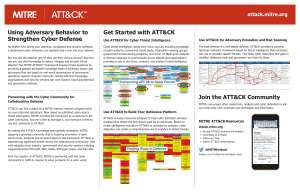
Ini�al Access Execu�on Persistence Privilege Escala�on Defense Evasion Creden�al Access Discovery Lateral Movement Collec�on Command and Control Exfiltra�on Impact Drive-by Compromise AppleScript .bash_profile and .bashrc Access Token Manipula�on Access Token Manipula�on Account Manipula�on Account Discovery AppleScript Audio Capture Commonly Used Port Automated Exfiltra�on Account Access Removal Exploit Public-Facing Applica�on CMSTP Accessibility Features Accessibility Features Binary Padding Bash History Data Destruc�on Account Manipula�on AppCert DLLs BITS Jobs Brute Force Communica�on Through Removable Media Data Compressed Command-Line Interface Applica�on Deployment So�ware Automated Collec�on External Remote Services Applica�on Window Discovery Data Encrypted for Impact Compiled HTML File AppCert DLLs AppInit DLLs Bypass User Account Control Creden�al Dumping Data Transfer Size Limits Defacement Replica�on Through Removable Media Component Object Model and Distributed COM AppInit DLLs Applica�on Shimming Clear Command History Bypass User Account Control CMSTP Domain Trust Discovery Exploita�on of Remote Services Exfiltra�on Over Alterna�ve Protocol Disk Content Wipe Applica�on Shimming Creden�als from Web Browsers Component Object Model and Distributed COM Data Encrypted Hardware Addi�ons Browser Bookmark Discovery Authen�ca�on Package DLL Search Order Hijacking Code Signing BITS Jobs Dylib Hijacking Compile A�er Delivery Bootkit Elevated Execu�on with Prompt Compiled HTML File Browser Extensions Emond Component Firmware Change Default File Associa�on Exploita�on for Privilege Escala�on Component Object Model Hijacking Extra Window Memory Injec�on Connec�on Proxy Spearphishing A�achment Control Panel Items Spearphishing Link Dynamic Data Exchange Spearphishing via Service Execu�on through API Supply Chain Compromise Execu�on through Module Load Trusted Rela�onship Valid Accounts Exploita�on for Client Execu�on Graphical User Interface InstallU�l Launchctl Local Job Scheduling LSASS Driver Mshta PowerShell Regsvcs/Regasm Regsvr32 Rundll32 Scheduled Task Scrip�ng Component Firmware Component Object Model Hijacking Create Account DLL Search Order Hijacking Dylib Hijacking DCShadow Deobfuscate/Decode Files or Informa�on Exploita�on for Creden�al Access Forced Authen�ca�on Hooking Input Capture Input Prompt Query Registry File System Permissions Weakness New Service DLL Side-Loading Private Keys Execu�on Guardrails Securityd Memory Exploita�on for Defense Evasion Steal Web Session Cookie Hooking Hypervisor Signed Binary Proxy Execu�on Kernel Modules and Extensions Signed Script Proxy Execu�on Launch Agent Source Launch Daemon Space a�er Filename Launchctl Third-party So�ware LC_LOAD_DYLIB Addi�on Trap Local Job Scheduling Trusted Developer U�li�es Login Item User Execu�on Logon Scripts Windows Management Instrumenta�on LSASS Driver Modify Exis�ng Service Netsh Helper DLL New Service Office Applica�on Startup Path Intercep�on Plist Modifica�on Port Knocking Port Monitors PowerShell Profile Rc.common Plist Modifica�on Port Monitors PowerShell Profile Process Injec�on Scheduled Task Service Registry Permissions Weakness Setuid and Setgid SID-History Injec�on Startup Items Sudo Sudo Caching Valid Accounts Web Shell Extra Window Memory Injec�on File and Directory Permissions Modifica�on File Dele�on File System Logical Offsets Gatekeeper Bypass Group Policy Modifica�on Hidden Files and Directories Data from Network Shared Drive Custom Cryptographic Protocol Data Encoding Pass the Hash Data from Removable Media Data Obfusca�on Pass the Ticket Data Staged Domain Fron�ng Remote Desktop Protocol Email Collec�on Remote File Copy Input Capture Domain Genera�on Algorithms Remote Services Man in the Browser Replica�on Through Removable Media Screen Capture Shared Webroot Video Capture Exfiltra�on Over Other Network Medium Exfiltra�on Over Physical Medium Scheduled Transfer Fallback Channels Taint Shared Content Port Knocking Security So�ware Discovery Third-party So�ware Remote Access Tools Windows Admin Shares Remote File Copy So�ware Discovery Windows Remote Management Standard Applica�on Layer Protocol Firmware Corrup�on Inhibit System Recovery Network Denial of Service Resource Hijacking Run�me Data Manipula�on Stored Data Manipula�on Mul�band Communica�on Mul�layer Encryp�on Endpoint Denial of Service System Shutdown/Reboot Mul�-Stage Channels Remote System Discovery Disk Structure Wipe Service Stop Mul�-hop Proxy SSH Hijacking System Informa�on Discovery Exfiltra�on Over Command and Control Channel Transmi�ed Data Manipula�on Standard Cryptographic Protocol System Network Configura�on Discovery Standard Non-Applica�on Layer Protocol System Network Connec�ons Discovery Uncommonly Used Port System Owner/User Discovery Web Service System Service Discovery System Time Discovery Virtualiza�on/Sandbox Evasion HISTCONTROL Image File Execu�on Op�ons Injec�on Indicator Blocking Indicator Removal from Tools Indicator Removal on Host Indirect Command Execu�on Install Root Cer�ficate InstallU�l Launchctl LC_MAIN Hijacking Masquerading Redundant Access Mshta Registry Run Keys / Startup Folder Network Share Connec�on Removal Scheduled Task NTFS File A�ributes Screensaver Obfuscated Files or Informa�on Security Support Provider Parent PID Spoofing Server So�ware Component Plist Modifica�on Shortcut Modifica�on Two-Factor Authen�ca�on Intercep�on Logon Scripts Data from Local System Custom Command and Control Protocol Hidden Window Modify Registry Setuid and Setgid Network Sniffing Internal Spearphishing Data from Informa�on Repositories Connec�on Proxy Hidden Users Re-opened Applica�ons Service Registry Permissions Weakness Peripheral Device Discovery LLMNR/NBT-NS Poisoning and Relay Password Filter DLL Path Intercep�on Password Policy Discovery Process Discovery DLL Search Order Hijacking Hidden Files and Directories Network Sniffing Keychain Launch Daemon Parent PID Spoofing Network Share Discovery Kerberoas�ng External Remote Services Disabling Security Tools Network Service Scanning Permission Groups Discovery Emond Service Execu�on XSL Script Processing Hooking Control Panel Items Creden�als in Registry Image File Execu�on Op�ons Injec�on Image File Execu�on Op�ons Injec�on Windows Remote Management File System Permissions Weakness Creden�als in Files File and Directory Discovery Clipboard Data MITRE ATT&CK Enterprise Framework ® Port Knocking Process Doppelgänging Process Hollowing Process Injec�on SIP and Trust Provider Hijacking Redundant Access Startup Items Regsvr32 System Firmware Rootkit Systemd Service Rundll32 Time Providers Scrip�ng Trap Signed Binary Proxy Execu�on Valid Accounts Signed Script Proxy Execu�on Web Shell Windows Management Instrumenta�on Event Subscrip�on Winlogon Helper DLL SIP and Trust Provider Hijacking Regsvcs/Regasm attack.mitre.org So�ware Packing Space a�er Filename Template Injec�on Timestomp Trusted Developer U�li�es Valid Accounts Virtualiza�on/Sandbox Evasion Web Service SOLVING PROBLEMS FOR A SAFER WORLD XSL Script Processing © 2020 MITRE Matrix current as of February 2020