HernandezVectorDB2013_2_9 - College of Engineering and
advertisement

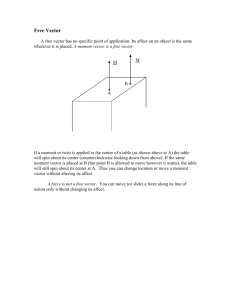
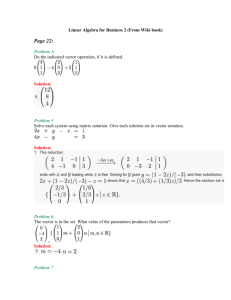
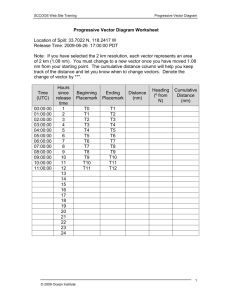
Joseph Hernandez hernandezjv2@gmail.com University of Colorado Colorado Springs Project Portfolio Vulnerability Enumeration Consolidation To Reporting Database (Vector DB) Joseph E Hernandez Masters of Engineering in Information Assurance 26 Mar 2013 Page | 1 Joseph Hernandez hernandezjv2@gmail.com Table of Contents Introduction .................................................................................................................................................. 2 Project Overview .......................................................................................................................................... 3 Development ................................................................................................................................................ 5 Database Structure ................................................................................................................................... 5 Application Functions ............................................................................................................................... 6 STIG Findings Import Form ................................................................................................................... 6 Build Final Report ....................................................................................... Error! Bookmark not defined. Conclusion .................................................................................................................................................... 8 References .................................................................................................................................................... 8 Table of Figures Figure 1 - Vector Main Control Form............................................................................................................ 4 Figure 2 - Vector Database Relationships..................................................................................................... 6 Introduction My name is Joseph Hernandez and I’m currently a Graduate Student pursuing a Masters of Engineering in Information Assurance (MEIA) Degree from the University of Colorado, Colorado Springs. I have been working in the Information Assurance Field for 15 Years and had obtained two Bachelor’s Degrees in Computer Science and Electronics Management from the University of Nebraska and Southern Illinois University prior to starting this program. I’ve seen a dramatic increase in the importance of Computer Security and Information Assurance (IA) over the last decade and felt the MEIA program combined with my background would open a new world of opportunity for me in this hot and critically important field. To further expand my background and obtain a synergistic affect with the MEIA degree I also obtained two professional certifications, Certified Information Assurance Professional (CISSP) and Certified Ethical Hacker (C|EH) since starting the program in 2009. I’m currently employed by Jacobs Technology, a subsidiary of Jacobs Engineering, supporting the 46th Test Squadron out of Eglin Air Force Base, Florida, on a Systems Engineering Support Contract that provides IA Support to the United States Air Force. I received this job largely in part of my enrolment in the MEIA program! With this project portfolio I expect to graduate in December of 2013 after completing my last class, Operating Systems (CS-5500), this Fall Semester. Page | 2 Joseph Hernandez hernandezjv2@gmail.com As a Systems Security Engineer supporting the 46th Test Squadron, a lot of what I learned in the MEIA program helps me immensely in my work. I provide system security design, conduct security testing and technical assessments of security configurations, policy and procedures for numerous Air Force Space and Missile Programs supporting Head Quarters United States Air Force Space Command, Air Force Life Cycle Management Center, Space Material Command, and various other military organizations. Multiple classes that I have completed in this degree program like Fundamentals of Computer/Network Security, Advanced System Security, Advanced Web Systems, Topics in Web Security and Applied Cryptography have provide me with a solid foundation in current and relevant security topics and security best practices that I consistently depend upon. Having a strong knowledge in topics like Public Key Infrastructure, Firewalls, Intrusion Detection Systems and web technologies are important for today’s Security Engineers. Additionally participating in the International Capture the Flag (ICTF) event has expanded my knowledge of computer hacking techniques in a real and practical hands on scenario! I have chosen to present some recent work on the development of an application database know as the Vulnerability Enumeration Consolidation To Reporting Database (Vector DB) that aids a security engineer in conducting a security evaluation, vulnerability analysis and risk assessment. Vector DB has become an important tool for consolidating technical findings, security vulnerabilities, evaluating associated residual risk and generate automated reports that summarize the systems overall security posture, for the Designated Accrediting Authority (DAA) prior to granting any Air Force System an Authority To Operate (ATO). Project Overview This paper was completed solely for the purpose of this Project Portfolio; no part of this paper was taken from any work related documents, nor did I receive any help in writing this paper. As a security engineer I’m charged with assisting multiple programs in designing, developing and evaluating security architectures that are consistent with their mission areas and operational requirements. The Department of Defense (DoD) 8500.2, Information Assurance Implementation, instruction provides the primary guidance and defines the IA standards DoD systems are built upon [1]. This guide forms the basis of security controls that must be compliant within systems security architectures, plans, policies and procedures before the system obtains an ATO through the DoD Information Assurance Certification and Accreditations Process (DIACAP) [2]. Together these documents define the process and a set of IA Controls that correspond to the IA Triad of Confidentiality, Integrity and Availably (CIA), for all DoD systems. These IA Controls are subdivided into nine general areas based on Mission Assurance Category (MAC) and Confidentiality Level (CL) [3] that define the subset of specific IA controls that provide the Defense-In-Depth security measures for a critical system. These security assessments involve the collection, evaluation and review of numerous security related documents like system requirements, security design documents, security policy and appointment letters, hardware and software baselines, network drawings, network ports and protocols, to very detailed security configuration for various systems, servers, clients, firewalls, intrusion detection systems, databases, web servers, etc. that cover the full scope of most modern day computer system. Each one of these documents typically related to one or more of the IA Controls assigned to a given system. Tracking, consolidating, evaluating, and assessing the overall risk in accordance with DoD defined security policy is an enormous undertaking for a security engineer and a monumental task with limited or no tools to help. This is where the Page | 3 Joseph Hernandez hernandezjv2@gmail.com idea for Vector DB was born; I wanted to develop an automated system that would provide a consolidated tool to aid and guide an engineer through the security evaluation and simplify the process of conducting a thorough evaluation and risk assessment. The Overall goal of Vector DB was three fold; 1) Import all DoD requirements outlined in the DIACAP and DoD 8500.2 into a single database, 2) Consolidate input from the various DoD Security Technical Implementation Guides (STIGs) and IA Testing Tools and 3) Provide an easy to use application that could help evaluate all the data, consolidate detailed security assessments and generate automated test reports that outline the systems compliance according to DoD requirements. The challenge with Vector DB was to utilize a single product that could meet the three goals mentioned above and be utilized on the Air Force Global Information Grid (GIG) without additional security testing, licenses, cost, and approvals or accreditations. Simplicity was paramount in this effort so I had to utilize software that was already available on the Air Force Enterprise and was already installed on the majority of Air Force Systems— Microsoft Office Access Database. Below is a screenshot of the Vector DB Main Control Form. This form is used to help guide a System Security Engineer through the evaluation process outlined in conducting an assessment [4], through a series of action buttons that step through the analysis. On the left we have System Options that equate to “Work Flow” from importing a new system in the database, assigning applicable IA Controls, to importing and evaluating technical findings and determining compliance with a given IA Control. The right side provides Database Options used to evaluate and access information from the DoD 8500 Series. At the bottom we have report generation; the bottom left Quick Reports are used to monitor the status/progress of the evaluation, on the bottom right Final Reports provides the options to generate reports like a Method Of Test (MOT) Report and Draft Final Report. Figure 1 - Vector Main Control Form Page | 4 Joseph Hernandez hernandezjv2@gmail.com Development Database Structure In order to build the database structure I first had to develop an understanding of the overall security assessment process the security relevant data and formats that would be collected so I could develop the proper tables. One of the initial challenges of this project was to build the relational database structure that would form the foundation for the development of Vector DB. There are many relationships defined in the database with a total of 16 tables in all, due to the complex IA relationships only someone with detailed knowledge in the IA process would be able to understand and define them. Building these tables requires knowledge of the structure of the Defense Information Systems Agency (DISA) Security Technical Implementation Guides (STIGs), for reference I utilized the Application Security and Development Checklist [5] that provides a great overview of IA Controls upon which to build the database tables. Additionally this STIG is extremely important to anyone working in the field of IA or trying to develop any secure system or software. I’ll briefly explain five of the main dynamic tables, IAControls, SystemInfo, System_ Assigned_IAControls, SubSystems, and STIGFindingsBySubSystem, and how they relate to the security assessment process. The IA Controls Table contains information from DoD 8500.2 and the DIACAP Knowledge Site that defines all the Security Controls required to ensure the CIA of an information system are being met, monitored, and managed accordingly. There are 157 IA Controls defined, they are grouped into eight main categories, Continuity (CO), Security Design and Configuration (DC), Enclave Boundary (EB), Defense Enclave Computing Environment (EC), Identification and Authentication (IA), Physical and Environmental (PE) , Personnel (PR) and Vulnerability and Incident Management (VI). Each one of these categories consists of multiple IA Controls and one or more Validation Procedures (another table in the database). The Validation Procedures further define the information necessary to complete the assessment of a give IA Control. The entire evaluation is based on a subset of system specific IA Controls that are defined by two criteria, the MAC and the Confidentiality Level (CL) of the System as defined by the data it processes, Classified, Sensitive or Public. The next table SystemInfo is the basic starting point for Vector DB, this is where a security engineer, assigned to evaluate a system imports critical information about the system, like the Systems Name, Acronym, Project Number, etc.. The primary input on this table, managed by the SystemsInfoForm, is the Assigned MAC and CL of the system. Once this info is input, the database will dynamically generate the next table, System_Assigned_IAControls, by selecting the subset of IA Controls applicable to this particular system. For example a system assigned as a MAC I – Classified system it will have 110 of the 157 IA Controls Assigned according to DoD guidelines. Currently the DoD is in the process of transitioning to the Risk Management Framework, which according to NIST 800-53 defines a new set of IA Controls for DoD systems. Under this new framework RMF Step 2 – Select Security Controls [6] the IA controls in this table would change but the overall process would remain the same. The SubSystems table is where individual subsystems evaluated during a technical assessment are input. This includes their component name and associated data files. Each subsystem is evaluated according to one of the applicable DISA STIGs, NSA Security Configurations Guides, or industry best practices. The DISA STIGs can be found at http://iase.disa.mil/stigs/a-z.html while the NSA Security Guides can be found at http://www.nsa.gov/ia/mitigation_guidance/security_configuration_guides/. Page | 5 Joseph Hernandez hernandezjv2@gmail.com The final table and one of the largest in the database is the STIGFindingsBySubSystem where all the technical findings generated during a test are imported, associated to an IA Control, and evaluated by the Security Engineer for overall Risk to the System. Identifying a non-compliant system configuration (known as a finding) does not always equate to a vulnerability, this is where the Security Engineer will rely heavily on Vector DB to provide all the information necessary to make a detailed assessment. The information used to populate the STIGFindingsBySubSystem table is generated by three different tools used in conducting an IA Assessment. One of these tools that I’ll address in this paper is the DISA STIG Viewer available from the IASE link above. Vector DB is capable of importing data files from these three tools in basically the same manner, and XML import using the Document Object Model (DOM), so I’ll only address the STIG Viewer. Figure 2 - Vector Database Relationships Application Functions Vector DB has numerous Access Database Forms, Objects and Modules that were built for this project as depicted in Figure 3 – Class Objects and Modules below. For brevity of this paper I’ve chosen to discuss two of these objects, STIGFindingsImportForm and BuildFinalReport Module. STIG Findings Import Form The first form, STIGFindingsImportForm allows an engineer to import STIG findings from multiple test tools into the database. The majority of these tools save their data in a XML file, so the purpose of this form and Page | 6 Joseph Hernandez hernandezjv2@gmail.com associated modules was to first create a database entry for each subsystem and then to load the respective XML files into the database. The majority of the code in this module parses the XML DOM utilizing the Microsoft DOM Document Object associating each node in the XML file with the respective database fields for every vulnerability record. As an example a few lines of the XML file shown below outlines the Vulnerability Attribute and Attribute Data, for the Vulnerability Number (Unique ID), Severity Code and Group Title, a subset of the 21 attributes in the file for each system vulnerability. The following snip of code shows how the module parses these XML fields and populates the database table for each record. Each XML Node is parsed using XPath expressions and a database record set (rst) is opened, populated then updated to the respective database table. In this example the Severity is enumerated from “high”, “medium” and “low” to 1, 2, 3 respectively for consistency within the database when compared to the severity of other tools that use 1-3, one being the highest severity associated with a given vulnerability. Page | 7 Joseph Hernandez hernandezjv2@gmail.com Conclusion This project was my first major software project related to Computer Security taking me about 10 weeks to complete. A short eight-page paper doesn’t do Vector DB or the IA knowledge I have obtained in this degree program any justice but a demo could be provided as necessary. While the programming behind the scenes of Vector DB could be done by most anyone it’s the knowledge obtained in this program combined with my experience in computer security that led to its development. To the best of my knowledge there are no other applications available on the market today that combine both the technical side of a security evaluation with the policy and procedures defined by the DIACAP. I learned a lot during the design, development and testing of Vector DB, but this is clearly the culmination of what I’ve learned from the MEIA program and my IA experience over the last few years. I was able to apply a lot of what I learned during my degree program including CS-5310 and CS-5320, Software Requirements and Software Design, to bring this project together. This project also included increasing my knowledge in relational databases, XML, VBA, Microsoft Word Macros, good coding practices, testing, documentation and training. Overall this was a well-rounded project that allowed me to clearly demonstrate the knowledge and capabilities a graduate from the MEIA program brings to the filed of Computer Security and Information Assurance. References [1] Department of Defense Instruction 8500.2, February 6, 2003. [2] Department of Defense Information 8510.01, November 28, 2007. [3] Sarah Pramanik, “Increased security for DoD systems, through specific security applications”, PH.D. Thesis Proposal, University of Colorado, Colorado Springs, Colorado, 2011. [4] National Institute of Standards and Technology Special Publication 800-30, September 2012 [5] Defense Information Systems Agency Application Security and Development Checklist, October 28, 2011. [6] National Institute of Standards and Technology Special Publication 800-37, February 2010 Page | 8