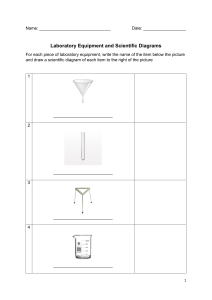
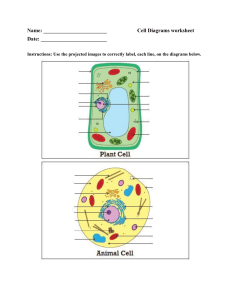
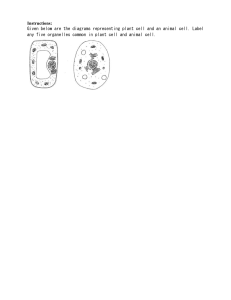
1. Executive Summary Purpose of the Report Overview of the System Key Findings and Recommendations 2. Introduction Background Objectives Scope Methodology 3. System Architecture Architecture Overview System Components o Hardware Components o Software Components o Network Components Data Flow Diagrams System Interfaces Security Architecture o Authentication and Authorization o Data Encryption o Security Policies 4. Integration Strategy Integration Objectives Integration Methods o Point-to-Point Integration o Middleware o Enterprise Service Bus (ESB) o API Management Data Integration o Data Sources o Data Mapping o Data Transformation o Data Loading 5. Implementation Plan Project Phases o Planning o Design o Development o Testing o Deployment Timeline Resources o Personnel o Tools and Technologies Risk Management o Risk Identification o Risk Mitigation Strategies 6. Testing and Validation Testing Strategy o Unit Testing o Integration Testing o System Testing o User Acceptance Testing (UAT) Test Cases Validation Criteria Issue Tracking and Resolution 7. Performance and Scalability Performance Metrics Load Testing Stress Testing Scalability Considerations Optimization Techniques 8. Security Considerations Security Requirements Threat Analysis Vulnerability Assessment Incident Response Plan 9. Maintenance and Support Maintenance Plan Support Plan Monitoring and Logging System Updates and Patching 10. Documentation and Training User Manuals Technical Documentation Training Materials Training Plan 11. Conclusion Summary of Key Points Final Recommendations Next Steps 12. Appendices Glossary of Terms Acronyms Detailed Diagrams Additional Resources