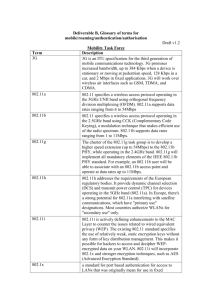
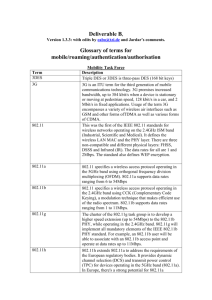
20120516
advertisement

Privacy-Preserving Universal
Authentication Protocol for
Wireless Communications
Daojing He, Jiajun Bu, Sammy Chan, Chun Chen and
Mingjian Yin
IEEE TRANSACTIONS ON WIRELESS
COMMUNICATIONS,VOL. 10, NO. 2, FEBRUARY 2011
Outline
Introduction
Method : Priauth
Scheme
Conclusion
Introduction
Seamless roaming over wireless networks is
Highly desirable to mobile users, and
security such as authentication of mobile
users is challenging.
In this paper, we propose a privacypreserving universal authentication
protocol, called “Priauth”.
Introduction
A typical roaming scenario involves three parties:
Roaming user
Visiting foreign server
home server 𝐻
U
V
H
Introduction
A privacy-preserving user authentication
scheme should satisfy the following
requirements:
1.Server Authentication
2. Subscription Validation
3. Provision of user revocation
mechanism
Introduction
4. Key establishment
5. User anonymity
6. User untraceablility
Outline
Introduction
Method : Priauth
Scheme
Conclusion
Method : Priauth
The method is the use of basic group signature.
Group signature
KEYGEN(N,T):
a master public key 𝑚𝑝𝑘
secret keys𝑢𝑠𝑘[𝑖]
The revocation token of member i at interval j is
urt[i][ j]=Bij
Method : Priauth
REVOKE ( RLj , urt[i][ j] ) :If i is revoked at
time interval j , then RLj ← RLj ∪{ Bij }.
SIGN ( mpk , j , usk[i],M) = σ
VERIFY ( mpk , j , RLj ,σ , M)
Method : Priauth
Each server manages a group of subscribers,
and each subscriber could be a roaming
user.
Each server also has a signing/verification
key pair (𝑠𝑘, 𝑝𝑘) of a conventional digital
signature method
Method : Priauth
Outline
Introduction
Method : Priauth
Scheme
Conclusion
Scheme
Outline
Introduction
Method : Priauth
Scheme
Conclusion
Conclusion
In this paper, we have proposed a novel
protocol to achieve privacy-preserving
universal authentication for wireless
communications.