All Questions
advertisement

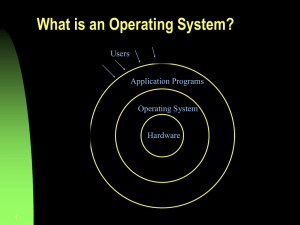
Sheet 1 “Chapter 1” Answer briefly without non-useful details the following Questions: 1. 2. 3. 4. 5. 6. 7. 8. 9. The fundamental goal of computer systems is to execute user programs and to make solving user constructed. Draw a figure that shows the computer hardware that can be considered as the Operating System. Describe the computer hardware modules that can be considered as the basic computing resource The Operating System can be simply defined as a program that acts as an intermediary betw Draw a figure that show how the Operating System is interfaced to both users and computer ha Define what is an Operating System? What are the Objective of teaching (Why we learn) Operating Systems? We can define the Operating System as a resource manager. Name the primarily resources it m What are the main differences between operating systems for mainframe computers and personal Name the functions performed by an Operating System. Discuss 5 (five) functions that can be performed by an Operating System. Discuss how can operating system can be classified? 10. Define what is afirmware? 11. Distinguish among Hardware , software , Firmware Part 2. Writ the Corresponding Scientific Terms : 1. The equipment of a computer system, its processor, its storage, its I/O devices, and its communication connections. Part 3. Chose (circulate, underline) the right answer. 1. Peoples charged with responsibility of monitoring the operating system, as responding to request for intervention. Systems Programmers Systems Administration * * Users Computer operators * * * Non of all 2. People who set policy and interface with the operating system to ensure that those policies are properly implemented. Systems Programmers Systems Administration * * Users Computer operators * * * Non of all “Chapter 2 ” 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. 11. 12. 13. Define, compare, and contrast each of the following terms : a. off line, b. on line, c. real time, d. time sharing, e. interactive computing Define the essential properties of the following types of operating systems : a. Batch b. Interactive c. Time-sharing d. Real-time e. Distributed Name the several levels of programming. Define, compare, and contrast compilers with interpreters. When should each of them be used? Distinguish between multiprogramming and multiprocessing. What is spooling? How would an input spooling system designed to read punched cards from a card reader operate? An extreme method of spooling, known as staging a tape, is to read the entire contents of a magnetic tape onto disk before using it. Discuss the main advantage of such a scheme. In a multiprogramming and time-sharing environment several users share the system simultaneously. This situation can result in various security problems. a. What are two such problems? b. Can we ensure the same degree of security in a time-shared machine as we have in a dedicated machine? Explain your answer. What are the main differences between operating systems for mainframe computers and personal computers? Why are distributed systems desirable? What is the main difficulty a person must overcome in writing an operating system for a real-time environment ? What is the nucleus or kernel of an operating system? Why the nucleus ordinarily maintained in primary storage? What functions are performed by the nucleus? Compare, and contrast absolute loaders with relocating loaders. 14. How do linkage editors differ from linkage loaders? 15. Under what circumstances would a user be better off using a time-sharing system rather than a personal computer or single-use workstation? 16. Describe the differences between symmetric and asymmetric multiprocessing. What are the advantages and disadvantages of multiprocessor systems? 17. Why does the nucleus ordinary run with interrupt disabled? 18. Describe several techniques for implementing storage protection 19. State the different types of storage protection against OS violation. 20. How does the distinction between monitor mode and user mode function as a rudimentary form of protection (security) system? 21. Define, compare, and contrast several levels of Storage Hierarchy. 22. In hierarchical storage systems, a certain amount of overhead is involved in moving programs and data between its various levels of the hierarchy. Discuss the memory hierarchy and show why the benefits derived from such systems justify this overhead involved 23. When are caches useful? What problems do they solve? What problems do they cause? If a cache can be made as large as the device it is caching for (for instance, a cache as large as a disk) why not do so and eliminates the device? 24. Give an example of each of the following types of interrupts : a. Input / Output b. external c. program check d. restart e. machine check 25. Explain briefly what is meant by “ status saving “ and “CPU status restoring” 26. Identify the three techniques used for status saving and status restoring (The techniques in this case refer to the locations where the contents of the critical registers/counters are stored). 27. Assume that the computer system uses the simple vectored interrupt. What happens if an interrupt is received by the CPU while servicing a prior interrupt request from another peripheral? 28. What is the function of program status word (PSW)? Why might the operating system ever want to know the current PSW? 29. What happens to PSW when an interrupt occurs? What are different schemes that can be used for that purpose? How we return to where we left after processing the interrupt in each one ? 30. What is the purpose of the command interpreter? Why is it usually separate from the kernel? 31. Describe the techniques for handling the communications between a processor and a channel 32. what is the major drawback of the programmed i/o transfer ? 33. Briefly explain how the interrupt I/O overcomes the disadvantages of programmed I/O. 34. Name the general sequence of events in case of an interrupt I/O. 35. Draw a figure that explains the execution path of an interrupted processor. 36. Assume that the computer system uses the : I ) The Simple Vectored Interrupt System. ii) The Hardware - Polled Interrupt System. iii) The Multilevel Priority Interrupt System. What happens if an interrupt is received by the CPU while servicing a prior interrupt request from another peripheral? 37. What happens in the daisy-chain priority interrupt, when device 1 requests an interrupt after device 2 has sent an interrupt request to the CPU but before the CPU responds with the interrupt acknowledge? 38. Consider a computer without priority interrupt hardware. Any one of many sources can interrupt the computer, and any interrupt request results in storing the rectum adders and branching to a common interrupt routine. Explain how a priority can be established in the interrupt service program 39. Identify the three techniques used for status saving and status restoring (The techniques in this case refer to the locations where the contents of the critical registers/counters are stored). 40. Describe different types of stacks, which are frequently used in computers to save the contents of the CPU status ( program counter and others ) when the interrupt handling subroutine procedure is initiated. Compare between them in highlighting the advantages and disadvantages of each. Part 2 : Writ the Corresponding Scientific Term : 1. The translator that translates a source program written in assembly language to an object program in machine code. 2. It collects the routines that have been written and translated separately (to form a program) together into a single machine language program that can be passed to the loader 3. The translator that translates a source program written in a high level language to an object program in machine language without producing an object code. 4. The translator that do not store the machine code image (object programs). 5. It can place programs in various free areas of memory. It means that its function is to take a machine language program which was generated on the assumption that it would be loaded at some location x, usually chosen at 0 for convenience, and load it starting at location y. 6. The part of an Operating System that handles Interrupts. 7. The most intensively used code of the operating system, that is why it is commonly thought to be the entire operating system. For that reason it is always stored in main memory. One of its main tasks is to handle Interrupts The module of an Operating System that Decide which processes are to be loaded into primary memory when memory space becomes available. 8. The part of an Operating System that is responsible for creation and deletion of directories Part 2. Chose (circulate, underline) the right answer. The program that translates a source program written in assembly language to an object program in machine language. Assembler * * * Compiler Interpreter * Non of all * All of them The translator that translates a source program written in assembly language to an object program in machine code. Assembler * * * Compiler Interpreter * Non of all * All of them It collects the routines that have been written and translated separately (to form a program) together into a single machine language program that can be passed to the loader. * Assembler * Compiler * Linker * Relocating loaders * All of the above Non of all It can place programs in various free areas of memory. It means that its function is to take a machine language program which was generated on the assumption that it would be loaded at some location x, usually chosen at 0 for convenience, and load it starting at location y. * Assembler * Compiler * Linker * Relocating loaders All of the above Non of all * protection technique implemented against operating system multiprogramming systems is don by using: Storage protection keys * * * Boundary registers Supervisor mode * Non of all * violation All of the them The translator that do not store the machine code image ( object programs ) is : in * * * Compiler Interpreter Non of all * Assembler * All of them The operating system can be defined as: * * Resource allocator Resource manager * All of them * Control program * User Interface Non of all (BIOS) basic input/output system can be classified as : Software * * * Firmware Hardware * Non of all * All of them The translators that translate a source program written in a high level language to an object program in machine language generate relatively inefficient code and operate quickly. Optimizing Compilers Quick-and-Dirty Compilers * * * Interpreter * Non of all * All Of them The program that translates a source program written in assembly language to an object program in machine language. Optimizing Compilers Quick-and-Dirty Compilers * * Interpreter All Of them * * * Non of all * Unlimited number of Programs can be archived for theoretically infinite time in: Primary Memory * Tertiary Memory * Non of all * Programs are saved in: Auxiliary Memory * * Tertiary Memory Non of all support of certain system accounting functions * Process manager * The resident monitor Memory manager * Dispatcher * Processor scheduler. * Non of all * The provision of mechanisms for process communication Memory manager * * File Management * Process manager * Processor scheduler. * The core of an OS Non of all * Interrupt handling. * * The kernel of an OS Memory manager * * Process manager * Dispatcher * All of the above Non of the above The most intensively used code of the operating system that is why it is commonly thought to be the entire operating system. For that reason it is always stored in main memory. The resident The Core * * monitor The Kernel All of the above * * * Non of all Chapter 3 1. What are the five major activities of an operating system in regard to process management? 2. What are the three major activities of an operating system in regard to memory management? 3. What are the three major activities of an operating system in regard to secondary storage management ? 4. What are the five major activities of an operating system in regard to file management? Part 2 : Writ the Corresponding Scientific Term : 1. The module of an Operating System that Decide which processes are to be loaded into primary memory w memory space becomes available. 2. The part of an Operating System that is responsible for creation and deletion of directories Part 3. Chose (circulate, underline) the right answer. Decide which processes are to be loaded into primary memory when memory space becomes available. * * Process manager * File Management Memory manager * * Dispatcher * All of the above Non of the above The creation and deletion of directories * Process manager * File Management * Memory manager * * Dispatcher * All of the above Non of the above Keeping track of status of each location of primary memory (either allocated or unallocated ). * Process manager * File Management * Main memory manager * * Dispatcher * All of the above Non of the above The support of primitives for manipulating files and directories. * Process manager * File Management * Memory manager * Dispatcher * * All of the above Non of the above Deallocation technique when the process no longer needs memory or terminated. * Process manager * File Management * Main memory manager * Dispatcher * Processor scheduler. * Non of all The backup of files on stable (non volatile ) storage media * Process manager * File Management * Memory manager * Dispatcher * Processor scheduler. * Non of all Chapter 5” 1. Consider a single processor timesharing system that supports a large number of interactive users. Each time a processor gets a processor the interrupting clock is set to interrupt after the quantum expires. Assume a single quantum for.All processors on the system. a. What would be the effect of setting the quantum at a very large number of minutes ? b. What if the quantum were set to a very small value , say a few processor cycles? 2. As an operating system designer, you have been commissioned to design the process and job schedulers of a new system. You have been told that the high priority jobs should be processed as quickly as possible, but that overall system throughput is also a major consideration. As a job scheduling scheme you have been chosen to take all high priority jobs before considering jobs of lower priority. In designing the process scheduler you are considering two schemes. The first is a priority scheme identical to the job scheduler. The second scheme first tries to run I/O bound jobs, then "normal" jobs, then CPU bound jobs, regardless of user specified priority. Discuss the two schemes with respect to overall system goals 3. Switching from one Process to another in multiprogramming system commonly occurs when the process has exhausted its allotted quantum of time. What are some other reasons and/or criteria for switching process? 4. Distinguish among the following three levels of schedulers : a. Job scheduler. b. Intermediate-level scheduler. c. Dispatcher. 5. Which level of scheduler should make a decision on each of the following question? a. Which ready process should be assigned the CPU when it next becomes available? b. Which of a series of waiting batch jobs that have been spooled to disk should next be initiated? c. Which process should be temporarily suspended to relieve a short-term burden on the CPU? d. Which temporarily suspended process is known to be I/O - bound and should be activated to balance the multiprogramming mix? 6. which of the following refer to ‘ static priorities ’ and state which of the following refer to ‘ dynamic priorities ’. a. are easier to implement. b. require less run-time overhead. are more responsive to changes in a process’s environment 7. Name the different scheduling schemes, compare of them according to the following scheduling objectives : a. b. c. d. to be fair to maximize throughput to be predictable to obey priorities 8. Describe the differences among short-term , medium term, and long-term scheduling. 9. A CPU scheduling algorithm determines an order for the execution of its scheduled processes. Given n processes to be scheduled on one processor, how many possible different schedules are there? Give a formula in terms of n. 10. Define the difference between preemptive and nonpreemptive scheduling. 11. What advantage is there in having different time-quantum sizes on different levels of a multilevel queueing system? 12. Many CPU-scheduling algorithms are parameterized. For example, the RR algorithm requires a parameter to indicate the time slice. Multilevel feedback queues require parameters to define the number of queues, the scheduling algorithms for each queue, the criteria used to move processes between queues, and so on. These algorithms are thus really sets of algorithms (for example, the set of RR algorithms for all time slices, and so on). One set of algorithms may include another (for example, the FCFS algorithm is the RR algorithm with an infinite time quantum).What (if any) relation holds between the following pairs of sets of algorithms? a. Priority and SJF b. Multilevel feedback queues and FCFS c. Priority and FCFS d. RR and SJF 13. Suppose that a scheduling algorithm (at the level of short-term CPU scheduling) favors those processes that have used the least processor time in the recent past. Why will this algorithm favor I/O-bound programs and yet not permanently starve CPU-bound programs? B. The following are common scheduling objectives : ii. iii. i. iv. v. vi. a. b. c. d. e. f. g. h. i. j. k. l. to be fair to maximize throughput to maximize the number of interactive users receiving acceptable response times to be predictable to minimize overhead to balance resource utilization to achieve a balance between response and utilization avoid infinite postponement to obey priorities to give preference to processes that hold key resources to give lower grade of service to high overhead process to degrade gracefully under heavy loads Which of the preceding objective most directly applies to each of the following? i. ii. iii. iv. v. vi. If a user has been waiting for an excessive amount of time, favor that user. The user who runs a payroll job for a 1000-employee company expects the job to take about the same amount of time each week. The system should admit jobs to create a mix that will keep most devices busy. The system should favor important jobs. Important processes arrive but cannot proceed because an unimportant process is holding the resources the important job needs. During peak period, the system should not collapse from the overhead. It takes to manage a large number of processes. Part 2. Chose (circulate, underline) the right answer. Which process should be temporarily suspended to relieve a short-term burden on the CPU? Dispatcher * * * Job scheduler Processor scheduler. * Intermediate-level scheduler. * * Non of all The resident monitor Which of a series of waiting batch jobs that have been spooled to disk should next be initiated? * * Dispatcher * Intermediate-level scheduler. * Non of all Job scheduler * Processor scheduler. * The resident monitor When processor should be assigned to which processes? * * Dispatcher * Intermediate-level scheduler. * Non of all Job scheduler * Processor scheduler. * The resident monitor Which ready process should be assigned the CPU when it next becomes available? * * Dispatcher * Intermediate-level scheduler. * Non of all Job scheduler * Processor scheduler * The resident monitor Part 2 : Writ the Corresponding Scientific Term : 1. The scheduler that should select a good job mix of I/O bound & CPU bound jobs to have a system with the homogenous combination to achieve the best performance. 2. The scheduler that decides Which of a series of waiting batch jobs that have been spooled to disk should next be initiated? 3. The scheduler that decides Which process should be temporarily suspended to relieve a short-term burden on the CPU? 4. The scheduler that selects a ready process to which the CPU is assigned when it next becomes available? 5. It is a non-preemptive discipline that corrects some of the weaknesses in SJF, particularly the excessive bias against longer jobs and the excessive favoritism toward short new jobs. In this discipline the priority of each process (job) is a function not only the job’s service time but also the amount of time the job has been waiting for service. 6. It is the interval from the time of submission of a process to the time of completion. It is the sum of time period spent waiting to get into memory, waiting in the ready queue, executing on the CPU, and doing I/O. C. Complete the following statements using the appropriate term : 1. Scheduling technique is …… …... if the user who runs a payroll job for a 1000-employee company expects that his job to take about the same amount of time each week. 2. Scheduling technique that favors a user, when this user has been waiting for an excessive amount of time, avoids the ………… ………… The scheduling discipline could be ………… …………If all processes are treated the same. Scheduling technique is said to that it…………. ………… if The system should favor important jobs. Sheet 6 " chapter 6" Answer briefly without non-useful details the following Questions: 1. Name the different memory management schemes. 2. Name the different memory management schemes. For each of the memory management schemes, describe briefly the major advantages and drawbacks. 3. In different techniques of memory management the main aim is to minimize the wasted area from memory or to use memory more efficiently, but fragmentation is one of problems that must be overcome. What is fragmentation?. Discuss the types of storage fragmentation and how they occur in each of the real storage organization schemes, and how can they be overcome? 4. Distinguish among the following placement strategies in the main storage : first fit best fit worst fit 5. In different techniques of memory management the main aim is to minimize the wasted area from memory or to use memory more efficiently. But fragmentation, which develops a large number of separate free areas, is one of the serious problems that must be overcome: Discuss the types of storage fragmentation Show which of them may occur in each of the different real memory management schemes For each of the real memory management schemes, describe briefly the major advantages and drawbacks. C. Complete the following statements using the appropriate term : 1. In the …………… ………… algorithm, the free table is kept stored by location When it is necessary to allocate memory to a job, we start at the free area at the lowest memory address and keep looking until we find the first free area enough for the place to fit. 2. In different techniques of memory management the main aim is to minimize the wasted area from memory or to use memory more efficiently, but ……… ……… is one of problems that must be overcome. Part 2 : Writ the Corresponding Scientific Term : 1. Placement strategies in which the free table is stored by location. When it is necessary to allocate memory to a new job, we scan the free area at the lowest memory address and keep looking until we find the free area enough to fit. 2. It is the wasted area from memory, or the large number of separate free memory divided into small pieces. 3. A memory management technique in which main memory is divided into a number of equal-size frames. Each process is divided into a number of equal size parts of the same length as frames. A process is loaded by loading all of its parts into available, not necessarily contiguous, frames. Part 3. Find which of the following statements are correct and which are incorrect. Put () in front of the correct statement and (X) in front of the incorrect one. Underline the wrong words, otherwise the answer is neglected. Note that an incorrect statement may have several wrong words. 1. Best fit places the program in the first storage hole which is large enough to hold it. ( ) 2. First fit places the program in the first “tightest” fitting hole, i.e., the smallest of the available storage holes large enough hold it. ( ) 3. Best fit places the program or data piece in the largest available hole that will hold it. ( ) 4. Best fit is a low overhead strategy. First fit is intuitively appealing to ( most people. Worst fit is appealing because it avoids creating small storage holes. 5. Best fit places the program or data piece in the largest available hole that will hold it. 6. Best fit places the program in the first storage hole which is large enough to hold it. 7. Best fit is a low overhead strategy. First fit is intuitively appealing to most ( people. Worst fit is appealing because it avoids creating small storage holes 8. Compaction is the method that combines all free areas together into one ( contiguous area. It is used to overcome the internal fragmentation problem. Chapter 7 “ Disk Shceduling : Answer briefly without non-useful details the following Questions: 1. i. ii. iii. Name the different Disk scheduling disciplines, Compare briefly between them according to the following disk scheduling goals : Throughput Mean Response Time Variance. ) ( ) ( ) ) ) 2. Name the main Disk Storage Selection Criteria. C. Complete the following statements using the appropriate term : 1. …………………… is the simplest disk scheduling technique Part 2 : Write the Corresponding Scientific Term : 1. The time the read / write head mechanism of a magnetic disk takes to be positioned above a given track. Part 1. Find which of the following statements are correct and which are incorrect. Put () in front of the correct statement and (X) in front of the incorrect one. Underline the wrong words, otherwise the answer is neglected. Note that an incorrect statement may have several wrong words. 1. Throughput is defined as number of requests serviced per unit of time. The objectives of disk scheduling techniques generally concentrate on minimizing the throughput. ( ) 2. The C-Scan scheduling technique is like Scan scheduling technique except that it services only requests waiting when a particular sweep begins. Requests arriving during a sweep are grouped together and ordered for optimum service during the return sweep. ( ) 3. Access time is defined as the time required to obtain the first byte of a randomly located set of data. In disk drives the average access time ( for read or write ) consists of three significant actions, namely a seek time to locate data, a rotational delay ( latency ), and record transmission. Of these, the largest by far is normally transmission time. Therefore, optimization techniques generally concentrate on minimizing the latency time. ( ) 4. One important measure in disk scheduling techniques is the mean of response time. It is the mathematical measure of how far individual items tend to deviate from the average of items. The smaller the variance the greater the fairness of the of disk scheduling techniques. ( ) 5. At medium to heavy loading SCAN yields the best result, while N-Step SCAN has Very small variance ( . ) 6. N-Step SCAN avoids delays and possibly indefinite postponement by forcing arriving requests to wait until return sweep for service. ( )