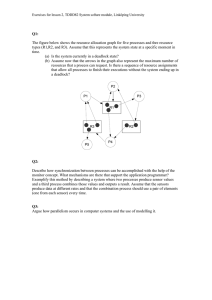
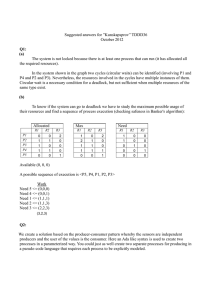
Priority Inversion: Priority inversion occurs in a real-time operating system (RTOS) when a higher-priority task is blocked because a lower-priority task holds a shared resource (e.g., a mutex or semaphore) that the higher-priority task needs. The problem is exacerbated if a medium-priority task, which does not need the shared resource, preempts the lower-priority task, thereby delaying the execution of the higher-priority task. Example Scenario: 1. Low-Priority Task (L) acquires a mutex. 2. High-Priority Task (H) becomes ready to run and tries to acquire the same mutex, but it gets blocked because L holds it. 3. Medium-Priority Task (M) preempts L and runs, preventing L from releasing the mutex. 4. H remains blocked until M finishes and L can run to release the mutex. Mitigation Strategies: 1. Priority Inheritance: o When L acquires the mutex needed by H, it temporarily inherits the higher priority of H. This prevents M from preempting L, ensuring L can run to release the mutex promptly. o Once L releases the mutex, it returns to its original lower priority. 2. Priority Ceiling Protocol: o Each shared resource (mutex) is assigned a priority ceiling, which is the highest priority of any task that may lock it. o When a task locks a resource, its priority is immediately raised to the ceiling priority, preventing any higher-priority tasks from preempting it. o This prevents priority inversion by ensuring that no intermediate priority task can preempt the task holding the critical resource. 3. Mutex with Timeouts: o Implementing mutexes with timeouts allows tasks to wait for a mutex for a specified period before taking alternative actions. o This can help avoid indefinite blocking but requires careful design to handle the timeout scenario effectively. 4. Avoiding Resource Contention: o Design the system to minimize the need for shared resources. Use lock-free data structures or minimize the critical sections to reduce the duration for which a resource is held. o This can be achieved by careful analysis and refactoring of the system's concurrency model. 5. Real-Time Scheduling Algorithms: o Use advanced scheduling algorithms like Earliest Deadline First (EDF) or Rate Monotonic Scheduling (RMS) to manage task priorities and resource access more effectively. Example Application: In an automotive Battery Management System (BMS), suppose a high-priority task is responsible for critical safety checks, and a lower-priority task handles non-critical logging. If the logging task locks a resource needed by the safety check task, priority inversion could occur, potentially delaying the safety checks. By applying priority inheritance, the logging task would inherit the higher priority when it locks the resource, ensuring the safety check task can proceed without undue delay. Conclusion: Mitigating priority inversion is crucial in real-time systems to ensure that highpriority tasks meet their deadlines. Employing strategies like priority inheritance and priority ceiling protocols can significantly enhance the reliability and predictability of an RTOS-based system.