Document
advertisement

An Efficient Key-Management Scheme for
Hierarchical Access Control Based on
Elliptic Curve Cryptosystem
Author: F.G. Jeng and C.M. Wang
Citation: Journal of Systems and Software
1
Outline
Introduction
Elliptic Curve Cryptosystem
Proposed Scheme
Analysis of Security
Analysis of Time Complexity
Analysis of Storage Complexity
Conclusion
Idea
2
Introduction
Hierarchical access control
President
problems :
access rights among a group of
Office of
Academic Affairs
Office of
Student Affairs
Office of
General Affairs
users in an organization
higher level user can access
lower level user’s data
Teachers
Students
Library
lower level user can not access
higher level user’s data
3
Introduction
Two Types of Hierarchies
Tree hierarchy
Each class (except root class) has only one parent class.
Partially ordered hierarchy
Each class (except root class) could have more than
one parent class.
4
Introduction
Tree hierarchy
C
The users are divided into a set of disjoint
1
C
C
C
2
security classes C = {C1, C2, …, Cn}.
4
3
C
C
C
C
5
6
7
8
A tree hierarchy
Ci
Cj
Each class has its own cryptographic key.
Each class (except root class) has only one
parent class.
Cj ≤ Ci : Ci can read or store information in
Cj, but the opposite is not allowed.
Ci can derive the key of Cj.
5
Introduction
Partially ordered hierarchy
C1
The users are divided into a set of disjoint
C2
C3
C4
security classes C = {C1, C2, …, Cn}.
Each class has its own cryptographic key.
C5
C6
C7
A partially ordered hierarchy
Ci
Each class (except root class) could have
more than one parent classes.
Cj ≤ Ci : Ci can read or store information
in Cj, but the opposite is not allowed
Ci can derive the key of Cj.
Ci
6
Introduction
Types of public-key cryptosystem
Integer Factorization System
n = pq, where p and q are two primes.
It’s hard to factorize n.
Discrete Logarithm System
rx ≡ h (mod p)
It’s hard to find x.
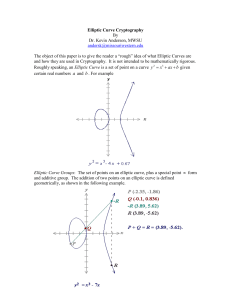
Elliptic Curve Cryptosystem
Q = aP, where P and Q are two points over an elliptic curve.
It’s hard to find a.
7
Introduction
Goals of a Key-Management Scheme
The scheme should be secure.
The key-derivation process should be efficient.
The scheme should have the dynamic access property .
The scheme should require low-cost computation overhead
and less storage.
The scheme should be flexible on selection of user’s own
secret key.
8
Elliptic Curve Cryptosystem
Advantages of ECC (Elliptic Curve Cryptosystem)
ECC provides greater efficiency roughly 10 times than
either integer factorization systems or discrete logarithm
systems in terms of computational overheads, key sizes and
bandwidth.
a key size of 4096 bits for RSA gives the same level of
security as 313 bits in an ECC
9
Elliptic Curve Cryptosystem
Mathematics Backgrounds on the ECC
Elliptic curve equation E over Zp
Zp = {0, 1, 2, …, p-1}
Ep(a, b) : y2=x3+ax+b (mod p),
where a and b Zp, and
4a3+27b2 0
A finite abelian group, which defined
y2 = x3 + x+ 1
over Ep(a, b)
10
Elliptic Curve Cryptosystem
(0, 1)
(6, 4)
(12,19)
(0, 22)
(6, 19)
(13, 7)
Mathematics Backgrounds of ECC
(1, 7)
(7, 11)
(13,16)
Operations of points in the ECC
(1, 16)
(7, 12)
(17,3)
(3, 10)
(9, 7)
(17,20)
(3, 13)
(9, 16)
(18,3)
(4, 0)
(11, 3)
(18,20)
(5, 4)
(11,20)
(19,5)
(5, 19)
(12, 4)
(19,18)
If P = (xp, yp), then P + (xp, –yp) = O.
The point (xp, –yp) is the negative of
P, denoted as –P.
Example
Let P = (6, 4), then, –P = (6, –4).
Since –4 mod 23 19, –P = (6, 19)
over E23(1, 1).
Points over E23(1, 1)
11
Elliptic Curve Cryptosystem
(0, 1)
(6, 4)
(12,19)
Mathematics Backgrounds of ECC
(0, 22)
(6, 19)
(13, 7)
Multiplication by an integer is
(1, 7)
(7, 11)
(13,16)
(1, 16)
(7, 12)
(17,3)
(3, 10)
(9, 7)
(17,20)
(3, 13)
(9, 16)
(18,3)
(4, 0)
(11, 3)
(18,20)
(5, 4)
(11,20)
(19,5)
(5, 19)
(12, 4)
(19,18)
Points over E23(1, 1)
defined by repeated addition; for
example, 2P = P + P .
xr = (2 xp xq) mod p
yr = ( (xp xr) yp) mod p
y q y p
x q x p
2
3x p a
2 y
p
mod
p , if P Q
mod
p , if P Q
Example
P = (6, 4); λ=5, xr=13, yr=7, 2P
= (13, 7) over E23(1, 1)
12
Elliptic Curve Cryptosystem
Mathematics Backgrounds on ECC
(0, 1)
(6, 4)
(12,19)
(0, 22)
(6, 19)
(13, 7)
(1, 7)
(7, 11)
(13,16)
(1, 16)
(7, 12)
(17,3)
(3, 10)
(9, 7)
(17,20)
xr = (2 xp xq) mod p
(3, 13)
(9, 16)
(18,3)
yr = ( (xp xr) yp) mod p,
(4, 0)
(11, 3)
(18,20)
(5, 4)
(11,20)
(19,5)
(5, 19)
(12, 4)
(19,18)
Addition operation of two different
points over Ep(a, b).
If P = (xp, yp) and Q = (xq, yq) in which
P Q, then R = P + Q = (xr, yr).
Example
P = (6, 4), Q = (7, 11), λ=7, xr=13,
yr=16, R = P + Q = (13, 16) over
E23(1, 1).
Points over E23(1, 1)
13
Elliptic Curve Cryptosystem
Comparison:ECC vs. RSA
Elliptic curve logarithms using the
Pollard rho method
Integer factorization using the general
number field sieve
Key size
MIPS-Years
Key size
MIPS-Years
150
3.8 x 1010
512
3 x 104
205
7.1 x 1018
768
2 x 108
234
1.6 x 1028
1024
3 x 1011
1280
1 x 1014
1536
3 x 1016
2048
3 x 1020
160
14
Proposed Scheme
Key-management Scheme for Tree Hierarchy
Mathematics background
A function H: A→ B is a one-way hash function, it is a one-
to-one function and implies that
For every x in A, H(x) can be computed easily;
For every y = H(x) in B, it is infeasible to compute x
15
Proposed Scheme
Key Generation Algorithm
Step 1
CA determines Ep (a, b) : y2 = x3 + ax + b (mod p)
p is a large prime number
4a3 + 27b2 ≠ 0 mod p.
CA picks a base point G = (x, y) with the order n such
that nG = O.
CA publishes Ep(a, b), G and n.
16
Proposed Scheme
Key Generation Algorithm
Step 2
CA selects Ã: (x, y) → v, v is an integer number.
The CA makes à public.
CA chooses a secret parameter nca and makes Pca public,
where Pca = ncaG.
Private parameter of the CA : nca
Public parameter of the CA : point Pca
17
Proposed Scheme
Key Generation Algorithm
Step 3
Class Ci chooses secret key Ki, 1 ≤ Ki ≤ p-1
Class Ci chooses secret parameter ni. ni ≤ n
Pi = niG is public
Ci sends (Ki, ni) to CA secretly
Private parameters of Ci :Ki , ni
Public parameter of Ci : point Pi = niG
18
Proposed Scheme
Key Generation Algorithm
Step 4
CA constructs a polynomial Hi(x) for Ci.
C1
For the root class, H(x) = nil.
C2
C3
C4
H1(x) = nil
For non-root class,
C5
C6
C7
Hi(x) =
~
( x A ( n i Pt )) K i ,
where Ci ≤ Ct.
t
19
Proposed Scheme
Key Generation Algorithm
Example
H2(x)=(x - Ã(n2P1)) + K2
H3(x) =(x - Ã(n3P1)) + K3
C
C
1
1
C
C
C
2
3
4
C
C
C
5
6
7
C
C
C
2
3
4
C
C
C
5
6
7
20
Proposed Scheme
Key Generation Algorithm
Example
H4(x) = (x - Ã(n4P1)) + K4 H5(x) =(x - Ã(n5P1)) (x - Ã(n5P2)) + K5
C
C
1
1
C
C
C
C
C
C
2
3
4
2
3
4
C
C
C
C
C
C
5
6
7
5
6
7
21
Proposed Scheme
Key Generation Algorithm
Example
H6(x) =(x - Ã(n6P1)) (x - Ã(n6P2)) (x - Ã(n6P3)) (x - Ã(n6P4))
+ K6
H7(x) =(x - Ã(n7P1)) (x - Ã(n7P4)) + K7.
C
C
1
1
C
C
C
2
3
4
C
C
C
5
6
7
C
C
C
2
3
4
C
C
C
5
6
7
22
Proposed Scheme
Key Derivation Algorithm
Step 1.
Ci derives the key of Cj.
C
1
C
C
C
2
3
4
Ci gets the public polynomial Hj(x) and Pj.
Example
C
C
C
5
6
7
C1 derives the key of C6.
C1 knows : P6 and H6(x)
23
Proposed Scheme
Key Derivation Algorithm
Step 2.
Ci Computes Hj(Ã(niPj))
Ci obtains Kj
C1
H6(x) =(x - Ã(n6P1)) (x - Ã(n6P2)) (x - Ã(n6P3))
C2
C3
(x - Ã(n6P4)) + K6
Example
C4
H6(Ã(n1P6))
C5
C6
C7
= (Ã(n1P6) - Ã(n6P1))(Ã(n1P6) - Ã(n6P2)) (Ã(n1P6)
- Ã(n6P3)) (Ã(n1P6) - Ã(n6P4)) + K6
= (Ã(n1 n6G) - Ã(n6 × n1G))(……) + K6
= K6
||
0
24
Proposed Scheme
Problems of Dynamic Access Control
Addition of a new security class
Deletion of a security class
25
Proposed Scheme
C
Addition of a new security class
1
C
C
C
2
3
4
Class C8 is added to the hierarchy,
C
C
C
5
6
7
C8 has private parameters (n8, K8)
and public parameter P8 = n8G.
The CA constructs H8(x) for C8,
C
1
C
C
C
2
3
4
C
C
C
5
6
7
H8(x) = (x - Ã(n8P1)) (x - Ã(n8P4)) +
K8
C
8
26
Proposed Scheme
C
Deletion of a Security Class
1
C
C
C
2
3
4
C
C
C
5
6
7
Class C3 is removed from
C
8
the hierarchy.
Only, the CA deletes K3, n3,
P3 and H3(x).
C
1
C
C
2
4
C
C
C
5
6
7
C
8
27
Analysis of Security : Conspiracy
C5
C
1
public parameters (P5, H5(x))
C
C
C
2
3
4
private parameters (n5, K5)
C6
C
C
C
5
6
7
C
public parameters (P6, H6(x))
private parameters (n6, K6)
C5, C6 know P2 , H2(x)
1
C
C
C
2
3
4
n2
C
C
C
5
6
7
P2 = n2G
H2(x) = (x - Ã(n2P1)) + K2
H2(Ã(n2P1)) = (Ã(n2P1) - Ã(n2P1)) + K2
hard
28
Analysis of Time Complixity
Constructing Hi(x)
O(m.log2m)
degree m
Updating Hi(x)
O(nm.log2m)
n classes
29
Analysis of Storage Complexity
ni
300 bits
Ki
300 bits
Point Pi
600 bits
Hi(x)
m log
p 1
RSA – 4096 bits
ECC – 313 bits
Pi = (xi, yi)
prime p : 300 bits
degree m
30
Conclusions
The problem of hierarchical access control is discussed and solved.
ECC is more efficient than other cryptosystems.
It is efficient in our key generation and key derivation based on ECC.
The proposed scheme achieves the dynamic access property.
Addition of a new class
Deletion of an old class
The proposed scheme has low computational overhead and less
storage based on ECC.
The proposed scheme is flexible on selection of user’s own secret key.
31
具有優先權概念之
不擴展漸進式視覺密碼
漸進式且具有不同權限等級的不擴展視覺密碼分享
方法
(n, n)-PPSM
(n, n)-priority and progressive sharing model
現行的漸進式視覺密碼的分享機制下,無法根據參
與者的重要性來賦予適當的權限等級
n個機密分享參與者,都擁有不同權限
32
實驗結果與分析討論
圖 5:圖 4 分享影像的重疊結果
左:疊合五張分享影像→ (NC = 0.74)
才能隱約看到機密影像的輪廓
右:疊合三張分享影像→ (NC = 0.72),
即可隱約看到機密影像的輪廓
疊合四張分享影像→ (NC = 0.78),即可
清晰地看到機密影像的內容
該研究的機密分享矩陣確實能給予分享
者不同的機密復原能力
33
實驗結果與分析討論
圖 7:圖 6 所產生的彩色分享影像
權限高→疊合分享影像→較少張→輪廓
權限低→疊合分享影像→較多張→輪廓
圖 5 , 7 實驗結果可發現,機密影
像的還原結果是根據參與者的權限
等級高低
34
感想
A
B
C
D
a
E
b
c
F
d
e
f
35
老師補充
想法:是否可以金鑰可以用群組的概念來作
為分享影像的作法?
36