Finding_29
advertisement
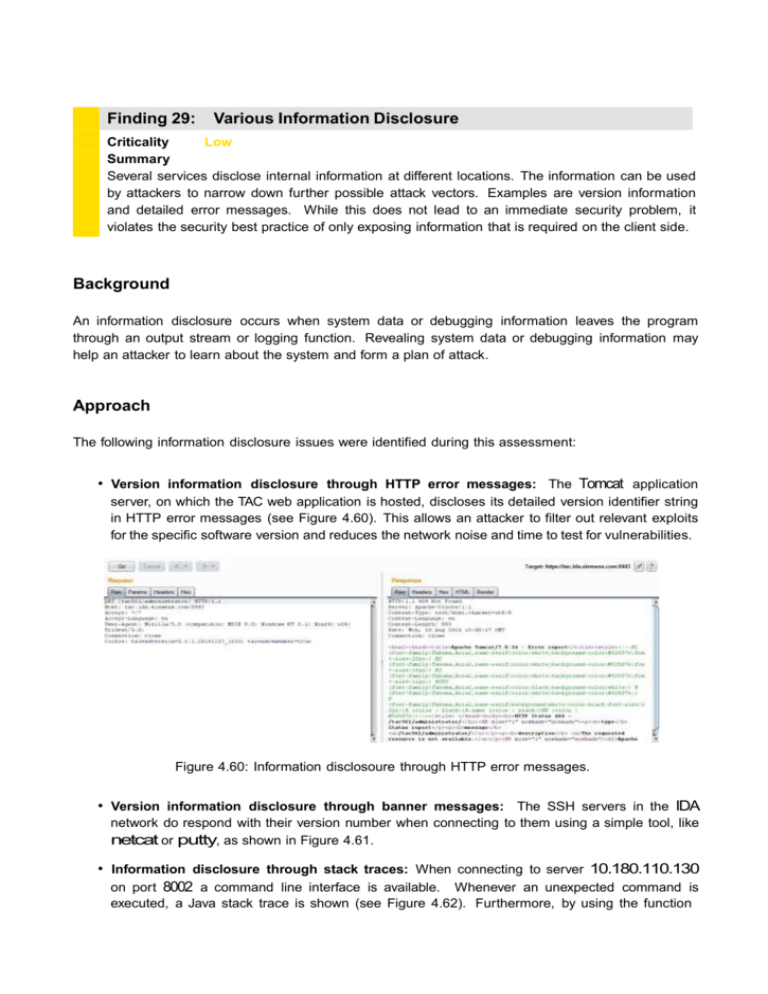
Finding 29: Various Information Disclosure Criticality Low Summary Several services disclose internal information at different locations. The information can be used by attackers to narrow down further possible attack vectors. Examples are version information and detailed error messages. While this does not lead to an immediate security problem, it violates the security best practice of only exposing information that is required on the client side. Background An information disclosure occurs when system data or debugging information leaves the program through an output stream or logging function. Revealing system data or debugging information may help an attacker to learn about the system and form a plan of attack. Approach The following information disclosure issues were identified during this assessment: • Version information disclosure through HTTP error messages: The Tomcat application server, on which the TAC web application is hosted, discloses its detailed version identifier string in HTTP error messages (see Figure 4.60). This allows an attacker to filter out relevant exploits for the specific software version and reduces the network noise and time to test for vulnerabilities. Figure 4.60: Information disclosoure through HTTP error messages. • Version information disclosure through banner messages: The SSH servers in the IDA network do respond with their version number when connecting to them using a simple tool, like netcat or putty, as shown in Figure 4.61. • Information disclosure through stack traces: When connecting to server 10.180.110.130 on port 8002 a command line interface is available. Whenever an unexpected command is executed, a Java stack trace is shown (see Figure 4.62). Furthermore, by using the function Figure 4.61: SSH server do respond with their version number when connecting to them. listCommand, a history of old commands can be displayed, which contains information, like local path names or job information (see Figure 4.63). Figure 4.62: Information disclosure through stack trace. Figure 4.63: Information disclosure through old history. Effort and Prerequisites Some of the error messages could be provoked as an unauthorized user. Most of them, however, require a valid session. In any case, access to the IDA network is necessary. Impact Information disclosure cannot be used immediately for a successful attack against the target system, but the information helps an attacker to learn more about the target system and may allow him to refine further attack scenarios. The information might be abused in connection with other vulnerabilities. The provided software version information can, for example, be used to filter out relevant attacks for specific and defined software components in use. Stack traces disclose details about the inner workings of the server implementation. Countermeasures CSA recommends reducing the amount of data that is disclosed to end users. Security best practices recommend only exposing information that is necessary for the correct operation of an application.