Firewalls
advertisement

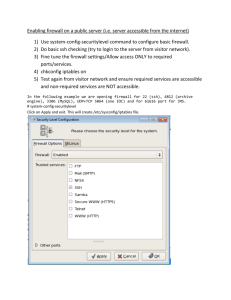
Firewalls What they do. How they work. cs490ns - cotter 1 Outline • What is a firewall? • Architectures – – – – Stand Alone / application / proxy Personal / host based Gateway / packet filters Enterprise / hardware • Roles – Bastion – DMZ • Packet Filtering concepts – IPTables – Stateful filtering • Packet Forwarding • Ethernet bridge cs490ns - cotter 22 What is a Firewall? • A hardware or software device that monitors (and controls ?) the transmission of packets that attempt to pass through the perimeter of a network (or host). • Provide 2 basic security functions – Packet Filtering – Application Proxy gateways • Additional security features – – – – Log unauthorized (and authorized ?) access attempts Provide VPN Connections Support user authentication Shield internal machines from outside view cs490ns - cotter 33 What should a firewall do? • Control the flow of packets to/from Internet • Block external login as root (?) • Must distinguish between local and Internet packets (even spoofed addresses) • Support limited user accounts • Log all system activities cs490ns - cotter 44 Types of Firewalls • • • • • Stand Alone / application / proxy Enterprise / Local Hardware / Software Gateway / router / packet filter Personal / host based – Windows firewall – incoming protection – ZoneAlarm, Linux, etc. – incoming / outgoing filter cs490ns - cotter 55 Types of Firewalls Stateful Firewall Application Proxy cs490ns - cotter Router / packet filter Corporate Network Internet Host-based Firewall 66 Standalone Proxy Firewalls Application Gateways • Intended to buffer the interface between an internal application and the Internet – Web Servers – Mail Servers – File Transfer • Controls flow of packets into and out of local network – Limit access to specific web sites – Cache results for use by other internal hosts – Hide internal IP addresses from network view cs490ns - cotter 77 Enterprise Firewalls • Intended to support larger traffic volumes • Provides more sophisticated support – Stateful filtering, etc. • Software – Checkpoint Firewall 1, Microsoft ISA, Semantic Enterprise, etc. • Hardware – Cisco PIX, SonicWall, Watchguard, etc. • Expensive! cs490ns - cotter 88 Gateway / Packet Filter • May be embedded in sophisticated routers • May be used for SOHO networks – May be incorporated into small SOHO routers – May be incorporated into a gateway host (Linux ?) • Provides the ability to monitor and control packets through the gateway / router. – Generally support in / out / through filtering – May not include stateful filtering capabilities cs490ns - cotter 99 Host-based Firewalls • Intended as a last line of defense for the host computer • Runs as a background process on host – Limited bandwidth available – Generally supports incoming port filtering – Can specify which ports (if any) can support incoming connection requests. – Occasionally supports outgoing filtering (looking for worms, trojans, etc.) cs490ns - cotter 1010 Firewall Roles • Bastion Hosts – Hardened systems that typically run a firewall and perhaps an application as well • DMZ – demilitarized zone – An isolated subnetwork that includes all services that are offered over the internet (and perhaps to the internal network as well). cs490ns - cotter 11 Bastion Firewall and Host LAN Internet Firewall Web Server cs490ns - cotter 12 DMZ LAN Internet DMZ cs490ns - cotter Web E-mail 13 What is Packet Filtering? • The process of deciding which packets to allow through the filter, based on attributes of the packet – – – – – Source / Destination Port Source / Destination IP Address Status flags in the packet (syn) Originating protocol (icmp, tcp, etc.) Connection state (tcp) • Linux (2.4+) supports Netfilter (based on iptables) cs490ns - cotter 1414 How does Packet Filtering Work? • Define rules to allow or block specific types of packets • Firewall screens all packet headers to look for matches against the rules • Apply rules in the order in which they are stored • Allow or block packets based on rule matches. • If a packet matches no rules, apply default behavior to the packet (usually deny). cs490ns - cotter 1515 Packet Filtering Issues • Rules are complex. Easy to introduce errors • Filters based on IP addresses. If authorized sites are hacked, your site is compromised • IP Spoofing can fake authorized (internal?) sites. • Routers can be hacked to reroute internal packets • Activities need to be logged • Internal host adresses should be hidden cs490ns - cotter 1616 Iptables • Administration tool for IPv4 packet filtering and NAT • Used to set up, maintain, and inspect the tables of IP packet filtering rules used by the kernel to manage packet flow through the firewall. • Based on tables that specify the overall task and chains that identify the position of the packet in the packet flow. cs490ns - cotter 1717 IPTables tables • Filter table – Used to control the flow of packets based on packet attributes – Only filter packets, don’t modify packets here. • Network Address Translation (NAT) table – Used to change the source / destination IP address and / or port of selected incoming / outgoing packets • Mangle table – Supports specialized packet handling / routing – Change contents of packet • Experimental and developing tables … cs490ns - cotter 1818 Basic Packet Filtering filter table Input Forward LAN Internet RH-Firewall-1-INPUT Output cs490ns - cotter 1919 Incoming Packets to Filter • Illegal Incoming Source IP Addresses – – – – – • • • • • • • Your IP Address Your LAN Address Private Network Addresses Multicast IP Addresses Loopback Interface Addresses Nuisance sites / networks Remote Source Port Filtering Local Destination Port Filtering Incoming TCP connection-state filtering Probes and Scans DoS Attacks Etc. cs490ns - cotter 2020 Packet Filtering alert list • CERT – www.cert.org – Carnegie-Mellon Software Engrg Inst. – www.us-cert.gov – • Port Filter List (3/08) – – – – – – – – – DNS zone transfers tftpd link RPC / NFS BSD “r” commands lpd uucpd openwindows X windows cs490ns - cotter 53 69 87 111 / 2049 512, 513, 514 515 540 2000 6000 + 2121 Outgoing Packets to Filter • Why? – Consideration for fair use in Internet – Distribution of private information – Detection of unwanted client programs (Trojans, etc.) • See http://www.us-cert.gov/cas/tips/ST06-001.html • What – – – – Legitimate, routable addresses only Destination IP Addresses Destination ports Source Ports cs490ns - cotter 22 Filter TableChains • May be associated with any interface (eth0, etc.) • INPUT – Used to test packets that come into the firewall • OUTPUT – Used to test packets that are leaving the firewall • FORWARD – Used to test packets that are passing through the firewall • Packets should pass through only 1 chain cs490ns - cotter 23 Filter table packet flow Routing Forward Chain Drop Input Chain Drop cs490ns - cotter Local Processes Output Chain Drop 24 Iptables rule structure • Iptables –t “table” “action” “chain” rule “target” – Which table are we working with (filter is default) – What action do we want to do to that table (insert, delete, etc.) – Which chain in that table are we working with – What do we want to do? – Where do we go if we match the rule? cs490ns - cotter 25 IPTables Actions • • • • • • Create a new chain (-N). Delete an empty chain (-X). Change the default policy for a chain. (-P). List the rules in a chain (-L). Flush the rules out of a chain (-F). Zero the packet and byte counters on all rules in a chain (-Z). cs490ns - cotter 26 IPTables Actions • • • • Append a new rule to the end of a chain (-A). Insert a new rule at some position in a chain (-I). Replace a rule at some position in a chain (-R). Delete a rule at some position in a chain, or the first that matches (-D). cs490ns - cotter 27 IPTables targets • ACCEPT – Stop processing and pass to application / OS • DROP – Stop processing and block packet • LOG – Packet info sent to syslog. Continue processing • REJECT – Stop processing and send reject message to source • DNAT – Change destination network address • SNAT – Change source network address • MASQUERADE – Do source network address translation (PAT) cs490ns - cotter 28 Example Filter Rules • • • • • • • #Allow traffic on the loopback interface iptables –A INPUT –i lo –j ACCEPT iptables –A OUTPUT –i lo –j ACCEPT # Set Default policy for chain Iptables --policy INPUT DROP #Allow all outgoing connections iptables -A block -m state --state NEW -i ! ppp0 \ -j ACCEPT • #Block incoming attempts to Xwindows • iptables –A INPUT –i eth1 -p tcp --syn \ --destination-port 6000-6003 -j REJECT cs490ns - cotter 29 Example Filter Rules #Allow incoming connections to local web server Iptables –t filter -A block –p tcp --dport 80 --i eth1 \ -j ACCEPT #Insert a rule that allows incoming udp packets to port 12345 iptables –I block 7 –p udp –dport 12345 –j ACCEPT #Allow DNS requests NOT from outside iptables -A block –p tcp --dport 53 -m state --state NEW \ -i ! eth1 -j ACCEPT #Allow (and redirect) incoming web connections to 192.168.5.6 iptables –t nat –A PREROUTING –d eth1 -p tcp \ --dport 80 -j DNAT --to-destination 192.168.5.6 cs490ns - cotter 30 Simple Firewall table ## Insert connection-tracking modules (not needed if built into kernel). insmod ip_conntrack insmod ip_conntrack_ftp ## Make chain that blocks new connections, except if coming from LAN. iptables -N block iptables -A block -m state --state ESTABLISHED,RELATED -j ACCEPT iptables -A block -m state --state NEW -i ! ppp0 -j ACCEPT iptables -A block -j DROP ## Jump to that chain from INPUT and FORWARD chains. iptables -A INPUT -j block iptables -A FORWARD -j block cs490ns - cotter 31 Iptables default config file /etc/sysconfig/iptables # Firewall configuration written by system-config-securitylevel # Manual customization of this file is not recommended. *filter :INPUT ACCEPT [0:0] :FORWARD ACCEPT [0:0] :OUTPUT ACCEPT [0:0] :RH-Firewall-1-INPUT - [0:0] -A INPUT -j RH-Firewall-1-INPUT -A FORWARD -j RH-Firewall-1-INPUT -A RH-Firewall-1-INPUT -i lo -j ACCEPT -A RH-Firewall-1-INPUT -p icmp --icmp-type any -j ACCEPT -A RH-Firewall-1-INPUT -p 50 -j ACCEPT -A RH-Firewall-1-INPUT -p 51 -j ACCEPT -A RH-Firewall-1-INPUT -p udp --dport 5353 -d 224.0.0.251 -j ACCEPT -A RH-Firewall-1-INPUT -p udp -m udp --dport 631 -j ACCEPT -A RH-Firewall-1-INPUT -p tcp -m tcp --dport 631 -j ACCEPT -A RH-Firewall-1-INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT -A RH-Firewall-1-INPUT -m state --state NEW -m tcp -p tcp --dport 22 -j ACCEPT -A RH-Firewall-1-INPUT -j REJECT --reject-with icmp-host-prohibited COMMIT cs490ns - cotter 32 CentOS 5.5 Firewall – part 1 [rcotter@lserver3 ~]$ sudo iptables -L Chain INPUT (policy ACCEPT) target prot opt source RH-Firewall-1-INPUT all -- anywhere destination anywhere Chain FORWARD (policy ACCEPT) target prot opt source RH-Firewall-1-INPUT all -- anywhere destination anywhere Chain OUTPUT (policy ACCEPT) target prot opt source destination cs490ns - cotter 33 CentOS 5.5 Firewall – part 2 Chain RH-Firewall-1-INPUT (2 references) target prot opt source destination ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 ACCEPT esp -- 0.0.0.0/0 0.0.0.0/0 ACCEPT ah -- 0.0.0.0/0 0.0.0.0/0 ACCEPT udp -- 0.0.0.0/0 224.0.0.251 ACCEPT udp -- 0.0.0.0/0 0.0.0.0/0 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 ACCEPT tcp -- 192.168.1.0/24 0.0.0.0/0 ACCEPT tcp -- 134.193.12.34 0.0.0.0/0 ACCEPT udp -- 0.0.0.0/0 0.0.0.0/0 ACCEPT udp -- 0.0.0.0/0 0.0.0.0/0 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 ACCEPT udp -- 0.0.0.0/0 0.0.0.0/0 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 REJECT all -- 0.0.0.0/0 0.0.0.0/0 cs490ns - cotter icmp type 255 udp dpt:5353 udp dpt:631 tcp dpt:631 state RELATED,ESTABLISHED state NEW tcp dpt:22 state NEW tcp dpt:22 state NEW udp dpt:137 state NEW udp dpt:138 state NEW tcp dpt:139 state NEW tcp dpt:445 state NEW udp dpt:2069 state NEW tcp dpt:3128 state NEW tcp dpt:3306 reject-with icmp-host-prohibited 34 Filter table • Input, forward chains point to custom chain – RH-Firewall-1-INPUT • Output chain set to accept all – (allow any outgoing traffic) • RH-Firewall-1-INPUT chain – – – – Initial 4 rules allow broad classes of packets Allow multicast DNS Allow ipp (Internet Printing protocol) Allow incoming UDP packets to port 12345 • Special server set up for cs423 class – Allow incoming SSH connections – Reject everything else! cs490ns - cotter 35 Network Address Translation • What? – “Translates” IP addresses and / or ports as packet passes through firewall – Only first packet of a connection will traverse the table. All remaining packets are modified the same as the first packet. • Why? – Private local IP Addresses – Multiple Servers (load sharing) – Transparent Proxying cs490ns - cotter 36 NAT table • Used to map local IP addresses to a set of routable addresses (NAT) • Used to map local IP addresses to a set of ports associated with a single routable address (NAPT) • Used to map local IP addresses to a set of ports associated with a variable routable address (masquerade) – Dial-up connection – Dynamically assigned IP address • Other cs490ns - cotter 37 NAT • Two types of NAT – Source NAT (snat) used to translate the source IP address of a packet (typically outgoing) – Destination NAT (dnat) used to translate the destination IP address of a packet (typically incoming). cs490ns - cotter 38 NAT table chains • Pre-routing – Used to test / modify the destination addresses of incoming packets • Output – Used to change the source (or destination) address of locally generated packets • Post-routing – Used to change the source address of outgoing packets. cs490ns - cotter 39 NAT table packet flow Destination NAT Pre-routing Routing Forward Chain Source NAT Post-routing Drop Input Chain Drop cs490ns - cotter Local Processes Output Chain Drop 40 Simple NAT table rules # Masquerade out ppp0 iptables -t nat -A POSTROUTING -o ppp0 -j MASQUERADE # Disallow NEW & INVALID incoming or forwarded packets from ppp0. iptables -A INPUT -i ppp0 -m state --state NEW,INVALID -j DROP iptables -A FORWARD -i ppp0 -m state --state NEW,INVALID -j DROP # Turn on IP forwarding (in RAM) echo 1 > /proc/sys/net/ipv4/ip_forward # Turn on IP forwarding (in file /etc/sysctl.conf) net.ipv4.ip_forward = 1 cs490ns - cotter 41 Mangle table • Used for special routing and packet modification. – Use TOS (type of service) field in IP header. – TTL – Can be used to set and test markers placed cs490ns - cotter 42 Mangle Table Routing Internet AS cs490ns - cotter 43 Linux Firewall Mgmt • iptables – Make changes to memory image of firewall rules • iptables-save – Display a copy of the memory image – Can redirect the copy to a file using output redirection – Iptables-save > /etc/sysconfig/iptables • iptables-restore – Rebuild memory image from keyboard or file (using redirection) • Security Level and Firewall Applet (Fedora) – Creates an automatic backup file: /etc/sysconfig/iptables cs490ns - cotter 44 IPTables Constraints • Based on IP – only – Don’t run IPX, appletalk, etc. as these protocols are not filtered • Packets traversing the filter table will pass through only 1 chain cs490ns - cotter 45 Port Forwarding HTTPD LAN Internet 123.234.56.78:80 192.168.3.6:80 cs490ns - cotter 46 SOHO Router Port Range Forwarding cs490ns - cotter 47 IPTables Port Forwarding • For incoming packets – iptables -t nat -A PREROUTING -p tcp -d <publishedip> --dport <published-port> -j DNAT --to-destination <private-ip>:<private-port> • For returned packets – iptables -m conntrack --ctstate DNAT -t nat -A POSTROUTING -p tcp -d <private-ip> --dport <private-port> -j SNAT --to-source <published-ip> • For packets originating on firewall – iptables -t nat -A OUTPUT -p tcp -d <published-ip> -dport <published-port> -j DNAT --to-destination <private-ip>:<private-port> cs490ns - cotter 48 IPtables rerouting Issues • Often, when we re-route packets, we only need to change destination (or source) IP address. • Sometimes (if we are rerouting to a locally connected destination) we need to change both IP address and MAC address. • IPtables only filters IP traffic. It cannot change IPX, netBEUI, Appletalk, etc. cs490ns - cotter 49 EBtables • Ethernet Bridge tables – Intended to support filtering of packets that IPtables cannot filter – Ethernet protocol, MAC address, ARP, netBEUI, IPX, etc. – Basically adds non–IP filtering. – 802.1Q VLAN filtering – MAC address NAT – Frame counters • Linux bridge-nf code – Passes bridged traffic to IPtables cs490ns - cotter 50 EBtables Structure • broute table – BROUTING chain – Choose whether to process packet at layer 2 (bridge) or at layer 3 (route) – e.g. route normal IP traffic and bridge IPX traffic • filter table – FORWARD, INPUT, OUTPUT chains – Route packets based on MAC addresses • nat table – PREROUTING, OUTPUT, POSTROUTING chains – Change MAC addresses (redirect based on MAC) cs490ns - cotter 51 Ethernet Bridge Firewall LAN Internet Linux box configured as a bridge, with firewall installed cs490ns - cotter 52 Ethernet Bridge Firewall • Use bridging firewall (ebtables) to set up rules to pass packets through host. – Since processing happens at Data Link Layer, there is no need to assign an IP address to host interfaces, so machine is invisible to network scanning. – Offers better protection, and less configuration of the remaining network. – Can also be configured with an IDS. cs490ns - cotter 53 Ethernet Bridge Firewall • Create a virtual Ethernet bridge interface – brctl addbr br0 • Add our interfaces to the bridge – brctl addif br0 eth0 – brctl addif br0 eth1 • Remove the IP configuration from interfaces – – – – Ifconfig eth0 down Ifconfig eth1 down Ifconfig eth0 0.0.0.0 up Ifconfig eth1 0.0.0.0 up • Configure access for the bridge – Local console, OOB network, configure 1 IP cs490ns - cotter 54 Ethernet Bridge Firewall (2) LAN Internet cs490ns - cotter 55 Example Firewall Application • Monitor all outgoing Traffic – Most firewalls only monitor incoming traffic by default • Identify what traffic is desired and block the rest. – Many applications generate queries to their servers – Spyware – Hacks cs490ns - cotter 56 App development process • Capture all outgoing traffic – Monitor traffic as it enters or leaves the network – (Ethernet Bridge) – Use iptables to log traffic. • -A firewall-win1 –j LOG –log-level 4 –log-prefix “Win1” –log-tcp-options –log-ip-options – Set up syslog to divert level 4 messages to a separate file (see syslog.conf) • kern.warning /var/log/iptables.log – Save data daily to separate file • iptables_log_022011 cs490ns - cotter 57 # Generated Manually 8/19/10 *filter :INPUT ACCEPT [0:0] :FORWARD ACCEPT [8183:1429550] :OUTPUT ACCEPT [14722:762210] -N RH-Firewall-1-INPUT # Create separate chains for each host - 8/19/10 -N Firewall-Win2 -N Firewall-Win1 -N Firewall-lserver3 #new line 8/26/10 - start monitoring this machine -N firewall-bridge -A OUTPUT -j firewall-bridge -A INPUT -j RH-Firewall-1-INPUT -A FORWARD --src 192.168.1.25 -j Firewall-lserver3 -A FORWARD --src 192.168.1.35 -j Firewall-Win2 -A FORWARD --src 192.168.1.30 -j Firewall-Win1 -A RH-Firewall-1-INPUT -i lo -j ACCEPT -A RH-Firewall-1-INPUT -p icmp -m icmp --icmp-type any -j ACCEPT -A RH-Firewall-1-INPUT -p esp -j ACCEPT -A RH-Firewall-1-INPUT -p ah -j ACCEPT -A RH-Firewall-1-INPUT -p udp -m udp --dport 631 -j ACCEPT -A RH-Firewall-1-INPUT -p tcp -m tcp --dport 631 -j ACCEPT -A RH-Firewall-1-INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT -A RH-Firewall-1-INPUT -j DROP Primary Firewall Filter Table cs490ns - cotter 58 -A Firewall-Win1 --dst 192.168.1.0/24 -j ACCEPT -A Firewall-Win1 -p icmp -m icmp --icmp-type any -j ACCEPT -A Firewall-Win1 --dst 134.193.123.45 -j ACCEPT -A Firewall-Win1 --dst 208.67.222.222 -j ACCEPT # Allow queries to Dropbox -A Firewall-Win1 --dst 50.16.0.0/16 -j ACCEPT # Allow queries to Kapersky -A Firewall-Win1 --dst 38.117.98.0/24 -j ACCEPT -A Firewall-Win1 --dst 38.124.168.0/24 -j ACCEPT -A Firewall-Win1 --dst 38.113.165.0/24 -j ACCEPT -A Firewall-Win1 --dst 79.141.216.0/24 -j ACCEPT # Allow queries to Microsoft (update) -A Firewall-Win1 --dst 207.46.206.0/24 -j ACCEPT -A Firewall-Win1 --dst 65.55.200.0/24 -j ACCEPT -A Firewall-Win1 --dst 64.4.30.0/24 -j ACCEPT -A Firewall-Win1 --dst 65.54.221.0/24 -j ACCEPT # Allow queries to dyndns.org -A Firewall-Win1 --dst 91.198.22.0/24 -j ACCEPT -A Firewall-Win1 --dst 204.13.248.0/24 -j ACCEPT -A Firewall-Win1 --dst 208.78.69.0/24 -j ACCEPT # Lots of multicast traffic. Drop it. -A Firewall-Win1 --dst 224.0.0.0/8 -j DROP # Now, log everything else before dropping it -A Firewall-Win1 -m physdev --physdev-in eth1 -j LOG --log-level 4 --logprefix "Win1 " --log-tcp-options --log-ip-options #For everything cs490ns - cotter else, reject the traffic. -A Firewall-Win1 -j DROP Win1 Outgoing Firewall Chain 59 Capture Outgoing Traffic • Data Record – 1 per packet – Feb 19 00:01:03 bridge kernel: Win1 IN=br0 OUT=br0 PHYSIN=eth1 PHYSOUT=eth0 SRC=192.168.1.35 DST=66.94.233.186 LEN=40 TOS=0x00 PREC=0x00 TTL=128 ID=10570 DF PROTO=TCP SPT=2323 DPT=80 WINDOW=65185 RES=0x00 ACK FIN URGP=0 – Records per day ~ 40k to 80k+ cs490ns - cotter 60 Port Scan Attack Detector PSAD • Can be configured to detect various network scans, invalid traffic, attacks, etc. • Can be used to fingerprint source machines • Can be configured to provide active response based on type of input, numbers of input packets for a predetermined period. • Can be used to sort and organize logged data. cs490ns - cotter 61 Summarize traffic • psad -m /var/log/iptables/iptables_log_022011 -gnuplot --CSV-fields dst src dp:count --gnuplotgraph points --gnuplot-xrange 0:100 --gnuplot-fileprefix test_022011 – test_022011.dat – 1, 172, 2 ### 1=12.29.100.148 172=192.168.1.35 –: – 39, 172, 96 ### 39=66.94.233.186 172=192.168.1.35 –: – 246, 171, 1 ### 246=216.191.247.139 171=192.168.1.30 cs490ns - cotter 62 Sort Traffic by Source • Use script (bash / awk / py / ?) to sort traffic into separate files by source • Use DNS to get domain name for sites • Win1_022011.lst – – – – – 12.29.100.148: Output was 0 : 66.94.233.186: r3.ycpi.vip.mud.yahoo.net. : 216.137.43.236: server-216-137-43236.dfw3.cloudfront.net. cs490ns - cotter 63 Analyze traffic • Are addresses identifyable? • Is the traffic known / expected? • Why is traffic there? cs490ns - cotter 64 References • Firewalls and VPNs – Principles and Practices – Richard Tibbs / Edward Oakes – Prentice Hall – 2005 • Linux Firewalls – 2nd ed. – Robert Siegler – New Riders Publishing – 2002 • Guide to Firewalls and Network Security – Greg Holden – Thomson/Course Technology – 2004 • EBtables/IPtables Interaction on a bridge - 2003 – ebtables.sourceforge.net/br_fw_ia/br_fw_ia.html • Red Hat Fedora Linux Secrets – Naba Barkakati – Wiley - 2005 cs490ns - cotter 65 Summary • What is a firewall? • Architectures – – – – Stand Alone / application / proxy Personal / host based Gateway / packet filters Enterprise / hardware • Packet Filtering concepts • Packet Forwarding • Roles – Bastion – DMZ • EBtables cs490ns - cotter 66