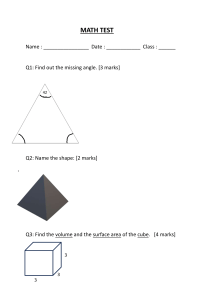
HAMPTON SCHOOL INFORMATION TECHNOLOGY COMPUTER MISUSE MONTHLY TEST Date: ________________________________ NAME:________________________________ FORM:__________ DURATION:1 hour Instruction: Multiple Choice -Choose the best answer to each question ( 10 marks) 1. The process of scrambling messages at the sending end and unscrambling them at the receiving end is called: a. Coding b. Espionage c. Encryption d. Eavesdropping 2. An official of Company X sells confidential information about his company to Company Y. What is the term used for this type of information misuse? a. Identity theft b. Computer fraud c. Industrial espionage d. Electronic eavesdropping 3. Unauthorized, real-time interception of private communication on a computer network is referred to as: a. Propaganda b. Identity theft c. Industrial espionage d. Electronic eavesdropping 4. The introduction of communication by means of means of computers has REDUCED the employment opportunities of which of the following groups of workers? a. Messengers and Postal Workers b. Analysts and Programmers c. Software Testers and Trainers d. Web Masters and Developers 5. The illegal copying and selling of programs is referred to as: a. Propaganda b. Software piracy c. Computer fraud d. Industrial espionage 6. What is the main purpose of propaganda on social media? a. Propagate good personal security b. Profile a user with the intention to steal their identity c. Influence persons to adopt an idea d. Bully or embarrass a person 7. Which of the following operations is considered a feature of a biometric system? a. Matching fingerprints b. Detecting irregular heartbeats c. Diagnosing medical symptoms e. Lubricating skeletal joints 8. Which of these is NOT an element of computer risk assessment? a. Vulnerability b. Threat c. Decision d. Attack 9. Music piracy is an example of computer misuse. To which category of computer misuse does music piracy belong? a. Identity theft b. Phishing attack c. Data theft d. Copyright infringement 10. What best describes a malicious program on a computer system? a. General-purpose program b. A system program c. A virus program d. A utility program SHORT ANSWER QUESTION (marks) 11. (a) Define the term ‘computer vulnerability’. (2 marks) ________________________________________________________________________ ________________________________________________________________________ ________________________________________________________________________ (b) Complete the table by classifying EACH of the following vulnerabilities as an internal source or an external source. (4 marks) Vulnerability Natural disasters such as floods, hurricanes, and earthquakes. Employees erroneously erasing or overwriting data Lack of anti-virus software to scan email attachments. Source Damage to hardware and software from electrical power surges and spikes. (c) Computer users can be the greatest threat to a company’s computer security. State TWO examples of strategies used to mitigate threats from users. (2 marks) ________________________________________________________________________ ________________________________________________________________________ ________________________________________________________________________ ________________________________________________________________________ (d) Distinguish between the terms ‘computer security’ and ‘cybersecurity’. ( 4 marks) ________________________________________________________________________ ________________________________________________________________________ ________________________________________________________________________ ________________________________________________________________________ ( e) Criminals acquire credit and debit card details from unsuspecting people and use this information to make fraudulent purchases and cash transactions. (i) State the term used to describe the scenario above. (1 mark) ______________________________________________________________ (ii) Outline TWO appropriate methods which can be used to prevent the scenario above. ( 2 marks) ______________________________________________________________ ______________________________________________________________ 12. Match the following professions with their description. (5 marks) Professions: Network Engineer, Computer Programmer, Computer Support Specialist, Social Media Specialist, Web Developer ANSWER DESCRIPTION Writes programs based on specifications, prepare documentation and maintains existing software. Responsible for planning and implementing social media strategies for company’s. Assist users who have problems with their computer systems. Takes a web design from a client and turns it into an operational website. Responsible for designing and implanting computer networks (LAN, MAN, and WAN) 13. Question 13 is based on the items shown below as Figures 1-3. The items shown are countermeasures used by a small business to keep its computer system. ( 2 marks) (a) State which of the items displayed are: (i) A physical countermeasure _____________________________________________ (ii) A software countermeasure _____________________________________________ b. Outline how EACH item may be incorporated into a strategy to minimize data theft from a computer located in an office accessible by all employees. ( 6 marks) ______________________________________________________________________________ ______________________________________________________________________________ ______________________________________________________________________________ ______________________________________________________________________________ ______________________________________________________________________________ ______________________________________________________________________________ ______________________________________________________________________________ ______________________________________________________________________________ ______________________________________________________________________________ ______________________________________________________________________________ ______________________________________________________________________________ TOTAL MARK 38 ALL THE BEST!!!