Security and Backup
advertisement
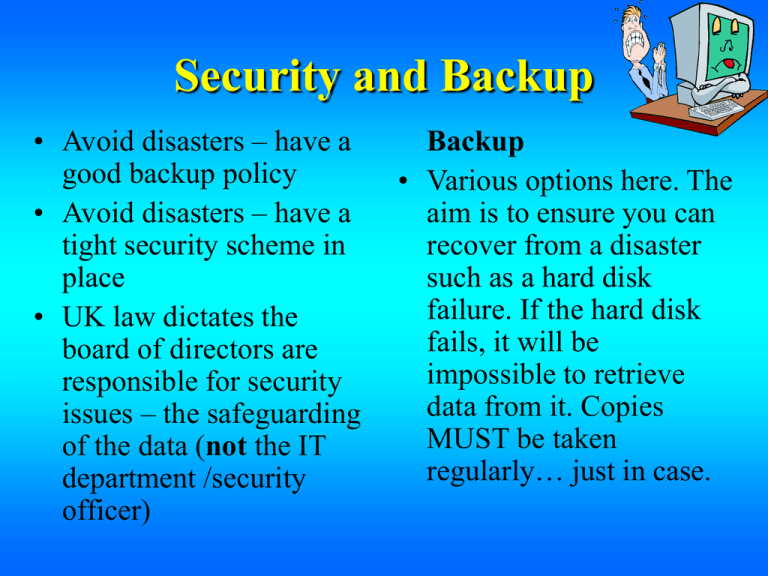
Security and Backup • Avoid disasters – have a good backup policy • Avoid disasters – have a tight security scheme in place • UK law dictates the board of directors are responsible for security issues – the safeguarding of the data (not the IT department /security officer) Backup • Various options here. The aim is to ensure you can recover from a disaster such as a hard disk failure. If the hard disk fails, it will be impossible to retrieve data from it. Copies MUST be taken regularly… just in case. Security and Backup Backup key points: • Decide with what, when, how and what is to be backed up: • WITH WHAT: floppy disk, tape streamer such as a Travan or DAT device .. or a larger capacity DLT drive? It comes down to capacity/speed/cost – look through recent magazine reviews/adverts for details • WHEN: as often as needed (within reason) as the data/files change often • Exact times will depend on the volume of data involved • Daily tapes + weekly tapes allows back-tracking through a week or month • During office hours or after? See WHATIS.COM Security and Backup HOW: Full Backup • A full backup is simply that: a complete backup of every single file. • The advantage of such a backup is that files are easily found when needed. Since full backups include all data on the hard drive, you do not have to search through several tapes to find the files you need to restore. In case you need to restore the entire system, all of the most current information can be found on the last backup tape. • The disadvantage is that doing nothing but full backups leads to redundancy which wastes both media and time. A backup strategy would normally include a combination of full, incremental and/or differential backups. See: Backup (Internet link) Another includes RAID (Internet link) And another with Grandfather/father/son (Internet link) Security and Backup • • • • HOW: Incremental Backup Incremental backups include files that were created or changed since the last backup (that is, the last full or incremental backup). To achieve this, the status of each file must be recorded either within the backup software or through the use of the archive attribute of the files. If no previous backup was made, an incremental backup is equivalent to a full backup. Incremental backups make better use of media compared to full backups. Only files that were created or changed since the last backup are included, so less backup space is used and less time is required. The disadvantage is that multiple tapes are needed to restore a set of files. The files can be spread over all the tapes in use since the last full backup. You may have to search several tapes to find the file you wish to restore. The backup software can minimize this by remembering where files are located; however a restoration may still require access to all incremental backups. Security and Backup • • • • HOW: Differential Backup A differential backup includes all files that were created or modified since last full backup. Note the difference between incremental and differential: incremental b/up save files changed since the last (incremental or full) backup, whereas differential b/up save files changed since the last full backup. The advantages over full b/up: it is quicker and use less media. The advantage over an incremental b/up: the restore process is more efficient - at worst, the restore will require only the latest differential b/up set and the latest full backup set, whereas an incremental b/up could require all incremental b/up sets and the full b/up set. The disadvantage of a differential backup is that longer and longer time is needed to perform them. The amount of data backed up each time following the full backup gets larger and larger. Compared to incremental backups, differential backups are more wasteful of time and media - each backup would store much of the same information plus the latest information added or created since the last full backup. Security and Backup WHAT: you pick what files should be included depending on how “valuable” they are • All systems need a complete backup – software/OS/files (Why?) Security and Backup To look for: Other points: • Grandfather-father-son backups for batch processing systems is used • See p281 / ch. 59 for an example • RAID • Disk Mirroring • And what about Internet Backup options? (See whatis.com) and… • http://www.ibackup.co m/intro.htm Security and Backup • • • • • Security Issues • Termination ! Out NOW & Personnel policy to cover: escorted off the premises … and User Name removed from Recruitment – references needed! Most damage to the system immediately: systems/files is done by WHY? employees… • Employee code of conduct Training – to stop errors (IT01 – re-read ch.11 “Codes Supervision of Practice”) Appraisal • Passwords? Separation of duties – duplication of key jobs