File Slack
advertisement
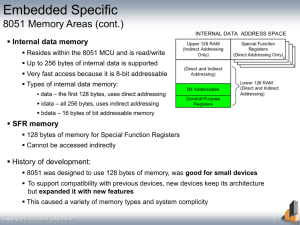
Computer Forensics BACS 371 Hiding Data in “Plain Sight” Places to hide data Evidence can be hidden in many places within a disk. The notion of “empty space” on a disk is more complicated than you might suspect. The question becomes “what are the different types of empty space?” Usable Storage Space Data can be found and hidden wherever there is usable storage space: Disk drives and file systems System processes and memory Central processing unit (CPU) and network card memory Digital cameras, mobile phones, music players Network storage and attached devices Network communications and protocols Where do Files Get Hidden on the Disk? File slack (RAM slack & Disk Slack) Volume slack, where partition boundaries leave free space Partition slack, where leftover sectors remain in stored blocks of data Good drive blocks marked as bad and used for storage Where do Files Get Hidden on the Disk? Host protected area (HPA) or vendor-specific drive space Master boot record (MBR) where empty drive sectors remain Boot sectors in non-bootable partitions Data Hiding Hard Drive Data Storage Concepts Sector Cluster (File Allocation Units) Minimum storage size on a hard drive One “pie shaped” arc of a platter Common storage size of 512 Bytes Established during low-level formatting Numbered sequentially starting at 1 Minimum storage size for a file as determined by file system Common cluster size is 4096 Bytes (4KB) – 8 Sectors File Determined by file system Sectors Clusters 8 Sectors File 2 Clusters * Just an example, your file may occupy more or fewer clusters. File Collection of Information written to a disk Generally created in an application-specific format Occupies a fixed number of clusters Each file’s cluster has a pointer to the next cluster in the file The final cluster contains the End of File (EOF) marker Files Logical File Size Physical File Size Exact size of contents of file in bytes Amount of space a file occupies on disc in bytes File Slack Unused space between logical end of file and physical end of a cluster Two types: RAM slack and Disk Slack Physical File Size <- Logical File Size -> <- File Slack -> File Slack What does File Slack Contain? Who knows??!! Old data that was deleted but not overwritten yet May contain remnants of older files, or other evidence including Passwords Old directory structures Miscellaneous information …. File Slack Example Hello World! Has 12 Characters in the file But occupies 4096 bytes on the disk! File Slack Example File Slack Example File Contents: “Hello world!” 12 bytes 3rd Sector 2nd Sector RAM Slack: 512 bytes – 12 bytes = 500 bytes Disk Slack: 4096 Bytes – 512 Bytes = 3584 Bytes Assumptions: • Sector Size = 512 Bytes • Cluster Size = 4KB = 8 Sectors File Slack Example RAM Slack Unused space at the end of a sector. Contains information adjacent to the stored information from Main Memory (RAM). The file has only 12 characters, but must write a minimum 512-byte block to the disk – the other 500 characters are whatever happen to be in RAM at the time. Disk Slack Unused space at the end of the cluster. Contains information left over on the disk from prior files. The file system must always write in multiples of clusters (4096 bytes in this case.) The other 3584 bytes (7 sectors) are filled with whatever used to be in the clusters before they were marked for deletion. Ways of Hiding Information Rename the File Make the Information Invisible Use Windows to Hide Files Protect the File with a Password Encrypt the File Use Steganography Compress the File Hide the Hardware Use Application programs Rename the File If you change the file suffix to a different one, then the standard Windows applications will not “see” it. This is not a particularly effective way to hide data since the file will still run the application if you double-click on it. This happens because there is an internal file signature that tells Windows which application to run. Changing the external name does not affect this. Use Windows to hide files You can set a property on a file to make it “hidden”. If you set a folder view options to not show hidden files, they become invisible. Windows also automatically hides files with particular suffixes from being seen in the directory window. The most common hidden type is .sys If you name a file with a .sys suffix and then change the folder view options to not show hidden system files, they will also disappear. Both of these methods are easy to overcome. Use a Password You can hide the contents of a file with a password. On older versions of Windows this was not particularly effective. More recent versions are significantly more robust. While the passwords can be broken, it is not a trival task. Basic Approaches to Password Cracking Illegal Methods Social Engineering Pretexting Phishing Login spoofing Keystroke logging Shoulder surfing Dumpster diving Security System Attacks Basic Approaches to Password Cracking Ask! Interview/Interrogation Social Engineering Plain sight Post-It Notes Documents Guess Social Engineering Weak Encryption Dictionary Attack Brute Force Attack 1 Guessing Not surprisingly, many users choose weak passwords, usually one related to themselves in some way. Repeated research over some 40 years has demonstrated that around 40% of user-chosen passwords are readily guessable by programs. Examples of insecure choices include: blank (none) the word "password", "passcode", "admin" and their derivates the user's name or login name the name of their significant other or another relative their birthplace or date of birth a pet's name automobile licence plate number a simple modification of one of the preceding, such as suffixing a digit or reversing the order of the letters. a row of letters from a standard keyboard layout (eg, the qwerty keyboard -- qwerty itself, asdf, or qwertyuiop) and so on. Some users even neglect to change the default password that came with their account on the computer system. And some administrators neglect to change default account passwords provided by the operating system vendor or hardware supplier. A famous example is the use of FieldService as a user name with Guest as the password. If not changed at system configuration time, anyone familiar with such systems will have 'cracked' an important password; such service accounts often have higher access privileges than a normal user account. The determined cracker can easily develop a computer program that accepts personal information about the user being attacked and generates common variations for passwords suggested by that information. 1http://en.wikipedia.org/wiki/Password_cracking Encrypt the File This is the next level up from using a password. It basically scrambles the bits of the file in a systematic way so that, with the proper key, it can be unscrambled. Typically, any file with a password is also encrypted. High level encryption can be extremely difficult to “crack” even with vast computer resources. Use Steganography This is a method where one file is embedded into the bits that make up another file. Like encryption, it depends upon a password and a decoding algorithm to recover the original hidden data. This can be particularly hard to uncover because text messages can be hidden in seemingly innocuous images or sound files. Compress the file This method is not particularly effective. Most modern operating systems have built-in programs to compress and decompress files and folders. Previously, this was not true, so a compressed file was as unreadable as an encrypted one. Hide the Hardware The computer settings can be manipulated so that specific hardware devices are invisible. A close examination of the actual machine can quickly find this situation and the hardware can be made visible again. Less obvious forms of this are to hide segments of a disk drive so that portions of the physical drive are not “counted” even by low-level disk partition tools. Use Application Programs You can hide data in application programs in various ways. Word, for example, has several hiding places that can be used. Likewise, webpages can hide a good deal of information in the code or in invisible text. Methods for Hiding Data in Word Docs Font Size Font Color Hidden Text Comments Track Changes Meta Data (File Properties) Author Organization … Versions Fast Saves Methods for Uncovering Data in Word Docs Select All -> Font Black on white Font Size Font Type Read as Text Forensic tools (Hex Editor)