Modern symmetric key ciphers
advertisement

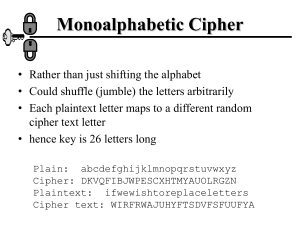
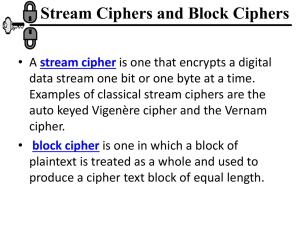
Encipherment Using Modern Symmetric-Key Ciphers Objectives ❏ To show how modern standard ciphers, such as DES or AES, can be used to encipher long messages. 8.2 8-1 USE OF MODERN BLOCK CIPHERS Symmetric-key encipherment can be done using modern block ciphers. Modes of operation have been devised to encipher text of any size employing either DES or AES. 8.3 Continued Modes of operation 8.4 Electronic Codebook (ECB) Mode The simplest mode of operation is called the electronic codebook (ECB) mode. Electronic codebook (ECB) mode 8.5 Pattern at block level are preserved Block independence creates opportunities for Eve to exchange some cipher text block without knowing key. 8.6 Example Assume that Eve works in a company a few hours per month (her monthly payment is very low). She knows that the company uses several blocks of information for each employee in which the seventh block is the amount of money to be deposited in the employee’s account. Eve can intercept the ciphertext sent to the bank at the end of the month, replace the block with the information about her payment with a copy of the block with the information about the payment of a full-time colleague. Each month Eve can receive more money than she deserves. Error Propagation A single bit error in transmission can create errors in the corresponding block. However, the error does not have any effect on the other blocks. 8.8 Cipher Block Chaining (CBC) Mode In CBC mode, each plaintext block is exclusive-ored with the previous ciphertext block before being encrypted. Cipher block chaining (CBC) mode 8.9 Cipher block chaining (CBC) mode 8.10 Continued It can be proved that each plaintext block at Alice’s site is recovered exactly at Bob’s site. Because encryption and decryption are inverses of each other, Initialization Vector (IV) The initialization vector (IV) should be known by the sender and the receiver. Error Propagation In CBC mode, a single bit error in ciphertext block Cj during transmission may create error in most bits in plaintext block Pj during decryption. 8.12 Cipher Feedback (CFB) Mode In some situations, we need to use DES or AES as secure ciphers, but the plaintext or ciphertext block sizes are to be smaller. Encryption in cipher feedback (CFB) mode 8.13 Note In CFB mode, encipherment and decipherment use the encryption function of the underlying block cipher. The relation between plaintext and ciphertext blocks is shown below: 8.14 CFB as a Stream Cipher Cipher feedback (CFB) mode as a stream cipher 8.15 Output Feedback (OFB) Mode In this mode each bit in the ciphertext is independent of the previous bit or bits. This avoids error propagation. Encryption in output feedback (OFB) mode 8.16 OFB as a Stream Cipher Output feedback (OFB) mode as a stream cipher 8.17 Counter (CTR) Mode In the counter (CTR) mode, there is no feedback. The pseudorandomness in the key stream is achieved using a counter. Encryption in counter (CTR) mode 8.18 Counter (CTR) mode as a stream cipher 8.19 Comparison of Different Modes 8.20 USE OF STREAM CIPHERS Although the five modes of operations enable the use of block ciphers for encipherment of messages or files in large units and small units, sometimes pure stream are needed for enciphering small units of data such as characters or bits. RC4 A5/1 8.21 RC4 RC4 is a byte-oriented stream cipher in which a byte (8 bits) of a plaintext is exclusive-ored with a byte of key to produce a byte of a ciphertext. State RC4 is based on the concept of a state. The idea of RC4 stream cipher 8.23 Initialization Initialization is done in two steps: 8.24 Key Stream Generation The keys in the key stream are generated, one by one. Algorithm 8.26 Algorithm Continued 8.27 A5/1 A5/1 (a member of the A5 family of ciphers) is used in the Global System for Mobile Communication (GSM), a network for mobile telephone communication.. General outline of A5/1 8.28 Key Generator A5/1 uses three LFSRs with 19, 22, and 23 bits. Three LFSR’s in A5/1 8.29 Initialization 1. set all bits in three LFSRs to 0. 2. Mix the 64 bit key with the value of register according to following code 3. Repeat above procedure but use 22 bit frame buffer 8.30 4. For 100 cycles clock the whole generator but use majority function to see which LFSR should be clocked. 8.31 A5/1 working example 0 18 17 16 01 1 0111 00 11 01 00 11 00 11 01 00 11 00 11 00 1 10 R1 C1 10 21 20 11 clock control 0 10 0 1111 0 0 01 10 00 01 10 011001100111111000011 R2 C2 1 0 22 21 20 0 11 00 11 00 11 0 01 0 10 1 01 10 11 11 01 10 11 01 00 10 01 1001 C3 R3 0 Prevent (or at least detect) unauthorized modification of data Encryption provides confidentiality (prevents unauthorized disclosure) Encryption alone does not assure integrity 8.34 The cryptography systems that we have studied so far provide secrecy, or confidentiality, but not integrity. However, there are occasions where we may not even need secrecy but instead must have integrity One way to preserve the integrity of a document is through the use of a fingerprint. If Alice needs to be sure that the contents of her document will not be changed, she can put her fingerprint at the bottom of the document. 8.35 Message and Message Digest The electronic equivalent of the document and fingerprint pair is the message and digest pair. Message and digest 11.36 Difference The two pairs (document / fingerprint) and (message / message digest) are similar, with some differences. The document and fingerprint are physically linked together. The message and message digest can be unlinked separately, and, most importantly, the message digest needs to be safe from change. Note The message digest needs to be safe from change. 11.37 Checking Integrity Checking integrity 11.38 Cryptographic Hash Function Criteria A cryptographic hash function must satisfy three criteria: preimage resistance, second preimage resistance, and collision resistance. Criteria of a cryptographic hash function 11.39 Preimage Resistance Preimage 11.40 Second Preimage Resistance Second preimage 11.41 Continued Collision Resistance Collision 11.42 A message digest does not authenticate the sender of the message. To provide message authentication, Alice needs to provide proof that it is Alice sending the message and not an impostor. The digest created by a cryptographic hash function is normally called a modification detection code (MDC). What we need for message authentication is a message authentication code (MAC). 8.43 A modification detection code (MDC) is a message digest that can prove the integrity of the message: that message has not been changed. If Alice needs to send a message to Bob and be sure that the message will not change during transmission, Alice can create a message digest, MDC, and send both the message and the MDC to Bob. Bob can create a new MDC from the message and compare the received MDC and the new MDC. If they are the same, the message has not been changed. 8.44 8.45 Message Authentication Code (MAC) Message authentication code 11.46 Note The security of a MAC depends on the security of the underlying hash algorithm. 11.47 Continued Nested MAC Nested MAC 11.48 Continued HMAC Details of HMAC Ipad=(36)H Opad=(5c)H 11.49 Continued CMAC 11.50 8.51