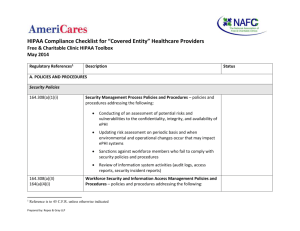
Physical Security
advertisement
It’s About The ePHI Objective Review the security rule as it pertains to › Physical Safeguards ♦ ♦ How to protect the ePHI in the work environment Implementation ideas for your office The Security Rule Reasonable and appropriate safeguards that cover › Information systems › Related equipment › Facilities What Are The Safeguards? Physical measures › Locking the door › Requiring passwords Policies and procedures › For everything from employee training to protecting the data Three Areas Of Focus Facility Access Controls › Limiting physical access to ePHI Workstation Use and Security › Defining business use of workstations › Controlling the environment Device and Media Controls › For all equipment that contains ePHI Facility Access Controls Contingency operations Facility security plan Access control and validation procedures Maintenance records Contingency Operations Disaster recovery or emergency operations › Maintains proper security while allowing for data recovery Cover such events as: › Loss of power › Flood Consider access, as well as recovery › Chemical spills › Propane leak Facility Security Plan Policies and Procedures covering: › Physical access control › Tampering and theft prevention Access Control & Validation Procedures › Access based on roles and/or functions › Visitor guidelines › Software access ♦ ♦ Limit authority/responsibility Track updates/modification Maintenance Records Document › Repairs and modifications to the facility ♦ ♦ ♦ Type of repair Authorized by whom Reason for repair › Changes to alarm codes Workstations Defined as an electronic computing device such as: › Laptops › Desktops › Tablets Capable of electronic media storage Workstation Use Define business use of workstations Policies and Procedures › Proper functions to be completed › Manner in which they are performed › Physical attributes of the surroundings for the workstations with access to ePHI ♦ ♦ Visibility to others Accessible to unauthorized persons Workstation Security Restrict access to authorized users › Are workstations identified? › Viewed only by authorized individuals with unique user IDs and passwords? › Filters? › Screen savers? › Automatic log off? Device and Media Controls Policies and procedures › That govern how ePHI is protected ♦ ♦ ♦ During moves On backup media During upgrades Elements of Control Disposal – of ePHI › How does this happen? Media re-use › Is re-use allowed? › What steps are taken to eliminate ePHI Accountability › Where is the ePHI? Data Backup and Storage Disposal Policies and procedures that address the final disposition of ePHI › Including the media that held it › Render it unusable ♦ By erasing and overwriting or magnetically clearing or both › Or inaccessible ♦ By physically damaging it Media Re-use Remove ePHI Document the removal Have a policy and procedure that outlines the process Accountability Involves record keeping › This is only addressable in the final security rule, however, it would be very difficult to justify not keeping track of equipment Inventory of equipment that includes portable media › Take account of ♦ ♦ Person responsible for each device Serial numbers and/or labels for identification Data Backup And Storage Address the backup of ePHI before the movement of any equipment › Best to have a copy, just in case something unexpected happens! Maintain Integrity Of The ePHI Have in place: Policies and procedures that cover › Audits ♦ ♦ To track changes to data To review accesses › Inventory ♦ To know where the ePHI is located Inventory Control Log Should contain elements such as: › › › › › › › Device Name Make/Model Date Acquired Serial Number Location User Maintenance Performed ♦ › Date taken out of Service ♦ ♦ ♦ ePHI destroyed (Y/N) Method of destruction Certificate of destruction › Person responsible for destruction of ePHI › Person who validated or verified destruction of ePHI Description and Date The Process To Follow Inventory › Walk through your office › Notice everything ♦ Both in-service and out of service equipment › Record it all › Include portable and mobile devices Check the ePHI on the inventory › Record everything Review Physical Elements Offices / Exam Rooms › Doors and windows - lockable? Restricted areas › Locked and log of access maintained? Alarms › Who has access? Recent changes? Wireless access points › Monitor the devices that access your network Wiring › Are surge suppressors in use? Assess With the eyes of an outsider is ePHI › › › › Viewable? Portable – on unattended laptops? In use – where? On what? Is there out-of-service equipment with ePHI? › Accessible via your network? ♦ ♦ Monitor users on the network Have in place termination procedures that include disabling network access Protect ePHI Make changes › › › › Move monitors Turn desks Lock up equipment Secure work areas Control access › Know who has had the opportunity to view or hack your ePHI ♦ ♦ ♦ Telephone repairs Electricians Locksmiths It’s Not Just Computers Printers › What’s being printed? › Who can retrieve the paper? › Where is it located? Faxes and scanners › What is stored on the machine? › Where is it located? › Who can access the data? Include Also Incidental equipment › › › › › Pagers Dictaphone tapes Answering machines Point of care devices External hard drives Network wiring › Are access points open and available? Location of the router › Is it secure? Protection Options Protect all equipment from: › Outside access › Unauthorized use › Wandering off For Electronics › Use surge protectors Review fire extinguishers › Rated for electronics Remember ePHI › Is vast › Requires special protections and safeguards › Is subject to HIPAA’s Security Rule You have to know where the ePHI is located in order to protect it Take every precaution possible to protect ePHI QUESTIONS?