Critical Infrastructure Cybersecurity18 includes standards, guidelines, and practices to help owners and operators of critical infrastructure to manage cybersecurity-related risk. It can help organisations determine their current cybersecurity capabilities, set goals for a target level of cyber resilience and establish a plan to improve and maintain cybersecurity. ISACA19 is an independent, non-profit, global association that engages in the development, adoption and use of knowledge and practices for information systems. ISACA provides practical guidance, benchmarks and other tools for all enterprises that use information systems. Does this security obligation apply to existing systems? While the security obligation will have immediate effect from the expiry date of the implementation period, existing systems, networks and facilities in place at the time the security obligation comes into effect that are non-compliant will not be penalised. C/CSPs are not expected to retrofit all systems on commencement of 13 Available at www.itu.int/rec/T-REC-X.1051 Available at www.asd.gov.au/infosec/ism/ 15 Available at http://www.asd.gov.au/infosec/cloudsecurity.htm 16 Available at www.asd.gov.au/infosec/mitigationstrategies.htm 17 Further information is available at www.gov.uk/government/uploads/system/uploads/attachment_data/file/317481/Cyber_Essentials_Requirements.pdf 18 Further information is available at www.nist.gov/cyberframework/ 19 Further information is available at www.isaca.org 14 Telecommunications Sector Security Guidelines 23 this security obligation, except in very rare cases where a significant security vulnerability is found in an existing network that could facilitate acts of espionage, sabotage and foreign interference. In such cases, government agencies will seek to work with the provider to develop cost effective solutions to better manage the risks posed by the existing vulnerability. Subject to how serious the security risk is and how willing the company is to collaborate with security agencies to manage the risk, a direction could be issued by the Attorney-General requiring mitigation measures to be implemented to better manage the risk. Telecommunications Sector Security Guidelines 24 Part 3: What do you need to do to meet your notification obligation? Notification requirement - Carriers and nominated carriage service providers (NCSPs) are required to notify Government of key changes to telecommunications systems and services that could have a material adverse effect on their ability to meet their national security obligation to protect networks and facilities (unless exempted from this requirement). The notification requirement in section 314A of the Telecommunications Act provides a trigger for C/NCSPs to engage with Government early in the design phase of any planned changes to telecommunications systems and services. This is to ensure that consideration is given to whether the change will create new, or exacerbate existing, risks or provide opportunities to address existing vulnerabilities. In this way the notification requirement seeks to facilitate a culture where national security considerations are embedded into business decision making and operations. Consideration by security agencies of notifications does not constitute an endorsement of proposals in any broader security sense (beyond risks to national security). It must not be considered as a substitute for standard business risk assessments, standard due diligence, enterprise security reviews or any other form of assessment that a network operator would usually perform when initiating a new project or change. An overview of the notification obligation is included at Attachment A. Who needs to notify Government of changes to systems? Only C/NCSPs are required to notify Government of changes to systems and services. The notification requirement is limited to C/NCSPs. However, for all CSP’s a key trigger in managing the risk of unauthorised access and interference will be at the point of designing and planning changes to networks and service. At this point, all C/CSPs should assess whether the proposed change to their networks or facilities may adversely impact on their ability to continue to meet their security obligation. Only C/CSPs will be required to engage with Government before making these changes through the notification process. Are exemptions available? The CAC within the Attorney-General's Department may exempt a C/NCSP from any notification requirements or for some types of changes. For example, a large carrier which offers a number of different types of services may be exempted from providing any notifications in relation to a part of their business (for example, a subscription television service), but would still be required to notify of changes to other parts of their business. The details of a partial exemption would be specified in a notice provided to the C/NCSP. There is no application process for C/NCSPs - instead the CAC will decide if and when to grant any exemption and write to the affected C/NCSP advising of the decision to grant the exemption. A decision to grant a full or partial exemption will be based on advice from ASIO having regard to the risk profile of individual companies otherwise required under section 314A of the Telecommunications Act to comply with the notification requirement. The risk assessment will consider factors such as the likelihood of a C/NCSP or class of C/NCSP's Telecommunications Sector Security Guidelines 25 networks, services or systems being vulnerable to unauthorised access and unauthorised interference and the consequences for national security if those risks are realised. As noted above such assessments will likely have regard to the following risk factors: percentage of market share - the larger the number of customers, the greater the aggregate data base sensitivity of customer base - some customers will have more information of a more sensitive nature being communicated and held on networks and facilities than others - such as government and critical service providers, science and research organisations, large or significant commercial organisations, and large healthcare provider organisations (or their suppliers and business partners), and criticality of the network - for example, where the telecommunications network or service supports the delivery of other critical services, e.g., health, power, water and/or where it provides niche services, e.g. is the only service provider for a mine. The CAC may also vary or revoke an exemption based on advice from ASIO, having regard to any changes to security risks and services offered by the C/NCSP and the national security threat environment. Further information on the exemptions process is available in Factsheet [X being developed]. What types of changes should be notified? It is important to keep in mind that not all proposals require notification. This section explains the kinds of changes that do and do not need to be notified. This summary is illustrative and not exhaustive. It will likely require updating from time-to-time to reflect changes in the threat environment, technology and telecommunications infrastructure and methods for delivering telecommunications services. The threshold for triggering the notification requirement is outlined in section 314A of the Telecommunications Act and is intended to capture changes that can increase risk, such as outsourcing arrangements, offshoring equipment and services, changes to services, procuring new equipment and changes to the management of services. The risks to these types of business decisions or methods of delivery may be particularly amplified when they relate to ‘sensitive parts of networks’ (see pages 8 – 11 for further information on sensitive parts of networks that are areas of greater security interest). The legislation limits the scope of the notification requirement to adverse material changes, which incorporates a value judgement about whether the change would have a negative impact of some substance on a C/NCSP’s ability to meet its security obligation. Telecommunications Sector Security Guidelines 26 If in doubt as to what might constitute an adverse material change, C/NCSPs should contact the general hotline [TBA] in the Attorney-General’s Department or submit an online inquiry form to telco.security@ag.gov.au A proposed change includes standard builds which might cover a particular change replicated at many points of a network, and also ‘bulk changes’ – a series of changes that can be treated as one overarching ‘bulk change’. C/NCSPs can submit a single (rather than repeated) notification for a standard build or a bulk change. Standard builds A standard build may comprise consistently procured equipment build or a network addition, which is replicated throughout the network. Notification of the standard build is only required in the first instance, provided the build does not change to a type of equipment that has not been previously submitted to the CAC by that network operator. In instances where a standard build is used, notification should also include details of the geographic locations in which it is intended to be deployed. An example of a standard build would be a build which is replicated across the country. In such a case, a notification of proposal which specifies which equipment will be used, the oversight and control mechanisms and the geographic locations that the build will be deployed in would be sufficient notification for all deployments of the same build (provided no network security risks are identified). Should the standard build change from that notified, a new notification would need to be submitted outlining the changes in the new build. Bulk changes In addition, one notification may be submitted for a standard set of equipment to be used in a network proposal, i.e. a bulk change. This could include all versions of a certain type of networking equipment, and the software/firmware builds that are likely to be deployed on it. Notification could also be supplied for a specific product range which may change incremental versions over time. Once the CAC has considered the proposal covering the product range, the equipment would be able to be deployed on the network without the need to submit a new notification. For example, where security agencies have been previously engaged on a similar change to a network or have previously approved a proposed procurement process, architecture or equipment it may not be necessary to submit a notification for the same type of change. Telecommunications Sector Security Guidelines 27 However, there are some practical limitations to notifications of bulk changes. A notification with an excessive number of equipment types or for an entire vendor’s product range does not amount to notification of a bulk change. Notifiable equipment Box 7: Case Study – Which proposed changes to their systems should the hypothetical company Security First Telco notify to Government? Security First Telco is reviewing proposed changes to their telecommunications systems to decide which changes need to be notified to Government. Examples of changes that should be notified After a risk assessment (based on the guidance in this document), they have decided the following changes are likely to have a material adverse effect on their ability to protect their networks from unauthorised access and interference (i.e. espionage, sabotage and interference) for the following reasons: 1. Engagement of a new billing provider This proposal would likely involve the new billing supplier and a third party, being used by the billing supplier, having access to sensitive customer information during the projects and possibly after the project as part of support arrangements. After discussing the project with Government, possible mitigations activities could include controlling the access any third party company located outside of Australia may have to the personal information and billing data for all of Security First Telco’s Australian customers. 2. A mobile network operator to deploy Long Term Evolution (LTE) technology A mobile network operator plan to deploy LTE would likely mean new or upgraded equipment and involve an equipment supplier or managed service provider to have access to sensitive parts of Security First Telco’s networks, including access to communications. In this instance, possible mitigation activities could include ensuring adequate control and monitoring over levels of access the equipment supplier may have, including remote access arrangements. This would also apply if the network operator were planning to trial new equipment before considering any tender related activity 3. Engagement of an existing supplier to upgrade core routing equipment This plan would likely require a supplier to access or install software on equipment where a significant proportion of the network traffic travels including telecommunications intercepted traffic. In this scenario mitigations actions could address concerns related to unauthorised access to the network real time traffic or interception data. 4. Renewal of a contract not previously notified to Government Security First Telco entered into a contract with a company to manage their data storage solution (which includes all customer details) before they were obliged to notify Government of changes to systems under this framework. Although the new contract would reaffirm the status quo, Security First Telco should notify Government that they are planning to renew the contract with this supplier as this arrangement could affect the ability of Security First Telco to maintain effective control and competent supervision of its networks and services. In most cases, if security agencies have not already identified the current arrangement as potentially Telecommunications Sector Security Guidelines 28 exposing the network to security vulnerability it will likely be assessed and confirmed as not giving rise to security risks. However there may be incidents where security agencies can provide guidance and advice to enhance control and supervision of data stored by the vendor. As noted on page 24, C/CSPs are not expected to retrofit all systems on commencement of this security obligation. However, opportunities such as renewal of a contract may provide an opportunity to better mitigate any existing security vulnerabilities (for example, specification of mandatory security requirements in the contract itself). Examples of changes not required to be notified Through their risk assessment, Security First Telco has assessed that the following changes are not likely to have a material adverse effect on their ability to protect their network and therefore do not need to be notified: 1. Renewal of a contract previously notified to the Government Security First Telco advised the Communications Access Coordinator (CAC) when they first engaged this supplier to provide their data storage solution. However, given the CAC previously advised there were no security concerns with this supplier (because Security First Telco had built in security requirements and protections into the original contract) there would generally be no need to notify again as there would be no change to existing arrangements (i.e. there are no changes to the location of the data storage or contractual requirements). However, if the threat environment has changed (for example if Security First Telco has been advised by security agencies of new security threats) then Security First Telco may need to notify of the renewal of a contract. 2. Construction of new mobile towers by Security First Telco Security First Telco has assessed that proposed construction of further mobile towers is unlikely to have a material adverse effect on their ability to protect their networks from unauthorised access and interference because they are using a standard build, which has been previously notified to the CAC and assessed as not giving rise to security concerns (see page 27 for further information about standard builds). 3. Upgrades to the operations centre Security First Telco is expanding and renovating their operations centre in Australia, including new access restrictions. As there will be no substantial change to existing arrangements (in fact the new access restrictions are likely to tighten physical and logical access and therefore will enhance the company’s ability to protect their network from security risks) there is no need to notify of the changes. 4. Business-as-usual maintenance Security First Telco does not need to notify of ongoing maintenance of legacy systems and infrastructure which do not amount to substantial modifications in network design, operations and service delivery. When should changes be notified? Although the legislation does not specify when a C/NCSP should notify Government of changes, it is in the C/CSP's best interests to notify as early as possible, such as early in the stages of considering a C/NCSP finalising any business plans, contracts or negotiations and before entering into any binding undertakings. Telecommunications Sector Security Guidelines 29 For example, if a C/NCSP is looking at a procurement or acquisition, it is in the best interests of the C/NCSP to notify the CAC before taking any steps as part of the decision-making approach (i.e. before they have approached the market whether by request for quote, tender or otherwise). This will allow security considerations to be built into the proposal from the start - not added later, which is generally more costly and less effective. Early notification is in the best interest of C/NCSPs– allowing security considerations to be factored into the proposal design as early as possible in a cost effective manner. Even the most informed C/NCSP is unlikely to have access to the most up to date threat information. Notification early in the procurement process will avoid unnecessary delay in the progress of procurements and minimise costs associated if procurement plans need to be modified to address security concerns. It is important to ensure that relevant parts of your business are aware when they need to notify Government of changes to systems and services. This could include having the following as parts of your procurement processes: education program within your organisation about your organisation's obligations under this legislation, including security thresholds for reporting providing relevant staff with information about relevant material on the AGD website, including these Guidelines, and thorough understanding of how your company's infrastructure operates, including the security arrangements of any outsourced processes. Box 8: Case study – Consequences of late notification of offshoring plans In an effort to increase their competitiveness and reduce operating costs, an Australian carrier outsourced the operation and maintenance of its network to a new company located overseas. The location of the new company does not pose a security concern but soon after taking control began to migrate the carrier’s network management facilities to a country of security concern. Company personnel located in that country have direct access to all elements of the active network, and there is a significant risk that unauthorised use of this access could be exploited for foreign intelligence purposes, or to disrupt the normal operation of the network. Offshoring raises security concerns because it enables access and control to critical parts of major Australian telecommunications networks outside of Australia, this can facilitate foreign intelligence collection (espionage) and disrupt the network itself (sabotage). Risks arise where control and supervision arrangements have the potential to allow unauthorised actions by third parties, such as theft of customer data or sabotage of the network. When were security agencies engaged? In this case, ASIO was not aware of the offshoring plans until it they were almost complete, which prevented the proactive deployment of relevant mitigation measures (such as building in security and oversight requirements into the contract with the third party). Implementing control measures once offshoring has been implemented can be significantly more costly, time consuming and challenging. A failure to implement control measure can expose significant national security vulnerabilities. If left unmanaged, this could provide foreign intelligence agencies and organised crime groups access to sensitive law enforcement information Telecommunications Sector Security Guidelines 30 stored on networks and reveal the location and movements of protected persons and other important people, such as the Prime Minister. How is this case study relevant to this framework? This case occurred before security obligation or reporting requirements came into effect and highlights that were early notification does not occur telecommunications companies can inadvertently expose their networks to an increased risk of espionage, sabotage and foreign interference activities – which ultimately impacts on customers and potentially damages the reputation of the telecommunication company. How can you notify the Government of changes? A notification should be made using the notification template available at www.ag.gov.au/telcosecurity to the CAC within the Attorney-General’s Department at CAC@ag.gov.au Can you submit a security capability plan instead of multiple individual notifications? A security capability plan may be submitted each year to notify about all proposed changes that are likely to have a material adverse effect on their ability to meet their security obligations to protect networks, instead of notifying the CAC of each individual change to systems and services – see section 314C of the Telecommunications Act. Note that this is entirely optional (for example if it is more efficient for a company and aligns with internal business and reporting processes). What proposed changes should be included in a security capability plans? The types of proposed changes that should be included in a security capability plan are the same as those that need to be notified to the CAC under section 202B of the TIA Act. In other words, security capability plans should only include changes that are likely to have a material adverse effect on the capacity of the C/NCSP to comply with their obligation to protect their networks and facilities from unauthorised access or interference under subsections 313(1A) and (2A). How far in advance should security capability plans forecast? While the legislation does not prescribe how far in advance the plan should capture proposed changes, the number and types of changes included will to some extent be shaped by practical considerations. For example, noting that the CAC has a maximum of 60 days to consider notifications covered in the Plan it may not be feasible to include changes that have tight deadlines for implementation and which require CAC consideration in a shorter timeframe to avoid delaying a project. For such proposed changes, a C/CSP may wish to notify under section 314A of the Telecommunications Act as the CAC must consider the notification within 30 days (unless further information is required). To maximise the benefit of submitting a security capability plan, it should, at a minimum, forecast proposed changes to systems and services for the upcoming 12 months. There is no maximum timeframe for forecasting changes, for example a C/NCSP may be able to forecast planned changes for the next 5 years and these may be included in the security capability plan. C/NCSPs are encouraged to notify proposed major changes such as development of a new service or network as soon as possible, but should include sufficient Telecommunications Sector Security Guidelines 31 detail about each proposal to enable the CAC and security agencies to adequately assess whether the proposed change is likely to give rise to national security risks. What other information can be included in a security capability plan? C/NCSPs may like to include information about their practices, policies or strategies in place to secure their networks from unauthorised access and unauthorised interference. For example, this might include: a description of the risk assessment processes used to identify and manage security risks on networks, systems and services; arrangements and mechanisms in place for overseeing contracted managed service provider compliance with security requirements etc. (for example standard contract terms concerning personnel, logical and physical security requirements and access restriction and how compliance with these terms is monitored and enforced) assurance processes for vetting security practices of a vendor. C/NCSPs may also like to detail any current or proposed mitigation measures or controls to reduce the risk of unauthorised access or interference. For example, this may include access controls in systems or oversight arrangements that are proposed to be built into contracts with third parties. These additional details will help expedite the assessment of the security plan by security agencies by reducing the likelihood that the CAC will need to request additional information from a C/CSP about a proposed change. When can security capability plans be submitted? Security capability plans may be submitted to the CAC at any time of the year. For example, C/NCSPs may choose to submit their security capability plan when they submit an interception capability plan. However, if the two plans are submitted simultaneously they need to remain as separate documents as they are likely to be reviewed by different areas of AGD and ASIO. How can you submit a security capability plan? A security capability plan should be submitted using the template available at www.ag.gov.au/telcosecurity to the CAC within the Attorney-General's Department at CAC@ag.gov.au Can you update a security capability plan if you modify a previously proposed change? No. A C/NCSP may only submit one security capability plan in a 12 month period. If a minor modification is made to a change already notified to the CAC (for example, a change in the intended implementation of the change) then no further notification is required. However, if the modification would be likely to have a material adverse effect on compliance with the security obligations then it must be submitted as a new notification under section 314A. For example, if a notification was previously made to locate a core control system in one country and the proposal changed to locate the system in a different country then the proposal would need to be notified again under section 314A. Can you update a security capability plan if you propose a new change? No. A C/NCSP may only submit one security capability plan in a 12 month period. Telecommunications Sector Security Guidelines 32 The C/NCSP must use the notification mechanism in section 314A of the Telecommunications Act for any additional changes not included in the security capability plan. What happens after you notify Government of proposed changes or submit a security capability plan? Further information on the administrative processes that follow individual notifications is included in the administrative factsheet [X being developed]. Factsheet [X being developed] contains further information on the administrative processes following submission of a security capability plan. Telecommunications Sector Security Guidelines 33 Part 4: When should you engage with security agencies? General threat advice AGD will publish and circulate general threat advice, as required. This may include, for example, updates on latest methodologies to access and interfere with networks or updated mitigation advice. The ASIO Business Liaison Unit (BLU)20, ACSC (www.acsc.gov.au) and CERT Australia (www.cert.gov.au) are other sources of information about threat advice and information. ASIO's BLU provides a public interface between the Australian Intelligence Community and Australian business. The BLU administers a secure website on a free subscription basis. The website contains intelligence-derived unclassified ASIO reporting on the domestic and international security environment as well as physical, personnel and information security advice. The website also contains reports from other Australian Government agencies and international partners. The Australian Cyber Security Centre Threat Report 21 also includes information tailored for Australian organisations about the threats their networks face from cyber espionage, cyber-attacks and cybercrime. The report also contains mitigation and remediation information to assist organisations to prevent, and respond to, the threat. C/CSPs will also be encouraged to share examples of good practice (such as Telstra’s ‘five knows of cyber security’ described on page 16). Specific threat advice C/NCSPs identified as high priority (a subset of Category A C/NCSPs) will be expected to engage more regularly with security agencies. A natural trigger for this engagement will occur at the time of notifying of proposed changes to networks and facilities. Alternatively, security agencies may initiate contact because, for example, they become aware of a particular risk to a network or facility. Security agencies will also seek to develop more collaborative partnerships with this category of C/NCSPs to encourage open dialogue about emerging threats and a partnership to manage these threats. As noted above, the objective of closer engagement with this group is to foster greater collaboration. Security agencies may seek to establish regular ongoing meetings with this group of C/NCSPs to provide general and specific threat advice, discuss proposed changes to systems and services and collaborate to develop mitigations or controls to address security risks. Existing forums such as the Telecommunications experts Group22, co-chaired by the Attorney General’s Department and Department of Communications and the Arts, and TISN23 may also be utilised to discuss threat advice and appropriate control measures. 20 http://www.asio.gov.au/ASIO-and-National-Security/Units/BLU.html https://www.acsc.gov.au/publications/ACSC_Threat_Report_2015.pdf 22 Further information (including membership and terms of reference) will be available at www.ag.gov.au/telcosecurity 23 Further information is available at www.tisn.gov.au 21 Telecommunications Sector Security Guidelines 34 Security agencies may request to have specified personnel within a C/CSP apply for a security clearance. Having cleared staff will allow security agencies to share certain information about network security risks that is classified. While these individuals cannot pass classified information to un-cleared colleagues, they will be able to give informed guidance on identifying and addressing network security risks. If a C/CSP does not have security cleared staff, security agencies will still seek to engage with them and share what information they can about security risks. Operational assistance Effective protection of telecommunications networks and facilities is not just about prevention of threats, it also relates to the overall resilience of an organisation. Monitoring processes to detect cyber-attacks and plans to respond to, and recover from, a cyber-attack are also very important to consider. Further information about developing effective monitoring processes and response plans is available in the resources listed on page 22. A key component of a response plan is knowing when to report a cyber-incident. C/CSPs should consider whether to contact the following organisations if there is an incident or breach in their organisation. CERT Australia We encourage major businesses to report cyber security incidents to CERT Australia, which is part of the Australian Cyber Security Centre. This allows the CERT to form a more accurate view of cyber security threats and make sure that businesses receive the right help and advice. To report an incident: call the hotline on 1300 172 499 email info@cert.gov.au, or visit www.cert.gov.au Australian Cybercrime Online Reporting Network Responsibility for combating different forms of cybercrime in Australia is shared between Commonwealth, state and territory agencies. Cybercrime includes crimes directed at computers or other devices (such as hacking), and crimes where computers or other devices are integral to the offence (such as online scams and fraud). Individuals and small to medium businesses may report suspected cybercrime online through the Australian Cybercrime Online Reporting Network (ACORN) at www.acorn.gov.au. The ACORN is a secure reporting and referral service for cybercrime and online incidents which may be in breach of Australian law. Certain reports will be referred by the ACORN to law enforcement agencies for further investigation. We encourage major businesses to report cyber security incidents to CERT Australia. Telecommunications Sector Security Guidelines 35 Office of the Australian Information Commissioner A robust data breach response plan is important should any data breaches occur (whether or not involving personal information). Further information on responding to data breaches is available in the OAIC resource Data breach notification — A guide to handling personal information security breaches24. C/CSPs are strongly encouraged to report to OAIC any incidents or breaches involving personal information where there is a real risk of serious harm to individuals. The OAIC can provide general information about obligations under the Privacy Act, factors to consider in responding to a data breach, and steps to take to prevent similar future incidents. The OAIC’s Data breach notification — A guide to handling personal information security breaches contains information about notifying and responding to an incident or breach. To report a breach email enquiries@oaic.gov.au Box 9: Case study – Engagement between ASIO and a C/CSP to mitigate security risks An Australian telecommunications company was considering a proposal to introduce a new customer management and billing system. ASIO assessed management and billing systems as a sensitive part of a telecommunications system because they are an aggregate of customer data and information. Through reporting from an overseas partner, ASIO became aware of security concerns associated with the company’s preferred supplier. In particular, that the preferred supplier could facilitate foreign intelligence services gaining unauthorised access to sensitive customer and network information. What engagement occurred? The C/CSP advised ASIO early in the planning stage of the proposal. This meant ASIO could advise the company of the potential national security risks associated with engaging the preferred supplier and the types of mitigation measures that would need to be implemented to manage the risks and provide an adequate level of mitigation. The company acknowledged the potential national security risks and worked with ASIO to revise the criteria in the tender process to incorporate security requirements (as the company had engaged ASIO early in the process it was less complex to incorporate these requirements than if engagement had occurred later in the process). The company also agreed to investigate additional mitigation options to sufficiently hinder actions which may directly harm Australia’s interests. What are the implications for this security framework? In this case the national security risks were managed through early engagement and the establishment of a cooperative partnership between the carrier and ASIO. TSSR seeks to support this cooperative approach through a more formal, transparent and accountable security framework. Development of mitigation to respond to the security risks was a cooperative process between ASIO and the company – allowing development of the most cost-effective and practical measures to mitigate the risk. 24 www.oaic.gov.au/privacy/privacy-resources/privacy-guides/data-breach-notification-a-guide-to-handling-personal-information-securitybreaches Telecommunications Sector Security Guidelines 36 Part 5: How will the Security Framework be administered? A step by step guide Telecommunications Sector Security Guidelines 37 Glossary This glossary provides a description of key terms used in these guidelines. The descriptions are not intended to be a legal definition. The descriptions are also specific for these guidelines only and should not be relied upon in other contexts. Telecommunications Sector Security Guidelines 38 Attachment A: Overview of the notification process