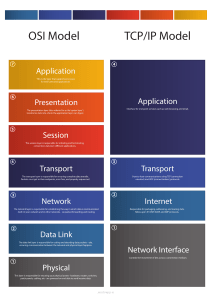
CompTIA Network+ Certification Exam Objectives Hey! Thanks for downloading this PDF! I’m looking forward to learning with you. If you have any questions about this, head to my website hackerbella.xyz and comment on the blog. I’m happy to help. - Allie Mellen 1.0 Networking Concepts 1.1 Explain the purposes and uses of ports and protocols. In computer networking, a port is an endpoint in a computer used for communication. Protocols and Ports Protocol Port TCP/UDP Description Applications Interesting Facts SSH 22 TCP The Secure Shell (SSH) protocol is a cryptographic network protocol that allows secure network services over an unsecured network. It uses a client-server architecture to connect an SSH client to an SSH server. Any Network Service Common: ● Remote Comman d-line ● Login ● Remote Comman d Execution SSH was meant to replace FTP (Port 21) and TELNET (Port 23), which is why it was assigned Port 22. DNS 53 UDP/TCP The Domain Name System (DNS) protocol is a detailed specification of all data structures and communication exchanges used in the Domain Name System. Human-readable Hostnames for Websites DNS functions as the phonebook for the Internet. SMTP 25 TCP The Simple Mail Transfer Protocol (SMTP) is a communication protocol for email. Email SMTP is believed to have roots in the Mail Box Protocol (disputed implementation). FTP 20, 21 TCP The File Transfer Protocol (FTP) is a network protocol to transfer computer files. It uses a client-server architecture to connect an FTP client with an FTP server. File Transfer I didn’t find anything really interesting about this one. Let me know in the comments if you do. TFTP 69 UDP The Trivial File Transfer Protocol (TFTP) is a lockstep file transfer protocol used for transferring files. Nodes Booting From a LAN As the name suggests, TFTP has a simple design and limited features, therefore it has a small memory footprint. TELNET 23 TCP The TELNET (Teletype Network) protocol is an application protocol to provide bi-directional eight-bit byte oriented communications. It is used as a method of interfacing terminal devices and terminal-oriented processes. ● ● Remote Manage ment Initial Device Setup for Network Hardware Not only does TELNET communicate over port 69, it was also developed in 1969. DHCP 67, 68 UDP The Dynamic Host Configuration Protocol (DHCP) is a network protocol used by DHCP servers to respond to queries by clients to be set up on the network. Without DHCP servers, network admins would have to manually set up every client that joins the network. Communicating network parameters DHCP is based on the Bootstrap Protocol (BOOTP). HTTP 80 TCP The Hypertext Transfer Protocol (HTTP) is a network protocol for distributed and collaborative hypermedia information systems. HTTP uses the client-server computing model and acts as a request-response protocol. For example, in this situation, a user's web browser may be the client, while the computer hosting the web application they are accessing through their browser would be the server. Data Communication on the World Wide Web HTTP development started at CERN in 1989. Yes, that CERN. HTTPS 443 TCP The Hypertext Transfer Protocol Secure (HTTPS) is the secure communication extension of HTTP. The communication protocol in HTTPS is encrypted using TLS. Secure Data Communication on the World Wide Web HTTPS is meant to provide all that HTTP does, with added authentication, privacy, and integrity through bi-directional encryption. The Simple Network Management Protocol (SNMP) is a protocol to help communicate management information for devices on the network. This can include routers, modems, switches, servers, workstations, printers, etc. Network Management and Monitoring I didn’t find anything really interesting about this one. Let me know in the comments if you do. TCP/UDP The Remote Desktop Protocol (RDP) is a network communications protocol for remote management and access. Remote Access of Windows and macOS. This protocol is proprietary and developed by Microsoft. 123 UDP The Network Time Protocol (NTP) is a network protocol to synchronize clocks between devices to within a few milliseconds of Coordinated Universal Time. Time Synchronization: Air traffic control was an early application of NTP. NTP uses the intersection algorithm to choose time servers and prevent network latency issues. SIP 506 0, 506 1 TCP/UDP The Session Initiation Protocol (SIP) is a protocol used for real-time voice, video, and messaging sessions. Communication Over Voice, Video, and Messaging SIP is lauded for having been established in the Internet community instead of the telecommunications community. SMB 445 TCP/UDP The Server Message Block (SMB) protocol is a protocol used to share files, printers, serial ports, and communications abstractions between devices. File Sharing I didn’t find anything really interesting about this one. Let me know in the comments if you do. POP 110 TCP The Post Office Protocol (POP) is a protocol that is used to retrieve email from a mail server in conjunction with SMTP. Email Retrieval The name speaks for itself. IMAP 143 TCP The Internet Message Access Protocol (IMAP) is a protocol to retrieve email from a mail server. Email Retrieval The main difference between POP and IMAP is that IMAP allows synchronization between devices and the mail server. LDAP 389 TCP/UDP The Lightweight Directory Access Protocol (LDAP) is a protocol for maintaining distributed directory information services. This is User Validation Through Storage of Usernames and Passwords LDAP was used for the basis of Microsoft Active Directory. SNMP 161 UDP RDP 338 9 NTP important to help share information about users, systems, networks, services, and applications. LDAPS 636 TCP/UDP The Lightweight Directory Access Protocol over SSL (LDAPS) is a method of securing LDAP using an SSL tunnel. User Validation Through Storage of Usernames and Passwords, Securely I didn’t find anything really interesting about this one. Let me know in the comments if you do. H.323 172 0 TCP H.323 is a series of protocols for audio-visual communication. It specifically addresses call signaling and control, multimedia transport and control, and bandwidth control. Voice and Video Conferencing Though H.323 was originally meant for videoconferencing over LAN, it quicky spread to a variety of networks including WAN and the Internet. Related Definitions ● ● ● ● ● ● ● ● ● ● Protocol ○ A protocol is a set of rules to determine how to act in a given situation. Cryptographic Protocol ○ A cryptographic protocol is a set of rules to allow secure communication under a given set of circumstances. Client-server Architecture ○ Client-server architecture is an architecture of a computer network that allows clients, or client computers, to request services from a server, or host computer. Domain Name System ○ The Domain Name System (DNS) is a decentralized, hierarchical naming system for devices connected to the Internet or a private network. Decentralized System ○ A decentralized system is one in which some components operate on local information instead of all being tied to the same source. Lockstep ○ Lockstep systems are systems that run the same set of operations at the same time in parallel so they may be fault-tolerant. This allows error detection and correction, since the outputs can be compared and corrected with at least three parallel systems. Local Area Network ○ A local area network (LAN) is a computer network that connects computers in a small (or local) area, such as a house. Transport Layer Security ○ Transport Layer Security (TLS) is a cryptographic protocol to secure communications on a computer network. Directory Service ○ A directory service is responsible for mapping network resources to network addresses. SSL Tunnel An SSL tunnel is a communications protocol used to move data from one network to another securely using SSL. Datagrams ○ Datagrams are a basic transfer unit with a header and payload section transmitted on the network. ○ ● Protocol Types ● ● ● ● ● ● ICMP ○ Internet Control Message Protocol (ICMP) is a supporting protocol for network devices. It allows them to send error messages and operational information regarding success or failure during communication with other devices. Unlike TCP and UDP, ICMP is not used for data exchange or for end-user network applications (except ping and traceroute). UDP ○ User Datagram Protocol (UDP) is a protocol to send messages to other devices on the network without the need for previous communications. UDP is fast, but not necessarily as reliable as TCP. TCP ○ Transmission Control Protocol (TCP) is a protocol to send bytes between devices on a network. It is reliable, ordered, and error-checked on delivery, unlike UDP, which is much faster but more error-prone. IP ○ Internet Protocol (IP) is the OG network communications protocol for relaying datagrams to other devices across network boundaries. The IP enables internetworking, the foundations of the Internet. Connection-oriented ○ A connection-oriented protocol is a protocol where data transmission relies on an established connection. A stream of data must be delivered in the appropriate order and a communication session has to be established before data can be sent. Connectionless ○ Connectionless communication is data transmission that does not rely on an established connection. Each data unit is addressed and routed based on the information it contains, therefore, any particular message can be sent without previous communications being established, and data units can arrive in any order. 1.2 Explain devices, applications, protocols, and services at their appropriate OSI layers. The Open Systems Interconnection (OSI) model is a standardized, conceptual model to help devices to communicate with each other. It splits communication into seven stacked layers, each of which is able to communicate with the layers above or below itself. When data is flowing through the OSI model, data on the sending device travels down, while data on the receiving device travels up. Something interesting to note: denial of service attacks target parts of the network layer. Application layer attacks target the application layer. And protocol attacks target the protocol layer. Makes sense! Layer 7: Application The application layer is the layer used to communicate with the user; applications like web browsers and email rely on the application layer for communication. Applications are not part of the application layer. They use the application layer to communicate. Layer 6: Presentation The presentation layer does just what it says: it makes data “presentable” for the application layer. Think things like data translation, encryption, and compression. Day to day, the presentation layer may need to work with the application layer or the session layer. It translates incoming data so the application layer on the device can understand it, and it also adds encryption/decryption as necessary. The presentation layer may also compress data coming in from the application layer that it will then efficiently pass on to the session layer. Layer 5: Session The session layer opens and closes sessions between devices (hence, the session layer. I’m sensing a pattern…). The session layer makes sure the session is open for as long as needed, can quickly close the session, and can synchronize data transfers with checkpoints. Checkpoints help keep everything connected - if a session layer has a checkpoint every five megabytes for a 100 megabyte file, but the file gets cut off at 44 megabytes, the session layer will reconnect and transfer starting from the 40 megabyte mark (the latest checkpoint). Otherwise, it would have to start from scratch every time a session is interrupted. Layer 4: Transport The transport layer is responsible for end-to-end communication on the network between devices; specifically, the transport layer receives and outputs data without errors. Typically, the sending device breaks down application messages into segments that are then passed on to the network layer. Contrastingly, the receiving device reassembles segments into messages, which can then be passed to the application layer. Layer 3: Network The network layer is responsible for the facilitation of data transfer between devices on different networks. The network layer is unnecessary if the devices are on the same network (more about that in the data link layer). On the sender device, the network layer is responsible for packets: it creates packets from the segments passed in from the transport layer. On the receiver device, the network layer reassembles the packets before sending them to the transport layer. The network layer is also responsible for routing, finding an optimized path to pass data through. Layer 2: Data Link The data link layer is responsible for data transfer between devices on the same network. The data link layer takes in data on the network and segments them into frames. It is also responsible for flow control and error control for devices on the network. Layer 1: Physical The physical layer is responsible for the physical equipment necessary for data transfer, things like the cables and switches. It’s also where data is converted into a bit stream. In order to properly align, the physical layer on both devices must agree on a signal convention. 1.3 Explain the concepts and characteristics of routing and switching. Properties of Network Traffic ● ● ● ● ● ● ● ● ● Broadcast Domains ○ Broadcast domains forward packets to all the machines on the network. It will only go to the machines on the network, no more than that, and they do not cross network boundaries. CSMA/CD ○ Carrier-Sense Multiple Access with Collision Detection (CSMA/CD) is a MAC protocol for local area networking used with Ethernet technology. The Collision Detection part references a method of detecting collisions with other information being sent via transmissions from other stations. CSMA/CA ○ Carrier-Sense Multiple Access with Collision Avoidance (CSMA/CD) is a wireless network multiple access method that allows travel of entire packets without collisions. It uses carrier sensing with nodes, which try to avoid collisions when they sense that the channel is idle. However, it is unreliable. Collision Domains ○ Collision domains are segments of the network that connect through a shared medium and are susceptible to simultaneous colliding data transmissions. This can happen for both wireless and early Ethernet networks. Protocol Data Units ○ Protocol data units (PDUs) are single units of information transmitted between devices on a computer network. This includes protocol-specific control data and user data. For TCP, the protocol data unit is a segment, while for UDP, the protocol data unit is a datagram. MTU ○ Maximum transmission units (MTUs) are the largest possible PDUs that can be transmitted through a single network layer transaction. Typically, the larger the MTU, the less overhead. However, the smaller the MTU, the less network delay. It’s a tradeoff. Broadcast ○ A broadcast is when a device is sending packets to multiple receivers at once, including all of the hosts connected to the network. This is known as all-to-all. Multicast ○ A multicast is when a device is sending packets to multiple receivers at once, but only to those that are intended recipients. This is known as one-to-many routing, or can be used for many-to-many routing. Unicast ○ A unicast is when a device is sending packets to a single receiver at once. This is known as one-to-one routing. Segmentation and Interface Properties ● ● VLANs ○ Virtual LANs (VLANs) are a group of devices in the same broadcast domain. What makes VLANs different from physical LANs is that hosts can be grouped together even if they are not connected to the same switch. Trunking (802.1Q) ○ Trunking is connecting two VLANs such that traffic may pass between them. 802.1Q is merely the trunking protocol. It is the most common trunking protocol and is standardized across vendors. ● ● ● ● ● ● ● Tagging and untagging ports ○ Tagged ports are a way of identifying that a packet belongs to the appropriate VLAN. The packets are tagged with a VLAN tag in the Ethernet frame. This is the core difference between tagged and untagged packets: tagged packets have VLAN information, untagged packets do not. Port mirroring ○ Port mirroring is where a device (Device A) on the same switch as another device (Device B) can “listen” to the incoming traffic on Device A. Device B receives a copy of every network packet seen going to Device A. Whether or not this is allowed depends solely on whether or not the switch Devices A and B are connected to supports port mirroring. Switching loops/spanning tree ○ A switching loop occurs when two endpoints are connected by more than a single Layer 2 path. This is meant to be addressed by the Spanning Tree Protocol. ○ The Spanning Tree Protocol (STP) is a layer 2 protocol to prevent loops from redundant paths in a network. It uses the Spanning Tree algorithm to ensure there are no loop paths in the network with Bridge Protocol Data Units (BPDUs), to identify redundant paths. PoE and PoE+ (802.3af, 802.3at) ○ Power over Ethernet (PoE) is a system dedicated to powering and transmitting data over twisted pair Ethernet cabling. The main difference between PoE and PoE+ is the power provided. Needless to say, PoE+ is much more. DMZ ○ The demilitarized zone (DMZ), a term taken from the military, is the physical or logical subnetwork. It is the interface between the local area network (LAN) and the Internet. This includes devices like public servers, resources, or servers. MAC Address Table ○ The MAC Address Table identifies where to forward traffic on a LAN for Ethernet switches. ARP Table ○ Address Resolution Protocol Table (ARP Table) correlates MAC addresses to corresponding IP addresses. Routing ● Routing protocols (IPv4 and IPv6) ○ Routing protocols are used to identify routes on the network, create routing tables, and make routing decisions. ○ Distance-vector routing protocols ■ Distance vector routing protocols use the hop count to determine the best route to take. This protocol will continuously send neighboring routers a copy of its routing table to make sure they are aware of the latest. ○ RIP ■ Routing Information Protocol (RIP) is a distance vector routing protocol that uses the hop count to determine the best path. ○ EIGRP ■ Enhanced Interior Gateway Routing Protocol (EIGRP) is a distance vector routing protocol able to automate routing decisions and configurations. It is only available on Cisco routers. ○ Link-state routing protocols ■ Link-state routing protocols is the yang to distance-vector routing protocols yin. Link state routing happens at every switching node in the network, where switching nodes on the Internet are also known as routers. Each node creates a map of the other nodes they are connected to and calculates the best and most logical path for the packet to take. ○ ● OSPF ■ Open Shortest Path First is a routing protocol that uses link state routing. OSPF is a common IGP used in larger enterprise networks. ○ Hybrid ■ The Hybrid Routing Protocol is a combination of distance vector routing and link state routing. It uses distance vectors for the most accurate distance metrics, but only sends routing information when there is a change in network topology. This requires less processing power than typical link-state routing. ○ BGP ■ Border Gateway Protocol (BGP) is an exterior gateway protocol for transmitting routing and reachability information between autonomous systems. Routing types ○ Static ■ Static routing is routing that requires the manual configuration of a routing entry. They are typically configured by network administrators, who add entries to a routing table. ○ Dynamic ■ In contrast, dynamic routing adapts to the existing conditions between communication circuits to avoid existing damages to the network. IPv6 Concepts ● ● ● ● ● Addressing ○ IPv6 addressing is how we interface with and find a device on the network. IP addresses get transmitted in packet headers as the source and destination of a particular packet. Tunneling ○ IPv6 tunneling is how to use the routing infrastructure from IPv4 for IPv6 traffic. Basically, this comes down to encapsulating IPv6 datagrams within IPv4 packets. Dual stack ○ Dual stack refers to creating a system where devices may run IPv4 and IPv6 simultaneously. This is particularly important as organizations transition from IPv4 to IPv6. Router advertisement ○ Router Advertisement Daemon (RADVD) is a way of automatically configuring devices joining the network for IPv6. If this is enabled, autoconfiguration of the device’s IPv6 address, subnet prefix, and default gateway can occur. If it is disabled, this must be done manually, typically by the network administrator. Neighbor discovery ○ The Neighbor Discovery Protocol (NDP) gathers information for Internet communication. This can include configuration information for local connections, domain name servers, and gateways for connecting with other systems. Performance Concepts ● ● Traffic shaping ○ Traffic shaping prioritizes bandwidth based on the type of network packet. Network packets with higher priority are ensured better network performance. QoS ○ ● ● Quality of Service (QoS) is the quantitatively measured performance of the network. It can be based on packet loss, bit rate, throughput, transmission, availability, delay, jitter, or more. DiffServ ○ Differentiated Services (DiffServ) is a networking architecture for managing network traffic and ensuring QoS. CoS ○ Class of Service (CoS) is the parameter for assigning priorities to packets on the network. Other Concepts ● ● ● ● ● ● NAT/PAT ○ Network Address Translation (NAT) is the way to remap an IP address space into another. It involves altering the network address information, which is in the IP header of the packets, while they are moving across a traffic routing device. ○ Port Address Translation (PAT) is the equivalent of NAT, but with ports. It is the way to translate ports. Port forwarding ○ Port forwarding is an application of NAT where not only is the IP address space remapped, but the port number is as well. This lets devices on the Internet connect to devices on a LAN. Access control list ○ An access control list is a list of conditions to filter network traffic. Distributed switching ○ Distributed switching is where a distributed switch acts as the sole virtual switch. It is used to maintain consistent network configurations as VMs move around several hosts. Packet-switched vs. circuit switched network ○ Packet-switched networks move data via packets. These packets can be sent in any order, as they are rearranged at the destination based on information in the packet header. In contrast, circuit-switched networks require point-to-point connections that are consistent and maintained until the data is transmitted. With circuit-switched networks, an entire channel must be dedicated to a single interaction. In contrast, packet-switched networks can maintain a single channel for multiple communications simultaneously. Software-defined networking ○ Software-defined networking (SDN) is a method of network management where the network configuration is dynamically upgraded to be the most efficient possible. THe goal is to improve network performance and monitoring. Helpful Definitions ● ● ● ● MAC ○ Medium Access Control (MAC) controls hardware that interacts wired, optical, or wireless transmissions. The data link layer is made up of the MAC layer and the logical link control (LLC) layer. Carrier wave ○ A carrier wave is used to send information at a higher frequency than the input signal, so it can allow several different carriers to transmit at once on the same transmission medium. Multiple Access Method ○ The multiple access method is a method that lets more than two terminals share one transmission method. Ethernet over twisted pair ○ ● ● Ethernet over twisted pair are twisted pair cables used for the physical layer of an Ethernet computer network. Interior Gateway Protocol ○ The Interior Gateway Protocol (IGP) is a protocol used to exchange router information. IGPs are divided into distance vector routing protocols and link-state routing protocols. Autonomous Systems ○ An autonomous system (AS) is a group of routers where their prefixes and routing policies are all controlled by the same administrator. This may be a Network Service Provider, a large business, a university, or other larger organizations. 1.4 Given a scenario, configure the appropriate IP addressing components. ● ● ● ● ● ● Private vs. public ○ A private IP address is the address a device uses to communicate within their network. ○ A public IP address is the address used to communicate publicly outside of the local network. Loopback and reserved ○ Loopback is the range of IP addresses reserved for the localhost address. It is entirely maintained on the device’s operating system. ○ Reserved IP addresses are addresses that have been reserved by the IETF and the IANA for special purposes. Default gateway ○ A default gateway is a device on the network that forwards packets to other networks and eventually on to their destination. A router is an example of a default gateway. Virtual IP ○ A Virtual IP address (VIP) is an IP address that isn’t actually for a physical network, but instead is used for things like NAT and fault tolerance. Subnet mask ○ A Subnet mask is what separates an IP address into network and host addresses. This takes the form of <network><subnet><host> to give additional subnetworks. Subnetting ○ Classful ■ Classful networks divide the IPv4 address space into five different classes: A, B, C, D, and E. ■ Classes A, B, C, D, and E ● Class A: Class A contains all addresses where the most significant bit is 0; this can accommodate 128 networks. ● Class B: Class B contains all addresses where the two most significant bits are 1 and 0; this can accommodate 65,536 addresses per network. ● Class C: Class C contains all addresses where the three most significant bits are 1, 1, and 0; this can accommodate 256 local addresses. ● Class D: Class D is reserved for multicasting and contains all addresses where the four most significant bits are 1, 1, 1, and 0. ● Class E: Class E is reserved for experimentation only and ranges from 240.0.0.0 to 255.255.255.254. ○ Classless ■ VLSM ● Variable-length Subnet Masks (VLSMs) use more than one mask for the same classful network. AKA, VLSMs subnet the subnet. ■ CIDR notation (IPv4 vs. IPv6) ● ● Classless Inter-Domain Routing (CIDR) is a method of allocating IP addresses introduced by the IETF. It was meant to replace classful networks and reduce the exhaustion of IPv4 addresses. CIDR is based on VLSM. Address assignments ○ DHCP ■ There are three different ways DHCP assigns IP addresses: ● Automatic Allocation: DHCP servers assign a permanent IP address from their dedicated IP Pools. ● Dynamic Allocation: DHCP servers assign a reusable IP address from their dedicated IP Pools. This only lasts for a set amount of time and is known as a lease. ● Static Allocation: Static allocation occurs when the network administrator manually assigns an IP address, which the DHCP server is then responsible for sending along to the client. These are permanent. ○ DHCPv6 ■ Dynamic Host Configuration Protocol version 6 (DHCPv6) is the IPv6 equivalent of DHCPv4. ■ Manual ● A manual assignment is typically completed by a network administrator, but this can be error-prone. ■ Stateless Address Autoconfiguration ● Stateless Address Autoconfiguration (SLAAC) is a way to assign IP addresses without needing a network administrator. Instead, the admin configures the router, which then sends Router Advertisement announcements to the devices on the network. This lets the devices configure themselves. ■ Stateful DHCPv6 ● Stateful DHCPv6 is a counterpart to Stateless Address Autoconfiguration that allows configuration parameters to be passed to IPv6 nodes. ■ DHCPv6-PD ● DHCPv6 Prefix Delegation (DHCPv6-PD) is used to assign a complete subnet from a DHCPv6-PD server to a DHCPv6-PD client. Instead of a single address assignment, DHCPv6-PD assigns an entire set of IPv6 subnets. ■ Stateless DHCPv6 ● Stateless DHCPv6 uses SLAAC to assign IPv6 addresses and DHCPv6 to add more parameters like DNS or NTP server addresses. ○ Static ■ Static IP addresses are IP addresses that have been manually configured, typically by a network administrator. ○ APIPA ■ Automatic Private IP Addressing (APIPA) is a way for a device on the network to discover an address on its own. When getting an IPv4 address, the device can select an address at random between 169.254.1.0 to 169.254.254.255 with a netmask of 255.255.0.0. The device sends an ARP packet for the MAC address associated with the IP address, and if it is not accepted (because the address is already taken), it will try a new IP. ○ EUI64 ■ Extended Unique Identifier (EUI64) is a way of automatically configuring IPv6 host addresses. This is meant to eliminate the need for manual configuration or DHCP, popular methods in IPv4. ○ IP reservations ■ With IP reservations, IP addresses are automatically assigned and managed without requiring addresses be set aside for exclusive use by certain devices. IP addresses are reserved and associated with a unique MAC address, so when a device requests an IP renewal, they may get the same IP. Helpful Definitions ● ● ● ● Internet Engineering Task Force ○ The Internet Engineering Task Force (IETF) is an organization that establishes standards for the Internet, especially when it comes to TCP/IP. Internet Assigned Numbers Authority ○ The Internet Assigned Numbers Authority (IANA) oversees global IP address allocation, Internet numbers, number allocation, root zone management, and other IP protocol-related systems. ARP ○ Address Resolution Protocol (ARP) is used to map IP addresses to their Ethernet addresses. ARP packets typically start a conversation between two devices. Stateful vs Stateless ○ Stateful IP addresses provide a log that certain IP addresses were assigned to a specific MAC address. ○ Stateless IP addresses are more dynamic and are used to determine a device’s IP address at the time for that particular network. 1.5 Compare and Contrast the Characteristics of Network Topologies, Types, and Technologies ● ● Wired Topologies ○ The actual physical layout of the cables that connect computers on the network. ○ Logical vs Physical ■ A logical topology is a way of visualizing the network with respect to how data flows, as opposed to what it actually may look like. ■ A physical topology is how the network is actually physically laid out, across network cables and devices. ○ Star ■ In a star topology, each device is connected to a central access point. ○ Ring ■ In a ring topology, each device is connected to the other devices in the network in a ring. This is considered an obsolete network topology. ○ Mesh ■ In a mesh topology, each device on the network connects directly to any other device on the network. In the past, this needed to be wired, which made it expensive and difficult to sacale. ○ Bus ■ In a bus topology, each device is connected linearly to the next, starting at the server and ending with the last device on the network. This is considered an obsolete network topology. Wireless Topologies ○ Mesh ■ In a mesh topology, each device on the network connects directly to any other device on the network. These connections are non-hierarchical, and this type of network self-organizes and self-configures to efficiently route data. ○ Ad hoc ■ ○ A wireless ad hoc network (WANET) is a decentralized network that does not have a defined infrastructure. Each device on the network works together to pass data based on routing algorithms and network connectivity. Infrastructure ■ An infrastructure wireless topology is centralized. Specific devices are used as access points for other devices on the network. Network Types by Spatial Scope, Michel Bakni Network Acronym Network Type Description LAN Local area network A local area network (LAN) is a network that connects devices in a small (or local) area, such as a house, over Ethernet. WLAN Wireless local area network A wireless local area network (WLAN) is a network that connects devices in a local area. It differs from a traditional LAN because it uses Wi-Fi instead of Ethernet. MAN Metropolitan area network A metropolitan area network (MAN) is a network that connects devices in a larger geographic region the size of a metropolitan area. WAN Wide area network A wide area network is a network that connects devices across a large geographic area. A WAN can connect smaller networks like MANs and LANs, so devices can communicate across vast locations. CAN Controller area network A controller area network (CAN bus) is a standard for microcontrollers that lets them communicate without a host. When a device communicates, the communication is sent to all devices, including itself. SAN Storage area network A storage area network (SAN) is a high-speed network for easy access to storage. Storage devices are presented to the host as though they are attached locally, which can be used for business continuity management. PAN ● Personal area network A personal area network (PAN) is a network for connecting an individual’s devices together. Technologies that facilitate IoT ○ Z Wave ■ Z Wave is a mesh network communications protocol that uses low-energy radio waves to help home automation devices communicate. ○ ANT+ ■ Advanced Network Topology (ANT+) is a low-power version of ANT. ANT+ and ANT are wireless network technology to allow sports sensors to communicate. The technology is owned by a division of Garmin Canada, though it is open access. ○ Bluetooth ■ Bluetooth is a well-known wireless technology that allows devices to communicate with each other at a short range. A lot of technology used every day uses Bluetooth, like Bluetooth headphones. ○ NFC ■ Near-field Communication (NFC) is a communications protocol that allows devices to communicate with each other at an incredibly short range, 1.5 inches or less. NFC is very common with touchless payment systems and some keycards. ○ IR ■ Infrared (IR) is a wireless technology used to send data through infrared radiation. It’s often used in intrusion detection, for cordless headsets, and for printers. IR cannot travel through walls, which limits its implementation capabilities. ○ RFID ■ Radio frequency identification (RFID) uses electromagnetic fields to identify objects. RFID tags contain a radio transponder that can be triggered from an electromagnetic pulse from a RFID reader, which transmits information identifying the object. RFID tags are used in a lot of applications and have faced privacy concerns. ○ 802.22 ■ IEEE 802.22 is a wireless regional area network (WRAN) standard. It uses unused sections of TV broadcast frequency to communicate, in order to give broadband access to low population density, rural areas. 1.6 Given a Scenario, Implement the Appropriate Wireless Technologies and Configurations 802.11 is the IEEE wireless networking standard. Variations differ in terms of speed, data rates, frequency, and other factors, but they are all implemented in a similar way: ad hoc or infrastructure topologies. IEEE Standard Frequency Data Rate (Mbps) Range (ft) 802.11 2.4 GHz RF 1 - 2 Mbps 20 ft 802.11a 5 GHz 54 Mbps 25 - 75 ft 802.11b 2.4 GHz 11 Mbps 150 ft 802.11g 2.4 GHz 54 Mbps 150 ft 802.11n 2.4 GHz/ 5 GHz 600 Mbps 175 ft 802.11ac 5 GHz 2.5 Gbps 175 ft Data collected from P earson. ● ● ● ● ● ● ● Cellular ○ GSM ■ The Global System for Mobile Communications (GSM) is a standard developed by the ETSI for second-generation (2G) cellular networks. It became the global standard for mobile communications with over 90% market share. ○ TDMA ■ Time-division multiple access (TDMA) is a cellular communications technology to ensure multiple individuals can use the same frequency without interference. ○ CDMA ■ Code-division Multiple Access (CDMA) is a channel access method, whereby several devices can communicate over the same channel at the same time. Frequencies ○ 2.4 GHz ■ 2.4 GHz transmits data slower, but has a large range. ○ 5.0 GHz ■ 5.0 GHz transmits data quickly, but has less range. The higher the frequency, the faster the data transmission. Its range is largely limited by its inability to pass through solid objects. Channel Bandwidth ○ Channel bandwidth changes the data transmission rate; higher bandwidth means faster connection. Channel Bonding ○ Channel bonding combines two channels with the same frequency to increase throughput. It is very common in Wi-Fi applications. MIMO/MU-MIMO ○ Multiple input, multiple output (MIMO) and multi-user, multiple output (MU-MIMO) are wireless network technology. MU-MIMO is the next evolution of MIMO, which enables devices with multiple antennas to communicate with one another. MIMO solely allowed a single antenna to communicate with another single antenna. Unidirectional/omnidirectional ○ A unidirectional network is a device that only allows data to flow in a single direction. This is commonly used in military bases, nuclear power plants, and other critical infrastructure, that need to ensure security. This is also known as a data diode. ○ An omnidirectional antenna is a type of antenna that sends equal radio power in every direction perpendicular to the antenna. This creates a donut-like radiation pattern. Site surveys ○ A wireless site survey is a way of designing a wireless network such that it will meet QoS, data rates, and coverage requirements. Helpful Definitions ● ● ETSI ○ The European Telecommunications Standards Institute (ETSI) is a standardization organization for telecommunications. Channel Access Method ○ A channel access method ensures that two devices can communicate over the same transmission medium at the same time. 1.7 Summarize cloud concepts and their purposes ● ● ● Types of services ○ SaaS ■ Software-as-a-Service (SaaS) is a form of cloud computing and a software distribution model. A third-party hosts applications for end users, typically for a subscription fee. ○ PaaS ■ Platform-as-a-Service (PaaS) is a form of cloud computing and an architecture wherein a third-party hosts a platform for end users, typically for a subscription fee. Users can develop, run, and manage business applications, all using the third-party infrastructure. ○ IaaS ■ Infrastructure-as-a-Service (IaaS) is a form of cloud computing and an architecture wherein virtualized computing resources are provided by a third-party to a user, typically for a subscription fee. Cloud delivery models ○ Private ■ Private clouds are a cloud delivery model where an organization can keep the necessary hardware locally managed. Access to applications in the private cloud can happen from anywhere, but the workloads are managed by the organization and delivered over WAN. ○ Public ■ Public clouds are a cloud delivery model where an organization uses a third-party for the physical hardware of their servers. IT staff can easily provision new cloud resources, which is why public clouds often follow a pay-as-you-go model. ○ Hybrid ■ Hybrid clouds are a h ybrid of private and public clouds. They are cloud delivery models where third-party resources are accessible, but are used to augment a private cloud. Connectivity methods ○ Cloud connectivity methods are the different ways to connect to cloud providers. ○ VPN ■ A virtual private network (VPN) gives a device an encrypted connection to a server over the Internet. ● Positives: VPNs are encrypted, and VPNs give IT admins a lot of control over who can access the network. ● Negatives: slow data speeds and increased network complexity, which means it is more difficult for IT teams to support. ○ RDS ■ ○ ● ● A remote desktop server (RDS) is a user interface for interacting with a server; all data is stored remotely, and every user interaction is sent back to the server. ● Positives: RDS has low bandwidth requirements and few servers are needed. ● Negatives: all users have the same interface, which limits customization, and there can be security concerns given that all users are accessing the same server. VDI ■ A virtual desktop infrastructure (VDI) is a dedicated space on a server for each user, much like RDS, except VDI allows for individual configuration of the user interface. ● Positives: users get a customized interface, less storage capacity is required, and applications, patches, and drivers are all managed centrally. ● Negatives: Compute requirements are high, and licensing costs are high. Security implications and considerations ○ Lack of Control ■ The biggest security implications from cloud computing seem to stem from one source: lack of control. As assets are moved to public clouds, organizations simply have less control over them. They are trusting another organization to manage their assets. ○ New, Unapproved Services ■ The cloud enables easy provisioning of new services, which means the IT department does not necessarily know or approve the cloud services a user is running. ○ Malware Infections ■ Given the amount of data organizations are storing on the cloud and the number of users accessing it, malware infections become more likely. ○ Compliance Issues ■ The cloud makes it easy to access a lot of data at once. This can pose issues for organizations that must meet HIPAA regulations, or GDPR. Relationship between local and cloud resources ○ Local Resources ■ Positives: Inexpensive, easy to use, and the data is 100% under the organizations control (for compliance and security purposes). ■ Negatives: Need to house the hardware, need to have fail safes in case the hardware fails, can potentially be stolen. The organization is entirely responsible for the security and management of the hardware. ○ Cloud Resources ■ Positives: Easily connect over the Internet, no physical storage necessary, small amounts of data can be stored for free or very low cost. ■ Negatives: Can be expensive depending on the resource usage, requires an internet connection to access, may be difficult to ensure compliance. 1.8 Explain the functions of network services ● DNS service ○ A DNS hosting service is the service that runs domain name system servers. The vast majority of domain name registrars include DNS hosting on registration. ○ Record types ■ A, AAAA ● A records are the most common kind of DNS record. They are used to translate domain names into IP addresses. Type A records are for Ipv4, while type AAAA are for IPv6. ■ ● TXT (SPF, DKIM) ● TXT records have text about a domain name, like the host, the main contact, and associated information. ● Sender Policy Framework (SPF) serves as an email authentication process to prevent spam. ● DomainKeys Identified Mail (DKIM) serves as an email authentication process so organizations may use public key cryptography to verify a message is sent from an authorized mail server. ■ SRV ● SRV records are used to state the location of a service, in three parts: service, protocol, and domain name. The actual service location is of four parts: priority, weight, port, and target. ■ MX ● Mail exchange records (MX) identify the email server associated with a particular domain name. MX records contain: the name of the email server and a number that decides preference for that server. ■ CNAME ● CNAME records are aliases for the particular domain name. ■ NS ● NS records identify which DNS servers correspond to which zone. ■ PTR ● PTR records translate IP addresses to domain names. They are often known as ‘reverse records’ from A and AAAA records. ○ Internal vs external DNS ■ An external DNS server is responsible for public DNS queries to a particular network. ■ An internal DNS server is responsible for not only the public DNS information about a particular network, but also additional information on internal hosts and services. ○ Third-party/cloud-hosted DNS ■ Third-party/cloud-hosted DNS is considered IaaS, basically a managed DNS server. They can benefit organizations by providing geographically diverse infrastructure and a reduction in cost, depending. ○ Hierarchy ■ The DNS hierarchy is responsible for managing a domain and its subdomains. It is a distributed database system in an inverted tree structure. Each domain name is an entity’s position in the DNS hierarchy. ○ Forward vs reverse zone ■ A forward lookup is when a DNS looks up the IP address of a device based on the hostname value. ■ A reverse lookup is when a DNS looks up the hostname based on the IP address. DHCP service ○ MAC reservations ■ DHCP reservations - specifically MAC reservations - ensure the IP address for the devices on your network use the same IP address consistently. ○ Pools ■ DHCP address pools are pools of IP addresses that the device managing the network can use to assign a client an address. ○ IP exclusions ■ ○ ○ ○ ○ ● ● NTP ○ IP exclusions are the IP addresses that are excluded from being assigned to client devices. Exclusions are based on which IP addresses are already assigned, therefore they will never be assigned automatically to any client devices. Scope options ■ DHCP scope is the set of IP addresses that can be assigned to client devices. The scope options include the DNS server, domain name, and gateway. Lease time ■ DHCP lease time is the time a device has to use the IP address it has been assigned. After that lease time, if the device is no longer connected, the address expires and is reassigned elsewhere. TTL ■ Time-to-live (TTL) is the set amount of time or number of hops before a packet is removed from the network. This is important for those instances where a packet gets “lost” on the network, or to track information on a packet such as how long it has been in transit. DHCP relay/IP helper ■ A DHCP relay is a host or router responsible for forwarding packets to other devices on the network. ■ IP helpers allow devices to act as a middle man to forward DHCP requests to the requested server. The Network Time Protocol (NTP) is a network protocol to synchronize clocks between devices to within a few milliseconds of Coordinated Universal Time. NTP servers are servers that help in that effort and that can be queried by other devices. This is considered a foundational network service. IPAM ○ IP Address Management (IPAM) encompasses how IP address space used in a network is planned, tracked, and managed. This typically involves the use of DNS and DHCP in tandem. Helpful Definitions ● Zone ○ A zone is a domain, not including the subdomains delegated to other DNS servers. Thanks again for downloading this PDF. I hope it was useful for you. If you have any questions about this, head to my website hackerbella.xyz and comment on the blog. I’m happy to help. - Allie Mellen