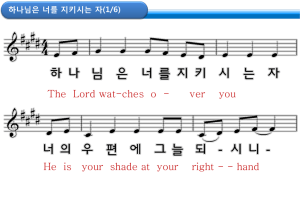
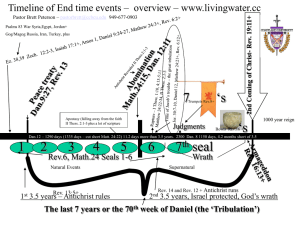
Summary
advertisement

Lesson Plans LabSim for (ISC)² Certified Information Systems Security Professional (Exam CISSP) Version 2.0 Table of Contents Course Overview ........................................................................................................ 3 Section 1.1: Security Management ................................................................... 7 Section 1.2: Risk Analysis ................................................................................... 9 Section 1.3: Security Planning .......................................................................12 Section 2.1: Operational Security Planning ............................................15 Section 2.2: Employee Management ..............................................................18 Section 2.3: Facility Management ..................................................................20 Section 2.4: Auditing and Testing .................................................................24 Section 3.1: Crime and Law .............................................................................27 Section 3.2: Incidence Response ......................................................................30 Section 3.3: Ethics..................................................................................................33 Section 4.1: Cryptography Concepts ..............................................................35 Section 4.2: Hashing .............................................................................................39 Section 4.3: Symmetric Cryptography..........................................................42 Section 4.4: Asymmetric Cryptography .......................................................45 Section 4.5: Implementations ...........................................................................48 Section 5.1: Access Controls ...............................................................................51 Section 5.2: Physical Security .........................................................................53 Section 5.3: Authentication ..............................................................................56 Section 5.4: Authorization ................................................................................59 Section 5.5: Auditing ...........................................................................................61 Section 5.6: Academic Models..........................................................................63 Section 6.1: Trusted Computing ......................................................................65 Section 6.2: Computer Architecture ..............................................................67 Section 6.3: Software Development................................................................71 Section 6.4: Database Management ...............................................................76 Section 7.1: Networking Models and Standards .....................................80 Section 7.2: Network Technology ....................................................................83 Section 7.3: Network Devices ............................................................................87 Section 7.4: Fault Tolerance .............................................................................91 Section 7.5: Internetworking .............................................................................94 ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 1 Section 7.6: Transmission Security ...............................................................97 Section 7.7: Wireless...........................................................................................100 Section 8.1: Cryptosystem Attacks ...............................................................103 Section 8.2: Access Control Attacks ............................................................105 Section 8.3: Availability Attacks ................................................................108 Section 8.4: Trusted Computing Base Attacks .......................................111 Section 8.5: Communication Attacks ........................................................115 Summary ..................................................................................................................117 Appendix A: Approximate Time for the Course .................................118 ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 2 Course Overview This course prepares students for the Certified Information Systems Security Professional certification exam by the International Information Systems Security Certification Consortium, Inc. (ISC)2. To qualify to take the exam, a candidate must have 4 years experience in a security-related field. This course focuses on how to protect organizations’ assets by providing the highest standards of security. Module 0 – Introduction This module introduces the instructor, the requirements for CISSP certification, and the goals of a security program. Module 1 – Security Management This module teaches how to manage security by identifying security needs and creating security policies, and creating a Business Continuity Plan (BCP) and a Disaster Recovery Plan (DRP) to implement preventive and corrective measures. Completing a risk analysis and a Business Impact Analysis (BIA) will help to determine appropriate countermeasures. Module 2 – Operational Security Module 2 explains the day-to-day operational security of the security program. This includes the basics of employee management, facility management, and testing the security program to identify weaknesses in the policies. Module 3 – Law and Ethics Module 3 discusses legal issues regarding cyber crime. Topics include procedures for collecting information and evidence, incident response plans, and an overview of United States and International legal systems. The code of ethics that should be adhered to by a security professional is also presented. ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 3 Module 4 – Cryptography Module 4 covers cryptography from the historical ciphers to the present day technologies, which are hybrids of symmetric cryptography, asymmetric cryptography and hashing. Module 5 – Access Control In Module 5 students will learn the methods to control access to objects. These include access controls, controlling physical access, authentication, and authorization. Auditing, recording user and system activities, is used by organizations to detect unauthorized activities. Students will also learn about several important academic security models that can be used for analysis of security systems and guidelines for implementation. Module 6 – Computing Architecture Module 6 explains the methods used to ensure computer information system remain secure from the design of the computing components, to the development of hardware and software architecture, and management of databases. Module 7 – Networking Security Module 7 discusses the basics of networking security technology. Subjects include network devices, fault tolerance, Wide Area Network (WAN) technologies, security for LAN-based data and also for Web-based applications, and security for wireless implementations. Module 8 – Attacks In Module 8 students will learn that attackers have come up with multiple ways to attack information systems. They include cryptosystem attacks, access control attacks, availability attacks, Trusted Computing Base attacks, and communication attacks. Specific types of attacks for each of these are presented and the countermeasures to protect the system. ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 4 Section 0.1: Introduction Summary The video introduces the video instructor for the Certified Information Systems Security Professional certification exam and the requirements for CISSP certification. Details include: Goals of a security program: o Confidentiality o Integrity o Availability Organizations to be familiar with: o International Information Systems Security Certification Consortium (ISC²) o Common Body of Knowledge (CBK) o National Institute of Standards and Technology (NIST) o International Organization for Standardization (ISO) o Defense Information Systems Agency (DISA) o Generally Accepted System Security Principle (GASSP) CISSP Objectives 3. Security Management Lecture Focus Questions: What are the things a security program must do in order to be effective? What are the respective purposes of maintaining confidentiality, availability, and integrity? What are the main organizations with which IS professionals need to be familiar? ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 5 Video/Demo 0.1.1 Introduction Time 9:14 Number of Exam Questions 5 questions Total Time About 15 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 6 Section 1.1: Security Management Summary In this section, students will learn security management is the overall security vision for an organization to preserve confidentiality, integrity and availability of assets. Under the direction of senior management, security professionals establish security policies for implementation. Concepts covered include: An effective security policy must be: o Planned o Maintained o Used Components of a security policy document include: o Policy o Standard o Baseline o Procedure o Guideline Security planning results in the following documents: o Organization security policy o Business Continuity Plan (BCP) o Disaster Recovery Plan (DRP) o Business Impact Analysis (BIA) o Acceptable Use Policy Senior management’s responsibilities CISSP Objectives 3. Security Management ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 7 Lecture Focus Questions: How do the five components of a security policy document work together to provide an overall security program for an organization? In what situations would you use a security guideline instead of a security procedure? How does a Business Continuity Plan differ from a Disaster Recovery Plan? Which security documents use data from the Business Impact Analysis? What is senior management's role in security management? What is the most important function of the Business Impact Analysis? How are baseline documents used? Video/Demo Time 1.1.1 Security Management 3:21 Number of Exam Questions 11 questions Total Time About 20 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 8 Section 1.2: Risk Analysis Summary This section discusses how by completing a risk analysis of critical assets and types of possible threats the security professional should be able to determine appropriate countermeasures. Details covered include: Terms related to risk analysis: o Asset o Threat o Vulnerability o Threat agent o Attack o Countermeasure o Exposure o Loss o Risk o Residual risk Asset identification Asset valuation o Tangible asset o Intangible asset Major types of asset valuation: o Quantitative o Qualitative Methods to prioritize assets: o Asset classification o Delphi method o Sensitivity vs. risk o Comparative Document procedures relating to classifications and other security procedures ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 9 Risk analysis process When identifying threats consider the sources of threats: o External o Internal o Natural events o Disasters Considerations when selecting countermeasures Responses to risk o Deploy countermeasures o Transfer risk o Accept risk o Reject risk Terms that relate to calculating the cost associated with a risk: o Asset Value (AV) o Exposure Factor (EF) o Single Loss Expectancy (SLE) o Annualized Rate of Occurrence (ARO) o Annualized Loss Expectancy (ALE) o Control Gap (CG) o Residual Risk (RR) CISSP Objectives 3. Security Management 8. Business Continuity Planning Lecture Focus Questions: What is the relationship between the control gap and residual risk? How does the single loss expectancy affect the annualize rate of occurrence? What are the five steps for performing a risk analysis? ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 10 When should a countermeasure not be implemented? When is risk acceptance appropriate? When is risk rejection appropriate? Video/Demo 1.2.1 Asset Identification 1.2.4 Risk Analysis Total Time 12:30 8:25 20:55 Number of Exam Questions 17 questions Total Time About 50 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 11 Section 1.3: Security Planning Summary This section presents information about planning operational security through the use of Disaster Recovery Planning (DRP) to identify short-term corrective actions and Business Continuity Planning (BCP) to identify long-term actions. Also discussed, is the purpose and functionality of a Business Impact Analysis (BIA). Activities required by operational security: o Disaster Recovery Planning (DRP) o Business Continuity Planning (BCP) Objectives of security planning Considerations when incident planning Roles that must be played to ensure that all aspects of DRP and BCP are implemented effectively: o Senior management o Recovery team o Salvage team o Security officers Phases an organization goes through to recover from an incident: o During or immediately following the event o Short-term o Mid-term o Long-term phase Considerations when creating the disaster and business continuity plans Guidelines for plan testing o Test types: o Checklist o Structured walk-through o Simulation ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 12 o Parallel test o Full interruption The role of the Business Impact Analysis (BIA) Categories based on maximum tolerable downtime: o Critical o Urgent o Important o Normal o Non-essential Considerations when analyzing the business impact Categories of business interruption that NIST has identified: o Non-disaster o Disaster o Catastrophe CISSP Objectives 3. Security Management 8. Business Continuity Planning Lecture Focus Questions: What is the highest priority of security planning? How do the primary tasks of the recovery team differ from the primary tasks of the salvage team? How does a parallel test of the security plan differ from a full interruption test? How does the Business Impact Analysis use data from risk management and risk analysis? Why is it important to establish maximum tolerable down time? Video/Demo Time ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 13 1.3.1 Security Planning 1.3.4 Business Impact Analysis Total 11:13 6:24 17:37 Number of Exam Questions 18 questions Total Time About 45 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 14 Section 2.1: Operational Security Planning Summary This section discusses how operational security is the day-to-day implementation of the security program as defined by the security policies. It defines the major components of a security policy, timelines, multiple layers of security and operational tasks. Details include: The role of operational security Defense in depth Components of operational security that help to establish defense and depth: o Change management o Employee management o Security awareness o Physical security The role of change control Organizational roles of an operational security program team: o Senior management o Information System Security Administrator o Application or Database Administrator o Data Entry o Media Librarian o Backup Operator o Restore Operator o Auditor o Process Owner o Technology Provider o Data Owner o Data Custodian o System Owner ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 15 o User or Subject Comparison of roles providing security counterbalance: o Information System Security Administrator vs. Network Administrator o Network Administrator vs. Auditor o Application or Database Developers vs. Application or Database Administrator o Backup Operator vs. Restore Operator o Data Owner vs. Data custodian o User or Subject vs. System Owner CISSP Objectives 3. Security Management Lecture Focus Questions: Why are security awareness and employee management important components of operational security? How does change control enhance security? How do the four components of operational security work together to establish defense and depth in securing an organization? What security principle is being implemented when the Information System Security Administrator is required to report to different management than the Network Administrator? How does role counterbalancing work? How does the role of the Data Owner differ from the role of the Data Custodian? Video/Demo Time 2.1.1 Operational Security Planning 10:05 ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 16 Number of Exam Questions 10 questions Total Time About 30 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 17 Section 2.2: Employee Management Summary This section covers the basics of managing employees to protect company assets. This includes hiring and termination procedures, employee agreements, employee monitoring, and security awareness training. Details include: Employment management practices: o Pre-employment o Security awareness o Termination Security principles: o Least privilege o Separation of duties o Two-man control Common security vulnerabilities: o Fraud o Collusion Employee agreement documents include: o Non-disclosure agreement o Non-complete agreement o Ownership of materials agreement o Acceptable use agreement o Employee monitoring agreement o Exit interview cooperation agreement Documents employees should receive on the first day of employment: o Security policy o Employee handbook o Job description ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 18 CISSP Objectives 7. Operations Security Lecture Focus Questions: How can pre-employment processing improve the security of an organization? Why is security awareness training so important? What is the role of the policy handbook regarding security? What guidelines must be considered when deploying employee monitoring? Why should employees be required to sign employment agreements? Video/Demo Time 2.2.1 Employee Management 7:18 Number of Exam Questions 15 questions Total Time About 30 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 19 Section 2.3: Facility Management Summary This section discusses the points to be considered when selecting a secure facility to protect personnel and assets. In case of a disaster, redundant systems and facilities can assure availability of critical assets to speed recovery. Another important part of facility management is fire prevention, detection, and suppression. Details include: Considerations when choosing or constructing a facility Types of protection that should be considered when choosing or building a facility Proximity to emergency services, and the likelihood of severe weather and earthquakes Evaluating the building construction Location of the data center Infrastructure components: o AC power o Heating o Ventilation o Air conditioning system (HVAC) o Gas o Water Power conditions: o Surge/Spike o Sag/Dip o Brownout o Blackout o Fault o Transient o Electro-magnetic interference (EMI) o Radio frequency interference (RFI) ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 20 Recommendations for preventing or correcting infrastructure problems: o AC power o HVAC system o Water and gas Redundancy solutions: o Mirror o Hot o Warm o Cold o Mutual aid (or reciprocal) agreement o Service bureau Important facts about redundant facilities Recovery terms: o Service Level Agreement (SLA) o Mean Time Between Failure (MTBF) o Mean Time to Repair (MTR) o Maximum Tolerable Downtime (MTD) Types of fire and smoke detectors: o Thermal o Photo-electric o Infrared o Ionized Components required for a fire to burn o Fuel o Oxygen o Heat o Chemical reaction Stages of fire o Incipient o Smoldering o Flame o Heat ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 21 Fire classes and the appropriate suppressant type: o Class A – Water or soda acid o Class B – CO2 or FM200 o Class C – Halon or CO2 o Class D – Dry powders o Class K – Halon, CO2, soda acid Types of automated sprinkler systems for fire suppression: o Wet pipe o Dry pipe o Pre-action o Deluge CISSP Objectives 10. Physical Security Lecture Focus Questions: What is the relationship between redundant site selection to maximum tolerable down time? Why are hot sites typically not implemented? Why might cold sites be of little use when recovering from a disaster? How is EMI different than RFI? What is the difference between a UPS and a redundant power source? Why are positive pressure HVAC system recommended over negative pressure systems? What common disadvantages do mutual aid agreements and service bureaus have as redundant solutions? What is the best type of fire suppression system to use in a data center? Video/Demo Time ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 22 2.3.1 Facility Selection 2.3.3 Redundancy 5:47 4:32 2.3.6 Fire Protection Systems Total 7:11 17:30 Number of Exam Questions 19 questions Total Time About 50 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 23 Section 2.4: Auditing and Testing Summary This section discusses how auditing and penetration testing are used to ensure systems are secure. Audits are used to protect an organization from unwanted change in security settings. Penetration testing attempts to breach security to evaluate the effectiveness of system security and identify vulnerabilities. Details include: Auditing terms to be familiar with: o Audit o Creeping privileges o Privilege escalation o Principle of least privilege o Privilege auditing o Usage auditing o Escalation auditing Penetration testing terms to be familiar with: o Rules of Engagement (ROE) o Penetration testing teams: Red team Blue team White team Types of penetration testing: o Physical penetration o Operations penetration o Electronic penetration Types of penetration tests that depend on the knowledge of the attacker and system personnel prior to attack: o Single blind test o Double blind test o Zero knowledge test ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 24 Stages of penetration testing: o Passive reconnaissance o Active scanning mode o Network enumeration o Target selection o System enumeration o Gaining access o Reporting CISSP Objectives 3. Security Management 8. Business Continuity Planning Lecture Focus Questions: Why are physical penetration and operations penetration tests valuable to system security? What boundaries should you define before starting a penetration test? Why? Why does a double blind penetration test provide more valuable data than a single blind test? What is the difference between network enumeration and system enumeration? How do creeping privileges occur? What countermeasures are used to prevent them? How do audits enhance security? ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 25 Video/Demo 2.4.2 Penetration Testing Time 7:44 Number of Exam Questions 10 questions Total Time About 25 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 26 Section 3.1: Crime and Law Summary In this section students will learn that cyber crime, a criminal act dealing with computers, is on the rise both locally and internationally. Organizations need to be aware of and in compliance with the laws and regulations for the areas in which business is conducted. Details include: Cybercrime major categories: o Computer-assisted o Computer-incidental o Computer-specific Reasons that successful prosecution for computer crime is difficult Procedures to effectively collect information in trans-border crimes Inter-connectivity to other organizations may make an organization vulnerable to a system attack: o Downstream liability o Upstream liability International legal system: o Common law o Customary o Religious American legal system: o Administrative o Criminal o Civil (tort) United States-specific acts and laws that affect business continuity planning and disaster recovery planning: o United Stated Code 18.1030 o Electronic Communications Privacy Act of 1986 ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 27 o Computer Security Act of 1987 o U. S. Federal Privacy Act of 1974 o Healthcare Insurance Portability and Accountability Act (HIPAA) o The Federal Computer Fraud and Abuse Act of 1986 (amended in 1996) o SEC Act of 1934 o Sarbanes-Oxley Act o California Senate Bill 1386 U. S. mechanisms for protecting corporate and individual rights: o Patents o Copyrights o Digital Millennium Copyright Act o Trade secrets o Sales and licensing o Privacy laws CISSP Objectives 9. Law, Investigations, and Ethics Lecture Focus Questions: What are some obstacles that prosecutors face when dealing with cyber crime? How might you be liable to attacks carried out on other organizations? What are the differences between common, customary, and religious laws? What are the different types of punishments associated with administrative, civil, and criminal law? What is the difference between a misdemeanor and a felony? ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 28 How could the Sarbanes-Oxley Act affect your business? What mechanisms can you put in place to protect company intellectual assets? Video/Demo 3.1.1 Legal Issues Time 8:31 Number of Exam Questions 7 questions Total Time About 30 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 29 Section 3.2: Incidence Response Summary This section discusses how to create an incidence response plan to deal with an incident that is a result of a security policy violation or a catastrophic event. This will include identifying members of a Computer Incident Response Team (CIRT) and their roles to act in the event of an emergency. Specialized training is required for evidence collection to be effective for successful prosecution. Details include: Terms to be familiar with: o Security incident o Incident response o Method of Operation (MO) Computer Incident Response Team (CIRT) Keeping evidence admissible Types of evidence: o Best o Secondary o Direct o Conclusive o Opinion o Circumstantial o Corroborative o Real or physical o Documentary o Demonstrative o Hearsay Evidence life cycle Stages of the evidence life cycle: o Collection and identification o Preservation and analysis ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 30 o Storage o Transportation and processing o Presentation in court o Return to owner Special procedures to follow when collecting computer evidence CISSP Objectives 9. Law, Investigations, and Ethics ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 31 Lecture Focus Questions: What are the main objectives of a security response plan? Who are the people that should be included in a CERT and how does that affect incident response? What are the main goals of short-term, mid-term, and long-term incident response? What is the biggest consideration that should be made when deciding to involve the police? What is the importance of the chain of custody? When should it start? Under what circumstances is hearsay evidence considered admissible? What is the correct process for collecting evidence from a crime scene involving a computer or its components? Video/Demo Time 3.2.1 Incident Handling 3:54 3.2.3 Evidence Collection 6:12 Total 10:06 Number of Exam Questions 18 questions Total Time About 35 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 32 Section 3.3: Ethics Summary This section covers the ethics required of a CISSP security professional. The students should be familiar with these general principles of ethical behavior. Details include: Terms to be familiar with: o Ethics o Code of ethics Organizations that publish a code of ethics for security professionals: o International Information Systems Security Certification Consortium (ISC²) o Internet Architecture Board (IAB) o National Institute of Standards and Technology (NIST) CISSP Objectives 9. Law, Investigations, and Ethics Lecture Focus Questions: Following the ISC² code of ethics, how do you decide between conflicting canons? What are the consequences of violating the ISC² code of ethics? What types of actions does the IAB board deem unethical? What are the most important security principles proposed by NIST? ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 33 Video/Demo 3.3.1 Ethics Time 2:34 Number of Exam Questions 5 questions Total Time About 10 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 34 Section 4.1: Cryptography Concepts Summary In this section the students will learn how our security is based on cryptography to protect confidentiality and integrity of data. Historical ciphers are presented and also the components of current cryptographic systems. The students will need to become familiar with several cryptographic terms that are defined to help understand cryptographic concepts. Details include: Terms related to the science of cryptography: o Cryptosystem o Cryptanalysis o Cryptology o Standard Cryptographic implementation can provide the following security services: o Confidentiality o Integrity o Authentication o Non-repudiation Terms used in cryptography: o Cipher o Plaintext o Cipher text o Encryption o Decryption Terms related to cryptography methods or procedures: o Key o Key space o Key clustering o Work factor o Symmetric key ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 35 o Asymmetric key o Public Key Infrastructure (PKI) o Digital signature o Digital certificate o Sealing o Master key/Persistent key/Long-term key o Subkey/Session key/Temporary key o Cryptographic Service Provider (CSP) o Exclusive or (XOR) o Bitwise operation o Hashing o Transposition cipher o Substitution cipher o Block cipher o Stream cipher o Poly-alphabetic o One-time keypad Historical ciphers: o Hieroglyphics o Scytale o Caesar cipher o Vigenere o Vernam o Enigma o Runing key o Concealment o Code Square o Steganography CISSP Objectives 5. Cryptography ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 36 Lecture Focus Questions: Why is non-repudiation an important component of cryptography? What are the advantages of asymmetric key cryptography over symmetric key cryptography? What is the relationship between keyspace and a cryptosystem's work factor? How are digital certificates used in asymmetric key cryptography? When would you sign and seal a document? How do changes in computing power affect cryptosystems? Video/Demo 4.1.1 Cryptography Time 19:24 4.1.2 Cryptography Systems Total 13:08 32:32 ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 37 Number of Exam Questions 5 questions Total Time About 45 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 38 Section 4.2: Hashing Summary This section discusses the use of hashing to ensure the data integrity of files and messages. Details include the following: The role of a hash Terms to be familiar with: o Message digest/digital fingerprint o High amplification/avalanche effect o Collision o Birthday attack Hashing algorithms: o MD-5 o SHA-1 o HAVAL Hashing methods: o Message Integrity Code (MIC) o Message Authentication Code (MAC) o Hashed Keyed Message Authentication Code (HMAC) o Digital signatures CISSP Objectives 5. Cryptography Lecture Focus Questions: What service or function is provided by hashes? How are hashes used in digital signatures? In what ways are HAVAL different from SHA-1? Which method provides greater security? What is collision and why is this condition undesirable in a hashing algorithm? ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 39 Why is high amplification an indicator of a good hashing algorithm? How does HMAC differ from MAC? Video/Demo 4.2.1 Hashing Time 11:11 ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 40 Number of Exam Questions 5 questions Total Time About 20 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 41 Section 4.3: Symmetric Cryptography Summary This section discusses how symmetric cryptography is up to 1000 times faster than asymmetric cryptography and is best used on large amounts of data when confidentiality only is sufficient. The role of symmetric cryptography Issues when implementing symmetric key cryptography systems Types of symmetric key ciphers: o Block cipher o Stream cipher The role of a symmetric block cipher Common symmetric block cryptography methods: o SkipJack o Data Encryption Standard (DES) o Triple DES (3DES) o Advanced Encryption Standard (AES) o Blowfish o Twofish o International Data Encryption Algorithm (IDEA) o Ron’s Cipher v5 or Ron’s Code v5 (RC5) Implementations of 3DES used to create strong cipher text: o EDE2 o EEE3 Electronic Code Book (ECB) Cipher Block Chaining (CBC) The role of a symmetric key stream cipher Common uses for symmetric key ciphers are encryption for: o Keystrokes for think clients o PIN numbers at ATMs o Smart cards ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 42 Terms to be familiar with symmetric key stream ciphers: o Keystream o Linear Shift Feedback Registers (LSFRs) o Keystream generator o Types of input typically fed into a keystream generator: o Initialization vector o Subkey o Pseudo-Random Number Generator (PRNG) Types of symmetric key stream cipher algorithms include: o Ron’s Code (Ron’s Cipher) v4 also known as RC4 (most frequently implemented) o Chameleon o Fish o Helix o SOBER o WAKE Types of symmetric key stream and block cipher combinations: o Output Feedback (FB) o Cipher Feedback (CFB) CISSP Objectives 5. Cryptography Lecture Focus Questions: Why are symmetric key stream ciphers considered to be stronger than symmetric key block ciphers? How is a pseudo-random number generator different than an initialization vector? What advantage does cipher block chaining have over other cipher block encryption methods? ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 43 What is the main disadvantage of symmetric key cryptography? What advantages does AES have over Triple DES? Video/Demo 4.3.1 Symmetric Cryptography Time 8:28 4.3.3 Symmetric Block Ciphers 11:20 4.3.5 Symmetric Stream Ciphers Total 5:20 25:08 Number of Exam Questions 11 questions Total Time About 45 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 44 Section 4.4: Asymmetric Cryptography Summary This section discusses how asymmetric cryptography provides, not only confidentiality, but also strong authentication, integrity and non-repudiation. This allows users to communicate securely. The role of asymmetric cryptography (public key cryptography) Asymmetric key cryptography process and services of each: o Signing o Sealing o Signing and sealing o Mutual authentication and return receipt o Digital envelope Management consideration in implementing asymmetric key cryptography Public Key Infrastructure (PKI) components: o Certificate Authority (CA) o Registration Authority o Cryptographic Practices Statement (CPS) o Certificate Revocation List (CRL) o Subordinate CA The structure of a PKI hierarchy: o Can vary from one to four tiers o Can be collapsed or expanded o Can implement two types of CA hierarchies: Private Public The role of cross certification Agent classes of registration agents: o Class 2 o Class 3 ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 45 o Class 4 o Class 5 Certificate management areas: o Template standard o Certificate validation o Certificate revocation o Certificate Revocation List (CRL) o Key archival o Certificate renewal CISSP Objectives 5. Cryptography Lecture Focus Questions: How do public keys differ from private keys? What is the relationship between the two? How does sealing differ from signing? When is a two tier PKI hierarchy appropriate? How does a hierarchy of trust differ from a web of trust? When should a private hierarchy be implemented? When should a public hierarchy be implemented? How does signing and sealing differ from a mutual authentication and return receipt? Video/Demo Time 4.4.1 Asymmetric Cryptography 15:41 4.4.2 Asymmetric Ciphers 5:35 4.4.3 Diffie Hellman 7:28 4.4.5 Public Key Infrastructure 4.4.6 Certificate Management 16:50 7:01 ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 46 Total 52:35 Number of Exam Questions 17 questions Total Time About 80 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 47 Section 4.5: Implementations Summary In this section students will learn how combining the technologies of symmetric cryptography, asymmetric cryptography, and hashing provides much of our current security. Details include: Strengths and weaknesses of cryptography types: o Symmetric key o Asymmetric key Technologies implemented in LAN- and Web-based environments: o Secure Hyper Text Transport Protocol (S-HTTP) o Hyper Text Transport Protocol Secure (HTTPS) o Domain Name System Security (DNSSec) o Secure Remote Procedure Call (Secure RPC) o Secure Shell (SSH) Encryption technologies implemented in securing e-mail messages: o Privacy Enhanced Mail (PEM) o Message Security Protocol (MSP) o Simple Mail Transport Protocol (SMTP) over SSL o Post Office Protocol v3 (POP3) over SSL o Internet Messaging Access Protocol v4 (IMAP4) over SSL Methods for securing e-mail attachments: o Secure Multipurpose Internet Mail Extensions (S/MIME) o Pretty Good Privacy (PGP) Types of integrity validation and authentication for messages using symmetric key cryptography (a weaker form of authentication): o Message Authentication Code (MAC) ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 48 o Hashed Message Authentication Code (HMAC) o Cipher Block Chaining Message Authentication Code (CBCMAC) o Digital signatures o Secure Electronic Transaction (SET) o Link Encryption o Encrypting File System (EFS) Key management protects the confidentiality of keys used for encryption. Key management areas include: o Key protection o Crypto period o Key strength o Key generation o Distribution o Storage o Key archival o Certificate renewal o Key disposal CISSP Objectives 5. Cryptography Lecture Focus Questions: For expired keys, when should you issue new keys? When should you reissue the expired keys? What are two ways that the M of n function can be used in key archival? How do distribution methods vary for symmetric and asymmetric keys? How can symmetric and asymmetric cryptography be used together? ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 49 What are the advantages of symmetric key cryptography over asymmetric key cryptography? Video/Demo Time 4.5.1 Cryptographic Implementations 4.5.3 Key Management Total 12:27 5:50 18:17 Number of Exam Questions 14 questions Total Time About 40 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 50 Section 5.1: Access Controls Summary This section discusses access controls, which limit a subject’s access to objects. Details include: Types of access control: o Administrative o Technical o Physical Characteristics for access controls: o Preventive o Deterrent o Detective o Corrective o Recovery o Compensative Considerations when implementing access control in multiple layers and of different types CISSP Objectives 1. Access Controls Lecture Focus Questions: How does authentication differ from authorization? What are the differences between administrative, physical, and technical access controls? How are corrective and recovery access controls similar? How can layering improve access control implementation? How do preventive access controls differ from deterrent access controls? ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 51 Video/Demo Time 5.1.1 Access Control 4:50 Number of Exam Questions 1 question Total Time About 10 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 52 Section 5.2: Physical Security Summary In this section students learn how restricting physical access to facilities and computer systems is an organization’s first line of defense. Details include: Types of physical access controls: o Doors o Door locks o Security guards o Guard dogs o Closed-circuit television (CCTV) o Fences and barriers o Mantraps o Lighting o Sensors o Physical Intrusion Detection and Assessment System (PIDAS) Implementing a layered defense system Removable media types: o Tape drives o CD/DVD writers o Removable hard drives o Zip or floppy drives o Flash or memory sticks o Smart cards Recommendations and terms to be familiar with when managing removable media: o Library-based inventory control o Sheep dip system o Sanitation o Cleaning ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 53 o Degaussing o Purge or sanitization o Destruction CISSP Objectives 10. Physical Security ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 54 Lecture Focus Questions: What advantages do security guards give you over various physical and technological controls? What can be added to a mantrap to increase its effectiveness? The use of guard dogs should be limited to which area of your facility? What two purposes are served by closed-circuit television? Why do removable media drives pose a security threat? What is the difference between cleaning and sanitizing? Why doesn't deleting files from a hard disk offer sufficient protection against disclosure? Video/Demo Time 5.2.1 Physical Security 7:50 Number of Exam Questions 16 questions Total Time About 30 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 55 Section 5.3: Authentication Summary This section discusses providing authentication credentials to access an object. Details include: Three ways a user can prove identity to an authentication server are: o Type 1: Something you know o Type 2: Something you have o Type 3: Something you are To increase security, you can use a combination of authentication methods: o Two-factor, Multi-factor o Strong o Mutual Methods to improve the security of password authentication: o Implement a strong password policy o Educate user on how to create and remember strong passwords o Use account lockout to limit the number of attempts a user has to enter the password o Protect access to the password file o Train user to create complex passwords that are easy to remember o Consider restricting password lifetime Weaknesses of smart cards: o Microprobing o Software attacks o Eavesdropping o Fault generation Considerations when implementing biometrics Measures of the effectiveness of a biometric solution ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 56 o False negative o False positive o Crossover rate o Processing rate Advantages and disadvantages of Single Sign-on (SSO) SSO systems are: o Kerberos o SESAME CISSP Objectives 1. Access Controls Lecture Focus Questions: Which form of authentication is generally considered the strongest? What are common attributes examined in a biometric system? What is the difference between synchronous and asynchronous token devices? What is the difference between strong authentication and two-factor authentication? How do behavioral biometric systems work? What types of information do they use for authentication? What types of attacks can be directed against smart cards? Which biometric error type is the most severe (Type I or Type II)? Why? What additional benefits does SESAME provide over Kerberos? Video/Demo Time 5.3.1 Authentication 12:20 ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 57 5.3.4 Single Sign-on Total 7:01 19:21 Number of Exam Questions 18 questions Total Time About 50 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 58 Section 5.4: Authorization Summary In this section students will learn how authorization is implemented through privileges and permissions to identify the level of access granted to a subject. Details include: Authorization types are: o Centralized o Decentralized o Hybrid Commonly used access control models: o Mandatory Access Control (MAC) o Discretionary Access Control (DAC) o Role-Based Access Control (RBAC) o Rule-Based Access Control Use the principle of least privilege. Common forms of privileges are: o Implicit deny o Explicit allow o Explicit deny CISSP Objectives 1. Access Controls Lecture Focus Questions: What are the advantages of a centralized authentication system? Which access control model uses a matrix? Which method uses classifications labels? How does role-based access control differ from rule-based access control? ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 59 What is the best security configuration for a new system? What three components are required for a lattice? In what ways does a lattice protect data better than a matrix? Video/Demo 5.4.1 Authorization Time 12:14 Number of Exam Questions 15 questions Total Time About 30 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 60 Section 5.5: Auditing Summary In this section students will discover that organizations use auditing to record user and system actions. Auditing can be used as a preventive method by informing users that their activities are being logged or can be done in a more passive manner as a detection security system. CISSP Objectives 1. Access Controls Lecture Focus Questions: How can auditing be a preventative security measure? In addition to defining the actions to record in an audit log, what else must you do to make auditing effective? What problems are associated with logging too many events in the audit trail? Why is auditing considered to be a passive detection system? What purposes can audit trails serve other than detecting unauthorized activities? Video/Demo Time 5.5.1 Auditing 1:27 Number of Exam Questions 6 questions Total Time About 10 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 61 ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 62 Section 5.6: Academic Models Summary This section discusses access control models used for the analysis of security and guidelines for the implementation of system security. Details include: Significant academic security models: o Bell-LaPadula o Biba o Clark-Wilson o Brewer and Nash Module/Chinese Wall o Take-Grant CISSP Objectives 6. Security Architecture Lecture Focus Questions: In the Bell-LaPadula model, how does the * property differ from the strong * property? Which academic model(s) address confidentiality? Integrity? Which model addresses conflict of interest? Which model(s) are examples of Mandatory Access Control (MAC)? What are the integrity goals included in the Clark-Wilson model? What are the requirements for the Clark-Wilson model? Video/Demo Time 5.6.1 Academic Models 10:23 ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 63 Number of Exam Questions 3 questions Total Time About 20 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 64 Section 6.1: Trusted Computing Summary This section discusses how a Trusted Computing Base (TCB) is used to ensure that computer information systems remain secure at all times by defining the design, assembly, installation and configuration of the system. Details include: TCB is based on the following models: o State machine o Trusted recovery o Information flow o Non-interference Ways to verify a system and its components fall within the TCB perimeter: o Assurance o Certification o Accreditation o Provisional accreditation Important terms to know are: o Subject o Object o Access o Security domain Evaluation criteria standards: o Trusted Computer Security Evaluation Criteria (TCSEC) o Information Technology Security Evaluation Criteria (ITSEC) o Common Criteria (CC) Facts about the Red Book also known as the Trusted Network Interpretation (TNI) ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 65 CISSP Objectives 6. Security Architecture Lecture Focus Questions: What are the defining qualities of the state machine? What should take place in the event of a system restart? According to the trusted recovery model, what should happen in the case of a security breach? How does certification differ from accreditation? What is the difference between provisional and full accreditation? Which evaluation criteria use different classes for functionality and assurance? What is a major limitation of the TCSEC criteria compared to the ITSEC criteria? What are two disadvantages to obtaining a higher classification level with any evaluation criteria? Video/Demo 6.1.1 Trusted Computing Time 10:37 Number of Exam Questions 18 questions Total Time About 40 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 66 Section 6.2: Computer Architecture Summary This section covers the basics of computer architecture. This will include discussions of hardware and operating system architecture. Hardware architecture of computer systems is designed to support the security requirements of the trusted computing base (TCB) and allow for secure computing. Main components of a CPU o Arithmetic Logic Unit (ALU) o Registers o Control unit Types of storage: o Random Access Memory (RAM) o Buffers (registers) o Cache o Virtual memory o Secondary storage The role of the Virtual memory Manager (VMM) Terms that relate to computer architecture: o Memory Architecture Memory mapped I/O address Physical segmentation Base address Relative address o Physical Architecture Address bus Data bus o Features of modern operating systems: Multithreading Multitasking Multiprocessing ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 67 Symmetric Asymmetric Concepts used by secure operating systems: o Layering o Ring architecture o Hiding o Isolation o Virtual machine ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 68 Process states of an application: o Stopped o Sleeping o Waiting o Running o Ready Actions to harden the operating system and the device CISSP Objectives 6. Security Architecture Lecture Focus Questions: What are the steps of the processing cycle? What is the difference between dynamic RAM, ROM, static RAM, and EEPROM? While examining system events for a computer, you notice that a page fault has been logged. What has happened? What is the role of the virtual memory manager? How does physical segmentation differ from logical segmentation? How does each provide a level of security? What is the difference between multitasking and multithreading? How can asymmetric multiprocessing provide security? What three principles must a security kernel satisfy? Video/Demo Time 6.2.1 Hardware Architecture 10:23 6.2.3 OS Architecture 10:10 Total 20:33 ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 69 Number of Exam Questions 7 questions Total Time About 35 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 70 Section 6.3: Software Development Summary This section discusses the fact that applications can introduce vulnerabilities into information systems. Several methods have been implemented at each phase of application development to ensure security. Details include: Secure planning models: o Ad-hoc o Waterfall planning o Structured programming o Prototype o Object-oriented programming o Spiral o Clean room o Extreme programming o Computer-Aided Software Engineering (CASE) Secure phases of application development: o Initial concept o Alternative evaluation o Project initiation o Functional design o Development and coding o Release o Maintenance o End of life Concepts to be familiar with: o Application vulnerability life cycle o Code escrow o Change control Mechanisms programmers can use to improve security: o Input validation ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 71 o Sandbox o Signed software o Check point o Save point o Application backup o Fail secure o Fail safe o Fail soft o Fail-over cluster ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 72 Problems that are typical in software development: o Buffer overflow o Back door o Excessive permissions o Unprotected temporary files Different levels of programming languages: o First Generation Language (1GL) o Second Generation Language (2GL) o Third Generation Language (3GL) o Fourth Generation Language (4GL) o Fifth Generation Language (5GL) Object-oriented languages contain three main functions: o Classes o Objects o Messages Vocabulary when working with object-oriented programming: o Methods o Procedure o Data o Polymorphism o Polyinstantiation o Cohesion o Coupling o Transformation Process (TP) o Constrained Data Item (CDI) o Unconstrained Data Item (UDI) o Active Content o Integrity Verification Procedures (IVP) Object-oriented languages: o C programming languages o Java ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 73 Other types of languages and scripts: that do not deal with traditional programming codes: o Visual programming languages o Hypertext Markup Language (HTML) o Javascript (JS) CISSP Objectives 4. Applications Security ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 74 Lecture Focus Questions: How does the spiral model combine the waterfall model and the prototype model? How do object-oriented languages simplify development and improve software quality? Why is change control necessary? What is the difference between a save point and a check point? How do temporary files present a security risk? Why do programmers sometimes add back doors during development? What is the difference between interpreters, compilers, and assemblers? Video/Demo Time 6.3.1 Software Development 10:00 6.3.2 Object Oriented Programming Total 4:01 14:01 Number of Exam Questions 11 questions Total Time About 35 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 75 Section 6.4: Database Management Summary This section discusses the basics of database management. When databases are written securely they can help to protect the confidentiality and integrity of information assets. The integrity of data in a database is ensured through rules imposed by the database management system and through secure database scripting techniques. A basic overview of distributed processing is also presented including multiple standards of technology that have been put in place to regulate and standardize distributed object-oriented systems. Databases are usually based off of one of the following types of databases: o Relational o Hierarchical o Distributed Types of Artificial Intelligence (AI) systems: o Expert system o Artificial Neural Network (ANN) The role of the Database Management System (DBMS) Key terms related to Database Management Systems: o User Database o Data Warehouse o Data Mark o Data Mining o Metadata o Data Normalization o Distributed Processing o Verification o Validation o Data Dictionary ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 76 o Schema o Query o Query Language o View o File o Open Database Connector (ODBC) o Polyinstantiation Relational Database Management Model terms: o Table o Tuple (also referred to as a field) o Attribute o Primary Key o Foreign Key o Cell (also referred to as an element) Issues to aware of when protecting data integrity: o Input Validation o Locking o Deadlocks o Transaction Processing Programmers should ensure that the change meets all of the criteria define by the ACID test: o Atomicity o Consistency o Isolation o Durability The role of distributed object-oriented processing Standards of technology used to regulate and standardize distributed object-oriented systems: o Component Object Model (COM) o Distributed Component Object Model (DCOM) o ActiveX o .NET o .NET Passport ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 77 o Enterprise JavaBean (EJB) o Object Resource Broker (ORB) o Common Object Resource Broker Architecture (CORBA) Additional methods of distributed processing: o CGI script o Cookie Persistent Session First-party Third-party CISSP Objectives 4. Applications Security ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 78 Lecture Focus Questions: What are the main differences between hierarchal, distributed, and relational databases? Which AI system type is best used to analyze concrete data with a discrete number of options? What functions are provided by the database management system? How can database views be used to provide a measure of security? How are a primary key and a foreign key different? How does locking protect the integrity of a database? How does locking sometimes lead to problems in query processing? When using transactions, what conditions must be met before changes are committed? How does Java use the sandbox to provide security? How do cookies pose a security threat? Which CIA triad component can be compromised by cookies? Video/Demo Time 6.4.1 Databases 17:31 6.4.4 Distributed Processing Total 6:54 24:25 Number of Exam Questions 16 questions Total Time About 45 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 79 Section 7.1: Networking Models and Standards Summary In this section students will review the basics of the following networking models and standards: OSI model layers: o Application o Presentation o Session o Transport o Network o Data Link Logical Link Control (LLC) Media Access Control (MAC) o Physical TCP/IP model layers: o Application o Host-to-host o Internet o Network Access TCP/IP protocols: o Transport Control Protocol (TCP) o User-Datagram Protocol (UDP) o Address Resolution Protocol (ARP) o Internet Control Message Protocol (ICMP) o Internet Group Management Protocol (IGMP) Institute of Electrical and Electronics Engineer (IEEE) committees: o 802.1 o 802.2 o 802.3 o 802.4 ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 80 o 802.5 o 802.6 o 802.7 o 802.8 o 802.9 o 802.10 o 802.11 o 802.12 o 802.15 o 802.16 o 802.20 o 802.22 CISSP Objectives 2. Telecommunications and Network Security Lecture Focus Questions: What functions are performed by the Data Link layer? Which devices operate at the Network layer? How does the TCP/IP Network Access layer relate to the OSI model? What are the differences between TCP and UDP? How are they the same? What function is performed by the Address Resolution Protocol (ARP)? Which IEEE committee defines standards for Ethernet? Wireless networking? Video/Demo Time 7.1.1 The OSI Model 9:27 7.1.3 The TCP/IP Model 6:49 ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 81 7.1.5 IEEE Standards Total 2:55 19:11 Number of Exam Questions 2 questions Total Time About 30 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 82 Section 7.2: Network Technology Summary This section overviews networking technologies. Topics include presentations on signaling, media access methods, networking components, and topologies. Students must have a basic and broad understanding of networking technology to plan adequate security measures to protect an information system. Details include: Network media: o Wireless o Twisted pair o Coaxial o Fiber optic Media access methods: o Carrier Sense, Multiple Access/Collision Detection (CSMA/CD) o Carrier Sense, Multiple Access/Collision Avoidance (CSMA/CA) o Token passing o Polling Network classifications: o Local Area Network (LAN) o Metropolitan Area Network (MAN) o Wide Area Network (WAN) Network classification based on the role of network devices: o Peer-to-Peer o Client/Server Types of multiplexing: Time-division o Statistical time-division o Frequency-division ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 83 Common physical topologies: o Bus o Ring o Star o Mesh o Hybrid CISSP Objectives 2. Telecommunications and Network Security ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 84 Lecture Focus Questions: What is the difference between wave frequency, amplitude, and phase? How are synchronous and asynchronous communication different? What are the main types of weaknesses involved in networking? Which twisted pair cable rating(s) are appropriate for 100 megabit Ethernet? Which media type is most resistant to EMI and eavesdropping? Which media type is the most susceptible? How does a plenum area pose a safety risk in the event of a fire? How does CSMA/CD differ from CSMA/CA? What two features are provided by the dual rings of FDDI? How many devices are affected by a cable break in a physical bus topology? Physical ring? Physical star? How are physical and logical topologies different? Video/Demo Time 7.2.1 Signaling 10:20 7.2.3 Networking Media 7.2.5 Media Access 7:27 16:38 7.2.7 Network Technologies Total 11:31 45:56 Number of Exam Questions 9 questions ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 85 Total Time About 70 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 86 Section 7.3: Network Devices Summary This section covers the network devices and systems that establish the information systems infrastructure. Topics include: Common internetworking devices: o Repeater o Hub o Wireless Access Point WAP o Switch o Bridge o Router o Gateway Segmenting the network o Collision domain o Broadcast domain Firewall types: o Generation one – packet filtering firewall o Generation two – application layer firewall o Generation three – stateful inspection firewall o Generation four – dynamic packet filtering firewall o Generation five – kernel proxy filtering firewall Methods of placing or deploying firewalls: o Screened host o TCP wrapper o Screened subnet o Bastion or sacrificial host NAT Address Translation (NAT) Types of intruder detection: o Intrusion Detection Systems (IDS) types: Network IDS Host IDS ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 87 o Intrusion Protection Systems (IPS) CISSP Objectives 2. Telecommunications and Network Security ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 88 Lecture Focus Questions: How are hubs and switches different? What are the differences between collision domains and broadcast domains? How many collision domains are on a switch? How many broadcast domains? What is a multi-homed firewall? Which firewall type can examine the entire contents of a message? What type of devices should be placed inside a demilitarized zone (DMZ)? How does NAT provide a measure of security to network devices? What is the difference between IDS and IPS? How are network-based IDS and host-based IDS different? How is a honey pot used? Video/Demo Time 7.3.1 Network Devices 7:48 7.3.3 Firewalls 6:46 7.3.4 Firewall Types 8:42 7.3.6 Network Address Translation (NAT) 7:25 7.3.8 Intrusion Detection Systems (IDS) Total 10:55 41:36 Number of Exam Questions 16 questions Total Time About 70 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 89 ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 90 Section 7.4: Fault Tolerance Summary In this section the students will review redundant information systems and methods of backup to protect the availability of valuable information assets. Details include: Levels of RAID: o RAID 0 (striping) o RAID 1 (mirroring) o RAID 2 (bit-level parity) o RAID 3 (byte-level parity) o RAID 4 (block-level parity) o RAID 5 (striping with distributed parity) o RAID 10 (also called RAID 0+1) Methods of providing system redundancy: o Mirroring o Disk duplexing o Shadowing o Journaling o Electronic vaulting o Backups o Network Load Balancing (NLB) o Server clusters o Code escrow Redundant components: o Dual components o Mean Time Between Failure (MTBF) o Hot spare o Cold spare o Hot-swappable Backup methods o Full ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 91 o Incremental o Differential o Copy o Daily Common backup strategies: o Full Backup o Full + Incremental o Full + Differential Electronic vaulting: o Online tape vaulting o Remote journaling o Database shadowing CISSP Objectives 2. Telecommunications and Network Security Lecture Focus Questions: What is the difference between RAID 1 and RAID 5? Which RAID level does not provide fault tolerance? Which RAID level does not provide an increase in performance? What is the difference between a cold spare and a hot spare? What is the difference between a full + incremental backup and a full + differential backup? Why can't you combine incremental and differential backup methods? Which backup methods do not reset the Archive bit? Where should backup media be stored for maximum security? Why should you test your restore methods? ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 92 Video/Demo Time 7.4.1 Redundancy 13:19 7.4.4 Backups 10:40 Total 23:59 Number of Exam Questions 17 questions Total Time About 55 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 93 Section 7.5: Internetworking Summary This section discusses internetworking using Wide Area Network (WAN) technologies and Remote Access. Details include: Common WAN transmission media types: o Plain Old Telephone Service (POTS) o T-1 o T-2 o T-3 o T-4 o E-1 WAN service options: o Public Switched Telephone Network (PSTN) o Leased lines o X.25 o Frame relay o Switch Megabit Data Service (SMDS) o Asynchronous Transfer Mode (ATM) o Integrated Services Digital Network (ISDN) o Cable o DSL Multiprotocol Label Switching (MPLS) Voice over Internet Protocol (VoIP) Remote access (RAS) o Protocols used to establish a dial-up connection: The Serial Line and Interface protocol (SLIP) Point-to-Point Protocol (PPP) o Protocols to authenticate users when using dial-up connections: Password Authentication Protocol (PAP) Shiva Password Authentication Protocol (SPAP) ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 94 Challenge Handshake Authentication Protocol (CHAP) Microsoft Challenge Handshake Authentication Protocol version 1 (MS-CHAP v1) Microsoft Challenge Handshake Authentication Protocol version 2 (MS-CHAP v2) Extensible Authentication Protocol (EAP) Protected Extensible Authentication Protocol (PEAP) Light-weight Extensible Authentication Protocol (LEAP) o Features to reduce cost and improve performance: Caller ID Callback Centralized remote access o Protocols for centralized remote access: Remote Authentication and Dial-In User Service (RADIUS) Terminal Access Controller Access Control System (TACACS) DIAMETER CISSP Objectives 2. Telecommunications and Network Security Lecture Focus Questions: Which WAN services use analog connectivity? What is the difference between basic rate and primary rate ISDN? What are the functions of a remote access server? How are SLIP and PPP different? ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 95 What advantages are provided by EAP over other forms of authentication? How can caller ID and callback be used to improve remote access security? In a RADIUS system, which component provides authentication for remote access clients? Video/Demo 7.5.1 WAN Technologies Time 5:53 7.5.3 Remote Access Total 11:54 17:47 Number of Exam Questions 7 questions Total Time About 40 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 96 Section 7.6: Transmission Security Summary In this section students will learn the basics of security for both LAN-based and Web-based transmissions. VPN technology is used for a LAN-based information flow and uses common tunneling protocols and IPSec for encryption. SSL and TLS are used to provide security for data in transit for Web-based applications. Details include: Virtual Private Network (VPN) tunneling protocols: o Point-to-Point Tunneling Protocol (PPTP) o Layer 2 Forwarding (L2F) o Layer 2 Tunneling Protocol (L2TP) o Internet Protocol Security (IPSec) IPSec protocols: o Authentication Header (AH) provides authentication o Encapsulating Security Payload (ESP) provides encryption o Internet Key Exchange (IKE) negotiates the connection IPSec modes of operation: o Transport mode o Tunnel mode The role of Secure Socket Layer (SSL) The role of Transport Layer Security (TLS) CISSP Objectives 2. Telecommunications and Network Security Lecture Focus Questions: Which VPN technologies operate at OSI model layer 2? What is the difference between AH and ESP? ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 97 What is the function of IKE in IPSec? What is the difference between IPSec tunnel mode and transport mode? How can you tell that a session with a Web server is using SSL? Why are server certificates required in SSL and TLS? What additional benefit is provided by requiring client certificates in TLS? ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 98 Video/Demo Time 7.6.1 Virtual Private Network (VPN) 7.6.4 SSL and TLS Total 17:57 7:26 25:23 Number of Exam Questions 17 questions Total Time About 50 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 99 Section 7.7: Wireless Summary This section discusses the major concerns of wireless devices and wireless architecture. Wireless networks are inherently insecure and require much attention regarding security. 802.11x standards are presented as well as the transmissions technologies they employ. Common security implementations to protect a wireless network are discussed. Details include: Transmission technologies used by wireless standards: o Frequency Hopping Spread Spectrum (FHSS) o Direct Sequence Spread Spectrum (DSSS) o Orthogonal Frequency Division Multiplexing (OFDM) o Infrared Comparison of specifications of 802.11a, 802.11b, and 802.11g Components of a wireless network: o Station (STA) o Access Point (AP) o Infrastructure o Basic Service Set (BSS) o Independent Basic Service Set (IBSS) o Distribution System (DS) o Service Set Identifier (SSID) o Basic Service Set Identifier (BSSID) Terms to help understand wireless security mechanisms: o Initialization Vector (IV) o Pairwise key o Groupwise key o Key rotation o Message Integrity Check (MIC) o Ciphersuite ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 100 Implementations of security for wireless networking: o Wired Equivalent Privacy (WEP) o Wi-Fi Protected Access (WPA) o Wi-Fi Protected Access 2 (WPA2) Methods used for authentication with WEP, WPA, and WPA2: o Open o Shared secret o 802.1x Comparison of the following wireless security implementations: o WEP o WPA o WPA2/RSN/802.11i Wireless implementations (from least secure to most secure): o Basic protections o Static WEP o Dynamic WEP o Wi-Fi Protected Access Pre Shared Kay (WPA-PSK) o Wi-Fi Protected Access (WPA) o Wi-Fi Protected Access 2 (WPA2) CISSP Objectives 2. Telecommunications and Network Security Lecture Focus Questions: How are FHSS and DSSS different? What are the different frequency ranges for ISM and UNIBAND? Which wireless standards use frequencies in the ISM range? How does the BSSID differ from the SSID? How does key rotation improve wireless security? ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 101 How are a groupwise key and a pairwise key different? What improvements did WPA make to overcome the weaknesses of WEP? Why shouldn't you use shared secret authentication with WEP? Why is a RADIUS server required when using 802.1x authentication? How can you add pairwise key rotation when using WEP? What is the function of the MIC with WPA and WPA2? What encryption mechanisms are used by WEP, WPA, and WPA2? How do disabling SSID broadcast and using MAC filtering add security to wireless networks? Video/Demo Time 7.7.1 803.11 Wireless 12:50 7.7.4 Wireless Security 19:04 7.7.6 Wireless Security Implementations Total 5:31 37:25 Number of Exam Questions 6 questions Total Time About 55 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 102 Section 8.1: Cryptosystem Attacks Summary This section discusses different types of attacks on cryptosystems. Topics covered include: Levels of information used by an attacker (strongest to the weakest security) o Cipher text only o Known plaintext o Chosen plaintext o Iterative chosen plaintext o Chosen cipher text General methods of classifying attacks: o Brute force attack o Dictionary attack o Weak key attack o Mathematical attack o Meet-in-the-middle attack o Birthday attack o Analytic attack o Implementation attack o Statistical attack Countermeasures to strengthen the cryptosystem: o Use strong passwords o Implement strong cryptosystems with redundant encipherment o Implement long key spaces CISSP Objectives 5. Cryptography ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 103 Lecture Focus Questions: How does a dictionary attack differ from a brute force attack? How is the statistical incidence of two people with the same birthday in a room relevant for cryptography? How does having chosen plaintext enhance an attacker's chances of breaking the code over having known plaintext only? How is having strong passwords a countermeasure for a dictionary attack? What effect does redundant encipherment have on a statistical attack? Video/Demo Time 8.1.1 Cryptosystem Attacks 3:44 Number of Exam Questions 9 questions Total Time About 15 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 104 Section 8.2: Access Control Attacks Summary This section discusses attacks that could be used against network confidentiality and integrity. Students must understand these to adequately protect their information systems. Details include: Attacks on integrity: o Data diddling o Salami attack Countermeasures for integrity attacks Automated access control attacks that affect confidentiality: o Hacking of a network o Man-in-the-middle o Session hijacking o DNS poisoning Attacks that are targeted at gathering information: o Disclosure o Inference and traffic analysis o Aggregation attack o Targeted data mining Social engineering attacks: o Dumpster diving o Shoulder surfing o Piggybacking o Masquerading o Eavesdropping o Phishing Countermeasures for social engineering attacks Common authentication attacks: o Brute force o Dictionary o Password sniffing ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 105 o Spoofing o Man-in-the-middle o Replay o Hijacking Countermeasures for attacks on authentication Suggestions for strengthening passwords CISSP Objectives 1. Access Controls Lecture Focus Questions: How are inference and aggregation attacks similar? What is the difference between a cracker and a white-hat hacker? For what attacks will disabling backdoors be most effective? How are spoofing and DNS poisoning similar? How does a data diddling attack differ from a salami attack? What is the best protection against social engineering attacks? What is the main purpose of a replay attack? Video/Demo Time 8.2.1 Confidentiality and Integrity Attacks 8.2.4 Authentication Attacks Total 8:11 1:14 9:25 Number of Exam Questions 18 questions ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 106 Total Time About 35 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 107 Section 8.3: Availability Attacks Summary In this section students learn about Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks. Common types of DoS and DDos attacks are presented, as well the countermeasures to protect an information system from these forms of attack. Details include: DoS attacks: o Smurf o Fraggle o Ping flood o Ping-of-death o SYN flood o Land o Teardrop o DNS poisoning o Banana attack o Negative Acknowledgment (NACK) o Deauthentication (Deauth) o Spam DDoS attacks: o Trinoo o Tribal Flood Network (TFN) o roBOT NETwork BOTNET Countermeasures for DoS and DDoS attacks CISSP Objectives 2. Telecommunications and Network Security 3. Security Management ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 108 Lecture Focus Questions: How are DoS and DDoS attacks similar? What is the difference between a DoS and a DDoS attack? How does a Fraggle attack differ from a Smurf attack? How are a Land attack and a Teardrop attack similar? What attacks are reverse DNS lookups a countermeasure for? How can hashes help prevent data loss from DoS or DDoS attacks? What is the role of a zombie? ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 109 Video/Demo Time 8.3.1 Availability Attacks 12:17 Number of Exam Questions 14 questions Total Time About 30 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 110 Section 8.4: Trusted Computing Base Attacks Summary In this section the students will learn about additional attacks, these include attacks on the trusted computing base, malware attacks, common exploitation methods, database threats and vulnerabilities, and attacks on Web servers. Countermeasures for each are explained. Details include: Common malware: o Virus o Worm o Trojan horse o Logic Bomb Countermeasures for malware Common exploitation methods: o Backdoor o Buffer overflow attack o Pointer overflow attack o Directory traversal o Covert channels Threats to integrity of the data in a database: o Asynchronous race condition o Data contamination o Deadlocking o Polyinstantiation o SQL injection o Time of check/Time of use (TOC/TOU) Additional database threat and vulnerabilities to components of the CIA Triad: o Aggregation o Backdoor o Bypass attacks ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 111 o Compromising database views o Denial-of-service o Inference o Interception of data o Query attacks o Physical security o Storage channel o Unauthorized Access Countermeasures to database threats and vulnerabilities ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 112 Web-based applications or scripting programs: o JavaScript, VBScript, other client-side scripting o Java o ActiveX o Cookies o CGI scripting, ASP, and other server-side scripting Countermeasures for Web server-based attacks CISSP Objectives 4. Applications Security 6. Security Architecture Lecture Focus Questions: What type of files do anti-virus software need to be able to identify known viruses? What must you do to make anti-virus software effective? What countermeasures are recommended for Trojan horse and backdoor attacks? What is the difference between a buffer overflow attack and a pointer overflow attack? What countermeasures do database attacks and Web server attacks have in common? Why are cookies a vulnerability? How are a cover timing channel and a storage channel similar? Video/Demo 8.4.1 TCB Attacks Time 4:20 8.4.2 Application Attacks Total 6:36 10:56 ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 113 Number of Exam Questions 18 questions Total Time About 40 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 114 Section 8.5: Communication Attacks Summary This section discusses threats to a Private Branch eXchange (PBX) system connecting T1 lines to a phone system and the countermeasures to protect it. Also discussed are the specific security attacks that can be implemented against wireless communications and the countermeasures. Details include: Threats to the PBX system: o War Dialing o 2600 Club o Emulation devices o Eavesdropping o Inbound fax exposure o Toll charge abuse o Unauthorized access to voicemail Consideration to protect the PBX system Protocols to provide security for wireless communication: o Wired Equivalent Privacy (WEP) Vulnerabilities o Wireless Application Protocol (WAP) Vulnerabilities Security attacks wireless networks are vulnerable to: o Eavesdropping o Site surveys or war driving o Rogue access point or Man-in-the-middle o Replay attack Countermeasures for wireless communications CISSP Objectives 2. Telecommunications and Network Security ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 115 Lecture Focus Questions: What are two potential effects or costs to businesses from PBX vulnerabilities? What is the difference between war dialing and war driving? How are replay attacks and man-in-the-middle attacks similar? What vulnerability does The Gap in the WAP expose? What are effective countermeasures for inbound fax exposure? How do strong password policies deter PBX attacks? Video/Demo Time 8.5.1 Telcom Attacks 2:57 8.5.2 Wireless Vulnerabilities 7:27 Total 10:24 Number of Exam Questions 9 questions Total Time About 25 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 116 Summary Summary The summary is a brief review of the major concepts of the CISSP objectives: The security program must be senior management driven and fully supported. There must be budget justifications for deploying countermeasures. Security objectives for the protection of your information system must provide confidentiality, integrity and availability. User training and penalties for non-compliance to security policies must be in place. Adhere to the ethics of a Security Professional. Total Time About 2 minutes ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 117 Appendix A: Approximate Time for the Course The total time for the LabSim for (ISC) 2 Certified Information System Security Professional course is approximately 36 hours and 37 minutes. The time is calculated by adding the approximate time for each section which is calculated using the following elements: Video/demo times Approximate time to read the text lessons (the length of each text lesson is taken into consider) Simulations (5 minutes assigned per simulation) Questions (1 minute per question) The breakdown for this course is as follows: Module Sections Time Minute HR:MM 0.0 Introduction 0.1 Introduction 15 15 :15 20 50 45 115 1:55 30 30 50 25 135 2:15 30 35 10 75 1:15 1.0 Security Management 1.1 Security Management 1.2 Risk Analysis 1.3 Security Planning 2.0 Operational Security 2.1 Operational Security Planning 2.2 Employee Management 2.3 Facility Management 2.4 Auditing and Testing 3.0 Law and Ethics 3.1 Crime and Law 3.2 Incidence Response 3.3 Ethics ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 118 4.0 Cryptography 4.1 Cryptography Concepts 4.2 Hashing 4.3 Symmetric Cryptography 4.4 Asymmetric Cryptography 4.5 Implementations 45 20 45 80 40 230 3:50 10 30 50 30 10 20 150 2:30 40 35 35 45 155 2:35 30 70 70 55 40 50 55 370 6:10 15 35 30 40 25 145 2:25 5.0 Access Control 5.1 Access Controls 5.2 Physical Security 5.3 Authentication 5.4 Authorization 5.5 Auditing 5.6 Academic Models 6.0 Computing Architecure 6.1 Trusted Computing 6.2 Computer Architecture 6.3 Software Development 6.4 Database Management 7.0 Network Security 7.1 Networking Models and Standards 7.2 Network Technology 7.3 Network Devices 7.4 Fault Tolerance 7.5 Internetworking 7.6 Transmission Security 7.7 Wireless 8.0 Attacks 8.1 Cryptosystem Attacks 8.2 Access Control Attacks 8.3 Availability Attacks 8.4 Trusted Computing Base Attacks 8.5 Communication Attacks Practice Exams Exam Preparation 1: Access Controls (55 questions) 2: Telecom and Network Security (83 questions) 3: Security Management (82 questions) 6 55 83 82 ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 119 4: Applications Security (41 questions) 5: Cryptography (92 questions) 6: Security Architecture (28 questions) 7: Operations Security (42 questions) 8: Business Continuity Planning (30 questions) 9: Law and Ethics (27 questions) 10: Physical Security (71 questions) Certification Practice Exam (250 questions) 41 92 28 42 30 27 71 250 Total Time 807 13:27 2197 36:37 ©2006 TestOut Corporation (Rev 01/2012) Certified Information Systems Security Professional Ver. 2 120