System Security Plan Checklist
advertisement
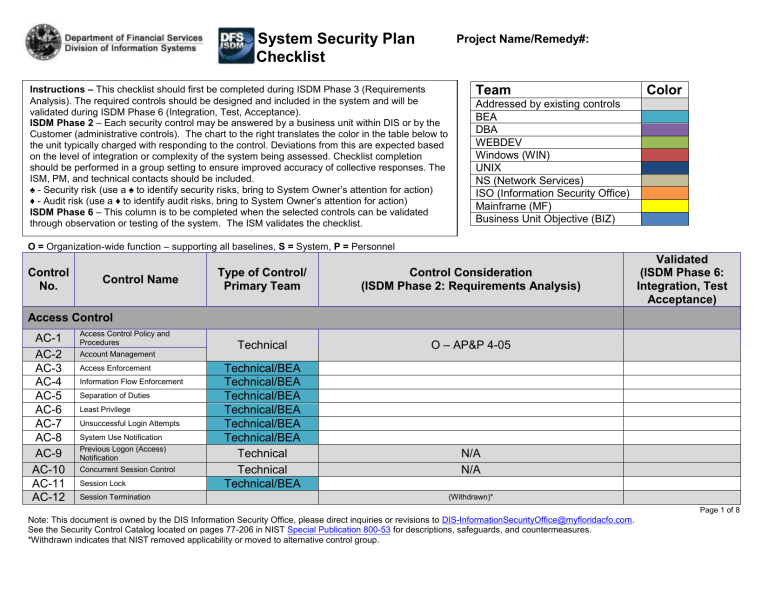
S System Security Plan Checklist Project Name/Remedy#: Instructions – This checklist should first be completed during ISDM Phase 3 (Requirements Analysis). The required controls should be designed and included in the system and will be validated during ISDM Phase 6 (Integration, Test, Acceptance). ISDM Phase 2 – Each security control may be answered by a business unit within DIS or by the Customer (administrative controls). The chart to the right translates the color in the table below to the unit typically charged with responding to the control. Deviations from this are expected based on the level of integration or complexity of the system being assessed. Checklist completion should be performed in a group setting to ensure improved accuracy of collective responses. The ISM, PM, and technical contacts should be included. ♠ - Security risk (use a ♠ to identify security risks, bring to System Owner’s attention for action) ♦ - Audit risk (use a ♦ to identify audit risks, bring to System Owner’s attention for action) ISDM Phase 6 – This column is to be completed when the selected controls can be validated through observation or testing of the system. The ISM validates the checklist. Team Color Addressed by existing controls BEA DBA WEBDEV Windows (WIN) UNIX NS (Network Services) ISO (Information Security Office) Mainframe (MF) Business Unit Objective (BIZ) O = Organization-wide function – supporting all baselines, S = System, P = Personnel Control No. Control Name Type of Control/ Primary Team Control Consideration (ISDM Phase 2: Requirements Analysis) Technical O – AP&P 4-05 Validated (ISDM Phase 6: Integration, Test Acceptance) Access Control AC-1 AC-2 AC-3 AC-4 AC-5 AC-6 AC-7 AC-8 AC-9 AC-10 AC-11 AC-12 Access Control Policy and Procedures Account Management Access Enforcement Information Flow Enforcement Separation of Duties Least Privilege Unsuccessful Login Attempts System Use Notification Previous Logon (Access) Notification Concurrent Session Control Session Lock Session Termination Technical/BEA Technical/BEA Technical/BEA Technical/BEA Technical/BEA Technical/BEA Technical Technical Technical/BEA N/A N/A (Withdrawn)* Page 1 of 8 Note: This document is owned by the DIS Information Security Office, please direct inquiries or revisions to DIS-InformationSecurityOffice@myfloridacfo.com. See the Security Control Catalog located on pages 77-206 in NIST Special Publication 800-53 for descriptions, safeguards, and countermeasures. *Withdrawn indicates that NIST removed applicability or moved to alternative control group. AC-13 AC-14 AC-15 AC-16 AC-17 AC-18 AC-19 AC-20 AC-21 AC-22 Supervision and Review—Access Control Permitted Actions without Identification or Authentication Automated Marking Security Attributes Remote Access Wireless Access Access Control for Mobile Devices Use of External Information Systems User-Based Collaboration and Information Sharing Publicly Accessible Content (Withdrawn) Technical/BEA (Withdrawn) Technical Technical/BEA Technical/BEA Technical/BEA Technical/BEA N/A Technical/BEA Technical/BEA Awareness & Training AT-1 AT-2 AT-3 AT-4 AT-5 Security Awareness and Training Policy and Procedures Security Awareness Security Training Operational O – Security Awareness Training Program O – AP&P 4-05. Security Training Records Contacts with Security Groups and Associations Audit & Accountability AU-1 AU-2 AU-3 AU-4 Audit and Accountability Policy and Procedures Auditable Events Audit Storage Capacity Technical Technical/BIZ Technical/BIZ Technical/DBA AU-5 Response to Audit Processing Failures Technical/DBA AU-6 Audit Review, Analysis, and Reporting Audit Reduction and Report Generation Time Stamps AU-7 AU-8 AU-9 AU-10 AU-11 Content of Audit Records Protection of Audit Information Non-repudiation Audit Record Retention (Withdrawn)* Technical/WIN Technical/BEA Technical/BEA Technical Technical/BEA N/A Refer to GS1-SL to properly configure, direct questions to the ISO Page 2 of 8 Note: This document is owned by the DIS Information Security Office, please direct inquiries or revisions to DIS-InformationSecurityOffice@myfloridacfo.com. See the Security Control Catalog located on pages 77-206 in NIST Special Publication 800-53 for descriptions, safeguards, and countermeasures. *Withdrawn indicates that NIST removed applicability or moved to alternative control group. AU-12 Audit Generation Technical/BEA Monitoring for Information AU-13 Disclosure Technical AU-14 Session Audit Technical Security Assessment & Authorization CA-1 Security Assessment and Authorization Policies and Procedures Security Assessments CA-2 Information System Connections CA-3 Security Certification CA-4 Plan of Action and Milestones CA-5 Security Authorization CA-6 Continuous Monitoring CA-7 Configuration Management CM-1 CM-2 CM-3 CM-4 CM-5 CM-6 CM-7 CM-8 CM-9 N/A N/A Management O – ISDM Toolkit Management Management/BEA Not currently in place (Withdrawn)* Management Management Management O – ISDM Toolkit Configuration Management Policy and Procedures Baseline Configuration Configuration Change Control O – ISDM Toolkit Security Impact Analysis Access Restrictions for Change Operational Configuration Settings O – AP&P 4-03 (X.N. 8) Least Functionality Information System Component Inventory Configuration Management Plan O – AP&P 4-05. Contingency Planning CP-1 CP-2 CP-3 CP-4 CP-5 CP-6 CP-7 CP-8 Contingency Planning Policy and Procedures Contingency Plan Contingency Training Contingency Plan Testing and Exercises Contingency Plan Update Operational O – DR/COOP Function (Withdrawn) Alternate Storage Site Alternate Processing Site Operational O – DR/COOP Function Telecommunications Services Page 3 of 8 Note: This document is owned by the DIS Information Security Office, please direct inquiries or revisions to DIS-InformationSecurityOffice@myfloridacfo.com. See the Security Control Catalog located on pages 77-206 in NIST Special Publication 800-53 for descriptions, safeguards, and countermeasures. *Withdrawn indicates that NIST removed applicability or moved to alternative control group. CP-9 CP-10 Information System Backup Information System Recovery and Reconstitution Operational/WIN Operational/DBA I&A IA-3 Identification and Authentication Policy and Procedures Identification and Authentication (Organizational Users) Device Identification and Authentication IA-4 Identifier Management IA-5 IA-6 IA-7 Authenticator Management IA-1 IA-2 IA-8 Authenticator Feedback Cryptographic Module Authentication Identification and Authentication (Non-Organizational Users) Technical O – AP&P’s 4-03, 4-04, and 4-05 Technical/BEA Technical/BEA Technical O – AP&P’s 4-03, 4-04, and 4-05 (User Account management). Technical/BEA Technical Technical/WIN Specified in AP&P’s 4-03 Technical/BEA Incident Response IR-1 IR-2 IR-3 IR-4 IR-5 IR-6 IR-7 IR-8 Incident Response Policy and Procedures Incident Response Training Incident Response Testing and Exercises Incident Handling Incident Monitoring Operational O – CSIRT Function Operational O – Change Management Function Incident Reporting Incident Response Assistance Incident Response Plan Maintenance MA-1 MA-2 MA-3 MA-4 MA-5 MA-6 System Maintenance Policy and Procedures Controlled Maintenance Maintenance Tools Non-Local Maintenance Maintenance Personnel Timely Maintenance Media Protection Page 4 of 8 Note: This document is owned by the DIS Information Security Office, please direct inquiries or revisions to DIS-InformationSecurityOffice@myfloridacfo.com. See the Security Control Catalog located on pages 77-206 in NIST Special Publication 800-53 for descriptions, safeguards, and countermeasures. *Withdrawn indicates that NIST removed applicability or moved to alternative control group. MP-1 MP-2 MP-3 MP-4 MP-5 MP-6 Media Protection Policy and Procedures Media Access Operational O – Data Center Controls Operational O – Operating Procedure DIS-006 Operational O – Data Center Controls Management Management O – AP&P 4-03 O – ISDM Toolkit Media Marking Media Storage Media Transport Media Sanitization Physical & Environmental Protection PE-1 PE-2 PE-3 PE-4 PE-5 PE-6 PE-7 PE-8 PE-9 PE-10 PE-11 PE-12 PE-13 PE-14 PE-15 PE-16 PE-17 PE-18 PE-19 Physical and Environmental Protection Policy and Procedures Physical Access Authorizations Physical Access Control Access Control for Transmission Medium Access Control for Output Devices Monitoring Physical Access Visitor Control Access Records Power Equipment and Power Cabling Emergency Shutoff Emergency Power Emergency Lighting Fire Protection Temperature and Humidity Controls Water Damage Protection Delivery and Removal Alternate Work Site Location of Information System Components Information Leakage Planning PL-1 PL-2 PL-3 Security Planning Policy and Procedures System Security Plan System Security Plan Update (Withdrawn)* Page 5 of 8 Note: This document is owned by the DIS Information Security Office, please direct inquiries or revisions to DIS-InformationSecurityOffice@myfloridacfo.com. See the Security Control Catalog located on pages 77-206 in NIST Special Publication 800-53 for descriptions, safeguards, and countermeasures. *Withdrawn indicates that NIST removed applicability or moved to alternative control group. PL-4 PL-5 PL-6 Rules of Behavior Privacy Impact Assessment Security-Related Activity Planning Management/BEA Management/BEA Management O – ISDM Toolkit, DR & CSIRT functions Operational O – Multiple DFS AP&P’s Management O – AP&P 4-03 O – SSP O – SSP Checklist Personnel Security Personnel Security Policy and PS-1 Procedures Position Categorization PS-2 Personnel Screening PS-3 Personnel Termination PS-4 Personnel Transfer PS-5 Access Agreements PS-6 Third-Party Personnel Security PS-7 Personnel Sanctions PS-8 Risk Assessment RA-1 RA-2 RA-3 RA-4 RA-5 Risk Assessment Policy and Procedures Security Categorization Risk Assessment Risk Assessment Update Vulnerability Scanning (Withdrawn) Management To be implemented… Management O – AP&P 4-06 Management ISDM Toolkit Management Management Management N/A N/A ISDM Toolkit Management/BEA IDENTIFICATION OF FUNCTIONS, PORTS, PROTOCOLS, SERVICES Management Management ISDM Toolkit ISDM Toolkit System & Services Acquisition SA-1 SA-2 SA-3 SA-4 SA-5 SA-6 SA-7 SA-8 System and Services Acquisition Policy and Procedures Allocation of Resources SA-9 External Information System Services Developer Configuration Management Developer Security Testing SA-10 SA-11 Life Cycle Support Acquisitions Information System Documentation Software Usage Restrictions User-Installed Software Security Engineering Principles Page 6 of 8 Note: This document is owned by the DIS Information Security Office, please direct inquiries or revisions to DIS-InformationSecurityOffice@myfloridacfo.com. See the Security Control Catalog located on pages 77-206 in NIST Special Publication 800-53 for descriptions, safeguards, and countermeasures. *Withdrawn indicates that NIST removed applicability or moved to alternative control group. SA-12 SA-13 Supply Chain Protection SA-14 Critical Information System Components Trustworthiness Management Management Management/WIN WIN N/A N/A (pending RMF) System & Communications Protection SC-1 SC-2 SC-3 SC-4 System and Communications Protection Policy and Procedures Application Partitioning Information in Shared Resources Technical Technical/BEA Technical Technical/WIN SC-5 Denial of Service Protection Technical/WIN Resource Priority Technical Technical/WIN Technical/WIN Technical/WIN Technical/WIN Technical Technical/WIN Technical/WIN Technical/WIN Technical Technical Technical Technical/BEA Technical Technical/BEA SC-6 SC-7 SC-8 SC-9 SC-10 SC-11 SC-12 SC-13 SC-14 SC-15 SC-16 SC-17 SC-18 SC-19 SC-20 SC-21 SC-22 SC-23 SC-24 SC-25 Security Function Isolation Boundary Protection Transmission Integrity Transmission Confidentiality Network Disconnect Trusted Path Cryptographic Key Establishment and Management Use of Cryptography Public Access Protections Collaborative Computing Devices Transmission of Security Attributes Public Key Infrastructure Certificates Mobile Code Voice Over Internet Protocol Secure Name /Address Resolution Service (Authoritative Source) Secure Name /Address Resolution Service (Recursive or Caching Resolver) Architecture and Provisioning for Name/Address Resolution Service Session Authenticity Fail in Known State Thin Nodes AP&P 4-03, AP&P 4-04 N/A N/A N/A N/A N/A N/A N/A Technical/WebDev Technical/WIN Technical/BEA Technical Technical N/A N/A Page 7 of 8 Note: This document is owned by the DIS Information Security Office, please direct inquiries or revisions to DIS-InformationSecurityOffice@myfloridacfo.com. See the Security Control Catalog located on pages 77-206 in NIST Special Publication 800-53 for descriptions, safeguards, and countermeasures. *Withdrawn indicates that NIST removed applicability or moved to alternative control group. SC-26 SC-27 SC-28 SC-29 SC-30 SC-31 SC-32 SC-33 SC-34 Honey pots Operating System-Independent Applications Protection of Information at Rest Heterogeneity Virtualization Techniques Covert Channel Analysis Information System Partitioning Transmission Preparation Integrity Non-Modifiable Executable Programs Technical Technical Technical/BEA Technical Technical Technical Technical/DBA Technical Technical N/A N/A N/A N/A N/A SC-8 N/A System & Information Integrity SI-1 SI-2 SI-3 SI-4 SI-5 SI-6 SI-7 SI-8 SI-9 SI-10 SI-11 SI-12 System and Information Integrity Policy and Procedures Flaw Remediation Malicious Code Protection Operational Information System Monitoring Security Alerts, Advisories, and Directives Security Functionality Verification N/A O – AP&P 4-03 X. W.11.e O – AP&P 4-04, SPAM Reporting procedures Software and Information Integrity Spam Protection Information Input Restrictions Information Input Validation Error Handling Information Output Handling and Retention O – AP&P 4-03, DIS-015, AP&P 4-03 X. H., AP&P 4-03 XI, AP&P 4-03 XI Operational/BEA Operational/BEA Operational/BEA Operational CSIRT Function Page 8 of 8 Note: This document is owned by the DIS Information Security Office, please direct inquiries or revisions to DIS-InformationSecurityOffice@myfloridacfo.com. See the Security Control Catalog located on pages 77-206 in NIST Special Publication 800-53 for descriptions, safeguards, and countermeasures. *Withdrawn indicates that NIST removed applicability or moved to alternative control group.