Tutorial 7 - Prince Sultan University
advertisement

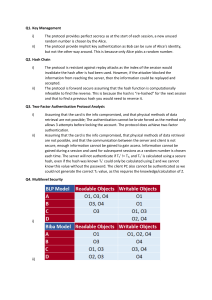
Prince Sultan University College of Computer & Information Sciences Department of Computer Science CS432: Computer Security Tutorial 5: Hash Functions & Wireless security 1- What are cryptographic hash functions, and for what purposes are they used? 2- What are the main required properties of cryptographic hash functions? 3- Discuss the use of hash functions in SSL (at what steps and for what purpose?). 4- Describe the MD5 hash algorithm. 5- Describe the SHA1 hash algorithms. 6- Give a general overview of the authentication process in 802.11 networks. 7- Explain how basic authentication may be performed using SSID’s and MAC filters in wireless LANs. What are the major drawbacks of this scheme? 8- Describe the WEP security protocol. What are the major parameters, and what is the encryption algorithms used? 9- What are the major types of authentication provided by WEP? 10- Explain how open authentication works. 11- Explain how shared key authentication works. 12- What are the major drawbacks of WEP? 13- What is 802.1x and what does it do? 14- Describe the general architecture of 802.1x and explain how it works. 15- What is WPA and how it works. 16- Describe the 802.11i security protocol and highlight its improvements over WEP.