HW9
advertisement
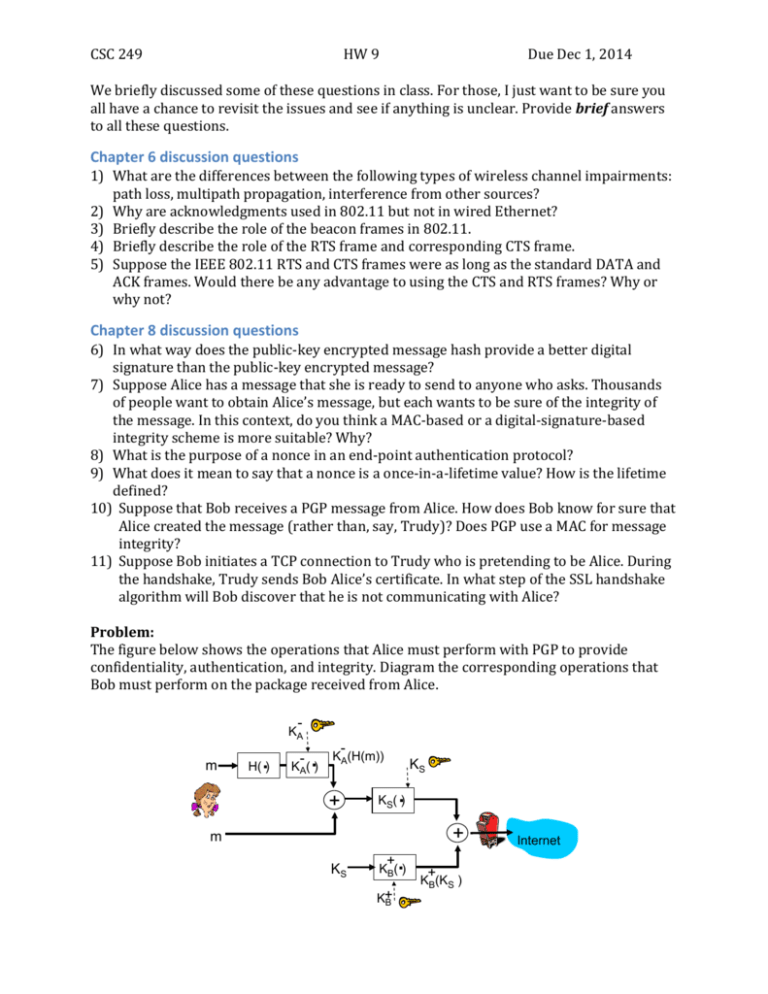
CSC 249 HW 9 Due Dec 1, 2014 We briefly discussed some of these questions in class. For those, I just want to be sure you all have a chance to revisit the issues and see if anything is unclear. Provide brief answers to all these questions. Chapter 6 discussion questions 1) What are the differences between the following types of wireless channel impairments: path loss, multipath propagation, interference from other sources? 2) Why are acknowledgments used in 802.11 but not in wired Ethernet? 3) Briefly describe the role of the beacon frames in 802.11. 4) Briefly describe the role of the RTS frame and corresponding CTS frame. 5) Suppose the IEEE 802.11 RTS and CTS frames were as long as the standard DATA and ACK frames. Would there be any advantage to using the CTS and RTS frames? Why or why not? Chapter 8 discussion questions 6) In what way does the public-key encrypted message hash provide a better digital signature than the public-key encrypted message? 7) Suppose Alice has a message that she is ready to send to anyone who asks. Thousands of people want to obtain Alice’s message, but each wants to be sure of the integrity of the message. In this context, do you think a MAC-based or a digital-signature-based integrity scheme is more suitable? Why? 8) What is the purpose of a nonce in an end-point authentication protocol? 9) What does it mean to say that a nonce is a once-in-a-lifetime value? How is the lifetime defined? 10) Suppose that Bob receives a PGP message from Alice. How does Bob know for sure that Alice created the message (rather than, say, Trudy)? Does PGP use a MAC for message integrity? 11) Suppose Bob initiates a TCP connection to Trudy who is pretending to be Alice. During the handshake, Trudy sends Bob Alice’s certificate. In what step of the SSL handshake algorithm will Bob discover that he is not communicating with Alice? Problem: The figure below shows the operations that Alice must perform with PGP to provide confidentiality, authentication, and integrity. Diagram the corresponding operations that Bob must perform on the package received from Alice. - KA m . H( ) - . KA( ) - KA(H(m)) + KS . KS( ) + m KS + . KB( ) K+ B + KB(KS ) Internet











