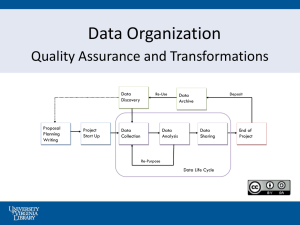
Accuracy-Aware Program Transformations
advertisement

Accuracy-Aware
Program Transformations
Sasa Misailovic
MIT CSAIL
Collaborators
Martin Rinard, Michael Carbin,
Stelios Sidiroglou, Henry Hoffmann,
Deokhwan Kim, Fan Long, Daniel Roy,
Zeyuan Allen Zhu, Michael Kling,
Jonathan Kelner, Anant Agarwal
Trade Accuracy
for Energy and Performance
[Rinard ICS’06, OOPSLA’07; Misailovic, Sidiroglou, Hoffmann, Rinard ICSE’10; Carbin, Rinard, ISSTA’10; Hoffmann, Sidiroglou,
Carbin, Misailovic, Agarwal, Rinard ASPLOS’11; Sidiroglou, Misailovic, Hoffmann, Rinard FSE’11; Misailovic, Roy, Rinard, SAS‘11;
Zhu, Misailovic, Kelner, Rinard POPL’12; Carbin, Kim, Misailovic, Rinard PLDI’12; Misailovic, Sidiroglou, Rinard, RACES‘12;
Misailovic, Kim, Rinard TECS PEC’13; Carbin, Kim, Misailovic, Rinard PEPM’13; Carbin, Misailovic, Rinard, OOPSLA ‘13; …]
Harness Approximate Computing
How to systematically generate
approximate programs? Automated Transformations
How to predict accuracy of the results of
approximate programs? Probabilistic Reasoning
How to find the most profitable
approximate programs? Explicit Search and
Mathematical Optimization
Transformations
Do less work
• Loop perforation
for (i = 0; i < n; i += 2) { … }
• Sampling, Task skipping
Do different kind of work
• Randomized substitution r = f_0(x) 𝒑 f_1(x);
Exploit Execution Environment
r = var +. 2;
• Unreliable operation placement
• Unreliable memory regions, Lock elision
Where and when should we
apply the transformations?
What are the benefits and costs?
for (i = 0; i < n; i++) { … }
for (i = 0; i < n; i += 2) { … }
Optimization Framework
• Find Candidates
for Transformation
• Analyze Effects of the
Transformations
• Navigate Tradeoff Space
c
cc
[Misailovic, Sidiroglou, Hoffmann, Rinard ICSE’10; Hoffmann, Sidiroglou, Carbin, Misailovic,
Agarwal, Rinard ASPLOS’11; Sidiroglou, Misailovic, Hoffmann, Rinard FSE’11]
Explicit Search Algorithm for Perforation
Find Transformation Candidates:
• Profile program to find time-consuming for loops
Analyze the Effects of Transformation:
• Performance: Compare execution times
• Accuracy: Compare the quality of the results
• Safety: memory safety, well formed output
Navigate Tradeoff Space:
• Combine multiple perforatable loops
Prioritize loops by their individual performance and accuracy
Greedy or Exhaustive Search with Pruning
Mean Normalized Time
x264 Cumulative Loop Scores
Accuracy loss (%)
Computational Kernels:
Several perforatable computations
execute for the majority of the time
# Perforatable
Loops
% Time
X264
14
> 60%
Bodytrack
8
> 75%
Swaptions
4
> 99%
Ferret
2
> 40%
Blackscholes
1
> 98%
Canneal
1
> 5%
Streamcluster
1
> 98%
Benchmark
Computational
patterns:
• Distance metrics
• Data Statistics
• Iteration steps
• Monte-Carlo
Next Step: Analyses with Guarantees
Accuracy analysis: Results valid for a whole
range of inputs, not just those used in testing
Navigation: Explore the space of transformed
programs to find those with optimal tradeoffs
Accuracy Analysis:
Probabilistic Reasoning
For approximate program configuration 𝐪
𝐏𝐫 𝐑𝐞𝐬 − 𝐑𝐞𝐬′ (𝐪) > 𝐁 < 𝜺
[Misailovic, Roy, Rinard SAS ’11; Zhu, Misailovic, Kelner, Rinard POPL ’12;
Misailovic, Sidiroglou, Rinard, RACES ‘12, Misailovic, Kim, Rinard TECS PEC ’13,
Carbin, Misailovic, Rinard, OOPSLA ’13, Misailovic, Rinard WACAS ‘14,
Misailovic, Carbin, Achour, Qi, Rinard MIT-TR ‘14]
[Zhu, Misailovic, Kelner, Rinard POPL 2012; Misailovic, Rinard WACAS 2014]
Optimization of Map-Fold Computations
outList = Map (
Func(x),
inputList
)
Accuracy Requirement:
∀𝑜 ∈ outList
𝐏𝐫 𝐨 − 𝐨′ > 𝐁 < 𝜹
Func0: (0,T0)
Func1: (1,T1)
Func2: (2,T2)
[Zhu, Misailovic, Kelner, Rinard POPL 2012; Misailovic, Rinard WACAS 2014]
Optimization of Map-Fold Computations
Func0: (0,T0)
Func1: (1,T1)
Func2: (2,T2)
Configuration: 𝑝0 , 𝑝1 , 𝑝2
Probability to execute each version of Func
Range: 𝑝𝑖 ∈ 0,1 ,
Sum:
𝑝0 + 𝑝1 + 𝑝2 = 1
outList = Map(
Func0(x)
Func1(x)
𝒑𝟎
𝒑′𝟏
Func2(x) ,
inputList
)
Accuracy Loss Constraint:
𝑝0 Δ𝑓0 + 𝑝1 Δ𝑓1 + 𝑝2 Δ𝑓2 ≤ 𝐵𝜀
Goal:
𝐦𝐢𝐧 𝑝0 𝑇𝑓0 + 𝑝1 𝑇𝑓1 + 𝑝2 𝑇𝑓2
Linear + Dynamic programming
[Misailovic, Carbin, Achour, Qi, Rinard MIT-TR 14]
Chisel: Automatic Generation of
Approximate Rely Programs
Developer’s reliability
specification
float<0.99*R(x)>
f(float in unrel x) {
y = g(x) +. h(x);
return y *. y;
}
Variable and
Operation
Annotations
[Misailovic, Carbin, Achour, Qi, Rinard MIT-TR 14]
Chisel: Automatic Generation of
Approximate Rely Programs
Developer’s
specification
float<0.99*R(x)>
f(float x ) {
ℓ𝟎
y = g(x) +
return y *
}
ℓ𝟏
ℓ𝟐
Configuration: ℓ0 , ℓ1 , ℓ2
Unreliable variable or unreliable operation
Range: ℓ𝑖 ∈ 0,1
h(x);
Reliability Constraint:
ℓ0 log 𝑟𝑥 + ℓ1 log 𝑟+ + ℓ2 log 𝑟∗ ≥ log 0.99
y;
Goal:
𝐦𝐚𝐱 ℓ0 𝐸𝑥 + ℓ1 𝐸+ + ℓ2 𝐸∗
Integer Linear Programming
Navigate Search Space:
Mathematical Optimization
Find configuration 𝐪 = (𝐪𝟏 , … , 𝐪𝐤 )
𝐦𝐚𝐱 Performance(𝐪)
𝒒
s. t. 𝐏𝐫 Res − Res ′ (𝐪) > 𝐁 < 𝜺
[Zhu, Misailovic, Kelner, Rinard POPL ’12; Misailovic, Rinard WACAS ‘14
Misailovic, Carbin, Achour, Qi, Rinard, MIT-TR ‘14]
Looking Forward
Fully Exploit Optimization Opportunities:
both application- and hardware-level transformations
Reasoning About Uncertainty:
• logic-based techniques
• probabilistic techniques
• empirical techniques
Practical Aspects: provide intuition and control
for developers and domain experts
Takeaway
Accuracy-aware transformations
• Improve performance
• Reduce energy consumption
• Facilitate dynamic adaptation
and software specialization
Program analysis and search
can help find profitable, safe,
and predictable tradeoffs
Takeaway
Accuracy-aware transformations
• Improve performance
• Reduce energy consumption
• Facilitate dynamic adaptation
and software specialization
Program analysis and search
can help find profitable, safe,
and predictable tradeoffs