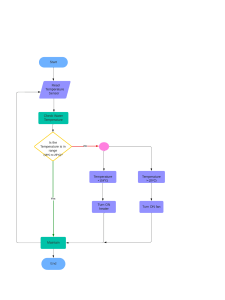
TABLE OF CONTENTS Candidate’s Declaration i Acknowledgment ii Table of Contents iii List of Figures iv List of Tables v List of Abbreviations vi-vii Abstract 1 Chapter 1: Introduction 2 1.1 Introduction to WSN 2-4 1.1.1 Wireless Sensor Network Constraints 4-6 1.2 Security Requirements in WSN 6-8 1.3 Security Attacks on WSN 8-15 1.4 Miscellaneous Attacks in WSN 15-16 Chapter 2: Literature Survey 17-28 Chapter 3: Present Work 29 3.1 Problem Formulation 29 3.2 Objectives 29 3.3 Research Methodology 29-30 3.4 Phase of Detection and Isolation of malicious nodes 32-34 Chapter 4: Examination Result 35 4.1 Network Simulator 35-38 Chapter 5: Conclusion and Future Work 51 5.1 Conclusion 51-52 References 53-58 APPENDIX 59 LIST OF FIGURES 1 Figure 1.1: Wireless Sensor Network 2 Figure 1.2: Component Node of a WSN 4 Figure 1.3: Software Requirement Analysis 9 Figure 1.4: Attacker receive packets 10 Figure 1.5: Wormhole Attack 10 Figure 1.6: Sybil Attack 11 Figure 1.7: Denial of Service Attack 14 Figure 3.3: Flowchart 31 Fig 4.1: Network Simulator 2 35 Fig 4.1 (a): Network Deployment 38 Fig 4.1 (b): Network Deployment 39 Fig 4.2 (a): Data Aggregation 40 Fig 4.2(b): Data Aggregation 41 Fig 4.3(a): Trigger attack 42 Fig 4.3(b): Trigger attack 43 Fig 4.4(a): Deployment of Sensor nodes 44 Fig 4.4(b): Deployment of Sensor nodes 45 Fig 4.5: Detection of malicious nodes 46 Fig 4.6: Malicious node isolation 47 Fig 4.7: Packet loss comparison 48 Fig 4.8: Energy Comparison 49 Fig 4.9: Throughput Comparisons 50 List of Tables Table 4.1: Simulation Parameters 36 2 ABSTRACT WSN is a self-arranging network without any centralized control. The sensing devices are commonly identified as nodes. These nodes are extremely small in size and quite inexpensive. Primarily, these networks were merely installed in the military areas for monitoring the activities of conflicting sides. Every movement of enemy was monitored and then the system used this significant information for taking suitable measures. In some applications, monitoring of suspicious actions and movements is extremely complicated because of the broad regions. Therefore, the exploitation of wireless sensor networks is extremely useful in these kinds of applications. Nowadays, wireless sensor networks are being used in various applications. These networks can perform several tasks like sensing, processing and sharing of information inside the areas. The wireless sensor network deploys the monitoring area for the random distribution of sensor nodes within the area. Wireless sensors networks are installed in such regions which are not appropriate and do not need any kind of infrastructure. The deployment of approximately hundreds to thousands sensor nodes is required for the accomplishment of required operation. As wireless sensor networks are heterogeneous, therefore the study of their deployment way within several areas is extremely significant. Security and power expenditure are the main concerns of WSN owing to these properties. The attacker nodes which make their entry inside the system launch the security intrusions. These safety intrusions are widely categorized into two sorts of intrusions, identified as active and passive attacks. Sinkhole intrusion comes in the category of active intrusion. In this kind of intrusion, attacker node spoofs the identity of base station and behaves like base station itself. The sensor nodes start sending information to the attacker node in the place of base station. In this investigate study, a new algorithm is introduced for the discovery and segregation of attacker nodes from the network. The new scheme is based on the identify confirmation. The presented algorithm is implemented in Network Simulator 2 and outcomes are scrutinized on the basis of several factors. It is scrutinized that presented approach shows better performance on every parameter in comparison with the obtainable schemes. 1 Chapter 1 Introduction 1.1 Introduction to WSN The wireless sensor network (WSN) includes as a combination of various sensing devices or nodes for getting the information about the contiguous situations of a particular area. The sensing devices also identified as nodes are extremely small and inexpensive. Primarily, these networks were merely installed in the military areas for monitoring the activities of conflicting sides [1]. Every movement of enemy was monitored and then the system used this significant information for taking suitable measures. In some applications, monitoring of suspicious actions and movements is extremely complicated because of the broad regions. Therefore, the exploitation of WSNs is extremely useful in these kinds of applications. Nowadays, WSNs are employed to serve many purposes. These networks can perform several tasks like sensing, processing and sharing of information inside the areas. The wireless sensor network deploys the monitoring area for the random dispersal of sensor devices within the area. Because of the broad and unfriendly applications of these networks, several issues raise. 2 Fig1.1 WSN As a result of small size, these sensor nodes contain only limited battery energy. These networks are positioned in subversive applications. The activities of these regions cannot be monitored because of their inaccessibility for human beings. The nodes deployed in these kinds of areas are more costly than the nodes deployed in worldly regions. The multimedia sensor networks install various microphones and cameras inside them with inexpensive sensor nodes. Larger bandwidth, power and quality of service are some important factors necessary for the appropriate processing of information. In auditory areas, sensor nodes are placed for the deployment of networks in order to create sparse environment. The wireless sensor network faces several constraints such as signal fading, delay and propagation [2]. Wireless sensors networks are installed in such regions which are not appropriate and do not need any kind of infrastructure. The deployment of approximately hundreds to thousands sensor nodes is required for the accomplishment of required operation. As wireless sensor networks are heterogeneous, therefore the study of their deployment way within several areas is extremely significant. The sensor nodes installed inside the wireless sensor networks perform various kinds of tasks. The proper distribution of network within the definite region is necessary for the collection of 3 information. In order to perform general scrutiny, the monitoring of such regions is imperative in mutual way for the collection of whole applicable information [3]. Aggregation and base station are the two significant mechanisms occurring inside the wireless sensor networks. The data is gathered from the sensor nodes present around the areas. This data is transferred to other nodes. These nodes forward this information to the dominion. The base station is identified as a component through which all gathered information is deceased. The base station is accountable for the further transmission of data. The information sharing carried out inside wireless sensor networks is defenseless and not confidential. This is due to the fact that these networks are positioned in hazardous areas with only minimum amount of reserves. The employment of security practices inside these networks is very tricky. But security is extremely imperative for the proper processing and transmission of data. Because of their properties, these networks face several issues in terms of security. Figure 1.2: Component Node of a WSN. Within a sensor node, five main units are involved named as memory transmitter or receiver, power or energy unit, sensing unit and embedded processor. These units are integrated in the sensor nodes according to the type of conditions in which these networks are to be positioned. The location recognition scheme is utilized for localizing the node’s location. Within the sensor nodes, a power generator is provided for providing energy to the battery. This scheme increases the life span of network. In these networks, a mobilize also remains present for the movement of 4 sensor nodes. Two sub-units named as sensor and analog-to-digital converter are integrated for the creation of sensing components. The sensor node senses the analog signal. Additionally, ADC component transforms analog signal into digital signal for processing. Processing unit works on these signals for proper functioning. The sensing device is connected to the network with the help of a transceiver component. The most vital component of a sensing device is battery. The battery provides energy for the activation of sensor nodes. 1.1.1 Wireless Sensor Network Constraints A wireless sensor network is generated with the help of resource-controlled based sensor nodes mutually, despite of the fact that these networks comprise restricted processing ability and storage potential. In these networks, the bandwidth is provided according to the available resources [4]. These networks are experiencing various problems because of the energy scarcity and mini sensing devices. Within these networks, the execution of security techniques is extremely difficult because of these restraints. Several restraints of sensor nodes should be considered for ensuring the development of traditional security algorithms. Several most imperative restraints being noticed in wireless sensor networks are described below: i. Power Restraints: Power restraint is the main imperative restraint of WSNs. The three wider classifications on the basis of power consumption with the help of some mechanisms are given below: ● Sensor transducer uses definite amount of power. ● The sensor nodes consume certain amount of power for information sharing. ● The microprocessors perform calculations. These microprocessors need power as well. Each bit travelling within the network utilizes approximately 800 to 1000 instructions of energy. Therefore, the cost of power for information sharing is higher than the calculation cost. If message size increases because of the security schemes then definite amount of cost has to be paid. The cryptographic functions consume large quantity of power for increasing the security 5 range of networks. Thus, in these networks, a number of security levels remain present according to the required power. ii. Memory limitations: A small sized device comprising restricted amount of memory and storage space is identified as sensor node. The sensor node’s memory involves a flash memory and RAM within it [5]. Mostly downloaded application code is amassed in this memory. The RAM amassed within the application programs, sense information and performs computations rapidly. The complex algorithms cannot be executed after the complete loading of operating system and application code due to the unavailability of storage area. Therefore, the accessibility of numerous security algorithms to these sensor nodes is imperative. iii. Unreliable communication: The untrustworthy information sharing is the other main constraint being faced by these networks. Link less protocols are the base of Packet-based routing. Thus, intrinsically, the routing is extremely untrustworthy in these networks. The fault scan occur or the packets can be dropped due to the extremely congested sensor nodes. This results in the disruption of whole information present inside the packets. These packets can be either damaged or disrupted because of the untrustworthy wireless information sharing tunnel of these networks. A number of vigorous fault management techniques are used in these networks due to the occurrence of large fault rate. The execution of these techniques increases network overhead. The presence of these kinds of faults results in the un-trust worthy exchanges with in the network even in the occurrence of a trustworthy channel. Packet collisions may occur. These packets can be retransmitted because of the broadcasting scenario of these networks. This causes issues of some other extent. iv. Higher communication delay: In these networks, larger latency happens due to multi-hop routing, congestion and processing during the transmission of packets through intermediary nodes. Thus, in these networks, synchronization is not possible. A lot of concerns may rise at security level during synchronization as the sharing of significant event reports and cryptographic key affect the performance of some techniques [6]. 6 v. Unattended operation of networks: Within the network, some nodes are not attended as a result of positioning of WSNs in hazardous situations. Therefore, in these conditions, a physical intrusion may occur. The distant managing schemes cannot practically observe any type of objective interference being reasoned in the network as these networks are positioned in hugely spread areas. Thus, the deployment of a safe wireless sensor network is extremely complicated. 1.2 Security Requirements in WSN Security of WSNs is extremely essential. For this purpose, some necessities should be kept in mind. The sensor node needs several kinds of surrounded resources inside it for ensuring the complete safety of extremely responsive information. The performance keeps this network lively. A malicious node can easily trigger attack within these networks because of some susceptibilities and occasions. The clients can go through huge loss because of these attacks. A. Data Confidentiality This property can be described as a procedure using which data can be concealed absolutely and does not remain visible to opponents. The information can be made absolutely imperceptible by a secret key for the encoding of information. Merely authorized users can assist in the importation of information. A number of essential dynamics related to the secrecy are needed to be considered in WSN. B. Data Authentication Data verification is the mainly considered aspect meant for several applications of WSN. Here, any types of illegitimate elements can be blocked. At the same time, the authentic nodes pay attention to identify any types of illegal nodes or clients. The attainment of information from a precise source is necessary. Also, the target must be guaranteed to be a fraction of communication for assuring that the information is not transmitted to any illegal users[7]. C. Data Integrity 7 This property can either adjust or transform the information. Thus, it should be ensured that the illegal customers cannot modify the recipients during information sharing. The property which ensures that no modifications are made in the data is identified as data integrity. D. Data Freshness This attribute describes the newness of information presented in the network. In some occasions, earlier accessible information is retransmitted within the network, for avoiding these kinds of situations, data freshness is measured. The newness of information should be maintained even in the presence of essential and secret information. This feature also guarantees that the attacker user is not retransmitting the accessible information. E. Access Control This property ensures the inaccessibility of information to illegal consumers. This feature does not allow any type of illegal interference within the network. F. Availability The whole cost of networks is enlarged due to the modification of conventional encoding algorithms within WSNs. As a result of existence of several techniques, the modification of code is required so that it can support the code reutilization. Also, some techniques require further interaction for the attainment of objective. For the simplification of algorithms, limited amount of approaches has been presented. But these techniques decrease the range of node accessibility. A number of factors can affect the accessibility and some of them are given below: ● The energy consumption is increased due to the further processing involved in the network. The information is lost from the network after the absolute utilization of power. ● Power utilization increases because of the existence of supplementary information sharing processes. The probability of collision increases due to the execution of huge amount of messaging. 8 ● A single point is provided in the network due to the availability of centralized method within the network. Thus, during the availability of network, a number of intimidations arise. Thus, when the intrusion occurs in network functions, the network can be made obtainable. Therefore, several security means are introduced in these networks. 1.3 Security Attacks on WSN WSNs are dissimilar from other networks due to their extremely exceptional features. The possibility of intrusions within these networks is high as well [8]. The susceptibility and receptiveness of these networks to other security threats is extremely high as they comprise distributive information sharing. The triggering of intrusion is higher in these networks because of their deployment in higher and hazardous areas. A number of intrusions may occur at different layers of the network as all these layers perform in dissimilar way and execute dissimilar operations. In these networks, a number of routing protocols are involved which do not comprise any security mechanism. Thus, the malicious can easily break the security of these networks. Different kinds of attacks or intrusions recognized in every layer of the network are given below: a. Physical layer attacks i. Congestion: As the radio frequencies experience intrusion within the sensor nodes, this result in the generation of a direct attack named as congestion. This kind of intrusion is totally different from the usual radio broadcasts the networks experience number of issues. The denial-of-service circumstances are experienced within the network due to the incidence of this kind of intrusion. ii. Tampering: This kind of intrusion conciliates the node absolutely. There is vast chance of this kind of intrusion. This attack causes extremely hazardous affects. This attack modifies the sensor nodes. The occurrence of this attack can destroy the whole network. B. Link layer attacks 9 i. Collision: This intrusion occurs when the channel intercession experiences neighbor-to-neighbor information sharing inside the link layer. The whole packet disrupts when collisions happen in any area of the positioned network. Thus, in this situation packet should be transmitted again due to the occurrence of single bit error. ii. Exhaustion: The occurrence of interrogation intrusion exhausts the battery power. The power consumption is extremely high in this situation due to the retransmission of packets. This causes absolute battery consumption of sensing devices [9]. C. Network layer attacks i. Hello flood attack: Higher communication energy is necessary for the transmission of hello packets so that adjacent can be revealed during this kind of intrusion. The malicious creates a delusion inside the network which depicts that a node is neighbor of other nodes. Thus, the incorporated routing protocol will be absolutely interrupted and larger number of intrusions may occur at this time. The malicious utilizes hello packet as a mace so that the sensor nodes present in the networks show faith on the attacker node. The attacker node comprises elevated radio communication rage and processing energy because of which different sensor nodes obtain hello packets. These nodes are partitioned in big regions. The sensor nodes suppose the opponent to be their adjacent node. The nodes will get a hello message from the attacker node and start exchanging extremely responsive information a done another. Figure 1.3: Attack broadcast packets 10 Figure 1.4: Attacker receive packets ii. Wormhole attack: In the networks, a low-latency connection is established so that the packets can be forwarded from to other end quickly using multi-hops. This process launches wormhole attack or intrusion within the network [10]. This intrusion is a big danger for any routing protocol accessible within the network. The detection and prevention of this kind of intrusion is extremely difficult. The wormhole depicts that the node that is though extremely distant, is extremely close to its adjacent, which is an attacker. This may produce perplexed circumstances within the network. The commencement of information sharing at this time will result in the exchange of secret data to the attacker nodes. Fig: 1.5 Wormhole Attack 11 iii. Sybil attack: A malevolent utilizes an attacker node for creating interference in the network’s traffic. Therefore, a number of units are established in the network which causes Sybil attack. An ID is created due to the generations of false accompaniments or due to the generation of replica of previously existing legal identities [11]. Sybil intrusions make their target to the multi-hop routing with the error tolerant techniques of sensor networks. A legitimate node produces several identifies. One or more nodes of the network can use these identifies because of this kind of intrusion. A distinct node therefore creates the numerous identities. Figure 1.6: Sybil Attack The occurrence of this kind of intrusion inside the network disrupts the reliability, safety and resource consumption. An outsider node can cause any kind of Sybil intrusion. The network having either verification or encoding method inside it can be prevented from this kind of intrusion merely. Because of the occurrence of this kind of interior malicious, public key cryptography is implemented. But the structures are extremely expensive in such case when resource relied networks are positioned. The possibility about the occurrence of Sybil node within the network can be measured with the help of the equation given below as: 𝑃𝑟(𝑑𝑒𝑡𝑒𝑐𝑡𝑖𝑜𝑛) = 1 − 𝑃𝑟(𝑛𝑜𝑛𝑑𝑒𝑡𝑒𝑐𝑡𝑖𝑜𝑛) = 1 − (1 − 𝑃𝑟(𝑛𝑜𝑛𝑑𝑒𝑡𝑒𝑐𝑡𝑖𝑜𝑛) 𝑟 1𝑟𝑜𝑢𝑛𝑑 𝑟 ) 1𝑟𝑜𝑢𝑛𝑑 12 ( = 1− 1 − ( )( )( ) 𝑆−(𝑚−𝑀) 𝑐 ( ) 𝑎𝑙𝑙𝑆,𝑀,𝐺 ∑ 𝑠 𝑆 𝑚 𝑀 𝑛 𝑐 𝑔 𝐺 ) iv. Sinkhole attack: Because of the occurrence of this kind of intrusion within the network, the base station cannot attain absolute and precise sensing information from the network. This generates a solemn danger in the higher-layer applications. In this situation, the malicious draws whole traffic from the network in its direction. The attacker node looks extremely eye-catching the another nodes [12]. During the occurrence of sinkhole attack within the network, the base station is not able to obtain accurate sensing information. Therefore, the higher layer applications experience a big threat because of this intrusion. The attacker node makes itself more eye-catching in comparison with other sensing nodes because of which whole sensed information is transferred in its direction. A sinkhole generates during the existence of attacker in the middle. The attacker node draws the data existing inside the adjacent nodes. Therefore, each bit of information is shared amid the adjacent nodes is snooped in this situation. The compromised node is made to appear extremely eye-catching regarding the used routing algorithm. Therefore, the information is promoted in the direction of this node crosswise the network. For establishing a high-quality path in the direction of base station such as the malicious can interfere in the network. D. Transport layer attacks i. Flooding Attack: This kind of intrusion is produced when large number of information is flooded across the entire system. Flooding refers the incessant getting of various packets. The higher processing of authentic link requests is executed for starting the unfinished link requests. These kinds of numerous links are created with the help of memory buffer because of the flooding which cannot be completed. The additional links cannot be established after the complete loading of buffer. This situation causes Denial of Service attack. E. Application layer attacks 13 i. Denial-of-Service (DoS): The functionality of sensor network is totally disrupted in a case when an adversary produces a planned intrusion identified as denial of service intrusion. A number of definite restrictions are caused in the performance of sensor network because of the incidence of this kind of intrusion. This attack can occur in any one of the OSI layers [13]. Whole resources can be consumed for destructing the arrangement of framework. Denial of service intrusion absolutely disrupts the network’s competence. In this situation, network components are disrupted physically because of this intrusion. Additionally, this intrusion destroys the wireless communication as well. This intrusion produces noise, collision or intervention at the receiver’s end. The malicious comprises definite targets to be focused on amid which few are related to the framework of network, server applications and the network entrance. The sufferer node sends the additional un-needed information in denial of service intrusion. In this case, the network resources are drained because of which clients cannot access the services absolutely. In few circumstances, the malevolent completely destroys the network. This adversary absolutely obliterates the capability of a network to execute definite operations. This kind of intrusion may probably happen in different network layers. Congestion and interference occurring inside the physical layer are denial of service kinds of intrusions [14]. Collision, collapse and injustice are noticed within link layer which belong to this category as well. In transport layer, flooding and de-management take place because of this kind of intrusion. For making certain that DoS intrusions do not exist within the network, it is imperative to pay the network resources and validate the traffic necessities. A number of approaches have been presented for securing the reprogramming procedure [15]. The network uses the verification inside itself for making it safe. 14 Figure 1.7: DoS Attack DoS intrusion gives an option for rekeying the request packet. Therefore, this intrusion is probable when two successive keys are nullified in the nodes or keys. Denial of service intrusion occurs because of the repeated rate of rekeying of requests. The packets are dropped in a constituted time span from the nodes. Packets are retransmitted and denial of service intrusion commences after the identification of re-keying request packet [16]. ii. Cloning attack: This kind of intrusion occurs when sensor nodes can be captured and compromised without difficulty. The limitless clones are generated for the compromised nodes in this situation. Now, all the duplicates can participate very easily in any of the tasks because of their legal access within the network. A number of internal intrusions are generated in this case and destroys the whole network. When the network is not able to recognize the secure node, then in this situation, the malicious can easily makes its entry within the network. Therefore, several other intrusions may also get the access of network. Therefore, an effectual and proficient solution should be executed within the network for the prevention of these types of intrusions. This will provide safe atmosphere for information sharing. 1.4 Miscellaneous Attacks in WSN a. Energy drain attack Several batteries are used to provide energy within the networks. The networks are deployed in a dynamic way. The recharging or replacement of nodes is imperative after the complete exhaustion of their battery power [17]. In case of battery energized networks, the fixed amount of power is drained. The intrusions may possibly occur in such a case when the attacker node sends the packets continuously. This process totally destroys the sensor nodes and degrades the network’s functionality. The network grid is completely partitioned and a novel sink node is 15 added for handling the component of sensor. The enrooted reports are dropped in this situation to minimize the harm of this intrusion. B. Data Integrity Attack The information requiring transmission across the nodes is compromised because of the changes created in the information. These changes are presented within the packets because of the accumulation of fake information [18]. The malicious node comprises advanced processing memory and energy in comparison with other nodes. The sensor information is snooped according to the purposes of intrusions. This compromises the discovery of sufferer node. The routing information is falsified for disrupting the usual function of sensor network. Thus this attack destroys the network totally. Asymmetric keys are implemented for the prevention of these kinds of intrusions. These keys provide encoding as well. C. Sniffing attack Any interference or eavesdropping occurring within the channels is the reason of this kind of intrusion. The attacker node is placed in the neighbor of sensor grid for the capturing of information. The gathered information is sent to the attacker for executing processing by using some method [19]. But this attack causes no effect on the regular performance of routing protocol. An outside attacker causes these kinds of intrusions for gathering important information from the sensor devices. D. Interference and Jamming In this kind of attack, radio signals are blocked or interfered so that the information can be vanished or tainted. A signal is produced within the network when a malicious comprises an influential communication [20]. This sturdy signal overpowers the targeted signals. This situation creates disturbance in information sharing. 16 Chapter 2 Literature survey Panagiotis Sarigiannidis, et.al (2016)described that the technology of WSN was used in large number of applications. This technology was mainly utilized in military areas, hospitals and unfocussed functions. The sensor nodes were organized arbitrarily in the hazardous areas where human could not reach. This network provided free communication atmosphere because of which this network was vulnerable to several kinds of intrusions. A number of intrusions affected the network performance [21]. In this study, Sybil intrusion was identified as the main damaging attack. In this intrusion, numerous identities were acknowledged illegal through single or several attacker nodes. When attacker nodes showed direct connection to the Sybil nodes, than this intrusion became more worsen in this situation. Thus, a comprehensive analysis was performed on the Sybil intrusion in this study. The performance of WSN was measured in the existence of Sybil intrusion. The possibility of Sybil-free WSN was measured according to the quantity of sensor devices and their strength. The simulations were executed for evaluating the performance of proposed technique. Yali Yuan, et.al (2015) stated that a development was seen in the WSNs due to the growth of technology. The WSNs were extensively used in almost all applications. In WSNs, the sensor devices were deployed accurately in hazardous surroundings because of the deployment-aware applications of this network. This network provided free communication atmosphere because of which this network was vulnerable for several kinds of intrusions. A number of intrusions affected the performance of wireless sensor network. Among these intrusions Sybil attack was 17 considered as one of the main intrusions. In this attack, numerous identities were depicted for the solo node which reduced the localization correctness. This resulted in the destruction of complete network arrangement [22]. In this study, a new frivolous SF-APIT algorithm was presented for the removal of this intrusion. This approach was admired because of its range free technique. The proposed approach could be implemented even at the single node. In wireless networks because of the minimum overhead, this novel algorithm was proposed as it provided the competent outcomes based on RSS. In this study, several simulations were executed for evaluating the performance of presented approach. These simulations estimated the efficiency of the proposed approach in comparison with other existing techniques for minimizing the consequences of this intrusion. Noor Alsaedi, et.al (2015) stated that WSNs were used in several applications because of their rising technology. Sensor nodes were arranged arbitrarily inside the network because of its dynamic network topology. This network faced several issues such as inadequate processing energy of sensor devices and restricted battery because of these issues this network subjugated occasionally. This network provided free communication atmosphere because of which this network was vulnerable for several categories of intrusions. A number of intrusions affected the performance of wireless sensor network. Among these intrusions Sybil attack was considered as one of the main intrusions [23]. The existence of this intrusion created disturbance in the complete network because of the occurrence of numerous identities generated from attacker node. In this study, a lightweight trust system was proposed for the minimization of all those concerns where power was utilized in the form of a metric parameter for a hierarchical WSN. A number of tests were conducted to compute the performance of suggested approach. The tested outcomes demonstrated the efficiency of the proposed approach. A lessening in the network messaging overhead was seen because of this proposed approach. Sepide Moradi, et.al (2016) discussed that the WSNs were utilized in several applications and various regions because of their rising technology. The sensor nodes were dispersed for gathering of information in the hostile situations [24]. The security in WSNs was imperative as these unprotected hazardous regions. In order to render security in WSNs, the detection of intrusions 18 was indispensable. Various attacks degraded the performance of the networks and Sybil attack was one of them. This intrusion was a huge danger for geological routing protocols and multi-path routing. A distributed technique was proposed with the help of movable agents and local data of every sensor to detect the Sybil intrusion. The simulation results proved the effectiveness of proposed techniques in comparison with the existing techniques. Salavat Marian, et.al (2015)stated that wireless sensor network had been extensively utilized in common applications. This network provided free communication atmosphere because of which this network was vulnerable against several categories of intrusions. A number of intrusions hampered the functionality of WSNs. Among these intrusions Sybil attack was considered as one of the main intrusions. In this intrusion, malicious nodes transmitted packets to numerous nodes with fake identities for making their existence in the network. This intrusion generated several other attacks after obtained the reach of the network. In this study, a safety counter was proposed. The proposed approach utilized RSSI technique for the easy detection of Sybil intrusion [25]. The earlier presented techniques were based on the random key allocation. In wireless sensor networks, two indicators identified as RSSI and LQI were used for estimating the quality of connection. A number of tests were executed for evaluating the performance of proposed approach and measured the efficiency of this approach in stationary atmosphere with high-quality transceivers. The acknowledged energy ought to be the function of remoteness according to the wireless channel models for their utilization in local Sybil nodes. Ruixia Liu, et.al (2014)stated that the rising technology of body sensor network (BSN) had been extensively used in a number of applications. This technology affected the lifestyle of people very much. The data related to the mental health of the client and privacy were some parameters linked with this network. Thus, in these networks, security was considered as one of the main threat. In this network, numerous node identifiers were utilized as messaging medium for the transmission of information because of which it was easy for Sybil intrusion for the degradation of the network’s performance [26]. In this study, a novel RSSI was presented to detect all the existing Sybil nodes within the network when they were regulating their broadcasting energy. Thus, the proposed approach showed enhanced performance in comparison with other existing 19 techniques. Every node maintained its own identity certificate. Therefore, this approach did not require any symmetric key encoding technique. Various simulations conducted for evaluating the suggested approach’s performance. These simulations measured the efficiency of proposed technique on the basis of high discovery rate and minimum operating cost. Imran Makhdoom, et.al (2014) described that wireless sensor network were more vulnerable against various kinds of intrusions because of the free information sharing provided by them. A number of intrusions hampered the performance of this network for example wormhole, Sybil, black hole attack and so on. The traditional cryptographic technique provided security against the external intrusion but this technique was not able to minimize the internal intrusions in which node compromised [27]. Sybil intrusion was estimated as one of the main intrusions amid all other intrusions because of the occurrence of the attacker node. All proposed techniques were scrutinized for minimizing this type of intrusion. In this study, a new One-Way Code Attestation Protocol (OWCAP) was proposed for wireless sensor network for recognizing its advantages and disadvantages. This proposed approach was extremely effectual because it minimized not only the Sybil intrusion but other main intrusions present in this network as well. Bayrem TRIKI, et.al (2014) proposed a novel approach to detect and prevent the Sybil intrusions occurring in MWSNs. Two kinds of authentication techniques were used for the identification of Sybil malevolent within the network. The RFID tags were embedded in the primary part for the certification to authenticate the army personnel. In the second case, the soldiers utilized these certificates for revealing their genuineness to their associates [28]. Thus, this technique proved very beneficial for the prevention of this attack. In this approach, the soldiers utilized two certificates at the similar time. The verification of soldiers was performed through the heartbeat of the combatant. The proposed approach identified the Sybil intrusion by protecting the privacy of soldiers. This approach helped in the detection of intrusion through recognizing the genuine identity of the combatant. P. Raghu Vamsi, et.al (2014) stated that a development was seen within the WSNs with the expansion of technology. A number of intrusions hampered the performance of this network and 20 Sybil attack was one of them. This attack was considered a big threat. Due to the free communication within this network, this network was prone to different kind of attacks. Extremely inadequate lightweight models were presented in the obtainable schemes [29]. Thus, a LSDF was proposed to alleviate the effects of Sybil intrusion. The proposed framework used two components identified as evidence collection and legalization. Every node monitors the activities of its adjacent nodes within the network for the collection of evidences. A sequential hypothesis analysis was performed for the justification of this technique and for identifying the condition of the node whether it was normal node or Sybil node. Several simulations were carried out for evaluating the performance of proposed technique. These simulations showed the efficiency of the projected technique. Bin TIAN, et.al (2013) stated that advancement in technology expanded microelectronics technology and wireless communication technology. These technologies proved extremely beneficial in the easy growth of low power, WSNs and so on. Due to the free communication provided by wireless sensor networks, these networks were more vulnerable towards the intrusions. Thus, in these networks, security was the main concern. In these networks, installed Sensors nodes were dispersed arbitrarily because of which this network comprised dynamic network topology. Sensor nodes had inadequate resources and battery energy which resulted in the breakdown of these networks occasionally. In this network, Sybil attack was considered as one of the main intrusions. In this study, Sybil discovery techniques were proposed in accordance with the range of WSNs [30]. The efficiency of the projected technique was concluded on the basis of executed tests. The tested outcomes demonstrated that proposed technique minimized the security issue present in these networks. Xun Li, et.al (2013)stated that the recent development in the Underwater WSNs made possible the utilization of these networks in various extensive applications. Due to the free communication provided by wireless sensor networks, these networks were more vulnerable towards the intrusions. Thus, in these networks, security was the main concern [31]. A number of intrusions hampered the performance of this network and Sybil attack was one of them. This attack was considered the most common and destructive intrusion. Thus, an effective method 21 was necessary to detect the Sybil attack. In this study, a new technique was suggested to detect the Sybil intrusion. Several mathematical scrutiny and simulations were performed for evaluating the performance of proposed technique using MATLAB tool. The attained simulation outcomes demonstrated the efficiency of the proposed technique with the help of which this intrusion was identified in an effective manner. James Harbin, et.al (2011) stated that the improvement in wireless sensor network (WSN) was imperative due to its finite battery power and signal congestion intrusions. Consequently, in this study, Distributed beam forming clusters were proposed to enhance the WSNs. Lesser numbers of sensor nodes participated in the communication procedure and caused connection failure in the network [32]. Due to the free communication provided by wireless sensor networks, these networks were more vulnerable towards the intrusions. During the intrusion, the attacker nodes spoofed the identities of their neighbors. For measuring the effect of these nodes, an investigative scheme was presented in this study. BinZeng, et.al (2010)stated that WSNs were employed in large number of applications. Due to the free communication provided by wireless sensor networks, these networks were more vulnerable towards the intrusions. Thus, in these networks, security was considered an indispensable factor for example in peer-to-peer networks. A number of intrusions affected the functionality of these networks and Sybil attack was one of them. In this attack, attack, the distributed system created the false numerous identities and showed that they were several and alienated nodes in the system. When attacker node tried to deceive the truthful node, an edge amid Sybil node and truthful node was existed. In this study, a new protocol was proposed for minimizing the effects of Sybil intrusion. This proposed protocol utilized ant colony optimization (Am) algorithm [33]. In this algorithm, nodes were arbitrarily dispersed and they were free for leaving or joining the network at any time. The tracks of the first node left on each node became weak. The quantity of edge intrusion could be limited successfully and proficiently according to the proposed algorithm. Thus, the proposed approach ensured that the truthful node must be received with high possibility and the Sybil nodes were discarded at larger level. 22 Shanshan Chen, et.al (2010) described that WSNs were utilized in several applications and various regions because of their rising technology. Limited battery power and security were the main challenges occurred before the WSNs. In this study, a security system was proposed on the basis of LEACH routing protocol beside Sybil intrusion. The proposed approach was planned on the basis of the RSSI by means of which Sybil attack could be identified without difficulty [34]. This technology had been used in such a situation when numerous CHs were above the threshold level. A number of tests were carried out for evaluating the performance of projected techniques by means of security and power utilization. The tested outcome demonstrated the efficiency of the proposed technique in the detection of Sybil intrusions. The proposed approach minimized the effects of the Sybil intrusions as well. Ren Xiu –li, et.al (2009) presented a novel approach for the detecting the Sybil attack on the basis of range. The range of neighboring nodes was verified through every node which was available within the network for identifying the attacker node [35]. The messages were shared amid the nodes to detect the Sybil node easily. The results of testing proved that proposed technique showed better performance in comparison with other existing techniques. This proposed technique was inexpensive and provided correctness. Thus, this approach was utilized mostly for the inexpensive networks and the network having restricted number of resources. Annie Mathew, et.al (2017) stated that a direct path was created from source to target for information sharing because of the availability of huge amount of sensor devices. This approach made the sensing procedure simpler [36]. Security was the main threat in these networks because of the free communication atmosphere provided by these networks. A number of intrusions affected the working performance of this network for example sinkhole attack, wormhole attack, gray hole attack and so on. The sinkhole node established a direct route amid the sink or destination node because of the occurrence of sinkhole intrusion within the network. Up to now, a number of methodologies had been presented using for the effective detection of sinkhole intrusion. In this study, sinkhole intrusion was discussed along with its categorizations and techniques for the detection of this intrusion on the basis of certain aspects. 23 Mahmood Alzubaidi, et.al (2017)stated in wireless network, several kinds of internal intrusions occurred. This detection of sinkhole intrusion and its effect on the RPL were the main objectives of this study [37]. In this study, different mechanisms and IDS approach were proposed for the easy detection of sinkhole intrusion. In this study, every method was scrutinized and reviewed for highlighting the false positive rate and resource utilization with their merits and demerits. In this study, a chart was demonstrated which provided the earlier demonstration of detection methods for sinkhole intrusion. A number of comparisons were performed for the selection of most efficient technique. Manpreet kaur, et.al (2016) described that WSNs were deployed in several applications because of their rising technology such as military and public regions. In these networks, huge amount of sensor nodes with restricted resources were organized. These nodes comprised base station, small cost and low power sensor nodes using which observation was performed [38]. In this network, small size and huge amount of sensor nodes were the main cause because of which these networks were affected badly by the intrusions. Thus, sinkhole intrusion was considered as one of the most disparaging routing intrusions among all intrusions. The sinkhole attack captured all routing data. This data was promoted through the attacker node which forced other nodes to route the information in its direction. Thus, the network performance was degraded because of the severe effect of sinkhole intrusion. The major objective was the scrutiny and recognition of the sinkhole intrusion within WSNs. Gauri Kalnoor, et.al (2016) stated that numerous randomly distributed sensor devices were rooted within the wireless sensor network. Several factors for example pressure, temperature, movement, resonance and many more were observed in the hazardous atmospheric circumstances. Sensor nodes had been used for the transmission of information across the network. An increase in the internet traffic was depicted because of the increase of network size and quantity of nodes. Security was the main issue faced in this network because of the major intrusion. This network provided free communication and security played a fundamental role in the safety of necessary data [39]. Thus, in this study, attack recognition scheme was proposed because of the security issue. The reliable Quality of Service (QoS) aid for example consistency, 24 congestion handling, power competence and end-to-end delay were the chief challenges experienced in WSN. A number of security routing protocols were used for protecting the quality of service parameter of WSN. These protocols were utilized to discover of the attacker as well. In this study, several routing protocols were reviewed for improving the performance of the network. Jianpo Li, et.al (2018) suggested a brief review of wormhole intrusion in and its effect on the network according to the distance vector routing. The DV-hop was a localization algorithm. In this study, a security AWDV-hop was proposed for the minimization of several issues occurring within the wireless sensor networks [40]. In the first algorithm, the neighbor node relationship list (NNRL) was formed through the utilization of the broadcast flooding. The sensor devices provided the identity numbers of their neighboring devices inside the network by using NNRL. The hypothetical and real number of adjacent nodes was compared for the identification of imaginary beacon nodes. The distance to other beacon was estimated within the NNRL for the identification of actual intrusion caused by the beacon nodes. They region was marked with 1 or 2 for the completion of this task. In the end, the other unidentified nodes marked themselves with 1 or 2on the basis of the marking done by the beacon nodes. No communication was found amid the nodes marked with 1 or 2 because of the extrication among the localization rounds. The tested outcomes demonstrated that a reduction was seen in the localization fault with the help of proposed AWDV-hop algorithm. This localization error was reduced up to 80% in comparison with the DV-hop algorithm. RanuShukla, et.al (2017) described that the WSNs were used in several applications and various regions because of their rising technology. These areas included wild life, military, patient observation, tremor forecasting, fire discovery and many more. Due to the free communication provided by wireless sensor networks, these networks were more vulnerable towards the intrusions. These networks experienced several issues like limited power, small size, inadequate resources, and so on. Thus, an exchange was found amid security and power in the WSNsdue to all these restrictions [41]. The architecture of secure routing protocol was the other issue experienced in this network due to this exchange. The cryptography technique could not be 25 utilized because of its heaviness for providing security within the wireless sensor networks. For overcoming this main concern, most advantageous solution was presented in this study which was identified as TESRP. This technique not only provided security against the wormhole intrusion but considered the finest trust-based routing protocol among other protocols as well. Thus, the concept of trust algorithm with sequence number was used for providing protection against wormhole intrusion. Bharat Bhushan, et.al (2017) presented a review of extensive applications of the WASN and sensor networks. These networks were installed in the hazardous situations to monitor the real time circumstances. This network comprised the main security issue because of its open commutation atmosphere [42]. The presence of wormhole intrusion degraded the performance of complete network. The malicious triggered the intrusion inside the network without damaging any node. The malicious node tracked the record of bits transmission in this intrusion which was further channelized to the different locations. This malicious node retransmitted packets within the network. No substitute path was provided to the nodes placed nearer to the malicious. After this, all the paths were forwarded to the wormholes. The triggering of wormhole intrusion in optimized link state routing protocols resulted in the transmission of wrong data inside the network. Thus, the method of wormhole discovery and prevention was reviewed in this study based on attained location data and time management amid nodes present within the network. Mayank Kumar Sharma, et.al (2016)stated that the wireless sensor network was identified as the set of clusters in which sensor nodes were interlinked with one another for performing communication. The sensor devices were utilized within the hostile environment for sensing the physical conditions. These devices gathered all the information about environment. This information was further forwarded to the sink. Thus, the usage of routing protocols was necessary to create an appropriate route for the efficient transmission of information from one node to another node. In this study, various routing protocols were built and arranged in accordance with their features. Because of the limited resources, a proficient and quick routing procedure was necessary for minimizing the routing overhead [43]. This network suffered various routing intrusions because of its free communication scenario. In this study, wormhole 26 intrusion was reviewed. This intrusion was considered a major threat to the wireless sensor networks. Thus, the routing protocols were used for minimizing the effects of this wormhole intrusion. The comparison of suggested approach was done with other AODV routing protocol for the scrutiny of threat diminution. The impact of high broadcasting energy on the wormhole intrusion was scrutinized as well which was the major aim of this study. In this study, various methods were presented for the efficient minimization of these threats. Qualnet 5.2 simulator was utilized for simulation procedure to evaluate the performance of proposed technique. Ali Modirkhazeni, et.al (2016) describes that the WSNs were deployed in several areas including military, health care, industrial applications and many more. The WSN was a rising technology. The huge amounts of sensor nodes were deployed in the hazardous atmosphere for sensing the physical conditions. These sensor nodes collected all the information about environment. This information was forwarded to the sink for additional processing. Because of the finite battery, this kind of wireless medium was used for communication purpose. These networks were more vulnerable against these intrusions because of their free information sharing surroundings. These intrusions affected the communication of entire network [44]. In WSN, traditional security schemes were not used because of their heaviness and limited number of nodes. in this study, wormhole intrusion was reviewed. This attack was considered as one of the main intrusions since it disrupted the performance of complete network. This intrusion utilized a distinct wormhole channel for the transmission of information from one location to another. Thus, this intrusion was considered as the most adverse intrusion to identify in wireless sensor network. In this study, a distributed network discovery approach was proposed for minimizing the effects of wormhole intrusion. Several tests were carried out to compute the performance of suggested technique. The tested outcomes demonstrated the efficiency of the proposed technique since it minimized the wormhole intrusion up to 100%. Swati Bhagat, et.al (2016) stated that wireless sensor network was used in several applications and in various regions because of their rising technology. These areas included military observation, hospital scrutinizing, forest, and many more. In this study, the wormhole intrusion was reviewed as well. This attack affected the nodes present in the network. These wormhole 27 nodes were identified as false courses as and smaller than the first course in the system. An issue was created in the routing of sensor devices on the basis of distance amid the nodes according to existing situations [45]. In this study, a novel technique was proposed for the powerful transmission of information. Mostefa BENDJIMA, et.al (2016) stated that wireless sensor networks were used in large number of applications. Sensor nodes were deployed in the hostile environment for sensing the physical conditions. The performance of network was degraded because of the occurrence of several intrusions. These networks faced several constraints for example restricted resources, inadequate energy source, huge quantity of nodes, infrastructures less, dynamic network topology. In this study, a secure network communication was proposed using an appropriate method for the minimization of all these concerns. Security was the main issue which divided the network into two sections. In this approach, the mobile agents were used for discarding the traffic malevolent. These malevolent were the main reason wormhole attack within the network [46]. The existing attacker nodes in the network launched the wormhole intrusion. This intrusion was identified as denial of service attack. In this intrusion, a channel was formed for the transmission of packets from one location to other. Several simulations were performed for evaluating the performance of proposed technique. For this purpose, SINALGO simulator was utilized. Decrease in the power utilization and improvement in the life span of network and packet delivery was seen through the simulation outcomes. ShaoheLv, et.al (2008)stated that wireless sensor networks were more prone to the intrusions because of their infrastructure less configuration and free communication. In this study, Sybil attack was reviewed. One or more malicious node launched this kind of intrusion because of which network applications were collapsed [47]. A novel identification approach named as CRSD was proposed for stationary wireless sensor networks. In this network, the received signal strength (RSS) was used utilized for measuring the remoteness among two identities. The location of interesting identities could be determined using this RSS information. This information was gathered from numerous neighboring nodes. The Sybil intrusion identified more than two identities in the same location. This attack disrupted the network functionality as 28 acknowledged through the scrutiny. Simulations were carried out for evaluating the performance of proposed technique. The simulation outcomes demonstrated the efficiency of CRSD approach. Jiangtao Wang, et.al (2007) proposed a novel technique for the detection of Sybil intrusion within the wireless sensor network (WSN) based on the received signal strength indication (RSSI). This approach followed the real time network condition where Jakes channel scheme was installed. The head nodes comprised the signal strength of received nodes and the location information of associate nodes. These factors were used for measuring the effects of Sybil intrusion [48]. In this study, two techniques were proposed for the minimization of Sybil intrusion occurring in the head nodes and associate nodes. These techniques provided wide ranging applications and demonstrated the effectual outcomes as well. Chapter 3 Present Work 29 3.1. Problem Formulation: The sensing devices sense the data in WSN. From there, the sensed information is forwarded to the sink. WSN is a decentralized kind of network without having any centralized control. This condition is accountable for the entry of attacker nodes within the network. These attacker nodes trigger different kinds of active and passive intrusions inside the network. The sinkhole intrusion decreases network efficacy in regard to throughput, power utilization and packet loss. The sinkhole intrusion floods the attacker nodes in the tunnel through communication is performed. This investigation is absolutely based on the discovery of attacker node which further launches the sinkhole intrusion within the network. 3.2. Objective 1. To isolate the attacker node. This node is responsible for the launching of sinkhole intrusion within the network. 2. To measure the threshold value of data packets transferred on the wireless link. 3. To implement proposed approach and compare this approach with former techniques with regard to several factors. 3.3. Research Methodology 30 31 Flowchart 32 3.4 Phase of Detection and Isolation of adversaries Following are the various phases of adversary discovering: 1. Pre-Processing: -The wireless sensor network is configured with fixed amount of sensing devices. The clustering on the basis of locality is applied in the entire network. In the proposed LEACH protocol, power and remoteness of all devices are verified correctly. The node having utmost powerand least distance is elected as CH. The whole nodes occurring in the network will send their information to the CH. CH further creates path with the help of other CHs and propels this information to the sink. AODV routing protocol is utilized to create path among source and the destination. AODV protocol is a source node protocol which deluges the route reply packets. The source node selects the most appropriate route towards the destination according to the hop count and highest sequence number. The source node forwards the information to the preferred place. Attacker node launches the mis-directional intrusion with the help of selected route. 2. Detection of malicious nodes: -A number of approaches were proposed in the last few years for the discovery of attacker nodes. The earlier method was monitor mode method. The activity of the neighboring node can be observed with the help of this method. This method does not give good performance in the recognition of attacker node. The second method implemented in the earlier investigation was named as delay tolerance method. This method needs extra hardware and software for the discovery of attacker nodes. This increases the intricacy and cost of the arrangement. The base station applies node localization method for the discovery and segregation of attacker nodes. The node localization technique gathers data with respect to the established route. Sink can collect the whole data of sensing devices with the help of node localization method. The sink can collect data about the location of sensor node and their delay during the information transmission. The sink scrutinizes the quality of service constraints. When the network throughput goes below a certain threshold level, then base station takes action for 33 the discovery adversary. The base station checks the network throughput on every hop for the detection of attacker node form the network. The node having throughput below the threshold level is designated as adversary. The gathered data comprises the remoteness of every node from sink. The distance creates delay in every hop count which exists on the formed route. The base station detects this delay. The delay of every hop is calculated due to which node will enhance the delay within the network and identifies the attacker nodes. The predictable delay is computed with the equation number 1 𝐷𝑖𝑠𝑡𝑎𝑛𝑐𝑒 𝑏𝑒𝑡𝑤𝑒𝑒𝑛 𝑒𝑎𝑐ℎ 𝑛𝑜𝑑𝑒 Expected Delay = Time to live * 𝐷𝑖𝑠𝑡𝑎𝑛𝑐𝑒 𝑏𝑒𝑡𝑤𝑒𝑒𝑛 𝑠𝑜𝑢𝑟𝑐𝑒 𝑎𝑛𝑑 𝑑𝑒𝑠𝑡𝑖𝑛𝑎𝑡𝑖𝑜𝑛 ---- (1) The distance between each node is calculated with the equation number 2 -------------(2) The predicted delay is defined with the equation number 3 𝐷𝑖𝑠𝑡𝑎𝑛𝑐𝑒 𝑏𝑒𝑡𝑤𝑒𝑒𝑛 𝑒𝑎𝑐ℎ 𝑛𝑜𝑑𝑒 Predicted delay= 𝑇𝑜𝑡𝑎𝑙 𝑛𝑢𝑚𝑏𝑒𝑟 𝑜𝑓 𝑚𝑒𝑠𝑠𝑎𝑔𝑒 𝑒𝑥𝑐ℎ𝑛𝑎𝑔𝑒 -- (3) When the predicted delay is above the expected delay then the attacker node is discovered. The threshold delay is the forecasted delay. The threshold delay in the network is described as 2 ms if the sensor node enhances the delay above the threshold level which is 2 ms, then that node will be adversary. The multipath routing method is implemented for the removal of attacker nodes from the route. The projected method follows the threshold system for the discovery of attacker nodes and the other applied methods. The proposed approach does not need additional hardware and software components for the discovery of attacker nodes because of this approach is preferred for the discovery of attacker nodes. 3. Isolation of Malicious nodes: -In the final stage, the segregation procedure is implemented for the removal of attacker node from the route formed between source and destination. The multipath routing method is used for the elimination of attacker node. The multipath routing technique isolates the attacker node from the network. In this technique, the source floods RREP 34 in the network and every node existing close to the destination will reply back with RRPs. The source node chooses the finest route from source to destination according to the hop count and sequence number. The source node does not choose the route in which attacker node subsists. The process used for the separation of attacker nodes is described below: Initialization: Sensor nodes Output: Assortment of safe route 1. The source transmits route request messages in the network 2. After receiving the route request messages Increase the hop count and sequence number 3. if sequence number of novelroute> than sequence number of earlierroute Process the request Else Discard the request 4. if (attacker node is presented in the path ) Reject the path Else Check the hop count and sequence number 5. Choose the saferoutefrom source to destination 35 Chapter – 4 EXPERIMENTAL RESULT 4.1 Network Simulator Network simulator emerges due to ongoing investigative study and expansion which is managed by the investigators at Berkeley. The network simulator comprises distinct event simulator target and NS-2 is one of them. This simulator principally utilizes OTcl as command and configuration language. This network simulator is mainly implemented in C++, with OTcl as the interpreter. Figure 4.1:Network Simulator 2 [39] The accumulated hierarchy in C++ controls the class hierarchy. This accumulated hierarchy performs in the same way as the interpreter hierarchy in OTcl performs. TcL is the root hierarchy 36 in which two classes communicate with each other. There exists single simulator which establishes the simulator objects with the help of commenced interpreter. The interpreter establishes the methods defined in the TcL class in automatic manner. These methods are commenced through the clients. The simulator performs two tasks i.e. the comprehensive simulation of protocol for making its configuration easier to the customer and transforms the parameters and can observe these alterations as well. The algorithms are implemented in C++. This programming language can handle the bytes and headers of the packet easily. Second scenario is the iteration, in which iteration time is more significant than runtime assignment. Tcl provide ssupport in the completion of these two tasks. The event scheduler is the main element of network. The event scheduler considers the schedule timer and pointer of packet in the form of an event. Timer or switching module uses the event scheduler. The information specified in the input script is similar to the one or two text files created by the network simulator after the execution of simulation. Network Animator or NAM in short form is a geographical tool which is utilized for analyze the text created by NS. The local and wide area network NS is used for simulation purpose. This network simulator simulates an extensive array of IP network, TCP and UDP and other network protocols which are executed through it. Traffic source behavior exists for example FTP, CBR and VBR, Router queue management methods. The NS project is now the part of the VINT project that produces tools for simulation outcomes, demonstration, scrutiny and transformers that transform the network topologies produced by eminent generators to NS arrangement. The existing version of network simulator does not is not compatible with mobile wireless environment [39]. 37 TABLE 4.1 Simulation Parameters [39] ● Number of nodes: This factor denotes nodes utilized for simulation purpose. ● Pause time: This metric denotes time interval for the devices which can be stopped throughout simulation. ● Traffic type: Traffic of two types, Variable Bit Rate (VBR) and Constant Bit Rate (CBR). CBR traffic is the reason of maximum time delay. ● Simulation time: The period of time in which simulation is performed is identified as simulation time. Quantitative Metrics: Quantity of quantitative metrics is accountable for the assessment of the working of routing algorithm for wireless ad-hoc networks. In this proposed scheme, four quantitative metricshave 38 been used and further RFC 25012 defines general notions. Two types of qualitative metrics are throughput and overhead. PDR corresponds to the ratio of entire data packets received at the destination to the total amount of data packets propelled by the sources. It is the most significant metric. The congestion in the network occurs because of the retransmissions of packets. 𝑃𝑎𝑐𝑘𝑒𝑡 𝐷𝑒𝑙𝑖𝑣𝑒𝑟𝑦 𝑅𝑎𝑡𝑖𝑜 = 𝑇𝑜𝑡𝑎𝑙 𝐷𝑎𝑡𝑎 𝑝𝑎𝑐𝑘𝑒𝑡𝑠 𝑟𝑒𝑐𝑒𝑖𝑣𝑒𝑑 …..(3) 𝑇𝑜𝑡𝑎𝑙 𝑑𝑎𝑡𝑎 𝑝𝑎𝑐𝑘𝑒𝑡𝑠 𝑠𝑒𝑛𝑡 ● Average End-to-End Delay End-to-end delay causes several issues within the network. The delay is added in every successful data packet delivery and that total is divided through the total successful data packets received and is utilized for finding standard end to end delay. The delay sensitive application proved most significant and useful video and voice transmission ∑(𝑇𝑖𝑚𝑒 𝑅𝑒𝑐𝑒𝑖𝑣𝑒𝑑−𝑇𝑖𝑚𝑒 𝑠𝑒𝑛𝑡) 𝐴𝑣𝑒𝑟𝑎𝑔𝑒 𝐸𝑛𝑑 𝑡𝑜 𝐸𝑛𝑑 𝐷𝑒𝑙𝑎𝑦 = 𝑇𝑜𝑡𝑎𝑙 𝐷𝑎𝑡𝑎 𝑃𝑎𝑐𝑘𝑒𝑡𝑠 𝑅𝑒𝑐𝑒𝑖𝑣𝑒𝑑 ….(4) ● Overhead Different protocol executes different tasks on the basis of their enlarged size as the Ad hoc networks being intended as scalable. The increased size of the network enhances the quantity of routing traffic. One of the most significant measures of protocol scalability is routing overhead. Overhead is described as the total amount of routing protocol forwarded over the network. Routing overhead is represented in terms of bits or packets per second. The route error packet and network jamming are the main cause of routing overhead. The presented study has been scrutinized on the NS2 and the outcomes have been estimated in regard to throughput, power utilization and packet loss. Three situations are compared within the network which involves 39 sinkhole intrusion andbase papermethod for the recognition and separation of sinkhole intrusion from the wireless sensor networks. Fig 4.1(a): Network Deployment The network is positioned with fixed amount of sensing r nodes as described by the figure 4.1(a).The entire network is separated into many clusters of finite size. Location-based clustering is implemented for the clustering of entire network. 40 Fig 4.1(b): Network Deployment The network is positioned with fixed amount of sensor nodes as described by the figure 4.1(b).The entire network is separated into many clusters of finite size. The location-based clustering is implemented for the clustering of entire network. LEACH protocol is implemented for the selection of CH in every cluster. CHs are chosen in regard to remoteness and power. 41 Fig 4.2(a): Data Aggregation The network is positioned with fixed amount of sensor nodes as described by the figure 4.2(a).The entire network is separated into many clusters of finite size. The location-based clustering is implemented for the clustering of entire network. LEACH protocol is implemented for the selection of CH in every cluster. CHs are chosen in regard to remoteness and power. 42 Fig 4.2(b): Data Aggregation The network is positioned with fixed amount of sensor nodes as described by the figure 4.2(b).The entire network is separated into many clusters of finite size. The location-based clustering is implemented for the clustering of entire network. LEACH protocol is implemented for the selection of CH in every cluster. CHs are chosen in regard to remoteness and power. The required information will be transferred to the sink with the help of CH. 43 Fig 4.3(a): Trigger attack The network is positioned with fixed amount of sensor nodes as described by the figure 4.3 (a).The entire network is separated into many clusters of finite size. The location-based clustering is implemented for the clustering of entire network. LEACH protocol is implemented for the selection of CH in every cluster. CHs are chosen in regard to remoteness and power. The required information will be transferred to the sink with the help of CH. A direct route is created between two CHs. In this route, the attacker node occurs that launch sinkhole intrusion. 44 Fig 4.3(b): Trigger attack The network is positioned with fixed amount of sensor nodes as described by the figure 4.3 (b).The entire network is separated into many clusters of finite size. The location-based clustering is implemented for the clustering of entire network. LEACH protocol is implemented for the selection of CH in every cluster. CHs are chosen in regard to remoteness and power. The required information will be transferred to the sink with the help of CH. A direct route is created between two CHs. In this route, the attacker node occurs that launch sinkhole intrusion. 45 Fig 4.4(a): Deployment of Sensor nodes WSN is positioned with finite number of sensing devices as described in figure 4.4(a).The entire network is separated into many clusters of finite size. The location-based clustering is implemented for the clustering of entire network. LEACH protocol is implemented for the selection of CH in every cluster. 46 Fig 4.4(b): Deployment of Sensor nodes WSN is positioned with finite number of sensing devices as described in figure 4.4(b). The entire network is separated into many clusters of finite size. The location-based clustering is implemented for the clustering of entire network. LEACH protocol is implemented for the selection of CH in every cluster. 47 Fig 4.5: Detection of malicious nodes WSN is partitioned into a number of sensing devices as depicted by the figure 4.5. The base station provides a unique identification to these sensor nodes. The node which is not provided this identification is identified as the attacker node. 48 Fig 4.6: Malicious node isolation The network is positioned with fixed amount of sensor nodes as described by the figure 4.6.The entire network is separated into many clusters of finite size. The location-based clustering is implemented for the clustering of entire network. LEACH protocol is implemented for the selection of CH in every cluster. CHs are chosen in regard to remoteness and power. The required information will be transferred to the sink with the help of CH. A direct route is created between two CHs. In this route, the attacker node occurs that launch sinkhole intrusion. 49 Fig 4.7: Packet loss comparison A comparison amid the fundamental leach and leach protocol is performed under the influence of sinkhole intrusion and proposed method on the basis of packet loss as demonstrated by the figure 4.7. The LEACH protocol exhibits highest effect and decreased packet loss after the separation of the sinkhole. 50 Fig 4.8: Energy Comparison The proposed method, basic LEACH protocol and LEACH protocol are compared under the influence of sinkhole intrusion as depicted by the figure 4.8.The power utilization reduces after segregation of sinkhole intrusion. 51 Fig 4.9: Throughput Comparisons Network throughput, basic LEACH protocol and LEACH protocol were compared under the impact of sinkhole intrusion as depicted by the figure 4.9. It has been evaluated that the network throughput is enhanced at stable rate after the separation of sinkhole intrusion. 52 Chapter - 5 CONCLUSION AND FUTURE WORK 5.1 Conclusion In this study, it has been analyzed that the LEACH protocol is most efficient approach utilized for the reduction of power utilization within wireless sensor networks. This network can sense the ecological circumstances using sensor nodes occurring inside them. These small sized sensor nodes reduce the life span of these networks. The sinkhole attack is identified as an active intrusion which decreases the efficiency of LEACH protocol. this research study presents mutual authentication for discovering and segregating sinkhole intrusion. Network efficiency is scrutinized on the basis of packet loss which is decreased by 15%, power utilization is reduced by 18% and network throughput is improved by 25%. The approach proposed in this study is used for discovering and segregating adversaries from these networks. Sink evaluates the delay per hop according to the threshold level. The attacker node is discovered in regard to delay. The node causing maximum delay is known as the attacker node. This reduces the power utilization, increases the network throughput and decreases the time delay. 5.2 Future Work Different future perspectives of this study are given below:The proposed approach can be used for the detection of different kinds of intrusions such as Sybil intrusion within the network. Several comparisons between the proposed approach and various other secure methods will be performed for testing their trustworthiness. In wireless 53 sensor networks, secure routing and power utilization issues occur due to the absence of any centralized control. The Sinkhole attack is an active kind of intrusion which decreases the performance of network on the basis of certain factors. In future, a structure can be designed in for the reduction of power utilization of the network with the help of information collection. This future approach is based on the proposed LEACH protocol which is a multi-hierarchal protocol. This proposed protocol is compared with other data aggregation protocols as well for checking their genuineness. 54 References [1] I.F.Akyildiz et al., “A Survey on Sensor Networks”, IEEE Commun.Mag.,Vol. 40, No. 8, pp.102-114, Aug. 2002. [2] E.Shi and A.Perrig, “Designing Secure Sensor Networks”, Wireless Commun. Mag., Vol. 11, No. 6, pp.38-43, Dec 2004. [3] Culler, D. E and Hong, W., “Wireless Sensor Networks”, Communication of the ACM, Vol. 47, No. 6, pp. 30-33, Jun. 2004. [4] Al-Sakib Khan Pathan, Hyung-Woo Lee, Choong Sean Hong, “Security in Wireless Sensor Networks: Issues and Challenges”, Proc. ICACT 2006, Volume 1, 20-22, pp. 1043-1048, Feb. 2006. [5] David J. Malan, Matt Welsh, Michael D. Smith, “A Public-Key Infrastructure for Key Distribution in TinyOS Based on Elliptic Curve Cryptography”, Division of Engineering and Applied Sciences, Harvard University, Dec 2007. [6] Dr. G. Padmavathi, Mrs. D. Shanmugapriya, “A Survey of Attacks, Security Mechanisms and Challenges in Wireless Sensor Networks”, International Journal of Computer Science and Information Security, Vol. 4, No. 1 & 2, 2009. [7] A. Perrig, J. Stankovic, and D. Wagner, “Security in Wireless Sensor Networks”, Communications of the ACM, 47(6):53–57, Jun. 2004. 55 [8] Shahnaz Saleem, Sana Ullah, HyeongSeonYoo, “on the Security Issues in Wireless Body Area Networks”, International Journal of Digital Content Technology and its Applications Vol. 3, No. 3, Sep. 2009. [9] Kalpana Sharma. M K Ghose, “Wireless Sensor Networks: An Overview on its Security Threats”, IJCA Special Issue on Mobile Ad- hoc Networks 2010. [10] David Martins, and HerveGuyennet, “Wireless Sensor Network Attacks and Security Mechanisms: A Short Survey”, 2010 IEEE. [11] AnithaS.Sastry, ShaziaSulthana and Dr.SVagdevi, “SecurityThreats in Wireless Sensor Networks in Each Layer”, International Journal of Advanced Networking and Applications, Vol. 04 Issue 04, pp. 1657-1661, 2013. [12] David R. Raymond and Scott F. Midkiff, “Denial-of-Service in Wireless Sensor Networks: Attacks and Defenses”, IEEE Pervasive Computing, Vol. 7, No. 1, pp. 74-81, 2008. [13] Chris Karlof and David Wagner, “Secure routing in wireless sensornetworks: attacks and countermeasures,” Ad Hoc Networks Journal, Vol.1, Issue 2-3, pp. 293-315, 2003. [14] Yan Sun, Zhu Han, and K. J. Ray Liu, “Defense of Trust Management Vulnerabilities in Distributed Networks,” IEEECommunications Magazine, Vol 46, Issue 2, pp.112-119, 2008. [15] Yanli Yu, Keqiu Li, Wanlei Zhou, and Ping Li, “Trust mechanisms in wireless sensor networks: attack analysis and countermeasures,” Journal of Network and Computer Applications, Elsevier, 2011. [16] W. Xu et al., “The Feasibility of Launching and Detecting Jamming Attacks in Wireless Networks,” MobiHoc ’05: Proc. 6th ACM Int. Symp. Mobile Ad Hoc Net. and Comp., pp. 46–57, 2005. 56 [17] W. Xu, W. Trappe, and Y. Zhang, “Channel Surfing: Defending Wireless Sensor Networks from Interference”, in Proc. Of Information Processing in Sensor Networks, 2007. [18] Shih, E., Cho, S., Ickes, N., Min, R., Sinha, A., Wang, A. &Chandrakasan, A., “Physical layer driven protocol and algorithm design for energy-efficient wireless sensor networks”, Proceedings of the 7th Annual International Conference on Mobile Computing and Networking, Rome, Italy, pp. 272-287. [19] Woo, A. and Culler, D., “A Transmission Control Scheme for Media Access in Sensor Networks”, Proceedings of the Seventh Annual ACM/IEEE International Conference on Mobile Computing and Networking, MobiCom, Rome, Italy, 2001. [20] Sohrabi, K., Gao, J., Ailawadhi, V., and Pottie, G. J., “Protocols for Self-Organization of a Wireless Sensor Network”, IEEE Personal Communications, pp. 16-27, 2000. [21] Panagiotis Sarigiannidis, Eirini Karapistoli and Anastasios A. Economides, “Analysing Indirect Sybil Attacks in Randomly Deployed Wireless Sensor Networks”, IEEE, 2016 [22] Yali Yuan, LiuweiHuo, Zhixiao Wang and Dieter Hogrefe, “Secure APIT Localization Scheme against Sybil Attacks in Distributed Wireless Sensor Networks”, JOURNAL OF LATEX CLASS FILES, VOL. 14, NO. 8, AUGUST 2015 [23] Noor Alsaedi1, 2, Fazirulhisyam Hashim, A. Sali, “Energy Trust System for Detecting Sybil Attack in Clustered Wireless Sensor Networks”, 2015 IEEE 12th Malaysia International Conference on Communications (MICC), Kuching, Malaysia (23 - 25 Nov 2015) [24] Sepide Moradi, MeysamAlavi, “A distributed method based on mobile agent to detect Sybil attacks in wireless sensor networks”, 2016 Eighth International Conference on Information and Knowledge Technology (IKT) 57 [25] Salavat Marian, Popa Mircea, “Sybil Attack Type Detection in Wireless Sensor Networks based on Received Signal Strength Indicator detection scheme”, 10th Jubilee IEEE International Symposium on Applied Computational Intelligence and Informatics • May 21-23, 2015 [26] Ruixia Liu, Yinglong Wang, “A New Sybil Attack Detection for Wireless Body Sensor Network”, IEEE, 2014 [27] Imran Makhdoom, Mehreen Afzal, Imran Rashid, “A Novel Code Attestation Scheme Against Sybil Attack in Wireless Sensor Networks”, 2014 National Software Engineering Conference [28] Bayrem TRIKI Slim Rekhist Noureddine Boudriga, “An RFID based System for the detection of Sybil attack in Military Wireless Sensor networks”, IEEE, 2014 [29] P. Raghu Vamsi and Krishna Kant, “A Lightweight Sybil Attack Detection Framework for Wireless Sensor Networks”, IEEE, 2014 [30] Bin TIAN, Yizhan YAO, Lei SHI, Shuai SHAO, Zhaohui LIU, Changxing XU, “A NOVEL SYBIL ATTACK DETECTION SCHEME FOR WIRELESS SENSOR NETWORK”, IEEE, 2013 [31] Xun Li, Guangjie Han, Aihua Qian, Lei Shu, Joel Rodrigues, “Detecting Sybil Attack based on State Information in Underwater Wireless Sensor Networks”, 2013 [32] James Harbin, Dr Paul Mitchell, “Reputation Routing To Avoid Sybil Attacks In Wireless Sensor Networks Using Distributed Beamforming”, 2011 8th International Symposium on Wireless Communication Systems, Aachen [33] BinZeng, Benyue Chen, “SybilACO: Ant colony optimization in defending against Sybil attacks in the wireless Sensor Network”, 201O International Conference on Computer and Communication Technologies in Agriculture Engineering 58 [34] Shanshan Chen, Geng Yang, Shengshou Chen, “A Security Routing Mechanism against Sybil Attack for Wireless Sensor Networks”, 2010 International Conference on Communications and Mobile Computing [35] Ren Xiu –li, Yang Wei, “Method of Detecting the Sybil Attack Based on Ranging in Wireless Sensor Network”, IEEE, 2009 [36] Annie Mathew and J.Sebastian Terence, “A Survey on Various Detection Techniques of Sinkhole Attacks in WSN”, International Conference on Communication and Signal Processing, April 6-8, 2017 [37] Mahmood Alzubaidi, Mohammed Anbar, Samer Al-Saleem, Shadi Al-Sarawi, Kamal Alieyan, “Review on Mechanisms for Detecting Sinkhole Attacks on RPLs”, 2017 8th International Conference on Information Technology (ICIT) [38] MANPREET KAUR, AMARVIR SINGH, “Detection and Mitigation of Sinkhole Attack in wireless sensor network”, IEEE, 2016 [39] Gauri Kalnoor, Jayashree Agarkhed, “QoS based Multipath Routing for Intrusion Detection of Sinkhole Attack in Wireless Sensor Networks”, 2016 International Conference on Circuit, Power and Computing Technologies [40] Jianpo Li1 , Dong Wang1 , Yanjiao Wang, “Security DV-hop localisation algorithm against wormhole attack in wireless sensor network”, IET Wirel. Sens. Syst., 2018, Vol. 8 Issue 2, pp. 68-75, the Institution of Engineering and Technology 2018 [41] RanuShukla, Rekha Jain, P. D. Vyavahare, “Combating against Wormhole Attack in Trust and Energy Aware Secure Routing Protocol (TESRP) in Wireless Sensor Network”, Proceeding International conference on Recent Innovations is Signal Processing and Embedded Systems (RISE -2017) 27-29 October,2017 59 [42] Bharat Bhushan, Dr. G. Sahoo, “Detection and Defense Mechanisms against Wormhole Attacks in Wireless Sensor Networks”, IEEE, 2017 [43] Mayank Kumar Sharma, Brijendra Kumar Joshi, “A Mitigation Technique for High Transmission Power based Wormhole Attack in Wireless Sensor Networks”, ieee, 2016 [44] Ali Modirkhazeni, SaeedehAghamahmood, Arsalan Modirkhazeni, NaghmehNiknejad, “Distributed Approach to Mitigate Wormhole Attack in Wireless Sensor Networks”, IEEE, 2016 [45] Swati Bhagat, TrishnaPanse, “A Detection and Prevention of Wormhole Attack in Homogeneous Wireless Sensor Network”, IEEE, 2016 [46] Mostefa BENDJIMA, Mohammed Feham, “Wormhole Attack Detection in Wireless Sensor Networks”, SAI Computing Conference 2016 July 13-15, 2016 [47] ShaoheLv, Xiaodong Wang, Xin Zhao and Xingming Zhou, “Detecting the Sybil Attack Cooperatively in Wireless Sensor Networks”, 2008 International Conference on Computational Intelligence and Security [48] Jiangtao Wang, Geng Yang, Yuan Sun, Shengshou Chen, “Sybil Attack Detection Based on RSSI for Wireless Sensor Network”, IEEE, 2007 60 APPENDIX Network simulator is the outcome of the ongoing work of research and development which is administrated by the researchers at Berkeley. It has discrete event simulator target in which NS-2 is one of them and primarily uses OTcl as command and configuration languages. This NS is particularly executed is C++, with OTcl as the interpreter. The hierarchy of class is controlled by the compiled hierarchy in C++. This compiled hierarchy is work in the similar manner to the interpreter hierarchy in OTcl. TcL is the root hierarchy in which two classes are one to one correspondence. There is presence of one simulator which creates the simulator objects through initiated interpreter. The methods which are defined in the TcL class are automatically established by the interpreter and are initiated by the users. 61