Session 10 2012
advertisement
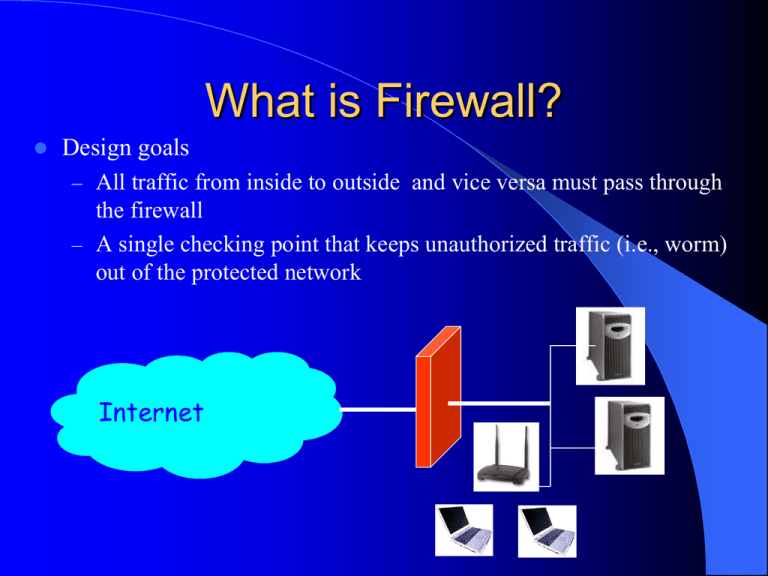
What is Firewall? Design goals – All traffic from inside to outside and vice versa must pass through the firewall – A single checking point that keeps unauthorized traffic (i.e., worm) out of the protected network Internet How it functions? Technique – Control access via security policy Types – Packet filter router – Application-level gateway – Stateful filter vs. stateless filter – Personal firewall Packet-Filtering Router Packet-Filtering Router – – – Applies a set of rules to each incoming IP packet Decides forwarding or discarding the packet Only examine the header, do not “see inside” a packet Pros & Cons – – Simple No application-specific protection HTTP Telnet Internet 129.10.10.1 209.10.10.1 Packet-Filtering Router Filtering rules – Src/dest IP address; src/dest port; protocol field; etc. – Default Discard vs. forward action Internal host address Internal port External host address External port function block * * 192.10.*.* * Block all packets from 192.10.*.* action Internal host address Internal port External host address External port function allow 129.10.10.3 25 * * Allow inbound mail to 129.10.10.3 Packet-Filtering Router The dangerous services – – – – – finger (port 79) telnet (port 23) ftp (port 21) rlogin (port 513) ICMP finger Telnet Internet ftp rlogin Stateful Inspection Firewall Stateful Inspection Firewall – Maintains state information from one packet to another in the input stream – Tightens up the rules for TCP traffic Source address Source port Destination address Destination port State 192.10.10.16 3321 216.10.18.123 80 established Application-level gateway Application level proxy/gateway – – – – Relay of application traffic Run pseudoapplications Looks to the inside as if it is the outside connection Looks to the outside as if it is the inside Pros & Cons – – Processing overhead Diverse functionality HTTP Internet SMTP FTP TELNET Deployment Considerations – Performance – Security of firewall itself – Runs on minimized OS non-firewall functions should not be done on the same machine Network Topology HTTP SMTP Internet FTP TELNET Packet filter Application gateway Personal Firewall Personal Firewall – An application that runs on a personal computer to block unwanted traffic Product – ZoneAlarm www.zonelabs.com – BlackICE Defender blackice.iss.net – Tiny Personal Firewall www.tinysoftware.com – Norton Personal Firewall www.symantec.com – Windows Benefit & Limitation Benefit – Provides a location for monitoring security- related events – Provides a platform for security-related functions: NAT, IPSec Limitations – – – – Attacks that bypass firewall Internal threats Performance Usability vs. security Intrusion Detection System Background What is Intrusion – An intrusion can be defined as any set of actions that attempt to compromise the integrity, confidentiality or availability of a resource. [Heady R. 1990] Three classes of intruder Masquerader – illegitimate user penetrates the system using a legitimate user’s account Misfeasor – legitimate user misuses his/her privileges, accessing resources that is not authorized Clandestine user -- privileged suppress audit control user uses supervisory control to Background What is Intrusion Detection System – An Intrusion Detection System (IDS) must identify, preferably in real time, unauthorized use, misuse and abuse of computer systems – It is a reactive, rather than proactive, form of system defense. Classification – Misuse intrusion detection vs. Anomaly intrusion detection Misuse intrusion detection -- detect attacks on known weak points of a system. Anomaly intrusion detection -- detect by building up a profile of the system being monitored and detecting significant deviations from this profile. – Host-based detection vs. Network-based detection History Conventional approach to system security: Authentication, Access control and Authorization. In 1980, James Anderson first proposed that audit trails should be used to monitor threats. In 1987, Dorothy Denning presented an abstract model of an Intrusion Detection System. In 1988, IDES (Intrusion Detection Expert System) – host-based IDS is developed. In 1990, Network Security Monitor is developed – network-based IDS is developed. In 1994, Mark Crosbie and Gene Spafford suggested the use of autonomous agents in order to improve the scalability, maintainability, efficiency and fault tolerance of an IDS. Structure of IDS Alerting System Data collection Agent Manager Classifier Agent Agent Agent I II III Agent IV Data reduction Data collection System Call Audit Files system Data reduction system Classifier Alerting system Data Collection and Reduction Data source – Audit files system audit files: messages,xferlog,syslog,sulog, .bash_ history... application audit files: Web server log files,…. – System Call Audit record [Denning 87] – Subject, Action, Object, Exception, Resource usage, Time stamp – User operation elementary actions COPY GAME.EXE to /usr/GAME.EXE Smith exec COPY.EXE 0 CPU = 00002 1058721678 Smith read GAME.EXE 0 RECORDS = 1 1058721679 Smith exec COPY.EXE Write-viol RECORDS = 0 1058721680 Misuse intrusion detection Misuse intrusion detection – Use patterns of well-known attacks or weak spots of the system to match and identify intrusions – Perform pattern matching – Used in the environment where a rule can be recognized. Example Misuse Intrusion Detection (Purdue) using Patten Matching Port scan Password guessing Anomaly Intrusion Detection Anomaly Intrusion Detection – Establish normal usage profiles – Observe deviation from the normal usage patterns – Example profiles: loginfrequency, locationfrequency, UseofCPU,UseofIO, ExecutionFrequencyFileReadFails、FileWriteFails Metrics – – – – Mean and standard deviation Multivariate Markov process Time Series Approaches – Data Mining Approaches – Neural Networks – Colored-petri-net Distributed IDS Honey Pot • Honeypots are closely monitored network decoys • Distract adversaries from more valuable machines on a network • Provide early warning about new attack and exploitation trends • Example • Honeypot can simulate one or more network services that you designate on your computer's ports. Product http://www.snort.org/ – http://www.dshield.org/ – – A distributed intrusion detection system, or a distributed firewall system. an attempt to collect data about cracker activity from all over the internet. This data will be cataloged and summarized. It can be used to discover trends in activity and prepare better firewall rules. Right now, the system is tailored to simple packet filters. As firewall systems that produce easy to parse packet filter logs are now available for most operating systems, this data can be submitted and used without much effort. NFR Security Inc. – Snort® is an open source network intrusion prevention and detection system utilizing a rule-driven language, which combines the benefits of signature, protocol and anomaly based inspection methods. NFR Security provides a comprehensive, integrated intrusion detection system that protects networks and hosts from known/unknown attacks, misuse, abuse and anomalies. http://www.nfr.com Real Secure by ISS http://www.iss.net/products_services/enterprise_protection/ Outline Introduction A Frame for Intrusion Detection System Intrusion Detection Techniques Ideas for Improving Intrusion Detection What is the Intrusion Detection Intrusions are the activities that violate the security policy of system. Intrusion Detection is the process used to identify intrusions. Types of Intrusion Detection System(1) Based on the sources of the audit information used by each IDS, the IDSs may be classified into – Host-base IDSs – Distributed IDSs – Network-based IDSs Types of Intrusion Detection System(2) Host-based IDSs – Get audit data from host audit trails. – Detect attacks against a single host Distributed IDSs – Gather audit data from multiple host and possibly the network that connects the hosts – Detect attacks involving multiple hosts Network-Based IDSs – Use network traffic as the audit data source, relieving the burden on the hosts that usually provide normal computing services – Detect attacks from network. Intrusion Detection Techniques Misuse detection – Catch the intrusions in terms of the characteristics of known attacks or system vulnerabilities. Anomaly detection – Detect any action that significantly deviates from the normal behavior. Misuse Detection Based on known attack actions. Feature extract from known intrusions Integrate the Human knowledge. The rules are pre-defined Disadvantage: – Cannot detect novel or unknown attacks Misuse Detection Methods & System Method Rule-based Languages State Transition Analysis Colored Petri Automata Expert System Case Based reasoning Anomaly Detection Based on the normal behavior of a subject. Sometime assume the training audit data does not include intrusion data. Any action that significantly deviates from the normal behavior is considered intrusion. Anomaly Detection Methods & System Method Statistical method Machine Learning techniques Time-Based inductive Machine Instance Based Learning Neural Network … Data mining approaches Anomaly Detection Disadvantages Based on audit data collected over a period of normal operation. – When a noise(intrusion) data in the training data, it will make a mis-classification. How to decide the features to be used. The features are usually decided by domain experts. It may be not completely. Misuse Detection vs. Anomaly Detection Advantage Disadvantage Misuse Detection Accurately and generate much fewer false alarm Cannot detect novel or unknown attacks Anomaly Detection Is able to detect unknown attacks based on audit High false-alarm and limited by training data. The Frame for Intrusion Detection Intrusion Detection Approaches 1. 2. 3. Define and extract the features of behavior in system Define and extract the Rules of Intrusion Apply the rules to detect the intrusion Audit Data 3 Training Audit Data 1 2 Features 3 Rules Pattern matching or Classification Thinking about The Intrusion Detection System Intrusion Detection system is a pattern discover and pattern recognition system. The Pattern (Rule) is the most important part in the Intrusion Detection System – – – Pattern(Rule) Expression Pattern(Rule) Discover Pattern Matching & Pattern Recognition. Machine Learning & Data mining & Statistics methods Traning Audit Data Feature Extraction Training Data & Knowled ge Pattern Extraction Expert Knowledge & Rule collection & Rule abstraction Pattern & Decision Rule Pattern Matching Alarms Intrusion Detection System Discriminate function Pass Pattern Recognition Real-Time Aduit data Rule Discover Method Expert System Measure Based method – Statistical method – Information-Theoretic Measures – Outlier analysis Discovery Association Rules Classification Cluster Pattern Matching & Pattern Recognition Methods Pattern Matching State Transition & Automata Analysis Case Based reasoning Expert System Measure Based method – Statistical method – Information-Theoretic Measures – Outlier analysis Association Pattern Machine Learning method Intrusion Detection Techniques Intrusion Detection Techniques Pattern Matching Measure Based method Data Mining method Machine Learning Method Association Pattern Discover Goal is to derive multi-feature (attribute) correlations from a set of records. An expression of an association pattern: The Pattern Discover Algorithm: Apriori Algorithm 2. FP(frequent pattern)-Tree 1. Association Pattern Detecting Statistics Approaches – Constructing temporal statistical features from discovered pattern. – Using measure-based method to detect intrusion Machine Learning Method Time-Based Inductive Machine – Like Bayes Network, use the probability and a direct graph to predict the next event Instance Based Learning – Define a distance to measure the similarity between feature vectors Neural Network Classification This is supervised learning. The class will be predetermined in training phase. Define the character of classes in training phase. A common approach in pattern recognition system Clustering This is unsupervised learning. There are not predetermined classes in data. Given a set of measurement, the aim is that establishes the class or group in the data. It will output the character of each class or group. In the detection phase, this method will get more time cost (O(n2)). I suggest this method only use in pattern discover phase Association Pattern Detecting Using the pattern matching algorithm to match the pattern in sequent data for detecting intrusion. No necessary to construct the measure. But its time cost depends on the number of association patterns. Constructs a pattern tree to improve the pattern matching time cost to linear time Discover Pattern from Rules The existing rules are the knowledge from experts knowledge or other system. The different methods will measure different aspects of intrusions. Combine these rules may find other new patterns of unknown attack. For example: – Snort has a set of rule which come from different people. The rules may have different aspects of intrusions. – We can use the data mining or machine learning method to discover the pattern from these rule. Machine Learning & Data mining & Statistics methods Traning Audit Data Feature Extraction Training Data & Knowled ge Pattern Extraction Expert Knowledge & Rule collection & Rule abstraction Pattern & Decision Rule Pattern Matching Alarms Intrusion Detection System Discriminate function Pass Pattern Recognition Real-Time Aduit data Penetration Testing 1. Define target and requirements. 2. Obtain a trusted agent. 3. Prepare test plan. 4. Obtain management signoff. 5. Confirm target addresses. 6. Port scanning Penetration Testing 7. Enumeration of web interfaces. 8. Initial vulnerability assessment using port scanner. 9. Verification scanned results. 10. Exploit vulnerabilities. 11. Password cracking. 12. Profile the target system. Penetration Testing 13. Try to find valuable info in hidden fields of html, xml, forms, applets and dynamically generated pages. 14. Try to attack application servers. 15. Glean info from banners, welcome messages and help screens. Penetration Testing 16. Glean info from cookies and session IDs. 17. Try to determine login access controls. 18. Try to spoof IDs and replay passwords. 19. Try to decompile code. 20. Try to view the password rules. 21. Locate and try to attack the DNS.