Steganografie
advertisement

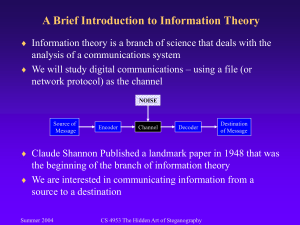
Faculty of Business and Economics Tomáš Foltýnek foltynek@pef.mendelu.cz Steganography. CyberWars Tomas Foltynek Department of Informatics Faculty of Business and Economics Mendel University in Brno Czech republic Steganography What is steganography • Part of cryptology • Art/science about hiding the very existence of message • Word origin from Greek – Stegos = hidden – Graphein = write • Hidden message doesn’t attract attention – No need to encrypt – Combination of steganography and cryptology ensures discreetness and security Steganography Using steganograpghy • In countries, where cryptography is illegal • When we want to hide the existence of message • Secret services – monitoring people – printer tracking dots • Private companies – copyright protection – WoW – hidden information in screenshots Steganography Steganography v antiquity • Salamis battle (480 B.C.) – Persians were about to attack Greece – Greek Damaratus hid a message under wax on empty tables – Greeks won • Mesage in hair (described by Herodotos) – Histiaios wanted to encourage Aristagor of Milet to revolt against Persians – Shaved messenger‘s hair, tattooed a message, waited until hair grew backg, then sent the messenger • Romans – Secret inks based on fruit juice or milk Steganography Steganography in middle ages • Ancient China – message on silk in wax bullet – messenger swallowed • Giovanni Porta (16. century) – special ink – write message to egg, boil – message penetrates the shell to eggwhite Steganography Boer war • Lord Robert Baden-Powell – founder of scout movement • Needed to draw a plan of boerean artillery configuration • For the case of capture, plan had to be discrete • Drawed a meadow with butterflies • Butterfles encoded artillery objects Steganography Twentieth century • WW2 – microdots – null messages • messages without real meaning • carry just hidden message • messages in radio, etc. – Common paranoia led to ban of sending newspaper clippings, flowers and childrens‘ drawings • Digital steganography – new opportunities Steganography N O T I C E Upper people try catching star kites. Do Indians ask at far trains? Attach asterisk to any of error file. Add last byte. Steganography N O T I C E Upper people try catching star kites. Do Indians ask at far trains? Attach asterisk to any of error file. Add last byte. Steganography Second letters • „Apparently neutral's protest is thoroughly discounted and ignored. Isman hard hit. Blockade issue affects pretext for embargo on by-products, ejecting suets and vegetable oils.“ • Used by German spy • PERSHING SAILS FROM NY JUNE 1 Steganography Digital Steganography • Any data can serve as a carrier • Human senses mustn’t notice a message • • • • • Hiding to text Hiding to images Hiding to audio files Hiding to video files Hiding to executables Steganography Hiding to formatted text • Using different fonts • Bacon cipher A = AAAAA N = ABBAA B = AAAAB O = ABBAB C = AAABA P = ABBBA – Francis Bacon (1561-1626) D = AAABB Q = ABBBB – Carrier 5 times longer than a message E = AABAA R = BAAAA F = AABAB S = BAAAB – Carrier written by two fonts G = AABBA T = BAABA – SOME TWENTY FIVE H = AABBB U + V = BAABB I + J = ABAAA W = BABAA LETTERS HERE K = ABAAB X = BABAB L = ABABA Y = BABBA M = ABABB Z = BABBB Steganography What is cryptology • Science of Cryptography and cryptanalysis • Cryptography – science of secret codes, enabling the confidentiality of communication through an insecure channel – e.i. how to make a message uncomprehensible for unauthorised persons • Cryptanalysis – theory of (in)security analysis of cryptographic systems – e.i. how to break ciphers and read secret messages • Also includes Steganography & Steganalysis – how to hide a message – how to find a hidden message • Word origin from Greek: crypto = hidden Steganography The Paradigms of Cryptography • Confidentiality – the content of a message remains secret – information should’n leak to third party • Data integrity – to avoid any malicious data manipulation • insertion, deletion, substitution • Authentication – identification of the author – signature authentication, access control, etc. Steganography Other Goals of Cryptography • Authorisation – confirmation about data origin • Non-repudiation – nobody can deny previous action • Practical notions – Anonymity, electronic payment, electronic votes, zero-knowledge protocol,… Steganography Where to use cryptography? • • • • • • Internet banking Phone calls Paid TV Multi-user OS Business Communication with the government • Love letters • Quizzes, games, etc. Steganography Cryptographic methods • Transposition – change the position of letters – letters remain the same • Substitution – position of letters remain the same – letters in the message are changed Steganography Transposition • The position of letters is changed • Example: IWSAYNMNAERG – TAMNADAYYAAO IAIGOBTEE – NKNDMYHSA TAAADNHRLVDHMOMYNW – HTMIETEEIEWOYUAKO BTEAEFNAELE – YHNMOANBLE • Solution: It was many and many a year ago In a kingdom by the sea That a maiden there lived whom you may know By the name of Annabel Lee Steganography Scytale (Sparta) • First military cipher in history • Leather tape wound on a pole of given thickness Steganography Substitution • The letters are changed • Codes – binary code – Morse code • Ciphers – Alphabet shifting (Caesar cipher) – Polyalfabetic substitution (Vigenère cipher) Steganography Let’s play a game… • Make groups of three – Alice – Bob – Eve (sitting between Alice and Bob) • First round – – – – – Eve shuts her ears Alice and Bob agree on the way of coding Eve can hear from now on Alice sends a message to Bob Eve tries to understand this message • Second round – Eve can hear all the communication from the beginning – Alice and Bob agree on the way of coding (Eve hears them) – Bob has to send a message secretly to Alice Steganography General encryption process • Sender applies encryption algorithm to a plain text • S/he gains a cipher text, sends it to the receiver • Recipient applies decryption algorithm to the cipher text • S/he gains the plain text again Steganography Division of Cryptography • Symmetric cryptography – both sender and recipient have the same key – deciphering is an inversion of enciphering • Asymmetric cryptography – – – – sender and recipient have different keys mathematic relation algorithms are generally different useful for both encryption and digital signature Steganography Modular arithmetics • Arithmetics on a cyclic set • 2 + 3 = 5 (mod 7) • 5 + 4 = 2 (mod 7) • 5 · 4 = 6 (mod 7) – because 20/7 = 2, remainder 6 • 11 · 9 = 1 (mod 7) – because 99/7 = 14, remainder 1 • 35 = 5 (mod7) Steganography XOR operation • eXclusive OR • Logical OR, only one of two given expression can be true – – – – 00=0 01=1 10=1 11=0 • Sum modulo 2 • Simple enciphering and deciphering C = M K, M = C K Steganography Kerckhoffs’ principle • Basic cryptographic principle • Dutch lingvist Auguste Kerckhoffs von Nieuwenhoff (1883) “A cryptosystem is secure even if everything about the system, except the key, is public knowledge” • Security shouldn’t depend on the secrecy of algorithm, but on the secrecy of the key Steganography Cryptology in Antiquity • Hebrew scholars (600 to 500 BC) – Atbash cipher • The battle of Salamis (480 BC) – message hidden under wax on empty tables • The revolat against Persians – The message tattooed to the shaved head of a slave, hiddeb by regrown hair • China – message writen on silk in a wax bullet, messenger swallowed the bullet… Steganography Caesar Cipher • Alphabet shifted by 3 abcdefghijklmnopqrstuvwxyz DEFGHIJKLMNOPQRSTUVWXYZABC • Example – veni, vidi, vici YHQL, YLGL, YLFL • Algorithm: alphabet shift • Key: by how many letters – 25 possible keys (English) Steganography Improvements of Caesar Cipher • Unsorted cipher alphabet abcdefghijklmnopqrstuvwxyz JULISCAERTVWXYZBDFGHKMNOPQ • More than 41010 possibilities • Monoalphabetic substitution cipher • Kryptanalysis via frequency analysis – found by arabic theologists Steganography Monoalphabetic cipher improvements • Zero letters – no meaning, change frequency • Code words • Homophonic substitution cipher – each letter has more representations according to its frequency – polygram frequency analysis Steganography Vigenère cipher • Polyalphabetic substitution cipher • 1586 Blaise de Vigenère • Enciphering: – Key – Plain text – Cipher text WHITEWHITEWHITEWHITEWHI diverttroopstoeastridge ZPDXVPAZHSLZBHIWZBKMZNM • Usage of tabula recta – sum mod 26 • Unbroken for 300 years Steganography Breaking Vigenère cipher • Charles Babbage (1791 – 1891) – Inventor of Difference Engines – Ciphers as a hobby • Kasiski examintaion – guessing key length KINGKINGKINGKINGKINGKING thesunandthemaninthemoon DPRYEVNTNBUKWIAOXBUKWWBT • Guessing the key – divide message to groups enciphered by the same letter – shifted alphabet – frequency analysis Steganography The unbreakable cipher • Problem of Vigenère cipher: repeating – we need a sequence of random letters – same length as the message • One time pad cipher – Gilbert Vernam (1890 – 1960) – unbreakability proved by C. Shannon – key distribution problem, practically useless Steganography Why was a computer invented? • New inventions mostly come of – human laziness – wars • First computer – 1943 Colossus – Great Britain, Bletchley Park – Breaking German ENIGMA code Steganography Steganography Steganography Breaking the Enigma • Poland – Marian Rejewski – codebooks for day key inference from repeated message key – mechanical decipherer – “bomb” • Alan Turing (1912 – 1954) – Inventor of Turing machine, founder of the theory of computation – Analysed plenty of messages • given structure (weather info) – New type of “bomb” guessing the key from ciphertext and supposed plaintext Steganography Steganography Computers in Cryptology • Breaking ciphers = trying huge amount of possibilities – computer does this in quite short time – the end of “classical” ciphers • One-way functions – computation of every input in polynomial time – computation of inverse in exponential time – P != NP problem Steganography Symmetric encryption algorithms • DES, 3DES, AES, IDEA – Block ciphers – Many rounds consisting of transpositions, permutations, substitutions, XOR with key, etc. • Security depends on the key length – – – – – – Let’s consider 128 bit key 2128 possible values 1GHz processor: 230 operations per second Breaking time: 298 seconds The age of the Universe: 260 seconds 1 more bit => breaking time doubles • Problem: How to distribute the key? Steganography Data Encryption Standard • Block symmetric cipher • 1973 – 1974 Horst Fiestel • 16 rounds, Fiestel funciton – expansion, XOR, substitution, permutation • Better methods than brute force attack are known • 3DES – good for the present Steganography Advanced Encryption Standard • Block symmetric cipher • 4 steps: – – – – AddRoundKey SubByte ShiftRows MixColumns • NSA top secret Steganography Key exchange algorithm • 1976 Diffie, Hellman, Merkle • One-way function Yx (mod P) – if we know the result, Y and P, it‘s infeasible to compute x • How to generate a common value – Alice and Bob agree on Y and P • via untrusted channel => Y and P are publicly known – Each of them has his/her own x • denoted A for Alice and B for Bob – – – – Alice counts α = YA (mod P), Bob counts β = YB (mod P) Alice and Bob exchange α and β Alice counts kA = βA (mod P), Bob counts kB = αB (mod P) Since kB = kA, both of them know the value of the key Steganography Asymmetric cryptography: RSA • A pair of keys is needed • How to generate a keypair – – – – – choose two distinct prime numbers p,q compute n = p·q compute φ(n) = φ(p)·φ(q) = (p-1)·(q-1) choose an integer e (1<e<φ(n); GCD(e,φ(n)) = 1) determine an integer d such that d·e 1 (mod φ(n)) • The public key is the pair (n,e) • The private key is the pair (n,d) • It’s impossible to determine one key from another without knowing p,q • Try to – count 13*37 – factorize 527 Steganography RSA enciphering and deciphering • Enciphering – c = me mod n • Deciphering – m = cd mod n • Proof of correctness – cd (me)d me·d (mod n) – Because e·d 1 (mod p-1) and e·d 1 (mod q1) – Then e·d m (mod p-1) and e·d m (mod q-1) – Therefore med m1 (mod p·q) ... Euler‘s theorem – And finally cd m (mod n) Steganography Using RSA for Encryption and Digital Signature • Using RSA for encryption – Sender encrypts the message with receiver’s public key (everyone can do this) – Only receiver is able to decrypt the message (s/he is the only one having private key) • Using RSA for digital signature – Author encrypts the message (hash) with his own private key (only he can do this) – Anybody can examine his/her authorship by decrypting the message by author’s public key • Combination (encryption and signature) – Sender encrypts the message both with receiver’s public key and his own private key – Only receiver can decrypt the message and examine authorship Steganography Digital signature scheme Steganography Verification of the Digital Signature Steganography Public key certification I. • Let’s imagine Alice wants to send a secret and signed message to Bob • Eve stands between them and controls the whole communication • Eve substitutes Alice’s public key with hers – Bob has Eve’s public key considering it as Alice’s • Eve substitutes Bob’s public key with her (another) key – Alice has Eve’s public key considering it as Bob’s • Neither Alice nor Bob know the real owner of the key • Eve can then control and change the whole communication considered to be secret. Steganography Public key certification II. • Solution: Public key certification • Certification authority (CA) verifies key owner’s identity • Certification = digitally signed message saying “This key belongs to Alice” • We need to trust the certification authority • CAs are certified by the government • CAs watch their confidentiality because of business Steganography Bypassing cryptography • Cryptanalysis stands behind cryptography • “Unbreakable” ciphers are known – Meant unbreakable in reasonable time • Electromagnetic tapping – Messages are captured before encryption – Tapping can be shielded; In USA special permission from FBI is required • Viruses, Trojan horses Steganography Steganography • Hiding the existence of the message • Hiding messages to almost all file types is possible – Images, Music, Video, Executables, Text, … Steganography Sources • Literature – Simon Singh: The Code Book – David Kahn: The Codebreakers – Serge Vaudenay: A Classical Introduction to Cryptography: Applications for Communications Security • Internet – computer.howstuffworks.com/computer-internetsecurity-channel.htm – en.wikipedia.org/wiki/Category:Computer_security – www.stegoarchive.com – Google Steganography The end • Thank you for your attention • Questions?