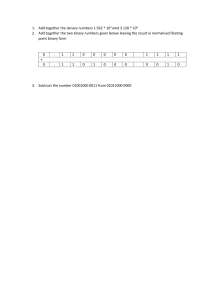
1 (PAPER 3 NOTES BELOW) Paper 1 1. Information Representation 1.1 Data Representation Benefits of BCD ● more straightforward to convert between BCD and denary ● less complex to encode and decode for programmers ● easier for digital equipment to use BCD to display information ● can represent monetary values exactly Applications of BCD ● electronic displays e.g. calculators, digital clocks – only need to show individual digits, conversion between denary and BCD is easier ● storage of date and time in BIOS of PC – conversion with denary is easier Applications of Hexadecimal ● MAC addresses ● HTML colour codes ● can also be used to refer to memory addresses in assembly language and in machine code ASCII Representation ● each character has a unique code ● character is replaced by its corresponding code ● codes are stored in the same order as in the word Character Set (e.g. ASCII, UNICODE, Extended ASCII) ● All of the characters that the computer can represent/use ● Each character has a corresponding unique binary number Similarities ● All can use 8 bits ● ASCII is a subset of Unicode/EA 2 ● Each represent characters using a unique code Differences ● Unicode can represent multiple languages and a wider range of characters than ASCII ● ASCII – 7bit, Extended ASCII – 8bit, UNICODE – 16bit 1.2 Multimedia Graphics ** Bitmap Graphic ● made up of pixels, each of a single colour (with each colour having a unique binary value) ● stored as sequence of binary numbers (store binary value of each pixel) ● prone to pixelation when enlarged ● larger file size – data is stored about each pixel ● can be compressed significantly ● more difficult to edit – each pixel needs to be edited separately Pixel ● The smallest addressable element in an image File header ● Stores data (metadata) about the bitmap image (e.g. colour depth, image resolution) ● Can store: file type, compression type, dimensions (width x height), file size Image Resolution ● Total number of pixels in an image (number of pixels wide * number of pixels high) ● Increasing resolution – more pixels can be stored, image is sharper/less pixelated Bit depth/Colour depth ● The number of bits used to represent each colour // number of bits per pixel ● Determines number of colours that can be represented in an image ● Increase in bit depth – image has greater range of colours and is closer to original (leads to increased file size) 3 Vector Graphic ● stores set of instructions about how to draw the shape ● does not pixelate when scaled/enlarged ● individual components of image can be edited ● smaller file size – contains just instructions ● do not compress well – has little redundant data Drawing Object ● component of vector graphic created using a formula/command Drawing Property ● contains data about the shapes ● defines aspect of appearance of a drawing object Drawing List ● the list of shapes that make up an image // list of all drawing objects in image ● stores commands required to draw each object Vector Graphic Representation ● encoded as series of geometric shapes ● stored coordinates of drawing objects in image ● contains drawing list – commands for creating each individual object (and their attributes) Sound ** Sound Representation ● amplitude is recorded a set number of times in a second ● each amplitude is given a corresponding unique binary value/number ● binary number is saved/stored in sequence Sampling ● taking measurements at regular intervals and storing the values Sampling Rate 4 ● number of samples taken per unit time // per second Effect of increasing sampling rate ● sound is recorded more often // smaller gaps in sound wave & between samples ● reduces quantisation errors ● improves accuracy – digital waveform resembles analogue one more closely ● increases file size (increases number of total samples taken – so more bits needed to store the data, takes up more space in memory) Sampling Resolution ● number of bits used to store each sample Effect of increasing sampling resolution ● increases number of bits used to store each sample // more bits per sample ● wider range of amplitudes can be stored // more amplitudes can be represented ● file size increases ● digital waveform is closer to original (improves accuracy) ● smaller quantisation errors Analogue data ● A variable // data value that is constantly changing 1.3 Compression Compression Reasons ● reduces file size – takes up less space in memory (leaves space for other files, allows more images/files to be stored) ● faster download/upload rate (reduced transmission time) from/to web ● less bandwidth used to download/transmit ● original might be too large to send through email/as attachment Lossy Compression ● Original data is lost/deleted (cannot be done in text file) & file cannot be reconstructed ● If used on text file, it would corrupt (all data is required, otherwise it would not make sense) 5 ● Videos have a lower resolution, will buffer less if being streamed real-time, lowers bandwidth required to transmit ● Used when all data is not required, quality can be reduced without user noticing or if a significant reduction in file size is needed Lossless Compression ● Original data is preserved ● Used when all data is needed (e.g. file needs to be fully restored), a high quality video/image is needed, or it is already a relatively small file Compressing Files Sound ** ● reduces amplitude range (to only range used) – reduces bits needed to store each sample ● run-length-encoding – consecutive sounds grouped (binary value of sound recorded along with number of times it repeats) ● record only changes in sound (not actual sounds) ● RLE – consecutive sounds grouped (binary value of sound recorded along with number of times it repeats) Images (Lossy) ● reduce bit depth – reduces number of bits used to store a colour (each pixel has fewer bits) ● reduce number of colours – fewer bits needed to store each colour ● reduce resolution – fewer pixels altogether (less binary to store) (Lossless) ● RLE – replaces sequences of the same colour pixel with colour code and number of identical pixels Run-length Encoding ** ● Identifies groups/sequences of repeated characters and replaces them with a copy of the character and number of times it occurred RLE Limitations 6 ● Works by storing a colour and the number of times it occurs consecutively – there may not be many sequences of same colour ● It would store each colour then the count, which would be 1 – only adds to file size // adds to total data ● E.g. RBG would become R1 B1 G1 7 2. Communication 2.1 Networks including the internet LAN allows… ● communication/sharing of data between devices on the network ● sharing of resources e.g. hardware/software applications ● central management (security, backup etc.) ● covers small geographical area, connection between devices is usually physical ● infrastructure is privately owned (not controlled by external organisations) PRIVATE OWNERSHIP ● high data transfer rate ● protection is easier to implement, more secure than WAN WAN ● covers a large geographical area, connection is often virtual ● low data transfer rate ● can have private or public ownership (likely to be controlled by external organisations Client-Server Model ● web pages/data saved on servers ● client sends request ● web servers process requests/performs requested tasks and returns results to the client ● client displays result to user ● user’s computer is the client ● server can host shared files ● users can request a file from any client computer ● files can be accessed simultaneously by several users Examples of Client-Server Models 8 ● sending and receiving an email ● using a print or file server ● a company/school centrally storing files Features of a peer-to-peer network ● computers are of equal status ● each computer provides access to data and resources // data is distributed ● computers can communicate and share resources ● each computer responsible for its own security Drawbacks of a peer-to-peer network ● reduced security (no central management of security) – each computer is at risk from viruses from other computers ● no central management of back-up – if data from one computer is not backed up it is lost to all of them ● no central management of files – hard to maintain consistency ● computers have slower response time – due to being accessed by other computers ● files may not always be available – not all computers are always switched on Thick-Client ● server performs minimal processing for client ● most resources are installed locally – clients do most of their processing independently Thin-Client ● server performs all processes required by task/data storage ● clients only send requests to server and displays returned results Star Topology ● devices only connected to central router/device (switch/hub etc.) ● each computer only connected to server ● fewer collisions – high performance as each device only connected to switch ● easily scalable – device directly connected to switch ● more resilient – not reliant on one single cable How data is transmitted ● data from sending device is transmitted to the router 9 ● data has address of recipient ● router determines recipient’s destination address – using routing table ● router transmits data directly/only to recipient Mesh Topology ● all computers connected to at least one other device ● multiple routes between devices ● computers can act as relays – forward packets to final destination Advantages of mesh top. ● if one line goes down alternate routes are available ● improved security – not using one main line ● fewer collisions (more routes available) ● new nodes can be added without interfering with others Cloud Computing ● accessing a file/service on a remote server ● Public cloud – services offered by a third party over public internet, available to anyone with appropriate software/equipment (resources available on Internet, available to anyone) ● Private cloud – services offered by a private internal network, only available to select users (not general public), dedicated system only accessible from the organisation Advantages ● can be free ● saves storage on existing devices ● data can be accessed from any device (with internet access) ● data will likely be backed up/ higher chance of recovery ● better security ● scalable & easily shared Disadvantages ● only accessible with internet access ● can take a long time to upload/download the data ● can be expensive (long term) 10 ● may have limited storage space for free ● may not have backup/recovery or security options ● you are reliant on someone else/dependant on third party (for security or backup) ● can’t access files if server goes down Disadvantages of public cloud ● loss of control – data is stored on remote infrastructure, relies on external provider ● requires reliable internet connection to access data ● increased recurring costs – provides charger must be paid, LAN is one-time only Advantages of a wired network (better performance, faster access) ● higher bandwidth – less latency (good for streaming larger files) ● more reliable/stable connection – less vulnerable to interference (distance/walls) ● more secure – confidential data can be transferred securely Advantages of a wireless network ● freedom of movement (not fixed to a single location) – can move between rooms, no need for physical connection // devices can be portable ● easily expandable/scalable if more devices want to join (ppl can join on multiple devices) ● less cabling needed – cheaper setup ● allows access in remote locations (e.g. rural areas) Disadvantages of a wireless network ● higher latency ● affected by weather ● slower transmission speed ● direct line of sight needed Copper Cables ● data is transmitted through electrical signals ● lower transmission rate ● chance of interference and interception ● require repeaters over long distances ● more sturdy/reliable/flexible 11 Fibre-optic Cables ● data is transmitted using light ● has a greater bandwidth and faster transmission speed ● smaller risk of interference ● can be used over long distances – needs less signal boosting ● more difficult to hack into ● more prone to damage, less flexible/can break when bent, more expensive to install, difficult to terminate Radio Waves ● carries data wirelessly in the form of electromagnetic waves Satellite ● communication device in Earth’s orbit ● receives and transmits data Switch ● allows communication between devices ● connects individual devices to each other ● receives transmissions and forwards them to their destination Server ● manages access to a centralised resource (usually between devices on LAN) Functions of WNIC ● provides interface/allows connection to wireless network as an antenna ● receives analogue waves and converts them to digital ● takes digital input and converts it into analogue waves -sends radio waves through antenna ● encrypts and decrypts data ● provides MAC address to identify device on network WAP ● hardware that provides radio communication from central device to nodes on a network ● allows connection of devices using radio waves/signals/Wi-Fi 12 ● allows wireless enabled devices to connect to wired network Bridge ● connects two LANs with the same protocol ● allows communication/data transmission between two networks with same protocol Repeater ● restores a digital signal so it can be transmitted over greater distances Role of Router ** ● receives packets from devices // external network/internet ● stores IP and MAC addresses of all devices attached to it ● maintains routing table ● routes/forwards packets to destination ● finds destination of a packet (using IP addresses) ● assigns private IP addresses to devices on a LAN ● finds most efficient path to destination ● can act as a firewall, gateway (+ perform protocol conversion/changes packet format) Ethernet ● a protocol ● used for data transmission over a wired network ● uses CSMA/CD ● data is transmitted in frames – each frame has source and destination address and error checking data CSMA/CD (protocol) ● used to detect and prevent collisions ● device/node that listens to a communication channel (scans voltage) ● data is only sent when channel is free/idle // line is empty As there are multiple nodes on network/topology… ● data from two nodes can start to transmit simultaneously, causing collision ● if collision occurs, nodes send signal to stop transmitting ● waits a random time before attempting to send data again 13 Bit Streaming ● Data is compressed before transmitting ● Video is transmitted continuously as series of bits ● On download, the server sends data to a buffer on the client computers ● Recipient receives bit stream from the buffer Real-time ● Used when watching a live stream of events that are currently taking place ● Event is captured live with a video camera connected to a computer ● Media is sent to user’s device/buffer via bit stream directly as it is being recorded ● Cannot be paused or rewound On-demand ● Video is already recorded/event has taken place ● Existing media is encoded to bit streaming format and uploaded to a server ● Can be watched at user’s convenience (can be paused/forwarded or rewound) Difference between the WWW and the internet WWW ● uses http/https protocol to transmit data ● collection of web pages Internet ● uses TCP or IP protocols ● interconnected network of networks Hardware Supporting the Internet PSTN ● consists of many different types of communication lines ● allows for full duplex data transmission ● communication passes through different switching centres ● line remains active even during power outage ● dedicated channel used between two points for duration of phone call 14 2.2 Networks including the internet continued IPv4 ● 4 groups each represented by 8 bits (32bit) ● Either denary or hexadecimal with numbers between 0-255 (in each group) ● Separated by full stops IPv6 ● 8 groups each represented by 16 bits (128bit) ● Hexadecimal numbers between 0 and FFFF ● Groups only contains 0 can be replaced with :: ● Separated using colons ● Used when the number or IP addresses needed exceeds number available using IPv4 Subnetting benefits ** ● improves security – data stays in its subnet, not all devices can access all areas of network, devices do not receive unintended data ● allows extension of network/easier to expand – allows greater range of IP addresses ● reduces amount of traffic in a network – improves network speed, data stays within subnet and devices are not flooded with data ● easier maintenance/management – only one subnetwork may need taking down, rest can continue *faults can also be isolated more efficiently IP address in subnetwork ● made up of network ID and host ID ● each device on subnetwork has same network ID // each subnetwork has different network ID ● every device in each subnetwork has different host ID but the same network ID ● host ID uniquely identifies device within the same subnetwork Public IP address ● is visible to any device on the internet ● assigned to allow direct access to the internet ● allocated by ISP 15 ● unique throughout internet Private IP address ● only visible to devices within the LAN ● used for internal LAN communication only ● allocated by router ● only unique within LAN Dynamic IP address ● new one is reallocated each time a device rejoins a network Static IP address ● does not change each time a device connects to the internet // is fixed URL, WWW and DNS Use ● A URL is entered into web browser and parsed to obtain the domain name ● The Domain name is sent to DNS ● DNS has database of domain names and their corresponding IP Addresses ● DNS searches its database for given domain name ● If found, the IP addresses is returned to web browser, which displays the resource ● If not found, the request is forwarded to a higher level DNS and the IP addresses returned is added to the database of the lower level DNS 16 3. Hardware 3.1 Computers and their components Need for Secondary Storage ● to store files/data/software long-term Need for Primary Storage ● to store files needed to boot system ● to store OS or any system software ● to store intermediate data/current data being processed Embedded system ** ● microprocessor within a larger system that performs a specific task ● has memory, input/output abilities and processor ● integrated into machine, not easily changed (by user/owner) ● e.g. a system in a washing machine that only controls cycle programs ● combination of hardware and software designed for a specific function ● does not have its own operating system ● does not require much processing power Disadvantages ● difficult to change/update firmware by user // difficult to upgrade to take advantage of new technology ● cannot be easily adapted for another task ● difficult to update or repair – usually thrown away instead ***no hardware operation questions have been repeated so far so chances are the other devices we have to know (e.g. speakers, laser printers etc.) will likely come up*** Operation of Laser Printer ● contains a revolving drum that is given an electrical charge ● contents of page (provided by buffer/user) are drawn on drum as an electrostatic charge by a laser beam that moves back and forth ● the drum is coated with oppositely charged toner which only sticks to areas charged by the laser beam ● the drum then rolls over electrostatically charged paper, transferring the pattern onto the page 17 ● paper is passed through a fuser/is heated to seal image ● the electrical charge is removed from drum, excess toner is collected Operation of 3D Printer ● additive manufacturing ● uses digital 3D model or CAD file ● builds up model one layer at a time – starting from bottom, using xyz coordinates ● material is fused together layer by layer ● Fused Deposition Modelling – material is heated and pushed through nozzle Use of temperature sensor ● prevents overheating // ensure material is hot enough ● identifies material of object/material being used Microphone Operation ● has a diaphragm ● incoming sounds waves cause vibrations about diaphragm ● this causes coil to move past a magnet ● electrical signal is produced Speaker ● an electric current is sent to speaker ● the electric current passes through a coil ● current in the coil creates an electromagnetic field ● an electromagnet is repelled by, or attracted to the permanent magnet based on direction of the current in the coil ● movement of coil causes the diaphragm to vibrate – this vibration creates sound waves Magnetic Hard Disk ● has platters – divided into sectors and concentric tracks ● surface of disk can be magnetised ● has a read/write head mounted on an arm ● data is encoded as a magnetic pattern ● writing – variation in current in head causes variation in magnetic field on disk 18 ● reading – variation in magnetic field causes variation in current through head Advantages ● costs less per unit storage (used when large storage capacity is required) ● has more longevity (used with devices that work all the time and have large number of read write operations) Solid State Memory ● uses a grid of columns and rows (arrays/blocks) that has two transistors at each intersection: ● floating gate – stores voltage (represents either a 1 or 0) ● control gate – controls movement of charge/electrons during read/write operations ● not possible to overwrite existing data (need to erase first then write data into location) Advantages ● no moving parts – more reliable ● faster data access times Optical Disk Reader/Writer ● a rotating disk with concentric tracks made from a reflective metal layer ● data is read/written using laser light (either red or blue) that is shone onto the disc ● data is stored in pits and lands on the track – sequences of amorphous and crystalline states on the metallic layer (correspond to 0s and 1s) ● reading – reflected light from different states is encoded as a bit pattern ● writing – laser changes surface to crystalline or amorphous states based on the bit pattern being stored ● read and write operation can occur simultaneously Features/Uses ● used for transferring data between devices or as back-up systems ● can be read-only – used to distribute software, movies or games ● generally have lower storage capacity 19 Resistive touch screen ● has two layers ● when user touches screen, layers touch and a circuit is completed ● processor determines horizontal and vertical point of contact ● will work if any object touches the screen Capacitive touch screen ● has several layers ● when top layer is touched, there is a change in the electric current ● a microprocessor identifies the coordinates of touch Virtual Reality Headset ● video/data is sent from a computer to the headset ● the video feed is sent to an LCD/OLED display ● there are two lenses placed between eyes and screen – allows for focusing and reshaping of video for each eye, creating 3D effect ● uses an fps of 60 to 120 ● sensors measure/track movements of user, allowing the video on the screen to react to and mimic movements ● uses binaural (surround) sound so sound from speakers appears to come from all directions ● can also use infrared sensors to monitor eye movement, allows depth of field on screen to be more realistic Purpose of a buffer ● To act as temporary storage – temporarily stores data until it is ready to be transmitted to the device ● Stores data before it is used by receiving device ● Allows processes to operate independently of each other ● e.g. video buffer when streaming videos, printer buffer when data is transferred from computer to printer Process ● instructions and data are sent by computer to buffer ● data is transferred from buffer to device – allowing user to continue using computer // allowing processor to continue processing ● when buffer is empty, an interrupt is sent to computer, requesting more data 20 RAM ● primary memory ● stores currently running part of software/data/OS/programs/processes ● either static or dynamic ● can store data about I/O devices, contents of buffer or information about current process ● SRAM – transistors arranged as flip-flops, more complex circuitry ● DRAM – uses (a single) transistors and capacitors, stores bits as a charge SRAM Advantages/Disadvantages ● faster access time – because it does not need to be refreshed ● used on CPU for performance (used in cache memory) ● has lower data density ● does not need to be refreshed – consumes less power DRAM Advantages/Disadvantages ● costs less per unit ● higher storage/data/bit density – more data stored per chip ● simpler design – uses fewer transistors ● needs to be refreshed – has higher power consumption ● slower access speed (used in main memory) ROM ● primary memory ● stores start-up instructions/BIOS, firmware, any permanently required data ● stores the kernel of the operating system // parts of OS ● PROM – can be set once ● EPROM – erased using UV light, needs to be removed from device, can be overwritten multiple times, must be entirely erased to rewrite ● EEPROM – erased using voltage (no additional equipment is needed), erased within device, can be overwritten multiple times, does not have to be entirely erased before rewriting, contents of firmware can be changed easily 21 Use in embedded systems ● to store data that does not change ● data must be stored when device is powered off ● stores boot up instructions Control system ● uses feedback ● produces an action Role of an Actuator ● generates signal // converts electrical energy into mechanical energy ● to produce an action (be specific to situation) Importance of feedback ● ensures system operates within given criteria ● allows system output to affect system input ● allows conditions to be automatically adjusted 3.2 Logic Gates and Logic Circuits 22 4. Processor Fundamentals 4.1 CPU Architecture Stored Program Concept ● instructions and data are stored in the same memory space/in main memory Components in Von Neumann Architecture ● Buses ● Registers ● CPU ● CU ● ALU ● IAS ● System clock General Purpose Registers ● Hold temporary data when performing operations ● Used for any purpose ● Can be used by most instructions Special Purpose Registers (All registers we have to know are special purpose) ● Hold status of a program ● Specialised for specific use ● Can only be used by certain instructions Program counter ● holds the address of the next instruction to be loaded ● is incremented once an instruction has been carried out Memory Address Register ● stored address from memory location currently being read from or written to (where data is being fetched from) Memory Data Register ● holds the data fetched from address in MAR 23 ● data is copied to CIR Current Instruction Register ● holds data from MDR ● holds instruction currently being decoded/executed Index Register ● stores a value that is added to an address to give another address Status Register ● stores flags – from results of logic and arithmetic operations // interrupt flags ● contains bits – can be individually set or cleared depending on operation ● synchronises actions of other components in the CPU *based on pulses of system CU clock ● sends/receives control signals along the control bus ● manages the execution of instructions – decodes an instructions opcode during FE cycle ● controls communication between components of CPU ● types of signals it transfers: interrupt, timing, read & write System Clock ● synchronises computer operations by creating time signals ● allows operations to be processed in the correct order / sequence ● keeps track of date and time Immediate Access Store ● holds all the data/programs currently in use ● volatile memory ● has fast access times 24 How data is transferred between components ● system clock gives out timing signals – sent on the control bus, this synchronises the other system components ● CU initialises data transfer – generates signals that are sent on control bus to other components Role of Buses in Storing Data ● Address bus – carries address where data is being/going to be written to or read from ● Data bus – carries data between the devices, buffer, or components Performance ** Number of cores ● each core processes one instruction per clock pulse ● more cores mean that more sequences of instructions can be carries out simultaneously ● multiple instructions can be executed per clock pulse (individua ● decreased time taken to complete a task Why this may not increase performance ● software may not be designed for multiple cores – one core will be left idle ● memory access speed wont match speed of cores – causes delay ● may be other differences – e.g. amount of RAM Bus Width ● allows transfer of more data each time/each transfer Clock speed ● each instruction is carried out on a clock pulse ● clock speed dictates the rate at which instructions are being run ● faster clock speed = more instructions can be run per second/time period // more FE cycles per unit time Cache ● higher capacity means it can store a higher amount of frequently used instructions for fast access 25 ● fast access memory (close to CPU) ● stores frequently used instructions/data ● more cache means more instructions can be transferred faster – less swapping between RAM and cache ● prevents CPU idling while waiting for data Quantity of RAM ● more applications can reside in main memory simultaneously ● saves/decreases disk access times Ports ● purpose – to provide connection to peripherals & provide interface between computer and other devices ● ● USB // COM port – fast data transfer speeds, universal standard - 1 bit transferred at a time - Can be asynchronous or synchronous - USB-3, full duplex, otherwise, half-duplex HDMI - allows video and audio to be transferred on one cable, convenient ● VGA ● DisplayPort Fetch-Execute Cycle (Role of Registers) ● PC stores address of next instruction to be fetched + contents are incremented each cycle ● MAR holds address where data is fetched from (from which data will be read from/written into) ● MDR holds data at/from address in MAR (or data to be entered into it) ● Instruction (from MDR) is copied to CIR for decoding and execution Register Transfer Notation ** [PC] ← [PC] + 1 – address in PC is incremented MAR ← [PC] – contents of PC loaded to MAR 26 MDR ← [[MAR]] – data located in address held in MAR is copied to MDR CIR ← [MDR] – contents of MDR copied to CIR Stages of the FE Cycle ● Next address to be fetched is stored in the PC ● This address is copied into MAR, using address bus ● Instruction located in that address is copied from main memory to MDR, using data bus ● Instruction is copied from MDR to CIR ● Instruction is decoded by CIR (into opcode and operand) ● Processor executes instruction ● Address in PC is incremented Purpose of an Interrupt ● to send a signal from a device/process ● seeking the attention of the processor Causes of Software Interrupt ** ● division by zero // runtime error ● attempt to access invalid memory location ● array index out of bounds ● stack overflow ● buffer overflow Causes of a Hardware Interrupt ● printer is out of paper ● keyboard key press ● power failure Interrupts ** ● Interrupt flag raised in interrupt register ● Register checked for at start/end of FE cycle (before it begins/after execution stage) ● Type and source of interrupt identified ● Priority is checked against the current process – if lower, FE cycle continues, if higher… ● Contents of registers are stored in/moved to a stack ● Address of Appropriate ISR called to handle the interrupt (loaded to PC) 27 ● Once ISR finishes, check for further interrupts (if found, repeat cycle) ● Otherwise load data/contents from stack into registers and continue with previous process 4.2 Assembly Language Two-Pass Assembler First Pass – create symbol table ● reads assembly language instructions, adds any new symbolic addresses to symbol table ● removes comments and white space ● reads assembly language program one line at a time ● checks the opcode is in the instruction set ● adds labels to symbol table Second Pass ● generates object/machine code ● reads assembly language program one line at a time Instruction Groups ** ● data movement – moves data between addresses or other locations ● input/output of data – takes input from user, outputs char of binary num ● arithmetic operations – perform addition or subtraction ● unconditional/conditional instructions – move to another instruction ● compare instructions – compares result to another value ● all types of addressing load contents of given/calculated address into accumulator Immediate Addressing ● operand is the data Direct Addressing ● operand holds memory address of data ● addresses address given by operand Indirect Addressing 28 ● the address used is at the address the user gives ● operand holds memory address that stores the memory address of the data Indexed Addressing ● forms address from given address/address in operand plus the contents of the index register Relative Addressing ● the address to be used is an offset number of locations away, relative to the address of the current instruction ● allows for relocatable code – all target addresses can be specified by the base address 4.3 Bit manipulation Binary Shifts – moving bits in a register a certain number of places within a register ● Logical Shift – bits shifted out of register are replaced with 0s ● Arithmetic Shift – bits shifted out of register are replaced with 1s ● Cyclic Shift – no bits are lost, bits shifted out of one end appear at the other end ● Left Shift ● Right Shift Bit Masking ● AND is used to check is bit has been set ● OR is used to set the bits ● XOR is used to clear a bit that has been set 5. System Software 5.1 Operating Systems Purpose of an Operating System 29 ● to provide a user interface ● to provide a platform for software to run ● to hide complexities of hardware from user Operating System – Management tasks ● memory management ● file management ● security management ● hardware management ● input/output management ● process management ● error checking and recovery Memory Management ● controls movement of data between RAM/processor ● allocates memory to processes ● dynamically allocates memory to processes/programs How MM Allocates RAM ● RAM is assigned into blocks ● dynamic allocation of RAM to programs ● reclaims unused block of RAM ● prevents two programs occupying same area of RAM simultaneously ● moves data from secondary storage when needed (manages paging & virtual memory) File Management Tasks ● space allocated to particular files ● maintains a directory structure ● provides file naming abilities ● implements access rights ● allows file sharing ● specifies tasks that can be performed on a file (copy, paste, delete, close…) Security Management ● creates accounts/passwords ● provides firewall or anti-malware ● validates user and process authenticity 30 Hardware Management ● receives data from input devices ● sends data to output devices ● operates/installs device drivers – installs programs for devices connected to external ports ● allows communication between peripheral devices and computer ● handles buffers for transfer of data – ensures smooth transfer between devices transmitting and receiving at different speeds ● manages interrupts from device Process Management ● manages scheduling of processes – decides which process to run next // order of processes ● manages resources the processes require – e.g. allocating memory ● enables processes to share/transfer data ● prevents interference between processes ● handles process queue ● supports/allows multitasking – ensures fair access, handling priorities/interrupts Utility Software ** ● help set-up/optimise/maintain the computer ● makes memory allocation more efficient ● checks the system for faults Disk formatter – disk needs to be prepared/initialised for use ● Prepares/initialises a disk for storing files by partitioning it (generates new file system) ● Can delete all data from disc ● Sets up file allocation table ● Needs to check disk for errors Defragmentation – over time, saving and deleting small files fragments disk ● Moves/rearranges blocks of files so that each individual file is contiguous in memory ● Moves free space together ● Less time taken to access files (less head movement as data is contiguous) ● Improves disk access times – no need to search for next fragment 31 Disk repair – needed to optimise performance ● Scans for errors/inconsistencies in a disk and corrects them – prevents bad sectors being used ● Reduces access times by optimising storage Back-up (Software) – allows retrieval of data, provides security against loss ● Creates copy of data in case the original is lost (in regular intervals) ● Allows retrieval of data is any is lost/corrupted Disk/System clean up ● Optimises storage by removing unwanted files Compression software ● Reduces file size ● Saves storage and memory space ● Reduces transmission time Virus Checker ● Frees up RAM – removes software that takes up memory/replicates, scans for malicious program code Program Library ** ● contains pre-written functions and subroutines ● can be referenced or imported ● the functions/routines it has can be called in own program ● saves time as code does not have to be written from scratch ● more likely to work (it’s already tested) ● program updates automatically (if update in routine) ● can perform more complex calculations than programmer is able to do Dynamic Link Library Benefits ** ● requires less main memory as DLL is only loaded once when needed ● executable file is smaller (does not contain all library routines) ● no maintenance needed from programmer (DDL is separate from program) 32 ● no need to recompile program if changes are made to DDL (changes/improvements to DDL file code are done independently of the main program) 5.2 Language Translators ● convert a high-level or assembly programming language to a different form (usually machine/object code) Assembler ● translated assembly code into machine code Compiler ** ● translate high-level language (entire code is translated then run) ● used after program is completed ● produces error report after translating ● creates executable file – can be run without source code After Testing ● produces executable file ● user cannot access/edit/sell the code ● users do not need translator to run program ● can be compiled for different hardware specifications – generates more income ● program can be tested multiple times without need to retranslate Drawbacks when testing ● code cannot be changed without recompilation ● program will not run if there are any errors ● errors cannot be corrected in real-time ● one error may result in false errors being reported ● cannot easily test individual sections of code / cannot test if unfinished Advantages when testing ● can debug multiple errors simultaneously ● produces executable file ● developer can test program multiple times without recompiling Interpreter ** ● translate high-level language line by line (is translated then run) 33 ● used while writing a program for testing and debugging ● errors can be corrected in real time – stops when an error occurs and displays position When Testing ● allows developer to make real-time changes that can be seen immediately ● program can be debugged at each stage ● developer can test when incomplete – small parts can be tested individually, if one section does not work others can still be tested ● to avoid dependant errors Partial Interpreters/Compilers ● can be used on different platforms as they are interpreted when run ● code is optimised for CPU as machine code is generated at run time ● source code does not need to be recompiled – more efficient to run (programs may not need to be compiled if the software is already an executable file, has been pre-compiled/built using compiler or if the source code has not been provided) IDE Features/Tools ** Coding ● context sensitive prompts – as the code is being written, displays predictions/options to complete the statements, suggests additions ● auto-complete – helps programmer figure out what to type next ● auto-correct Error Detection ● dynamic syntax check – underlines/highlights syntax errors as code is being entered/in real-time Presentation ● pretty printing – helps identify key terms ● auto indentation ● expand/collapse code blocks Debugging 34 ● single stepping – allows programmer to run the code one line at a time (breaking in between) so effects of each statement on values can be seen/checked ● breakpoints – stop the code executing at a set line (to check current values/progress) ● report windows – output contents of variables and data structures (see how variables change) ● variables & expressions 6. Security, Privacy and Data Integrity 6.1 Data Security Data Security ● protects data against loss/corruption 35 ● ensure recovery Data Privacy ● ensuring data is protected against unauthorised access Data Integrity ● ensures consistency/accuracy of data and whether it is up to date ● e.g. validation/verification rules, cascading update/delete Why Data needs to be kept secure ● to protect against someone deleting/modifying or stealing it Why the computer system need to be kept secure ● to protect against someone installing malware or damaging the system/accessing data on it Measures Used to Protect Computer Systems Two factor authentication Strong username and password ● prevents unauthorised access Biometric passwords Digital signatures ● user puts message through hashing algorithm to produce a digest ● digest encrypted with sender’s private key (creates digital signature) ● message and signature sent to receiver ● receiver decrypts signature to reproduce digest – same hashing algorithm used on received document to create second digest ● signature digest and receivers digest are compared (document is authentic is they are the same) ● digital signature can only be decrypted using matching sender’s public key Firewall – accepts or rejects incoming/outgoing packets based on criteria 36 ● monitors incoming and outgoing traffic/packets – compares it to criteria set by user (checks against whitelist/blacklist/blocked IP addresses) ● blocks/rejects files or transmissions that do not match criteria, accepts ones who do Up-to-date Anti-Malware – scans files on hard drive for malicious software ● regularly scans computer for viruses, checks against stored database of viruses ● database needs to be updated regularly ● if virus detected, it is quarantined or deleted ● compares downloaded files to database of known viruses – prevents download from continuing Anti-spyware ● scans computer for spyware, checks against stored database of spyware ● database needs to be updated regularly ● if spyware detected, it is quarantined or deleted ● compares downloaded files to database of known spyware – prevents download from continuing Backups ● data can be restored in case it is damages/lost due to malware Encryption ● converts data into cipher text Access rights Threats Posed by Internet/Networks Virus/Malware ● malicious software that replicates itself ● downloaded/run without user’s knowledge ● runs in background ● can pretend to be legitimate 37 ● can damage/delete/corrupt data ● does not send data out of computer Spyware ● malicious software ● downloaded/run without user’s knowledge ● runs in background ● can pretend to be legitimate ● secretly records/collects user’s data/actions ● sends data/activity logs to third party ● does not replicate itself Hacking/Hackers ● illegal/unauthorised access used to delete/damage/collect data ● done with malicious intent Phishing – REQUIRES USER ACTION ● email pretends to be from official body ● persuades individuals to disclose private information ● requests authentication by redirecting to unofficial website Pharming – AUTOMATIC ● redirects user to a false/fake website ● prevention – check URL validity, ensure connection is secure (https) Security Methods to Protect Security of Data Access Rights ● give certain users access to different elements ● uses different accounts/logins which have different levels of access 38 ● specific views can be assigned Encryption ● data is converted into cipher text // data is encoded ● use – cannot be understood if intercepted without a decryption key 6.2 Data Integrity Validation ● checks data is reasonable/sensible ● e.g. checking data is given in the right data type when explaining use, refer to specific checks… ● format check: makes sure data is in required format ● length check: makes sure data contains correct number of characters ● type check: ensures only correct data type e.g. non-numeric data is entered ● existence check: makes sure data is already present in the system Verification ● checks that data matches the original/is accurate ● e.g. visual check (manual comparison with source document/material), double entry (enter twice, computer system compares) Reasons why data might still be incorrect ● data on original document may not be correct – verification only checks if it matches ● validation doesn’t check accuracy of data, only if it’s reasonable Parity Check (used during transfer) ● type of parity is decided upon before transfer (even or odd) ● each byte contains a parity bit In parity blocks… ● an additional parity byte is sent with vertical AND horizontal parity ● each row/column must have an even or odd number of 1s ● receiver counts the number of 1s and 0s in byte, allowing errors to be identified ● the intersection is the error 39 ● *an error cannot be detected if an even number of bits has been changed, as they could cancel each other out* Checksum (used during transfer) ● checksum value calculated from the data before transmission ● value is transmitted along with data ● receiving computer recalculates checksum from the received data ● the received checksum and recalculated checksum match, no error has occurred ● if they don’t match, an error has occurred 7. Ethics and Ownership 7.1 Ethics and Ownership Benefits of Joining an Ethical Body e.g. BCS, IEEE ● has set ethical guidelines to follow – clients/staff know standards, no decision-making required 40 ● professional integrity - clients/staff know he is reputable (shows skills/knowledge) ● they provide help and support (legal advice) ● training courses – helps to keep skills up to date Reasons to Act Ethically ● make sure team members feel valued ● maximise quality of work ● promote teamwork and cooperation ● enable creation of best product for customer How to Act in Best Interest of Client ● keep client’s personal data private ● involve client in development // communicate with client ● provide solutions the client asked for ● keep project on schedule and stay within given budget ● keep client informed of any problems/delays How to Act Ethically ● be truthful – ask for help on how to use a program ● perform your own research ● ask for additional training/mentor Being Unethical (Not acting in the best interests of…) ● product – might fail if error isn’t reported ● client – code might not work, lets down client ● profession – failing in his duties as an employee ● company Copyright ● The formal and legal rights to ownership // Intellectual property rights ● Protects against unauthorised reproduction of work ● Allows for legal right of redress Preventing Illegal Copies ● encryption ● use product key ● Compile source code (distribute as .exe file) 41 Software Licencing Free Software Foundation & Open Source Initiative ● user can edit/improve source code (must be released under same conditions as original software/same legal rights apply) ● user can redistribute the software Reason for an open source licence ● allows user to customise code ● allows errors to be reported ● allows additional features to be added to code ● allows for collaboration Reasons against an open source licence ● requires you to release source code ● allows anyone to edit/modify and share the source code/program ● doesn’t allow you to profit off the created program Shareware ● enables program to be copyrighted – user cannot legally modify it, control over product is maintained, protects intellectual property rights ● user always gets a trial period – can also gain income if bought afterwards ● user cannot redistribute the software ● cannot be edited – developed keeps control ● more people might try it – free trial allows more people to experience it, meaning they are more likely to buy it (also allows people to give feedback based on free trial Commercial Software ● user must pay before being able to legally use the software ● cannot be redistributed or edited Advantages of commercial software ● enables program to be copyrighted – user cannot legally edit it, control over product is maintained ● protects source code / prevents changes being made ● a fee can be charged for program – programmer gains income 42 ● prevents illegal copies being made – action can be taken if this occurs ● for customer – likely to have fewer bugs, redress available if game is broken, potentially better support as a fee is being charged Applications of AI ** ● police identifying wanted people – image/facial recognition (can identify features/patterns in an image and match them to a person/object) ● natural language interfaces – speech recognition (can identify language/words being spoken, can learn accents, matches words to database, generates most likely sentence) ● self-driving cars – can detect position on road (self-parking, collision avoidance, following a route) ● game playing – models characters in computer games (allows comp characters to react according to player’s movements) ● can start recording to secondary storage when person is detected ● can identify direction of movement and then move the camera accordingly ● scans scene in real time ● facial/image recognition – takes each frame individually, analyses pixels ● camera focuses on pattern identified Social impacts ● privacy issues – people do not like their data being stored ● incorrect recognition leads to mistakes (systems may be denied) ● individuals will feel safer – reduction in crime ● helps in catching criminals (links to reduction in crime) Economic Impacts ● reduces costs – less time taken for tasks to be carried out ● increases profits – leads to more efficient work performance (redundant tasks done by AI) ● decreases cost for customer ● decreases profit margins – program may be expensive to maintain/buy/update 43 8. Databases 8.1 Database Concepts Drawbacks/Limitations of a file-based approach ** ● more data redundancy – same data is stored many times ● more data inconsistency (worse data integrity) – data is not updated across the whole program and there may be duplicates that are stored differently ● hard to perform complex queries – new program has to be written each time ● lack of privacy – user views/access cannot be implemented Advantages of a relational database (compared to file-based approach) ** 44 ● reduced data redundancy – each data item is only stored once (due to linked tables) ● maintains data consistency (data integrity) – changes in one table automatically update in another ● complex queries easier to run ● can provide different views – user can only see specific aspects/parts of the database (improved privacy) ● program-data independence – programs do not need to be rewritten if data is changed (data is separate from software) Entity ● object which data can be stored about Field ● column/attribute in a table Tuple (Record) ● a single row of data in a table (about one instance of an object) Primary Key ● unique attribute – used to uniquely identify a record/tuple ● can be used as foreign key in another table // form link between the tables Candidate key ● an attribute that could be a primary key Secondary Key ● alternative/additional key used along with primary key to locate specific data (candidate key that has not been chosen as primary key) Foreign Key ● a field in one table that links to a primary key in another Importance of referential integrity ● makes sure data in the database is consistent and up-to-date 45 ● ensures that every foreign key has a corresponding primary key ● prevents records being added/modified/deleted incorrectly ● makes sure any changes made to data in one place are reflected in all related records ● ensures any queries made return accurate and complete results ● makes sure non-existent data cannot be referenced Normalisation 1NF ● no repeating groups of attributes 2NF ● has no repeated attributes ● no partial key dependencies (all attributes fully dependant on primary key) 3NF ● no transitive dependencies ● all attributes/fields fully dependant on primary key AND NO OTHER ATTRIBUTES 0NF to 1NF ● remove/identify any repeating groups of attributes ● ensure each field is atomic (e.g. Name should be split into FirstName and LastName) ● identify primary key 1NF to 2NF ● remove any partial key dependencies 2NF to 3NF ● remove any non-key dependencies 8.2 Database Management Systems (DBMS) DBMS 46 ● provides data management Data Dictionary Contents (metadata about database) // data abt data in a database ● table name // field name ● data types ● type of validation used // validation rules ● primary and foreign keys ● relationships between elements Logical Schema – shows structure of database, its relationships (e.g. E-R diagram) ● overview of a database structure ● models the problem, using methods such as ER Diagrams ● independent of any particular DBMS // model of a database that is not specific to one DBMS ● describes the relationship between data and its structure Security in a DBMS ● authentication ● backup/recovery procedures – automatically creates copies of database and stores it off-site on a regular basis, allows data to be recovered if lost ● access rights – users are given different access permissions to different tables, read/write, read only etc. ● views – different user able to see different parts of database, only see what’s required ● encryption – data is turned into ciphertext, cannot be understood without decryption key ● record and table locking – prevents simultaneous access to data, so data is not overwritten Software Tools in DBMS ● provides a developer interface - allows user to create items such as tables, forms and reports - creates input & output abilities through menus/buttons/touchscreen/monitor etc. ● query processor - allows user to enter criteria - searches for data that meets the entered criteria - organises results to be displayed to the user 47 - software that that processes and executes queries written in SQL 8.3 DDL and DML ● DDL statements – always end with a semicolon!!! CREATE DATABASE database_name; CREATE TABLE table_name( column_name1 DATATYPE column_name1 DATATYPE NOT NULL PRIMARY KEY(column_name) FOREIGN KEY(column_name) REFERENCES external_database_name(column_name) ); ALTER TABLE table_name ADD column_name DATATYPE ADD PRIMARY KEY(column_name) ADD FOREIGN KEY(column_name) REFERENCES external_database_name(column_name) DROP COLUMN column_name RENAME COLUMN old_column_name TO new_column_name; ● Data Types - CHARACTER - VARCHAR(n) – like a string, VARCHAR(255) allows 255 characters - BOOLEAN - INTEGER - REAL - DATE - TIME 48 Paper 2 9. Algorithm Design and Problem-solving 9.1 Computational Thinking Skills Abstraction ● Used to filter out unnecessary information // Means only essential information is included ● Simplifies the solution – makes it easier to implement/design ● System is tailored to need of user Decomposition 49 ● Breaking down a complex problem into smaller problems/subproblems which are easier to program ● Makes problem easier to solve ● Leads to concept of program modules – subproblems can be assigned to individual teams Benefits ● Makes task easier to understand/solve – smaller problems are easier to solve ● Smaller problems are easier to program, test and maintain ● Sub-problems can be given different teams // can be solved separately 9.2 Algorithms ● algorithm – sequence of defined steps that describe how to solve a problem Stepwise Refinement ● process of developing a modular design by splitting a problem into sub-tasks ● the sub-tasks are repeatedly split into smaller sub-tasks until each is just one statement/element from which the task may be programmed could include statements such as… ● set total/count to 0 ● input a number ● check if… ● repeat from step # a set number of times // repeat for total of # iterations ● output the total/count/element/string ● calculate the rounded value of… ● assign value to an element ● use function … to return a value ● open file in read/write mode ● loop through all lines in a file ● loop ends when… (obviously, be specific to the question, for example, say how many times it repeats and from which step) 9.3 Algorithms Continued 50 10. Data Types and Structures 10.1 Data Types and Records Defining Record Structures (using arrays of given records and type) ● declare a record – containing all data items required // containing items of different data types ● declare an array of the given record – each array element represents data for one instance of an object (e.g. would store one customer order) Advantages of Records ● a set of data of different data types is stored under a single identifier ● allows multiple instances to be referenced using the single identifier Uses of BOOLEAN ● to terminate a conditional loop when value has been found 51 ● when the variable can only take one of two possible values 10.2 Arrays ● simplify an algorithm, makes it easier to amend or add data ● are easier to understand, test and debug ● it is possible to iterate through the values using a loop – make data organisation easier ● arrays of records can store multiple data types 10.3 Files Advantages of storing data ● Data in file is saved after computer is switched off (stored permanently) ● Data does not need to be manually re-entered when program is re-run * WRITE mode overwrites a file completely/overwrites any existing data in file How to store a set of data in a file ● Data items are combined to form a single string (set of data is saved as a single line in file) ● Items are separated by a special character 10.4 Abstract Data Types Linked Lists ● Consists of nodes – each node contains data and a pointer to the next node ● Has a pointer to the start of list (start pointer) ● Last node in list has a null pointer (indicated there are no further nodes in list) ● Data is added by manipulating pointers (Data in nodes does not need to be moved) ● Nodes are traversed in sequence (based on pointers) ● Unused nodes are stored on free list Adding/inserting a new node ● check for a empty node ● assign data item to first empty node in free list (from now on referred to as X) ● set the pointer of X to point to the node that will come after it after insertion (Y) ● set pointer of node that previously pointed to Y to point to X 52 ● set pointer of free list to point at next empty node Advantages ● It is easier to add/delete data in a linked list ● Only the pointers need to be changed if data contents are changed (determine ordering of data) Disadvantages ● Pointers need to be stored as well as data ● More complex to implement/set up Implementing a Linked List ● Declare two 1D arrays – one for data, one for pointers ● Elements from same index represent one node (data in index position in array 1 maps to pointer in index position in second array) ● Declare variable for start pointer ● Declare variable for next free node pointer ● Define appropriate value for null pointer ● Use routines to add/delete/search within list Using Record/based Implementation ● Define record type with fields for data and pointer ● Declare a 1D array of defined record type Queues ● Each queue element contains one data item ● Has a pointer to the start and end of queue ● Works on a FIFO* basis ● May be circular ● Front of queue and End of queue pointers are equal when there is only one data item in the queue * first in first out – first data item put in queue is also the first one removed Adding/inserting a value ● check queue is not full 53 ● increment variable/pointer that signifies end of queue ● increment variable storing the number of items in queue ● store data value being added in location pointed to by end of queue pointer ● in arrays – set element of array at end of queue to value/item being added Removing a value ● value pointed to by the front of queue pointer is removed first – can be assigned to a variable ● front of queue pointer is incremented Required Operations ● adding an item – a check needs to be carried out to ensure queue is not full ● removing an item – a check needs to be carried out to ensure queue is not empty Implementing a queue ● Declare 1D array of required/specified size ● Declare integer variable for front of queue pointer ● Declare variable for end of queue pointer ● Declare variable for size of queue to limit max number of items allowed ● Initialise variables e.g. the size of the queue Stacks ● Used to store string data which needs to be accessed in several modules within a program Implementing a Stack ● Declare a 1D array of type string ● Number of elements in the array corresponds to the size of the required stack ● Declare variable for a stack pointer ● Declare variable for size of stack/max value of pointer ● Use stack pointer as index to array ● Initialise pointers and variables to indicate empty stack ● Store each item on stack as one array element ● Push and Pop routines used to operate stack (need to check if stack is full or empty first) 54 Why files may not appear correctly if using a stack (from O/N 2023 paper 22) ● If a multiple lines are stored at once, lines transferred to file will appear out of sequence as stacks operate on a FILO basis ● Stack is full – not all lines can be stored on stack, resulting file will be missing original lines ● Stack is empty – stack is being read faster than being written into, so blank lines may be inserted into file 11. Programming 11.1 Programming Basics Features that made codes understandable ● Indentation ● White space ● Comments ● Meaningful variable names, use of camelCase ● Capitalised keywords ● Standard way to indicate special cases (such as unused array elements) – allows recognition when processing, means there is no unexpected data Importance of ‘Good Practice’ ● makes code easier to understand, describes purpose of sections of code and of identifiers 55 ● makes code easier to debug/test and maintain Constants ● used for values that are only entered once ● avoids input error or accidental change of value ● easier to maintain program when constant has to change ● make program easier to understand Library Routines/Program Libraries ● More complex functions can be used in code through use of a program library Benefits during development ● tried and tested free from errors ● perform function you may not be able to program yourself ● readily available and speed up development time Use ● Used for tasks that are performed/repeated in several places within the code ● When part of an algorithm performs a specific task ● Reduces complexity of program ● Testing/debugging is easier 11.2 Constructs Selection constructs ● IF statement ● CASE statement (from O/N 2023 paper 21) - consists of clauses that are checked in sequence - if a value satisfies the first clause, other clauses will never be tested - the “otherwise” clause may never be performed if all possible values are addressed via the other previous clauses Iterative constructs ● WHILE pre conditional loop – used when number of iterations is not known ● REPEAT post conditional loop – used when number of iterations is not known ● FOR count-controlled loop – used for known number of iterations 56 Sequence construct 11.3 Structured Programming Functions/Procedures ● A function/procedure interface refers to the parameters and return value – e.g. a function takes two integer parameters and returns a boolean value - it provides a mechanism to allow calling a program to pass data - defines/provides parameters, giving their data type and order Benefits ● Can be called repeatedly when required ● Is only designed and tested once (then used repeatedly) ● Any changes to function code need to be made once only (easier to maintain) ● A function returns a value, a procedure can output values 12. Software Development 12.1 Program Development Life Cycle Benefits ● makes projects/programs easier to plan and manage ● clear deliverables produced at end of each stage (can show prototypes to client) Stages Analysis ● Documents produced include: the problem definition, client requirements, documentation related to current system e.g. ER diagrams ● Developer discusses program requirements with customer/client Design 57 ● An identifier table is produced ● Data structures and choice of programming language are decided ● Includes algorithms, programs and pseudocode ● User interface Coding ● Syntax errors can occur Testing ● A trace table is produced Waterfall Design ● each stage completed before new one is begun (linear) ● full documentation, lots of planning involved ● client only involved at start and end of process Benefits ● easy to manage, stages do not overlap and are completed one at a time ● each stage has clear/specific deliverables (detailed documentation of project) ● leaves little room for client to change mind and the project is planned out thoroughly, meaning a smoother development process (client also has better idea of the finished product when designing it) Disadvantages ● no working program/software until late in life cycle – slower to market than competitors (does not allow early versions) ● more difficult to cope with changes in requirements ● needs high amount of feedback/involvement from client Iterative Design ● development cycle is run repeatedly until full program has been developed ● split into stages which are repeated Benefits ● working programs developed early on in cycle, produced at each iteration 58 ● easier to test and debug ● more flexible to changes in client requirements ● customer involved during all stages/at each iteration Drawbacks ● a lot of planning needs to be done in order to section project into clear stages/iterations (whole system needs to be defined at start) ● makes it easy for client to change mind often about end result Rapid Application Development (RAD) ● modules are developed in parallel as prototypes ● minimal planning is carried out – allows for changes to requirements ● flexible development process ● used for time critical/sensitive development ● client involved during all stages of development Benefits ● quicker development possible – multiple areas worked on simultaneously ● prototype produced in early stages ● easier to change requirements ● early review possible Drawbacks ● difficult to estimate cost/time needed to complete project ● makes it easy for client to change mind often about end result ● documentation often omitted 12.2 Program Design Structure Chart Purpose ● To module relationships and see how a problem is broken down ● To determine whether a module is a function or procedure Symbols ● Curved arrow – means iteration/looping 59 ● Downward arrow – result from one stage is input/passed to next stage ● Upward arrow – more work required on previous stage to complete the current stage State-Transition Diagrams ● arrows represent transitions between states ● each arrow can have an input or an output – always in format of i|o ● X signifies start 60 12.3 Program Testing and Maintenance Types of Maintenance Adaptive ● Accommodates legislative changes or user requirement changes ● Allows program/software to be updated if new technology or library routines are made available Perfective ● Changes are made to program after it has been made available to public Corrective ● Used when program does not operate as expected // contains a bug Types of Testing Beta Testing ● testing carried out by small group of potential users ● users check that program works as intended and identify any errors present ● users will provide feedback/suggestions for improvement ● problems identified are addressed before program is sold Integration Testing ● each module in program is tested individually during development and is debugged as necessary ● individual modules are combined into single program (or added to existing program) and tested as a whole Stub Testing ● used when program contains modules with errors/incomplete modules ● dysfunctional modules are replaced by dummy modules ● dummy modules return a known/expected result or output a statement to show they have been called 61 Walkthrough Method (Required Information) ● the program code/specification – structure/design of the program needs to be known ● test data and expected results – so all paths through program can be tested How Errors are Identified ● program is checked by creating a trace table, going through program one line at a time ● records/checks variables as they change ● error may be indicated when… - variable is given an unexpected value - unexpected path through program/faults in logic of program White-box Testing ● detailed testing of how each procedure works ● tests logic of all possible paths through the program module Black-box Testing ● tests a module’s inputs and outputs Alpha Testing ● testing carried out by development team ● check program works as intended and address/identify any errors within the program before releasing it to the public Types of Errors Syntax Errors (Errors cannot be detected by examining a single line) ● Selection and iteration ● Incorrect block structure – missing keywords like ENDIF, ENDPROCEDURE ● Data type errors ● Incorrect parameter use 62 ● Incorrect brackets or misspelt keywords A program with no syntax errors… ● Obeys the rules/grammar of the programming language used ● The program will run without an error being flagged Run-time Errors ● Program performs and invalid operation ● E.g. division by zero or endless loop Test Data ● Normal – value within an acceptable range (should be accepted) ● Abnormal – value outside acceptable range (should be rejected ● Boundary/Extreme – minimum/maximum acceptable value (should be accepted) Pseudocode General Operations INPUT variable_name OUTPUT variable_name1 , variable_name1 , “...” * comments added using // * <= and >= used * <> used for not equal to 10. Data Types and Structures 10.1 Defining Records 63 TYPE record_name DECLARE field_name1 : DATA TYPE DECLARE field_name2 : DATA TYPE DECLARE field_name3 : DATA TYPE ENDTYPE Reading From Records *data from a record can be transferred to an array… DECLARE array_name : ARRAY[1:30] OF record_name *referenced similarly to 2D arrays… name of the column in record is used as 2nd index array_name[Index].column_name e.g. staff[1].EmployeeName Saving Data to Records DECLARE variable_name : record_name array_name[Index].column_name ← *value* 10.2 Arrays DECLARE 1Darray_name : ARRAY[x:y] OF DATA TYPE DECLARE 2Darray_name : ARRAY[x:y , x:y] OF DATA TYPE 10.3 Files OPENFILE file_name FOR WRITE WRITEFILE file_name, *data being inserted* OPENFILE file_name FOR READ READFILE file_name, *variable data from file is being stored in* 64 CLOSEFILE file_name * file name should always end in .txt and be written in quotation marks e.g. “filename.txt” * in exams, if given a file name as a variable, assume that is it already in the correct format and includes the .txt portion 11. Programming 11.1 Basics CONSTANT constant_name : *value* * use constants with variables that do not change throughout code, you get marks for using them instead of variables * mark scheme tends to make constant names capitalised DECLARE variable_name : DATATYPE * when declaring multiple variables of the same data type, commas can be used and only one declaration statement has to be made (e.g. DECLARE index, total, count : INTEGER) variable_name ← *value* e.g. Counter ← Counter + 1 or Counter ← 0 11.2 Constructs (all have a statement indicating end of loop/condition e.g. ENDIF) ● if statements IF <condition> THEN *enter code to be executed* ELSE *enter code to be executed* ENDIF 65 * elif does not exist in pseudocode ● case statements CASE OF variable_name condition1 : *enter code to be executed* condition2 : *enter code to be executed* condition3 : *enter code to be executed* OTHERWISE : *enter code to be executed* ENDCASE ● count-controlled loops (for loop) FOR variable_name ← *value1* TO *value2* *enter code to be executed* NEXT variable_name ● post-condition loops (repeat loop) REPEAT *enter code to be executed* UNTIL <condition> ● pre-condition loops (while loop) WHILE <condition> *enter code to be executed* 66 ENDWHILE 11.3 Structured (Functions and Procedures) ● procedure PROCEDURE procedure_name( parameter : DATA TYPE) *enter code to be executed* ENDPROCEDURE * if more parameters, use a comma to separate them * there can also be no parameters, in which case leave brackets empty e.g. parameter_name() CALL procedure_name() ● or CALL procedure_name( *value* ) if parameters function FUNCTION function_name( parameter : DATA TYPE) RETURNS DATA TYPE *enter code to be executed* ENDFUNCTION * return is used to output values e.g. RETURN variable_name Pass by Value ● a copy of the variable is passed into the module, the variable is not changed outside of the module PROCEDURE name(BYVAL parameter : DATA TYPE) Pass by Reference ● any changes made to variable within the module are permanent PROCEDURE name(BYREF parameter : DATA TYPE) 67 Paper 3 did not expect this many people asking for paper 3 notes, kinda crazy but here it is, hope it's helpful I will still add stuff but I haven’t actually covered most of the topics myself yet and don’t want to spread misinformation. sorry it took so long, simply just a girl who wanted to enjoy her summer :) 13. Data Representation 13.1 User-defined Data Types Purpose of user defined data types ● To create a new data type ● To allow construction of data types not available in a programming language (extends flexibility of a programming language) ● Constructed by the programmer 68 Composite ● Collection of data that consists of multiple elements of different (or the same) data types which are grouped under a single identifier ● Can be user-defined or primitive ● Contain more than one data type in their definition ● Includes a record, set and class/object Non-Composite ● Can be defined without referencing another data type ● Can be a primitive type available in a programming language or a user-defined type ● Contains only one data type in their definition ● Includes a pointer and any primitive/enumerated data type ➔ Enumerated Data Type – has an ordered list of all possible values ➔ Pointer Data Type – used to reference a memory location, stores addresses/memory locations and indicates the type of data stored in the memory location 13.2 File Organisation and Access File Organisation Methods Serial Files ● Files are stored (and need to be accessed) one after the other ● Files are stored in chronological order ● New records are added in the next available space – records are appended to file ● When searching – every record needs to be checked until the record is found or all have been checked Sequential Files ● Files are stored and addressed one after the other ● A new version of the file has to be created to update it ● Files are stored with ordered records – records are stored in order of the key field ● New records are inserted in the correct position ● When searching – the key field is compared and every record is checked until it is found, or the key field of a current record is greater than the one being searched for 69 Random Files ● Records are stored in no particular order within the file (there is no sequencing) ● There is a relationship between the record key and its location within the file – the location of the record is found using a hashing algorithm ● Updates to the file can be carried out directly File Access Methods Sequential Access Process (For Sequential and Serial Files) ● Records are checked linearly until the desired record is found/end of file is reached ● Starts searching for records one after the other from the physical start of the file until the record is found or the end of the file is reached ● Most suitable when data is stored in a certain order based on a field – e.g. bank stored data records in ascending order of account number Direct (For Sequential and Random Files) ● Most suitable when a record is referenced by a unique address ● Allows a record to be found in a file without other records being read – records are found by using the key field of the target record (the record’s location is found using a hashing algorithm) ● Sequential Files ➔ an index of all key fields is kept – the index is searched for the address of the file location where the target record is stored ● Random Files ➔ a hashing algorithm is used on the key field of the record to calculate address of the memory location where the target record is expected to be stored ➔ Linear probing or Search overflow can be used to find a record if it is not at the expected location Hash Value Duplicates (a calculated hash value is a duplicate of another value for a different record key) Collisions ● occurs when two values/data items in the key field for two records result in the same hash value (when passed through a hashing algorithm) ● Means the storage location identified by the algorithm may already be in use by another record – two records cannot occupy the same address 70 Process of Collision Resolution ● when storing a record – search the file/overflow area linearly, starting at the original hashed storage slot, to find the next available storage space (data item is stored in first available slot) ● when finding a record – search the overflow area linearly until the matching record key is found (if not found, record is not in file) 13.3 Floating-point Numbers, Representation and Manipulation Changing the bit allocation ● When the number of bits in the mantissa is raised, the precision/accuracy of the represented number increases – when the bit number is lowered, the accuracy is reduced ● When the number of bits in the exponent is raised, the range of possible numbers can be represented is increased – when the bit number is lowered, the range decreases Why binary numbers are stored in normalised form ● To store a maximum range of numbers in a minimum number of bytes/bits ● Normalisation minimises the number of leading 0/1s represented (Numbers whose mantissa begins with 10 or 01 are normalised) ● Maximises the number of significant bits – increases precision/accuracy when storing very small/large numbers ● Avoids the possibility of many numbers having multiple representation Storing floating point numbers ● Large numbers require a greater number of bits for the mantissa – to store larger numbers, the number of bits for the mantissa must be increased Overflow ● Occurs following an arithmetic/logical operation – result is too large to be precisely represented in the available system ● Numbers cannot be stored accurately in certain computer systems if they require more bits than is available Underflow 71 ● Occurs following an arithmetic/logical operation – the result is too small to be precisely represented in the available system (number does not have enough bits to be represented) *always refer to the loss in precision and state the number/digits would be truncated Why A Binary Number Is Sometimes An Approximation ● Real (decimal) numbers can have a fractional part ● Binary numbers have limited fractional representation (limited to powers of 2) ● Fixed length of storage means you can’t store very large/small numbers – it’s not possible to store all fractions with the level of precision that is provided Converting between denary and floating-point binary M x 2E where M is the mantissa and E is the exponent ● Floating-point binary → Denary 1. convert the mantissa into denary (using two’s complement) -128 1/2 1/4 1/8 1/16 1/32 1/64 1/128 2 1 2. convert the exponent into denary -128 64 32 16 8 4 3. use M x 2E to form the denary number 72 E.g. 01011010 x 00000100 ➔ 01011010 = 45/64 ➔ 00000100 = 4 ➔ M x 2E = 45/64 x 24 = 11.25 ● Denary → Floating-point binary 1. turn the number into a fraction ➔ 4.5 = 9/2 2. divide by 2 until the denominator > numerator ➔ number of divisions = exponent ➔ e.g. 9/2 → 9/4 → 9/8 → 9/16 = 3 divisions = 23 3. split new fraction into sub-fractions available in binary ➔ e.g. 9/16 = 8/16 + 1/16 = 1/2 + 1/16 = 01001000 hence, 4.5 = 001001000 x 00000011 in floating-point binary 14. Communication and Internet Technologies 14.1 Protocols Purpose of Protocols ● Provide a standard set of rules to enable successful data transfer ● Enables communication/compatibility between devices from different manufacturers or platforms ➔ makes communications independent of software and hardware ● If two devices with different protocols were sending messages between each other, they would not be able communicate properly Purpose of SSL and TSL protocols ● Provide communications security over the internet/network (by providing encryption) ● Enable two parties to identify and authenticate each other – allows them to communicate with confidentiality and integrity Protocol Suites 73 ● The protocols in a stack determine the interconnectivity rules for a layered network model such as the TCP/IP model TCP/IP Protocol Suite 1. Application Layer (Protocols Used) ● HTTPS – for sending/receiving/transfer of web pages and hypertext documents ● FTP – for sending and receiving files over a network/between devices (used to transfer data from server to client on the network) ● SMTP – handles sending/uploading emails (push protocol) ● POP or IMAP – handle retrieving/receiving emails from a mail server (pull protocol) ➔ Keeps the server and client in sync by not deleting the original email ● BitTorrent – provides peer-to-peer file sharing ➔ Allows sharing of files between many users connected together over the internet ➔ Allows more users to share files than a normal peer-to-peer network would ➔ Users share files directly with each other – there is no web server (all users are of equal status) 2. Transport Layer – handles packets ● Responsible for delivery of data from source host to destination host ● Breaks data into manageable packets (performs segmentation) and sends them to the internet layer ● Adds a packet header and the sequence number to the header (sequences packets) ● Controls flow of packets ● Handles packet loss/corruption – ensures data arrives error free 3. Internet Layer – handles transmission of packets ● Identifies the intended network and host ● Transmits packets to the Data Link ● Routes packets independently – through optimum route ● Addresses packets with their source and destination IP addresses ● Uses an IP address and port number to form a socket 4. Link Layer (Network Access Interface) – Handles how data is physically sent ● Ensures the correct network protocols are followed 74 ● Enables the upper layers to access the physical medium (allows communication with the network layer) ● Responsible for transporting data within the network – formats data into frames for transmission ● Maps IP addresses to MAC addresses 14.2 Circuit Switching, Packet Switching Circuit Switching ● Data is transferred using a dedicated circuit/channel and implemented at the physical layer ● Circuit is established before transmission starts & released once it ends ● Data is transferred using the whole bandwidth ● All data is transferred over the same route Use ● When a dedicated path needs to be sustained throughout a call ● Where the whole bandwidth is required or real time communication is used ● E.g. standard voice communications, video streaming, private data networks ● Suitable for long continuous communication Advantages ● Data/frames arrive in order (no time needed to reassemble packets) ● Whole bandwidth is available ● Simpler and fast method of data transfer – data is transmitted with a fixed data rate and follows the same path (means no data is lost or disordered) Disadvantages ● Nobody else can use the same circuit to transmit data even if it is idle due to the dedicated connection ● Less secure – only one route is used (easier to intercept) ● No alternative route in case of failure ● Significant cost and time required to establish dedicated connection between stations ● Bandwidth cannot be shared Packet Switching 75 ● Implemented at the network layer Use ● On digital data networks such as the internet – for sending large files that don’t need to be live streamed ● When it is necessary to overcome faulty lines through rerouting ● For secure communication and high volume data transmission ● When the entire bandwidth isn’t required ● E.g. emails, text messages, documents etc. Transferring Messages Across Internet ● A large message is split into a group of smaller chunks of equal size called packets ● Packet has a header and payload – the header contains source and destination IP addresses ● Each packet is dispatched independently and given its own route - the routing for a packet depends on the network traffic ● The packets arrive out of order and are reassembled into the original message at the destination ● If packets are missing/corrupted a resend request is sent Advantages ● Packets can be rerouted if problems arise ● More secure – harder to intercept messages ● A dedicated path does not need to be established Disadvantages ● Significant time taken to reassemble the packets at the destination Function of a Router in Packet Switching ● Router examines the packet’s header – reads the IP address of destination ● Has access to a routing table – contains info about the netmask/gateway used, available hops and the status of the routes along route ● It decides on the next hop/best route and sends the packet on its next hop Benefits ● Accuracy – Ensures accurate delivery of message 76 ● Completeness – Missing packets can be easily detected and a resend request sent to message arrives complete ● Router can detect changes in networks and send data another way, ensuring it arrives ● Allows simultaneous use of channel by multiple users ● Better security – packets are hashed and send by different routes Drawbacks ● Time delays – due to correcting potential errors in packets caused by network problems ● Requires complex protocols for delivery ● Unsuitable for real time transmission applications 15. Hardware and Virtual Machines 15.1 Processors, Parallel Processing and Virtual Machines RISC (Reduced Instruction Set Computers) ● Uses simple, fixed-length instructions, fewer instruction formats & addressing modes ● Instructions only require one clock cycle (single-cycle) ● Uses many general purpose registers and a hard-wired CPU/code ● Makes use of pipelining – executes instructions in parallel, where the output of one instruction is the input of the next ● Makes more use of RAM than cache ● Design emphasis is on software ● Processor chips require fewer transistors Pipelining ● Allows several instructions to be processed simultaneously – used to increase instruction throughput during FE cycle 77 Process ● Instructions are divided into subtasks ➔ Instruction fetch ➔ Instruction decode ➔ Operand fetch ➔ Opcode/Instruction execute ➔ Result store ● Each subtask (instruction stage) is completed during one clock cycle ● No two instructions can execute their same stage at the same clock cycle ● The second instruction begins in the second clock cycle, while the first instruction has moved on to its second subtask etc. – while one instruction is being executed, the next one can be fetched and so on… CISC (Complex Instruction Set Computers) ● Uses many instruction formats, has a large instruction set and variable-length instructions ● Makes use of different addressing modes ● Uses few registers and a programmable CPU ● Instructions may require many clock cycles (multi-cycle) ● Requires complex circuits and frequently uses cache (uses less RAM) Interrupt Handling (In both RISC and CISC) 1. The processor detects an interrupt at the start/end of the FE cycle 2. The current program is temporarily stopped and the status/contents of each register are stored on a stack 3. The appropriate ISR routine is called and executed 4. After the interrupt has been serviced the registers are restored to their original status (data is restored from the stack) Effect of Pipelining (only in RICS) ● Adds additional complexity – there could be a number of instructions still in the pipelining when interrupt is received ● All currently operating instructions are discarded except for the last one – the interrupt handling routine is applied to the remaining instruction ● Once interrupt has been serviced the processor can restart with the next instruction in the sequence Computer Architecture 78 SISD – single instruction, single data ● One processor executes a single instruction using the same data set – data is taken from a single source and only a single instruction is performed on it SIMD – single instruction, multiple data ● Processors execute the same instruction on multiple different data sets simultaneously ● Instructions can be performed sequentially (Pipelining) ● Parallel computers with multiple processors MISD – multiple instructions, single data ● Performs different instructions/operations on the same set of data ● Each processor works on the same data set independently ● Parallel computers with multiple processors MIMD – multiple instructions, multiple data ● Consists of many processors that operate asynchronously/independently ● Any processor can execute different instructions on different data sets Massively Parallel Computers ● kind of network infrastructure ● a large number of computer processors or separate computers connected together – simultaneously performing a set of coordinated computations ● communicate using a message interface (send messages between each other) Virtual Machines ● Are an emulation of a computer system (and hardware/software) using a host computer system ● Uses guest operating system for emulation Benefits ● cost saving – new system can be tried on different virtual hardware without the need to purchase the hardware ● different instruction set architectures can be emulated on a single computer 79 ● the system can crash without affecting the host machine – virtual machine provides protection to other software ● security – if a virus is downloaded on the emulated system, it only affects the VM ● more than one new computer system can be emulated – allows multiple new systems to co-exist on a single computer (multiple VMs can be used on the same computer) ● allows emulation of programs for new CS that are not compatible with the host operating system – through the use of a guest operating system ● can emulate old software on a newer system using a compatible guest OS Limitations ● cannot emulate some hardware – new hardware might have been developed after the VM was ● using the machine means extra code has to be executed and more load is put on the host computer – is less efficient, increases processing time, uses more RAM (hence has poorer performance) ● increases the maintenance expenses as both host system and the virtual machine must be maintained (is also more complex to manage & implement) ● VM may be affected by weaknesses of the host machine Roles of Host Operating System ● Is the normal OS used by the host machine ● Has control of all the resources of the host machine/computer (and can access all the physical resources) ● Provides a user interface to operate the virtual machine software ● Runs the virtual machine software Roles of Guest Operating System ● OS that runs within the virtual machine ● Controls the virtual hardware/software during the emulation – accesses actual hardware through the virtual machine and host OS ● Provides a user interface for the emulated hardware/software ● Runs under the control of the host OS 15.2 Boolean Algebra and Logic Circuits Will add stuff eventually… 80 16. System Software 16.1 Purpose of an Operating System User Interface ● hides the complexities of the computer/hardware/operating system from the user ● provides appropriate access systems for users with differing needs ● avoids complex commands involving memory locations or computer hardware ● e.g. a graphical user interface uses icons for navigation Process Management Multi-tasking ● managing execution of many programs that appear to run at the same time Interrupt Handling ● transferring control to another routine when a service is required Process States ● Running 81 ● Ready ● Blocked Process Changes ● From Running to Ready ➔ The time slice of the running process expires – there is a process with a higher priority in the ready queue (the running process gets pre-empted) ➔ An interrupt arrives at the CPU – the process running on the CPU gets preempted Scheduling – managing the processes running on the CPU ● Allows more than one task to appear to be executed at the same time (enables multi-tasking) ● Allows high priority jobs to be completed first ● Keeps the CPU busy at all times – this ensures all processes execute efficiently and reduces wait times for all processes Scheduling Routines Shortest Job First ● Short processes are executed first and followed by longer processes (executed in ascending order of CPU time required) ● Leads to an increased throughput – as more processes can be executes in a smaller amount of time Round Robin ● Each process is served by the CPU for a fixed time ● Starvation doesn’t occur – as each process is given a fixed time to be executed every round robin cycle First Come First Served ● No complex logic – each process is executed one by one ● Received processes are queued ● Starvation doesn’t occur – every process will eventually get a chance to run Shortest Remaining Time 82 Virtual Memory ● is created temporarily ● secondary storage is used to simulate additional main memory ● extends RAM – means the CPU appears to be able to access more memory space than the actual RAM available ● only data in use needs to be in main memory – data can be swapped between RAM and virtual memory as necessary Reasons for Use ● when RAM is running low – e.g. when a computer is running many processes at once ● for more efficient use of RAM – if programs are not immediately needed, they can be moved from RAM to virtual memory Paging – reading/writing blocks of data from/to secondary storage when required ● memory is divided into fixed size blocks ● dividing of memory into pages done by the operating system ● faster access times than segmentation Segmentation ● divides memory into variable sized blocks ● segment size is calculated by the compiler ● slower access times Disk Thrashing ● occurs when frequent transfers between main and secondary memory take place (when virtual memory is being used) ➔ as main memory fills up, more pages need to be swapped in and out of secondary memory ➔ this swapping leads to a very high rate of hard disk head movements ➔ eventually, more time is spent swapping the pages/data than processing it 16.2 Translation Software Interpreter ● examines source code one statement at a time ● checks each statement for errors 83 ➔ …if no error is found, the statement is executed ➔ …if an error is found, it is reported and the interpreter halts ● interpretation is repeated for every iteration in loops ● interpretation has to be repeated every time the program is run Compilation Stages Lexical Analysis ● converting a sequence of characters into a sequence of tokens Syntax Analysis ● uses parsing algorithms to interpret the meaning of a sequence of tokens ● checks code matches the grammar of the language ● syntax errors are reported ● a parse tree is produced Code generation ● converting an intermediate representation of source code into an executable form Optimisation ● minimising a program’s execution time and memory requirement Reverse Polish Notation ● Used to carry out evaluation of expressions ➔ Provides an unambiguous method of representing an expression ➔ Reads from left to right ➔ Doesn’t require brackets or rules of precedence (BODMAS) Data Structures used to evaluate in RPN ● Stack – operands are popped from stack in reverse order to how they were pushed ● Binary Tree – allows both infix and postfix to be evaluated (tree traversal) 84 17. Security 17.1 Encryption, Encryption Protocols and Digital Certificates Key Cryptography ● Ensures a message is authentic/from a trusted source ● Ensures message has not been altered during transmission ● Makes sure only intended receiver is able to understand a message ● Non-repudiation – neither sender or receiver can deny the transmission happened Asymmetric Encryption ● Provides better security – by using a pair of different keys ● One of the keys is used to encrypt the message, the matching one is used to decrypt it ● Only the public key is available to everyone, the private key is kept secret ● Is a longer process, as it is more complex ● Length of keys is longer (usually 2048 bits) Process 85 ● The receiver’s computer uses an algorithm to generate a matching pair of keys (public and private) ● The public key is sent to the sender’s computer ● The sender encrypts the document/file/data using the public key to create cipher text ● The sender’s computer sends the cipher text to the receiver’s computer – can only be decrypted using the receiver's private key Detecting Alterations ● The message, together with the digital signature, is decrypted using the receiver’s private key ● The digital signature received is decrypted with the sender’s public key to recover the digest sent ● The decrypted message received is hashed with the agreed hashing algorithm to reproduce the message digest received ● The two digests (received and reproduced) are compared – if they are the same, then the message has not been altered Symmetric Encryption ● Uses a single key which is used/shared by all to encrypt and decrypt messages ● Simple process that can be carried out quickly - risk of compromise is higher ● Length of keys is shorter (usually 128/256 bits) Quantum Cryptography ● Protects security of data transmitted over fibre optic cable ● Is a virtually unhackable encryption system Benefits ● Detects any eavesdropping (due to change in photon properties) ● Once transferred, the integrity of the key can be guaranteed – it cannot be copied or decrypted later ● More secure, longer keys can be used Limitations ● Limited range – works only over relatively short distances ● Requires a dedicated fibre-optic line and specialist hardware – is expensive 86 ● Polarisation of light may be altered during transmission through fibre-optic cable ● Lacks many vital features and has high error rates (still new and being developed) – e.g. digital signatures, certified mail etc. Private Key ● An unpublished/secret key that is never transmitted anywhere ● Has a matching public key ● Is used to decrypt data that was encrypted with its matching public key SSL/TLS use when Client-Server Communication is Initiated ● A SSL/TLS connection is initiated by an application which becomes the client ● The application which receives the connection becomes the server ● Every new session begins with a handshake ● A digital certificate is requested/sent from the client/server ● The client verifies the server’s digital certificate and obtains the server’s public key ● The encryption algorithms are agreed upon by the server and client – the symmetric session keys are then generated Digital Certification Digital Signatures ● An enquiry is made to Certificate Authority (CA) ● The enquirer sends their public key and all required information (e.g. to prove identity) to CA ● The enquirer’s details are checked by the CA – If details are verified then the public key is agreed upon ● The CA creates/issues a certificate that includes the enquirer’s public key ● Encrypting data is sent to the CA using their public key and sent by the CA using their private key How it’s produced before a message is sent ● Message is hashed using the agreed hashing algorithm to produce a digest ● The message digest is then encrypted with the sender’s private key to form the signature Digital Certificate 87 ● An electronic/online document used to authenticate the identity of a website/individual/organisation ● Typically issued by the CA ● Contains information for identifying an individual/website owner as well as a public key (Role in Creating a Digital Signature) ● Provides the public key which can be used to validate the private key associated with the signature 18. Artificial Intelligence (AI) 18.1 Artificial Intelligence How graphs aid AI ● Artificial Neural Networks can be represented using graphs ● Graphs provide structures for relationships ● AI problems can be defined as finding a path in a graph ● Graphs may be analysed by a range of algorithms e.g. Dijksta’s algorithm Purpose of A* and Dijkstra’s Algorithms ● To find the optimal shortest and most cost-effective route between two nodes based on distance/cost/timeArtificial Neural Network ● Part of AI that is meant to simulate the function of a human brain ● Key component of machine learning ● Have self-learning capabilities – enables production of better results as more data becomes available ● Can solve complex problems humans cannot/find it difficult to Artificial Neural Networks Multiple Hidden Layers in an Artificial Neural Network 88 ● Enables deep learning to take place ● Needed when the problem you are trying to solve has a higher level of complexity (requires more layers to solve) ● Enables the neural network to learn and make decisions on its own ● Improve accuracy of results – more hidden layers means more complex learning capabilities How Artificial Neural Networks Enable Machine Learning ● They are intended to replicate the way human brains work ● Weights/values are assigned between nodes – adjusted through training to give more accurate results ● The output layer provides the results ● Data is input at the input layer and is passed into the system ➔ it is then analysed at each subsequent (hidden) layer where characteristics are extracted/outputs are calculated ➔ reinforcement learning takes place through repeating the training/learning process ● Decisions can be made without being specifically programmed ● The deep learning net will have created complex feature detectors ● Back propagation (of errors) will be used to correct any errors that have been made. Deep Learning ● simulates data processing abilities of the human brain to make decisions ● uses artificial neural networks which are modelled after the human brain – structures algorithms in layers – an input layer, output layer and many hidden layers ● uses large number of hidden layers to progressively extract higher level features from the raw input (has more success) ● is a specialised form of machine learning ● trained using large amounts of unlabeled data Reasons For Use ● makes good use of unstructured data ● outperforms other methods of machine learning if the data size is large ● enables machines to process data with a nonlinear approach 89 ● is effective at identifying hidden patterns (ones that are too complex for humans to spot/are undetectable) ● can provide more accurate outcome with higher numbers of hidden layers Reinforcement Learning ● based on feedback – AI learns in an interactive environment through actions and seeing the results of each action (works through trial and error, learns through its own experiences) ● for each good action, the AI gets positive feedback, for each bad one it receives negative feedback ● Node weightings are adjusted to achieve correct outcome – the AI uses feedback to improve its performance in similar tasks Reasons for Use ● enables autonomous learning using feedback without any labelled data Machine Learning Supervised Learning ● allows data to be collected/a data output to be produced from a previous experience ● a known input and associated outputs are given – uses sample data with known outputs (labelled input data) ● able to predict future outcomes based on past data Unsupervised Learning ● helps all kinds of unknown patterns in data to be found – enables learning by allowing the process to discover previously undetected patterns on its ● only requires input data to be given ● uses any data – not trained using a right output (uses unlabeled input data) 90 19. Computational Thinking and Problem-solving 19.1 Algorithms Binary Search ● Necessary condition – the elements in the list being searching must be ordered/sorted in ascending/descending order ● The time to search a list increases with an increasing number of items in the list ● Starts in the middle of the array/list ● Works by finding the mid-point of an array/list and determines which side contains the item to be found – it discards the half of the array/list not containing the search item Process ● Find middle index/item ● Check the value of the middle index in the list ● The item searched for has been found if the index value is equal to it ● Otherwise, discard half the list that does not contain the searched item ● Repeat the previous steps until the item searched for is found, or there is only one index left in the list and it is not the item searched for Linear Search ● sequentially checks each element of the array/list until the matching element is found, or the end of the array/list is reached. ● does not require the elements to be sorted. 91 ● will usually do more comparisons of records/iterations against the target (before finding it) than a binary search ● starts at the beginning of the array/list. Binary VS. Linear Searches ● time to search increases linearly in relation to the number of items in the list for a linear search and logarithmically for a Binary search ● time to search increases less rapidly for a binary search and time to search increases more rapidly for a linear search Big O Notation ● is used to indicate the time/space complexity of an algorithm. ● Linear search → O(n) ● Binary search → O(log 2n) / O(Log n) ● O(log n) is a time complexity that uses logarithmic time – the time taken goes up linearly as the number of items rises exponentially ● O(log n) is the worst case scenario – time complexity for a binary search Performance of a sorting algorithm is affected by… ● Initial order of data ● Number of data items to be sorted ● The efficiency of the sorting algorithm Queue ● Uses FIFO data structure – data is removed in the order it is received ● Is of varying length ● Data is ‘enqueued’ and ‘dequeued’ at different ends ● Has two movable pointers Stack ● Uses FILO data structure – data is removed in the reverse order to which is it received ● Is of varying length 92 ● Data is popped and pushed onto/off a stack from the same end ● Has one movable pointer Uses of a Stack ● Recursion ● Implementation of ADTs ● Procedure calls ● Interrupt handling ● Evaluating an RPN expression Linked List Implementation ● Is a dynamic data structure (not restricted in size) ● Has freedom to expand or contract – by adding/removing nodes as necessary ● Allows more efficient editing using pointers than an array Array Implementation ● Is a static data structure, generally fixed in size ● When array is full, stack cannot be extended any further 19.2 Recursion Recursion ● A process using a function/procedure that calls itself ● Must have a base case (stopping condition) ● Must have a general case – which calls itself recursively, changes its state and moves towards the base case Why Stacks are Effective for Implementation ● Stacks have a LIFO data structure ● Each recursive call is pushed to the stack and is then popped as function ends ● Enables backtracking/unwinding to maintain the required order Translating Recursive Programming Code ● The compiler must produce object code to ➔ Push return addresses/values of local variables onto a stack with each recursive call 93 ➔ Pop return addressed/values of local variables off the stack after the base case is reached 20. Further Programming 20.1 Programming Paradigms Programming Languages/Paradigms Low-Level ● Uses the instruction set of a processor ● Makes use of different addressing modes – immediate, direct, indirect, indexed and relative Imperative ● Uses variables – changed using assignment statements, rely on an iterative/repetitive method ● Statements provide an explicit sequence of commands for the computer to perform (in the order written) – each line of code changes something in the program being run, commands update the program state Object Oriented ● Uses the concept of class, inheritance, encapsulation and polymorphism Object-Oriented Programming Terminology Properties/Attributes 94 ● the data items or data types defined in a class ● properties are set to PRIVATE ➔ enforces encapsulation (ensures they are hidden) ➔ ensures that the attributes can only be accessed by the class’s own methods Methods ● the modules (e.g. functions) in a class implementing the behaviours that act on the attributes (properties) Inheritance ● methods and properties contained in one class are reused/made available to a derived class Polymorphism ● allows methods to be redefined (take on different behaviours) for derived classes Encapsulation ● process of putting properties and methods inside a class (ensures sensitive data is hidden) together as a single unit Getter ● method that is used to return the value of a property Setter ● method that is used to update/set the value of a property Instance ● an occurrence of an object Declarative ● Instructs a program on what needs to be done instead of how to do it – specifies desired result rather than method of acquiring it ● Uses facts, rules and queries to satisfy goals ● Can be logical (states program as set of logical relations) or functional (constructed by applying functions to arguments) 20.2 File Processing and Exception Handling Exception Handling Routine 95 ● Responds to unexpected events while a program is running – prevents programs from halting unexpectedly ● Traps runtime errors ● Produces meaningful error messages Exception ● Unexpected event that occurs during the execution of a program ● Causes the program to halt execution ● Examples of Exceptions – end of file, programming/user error, hardware failure, division by zero (runtime errors)