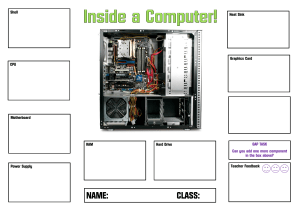
Computer Science Worksheet Chapters 3, 4, 5 Q1: Give the suitable word for the following definitions. ________CPU_________: A component in a computer system that processes data and instructions. _____microprocessor_______: An integrated circuit that is able to perform many of the functions of a CPU. __internet of things__: The connection of computer systems and everyday devices, using the internet to allow data to be exchanged. ________RAM_________: A component in the CPU that holds data and programs that is currently in use. _____input device________: A device that allows data to be entered into a computer system. ____hard drive______: A storage device that stores data permanently until it is deleted by the user. ____address bus________: Wires used for the transmission of addresses between components in a computer. _________MAR___________: A component in the CPU that holds the address of the data or instruction to be located in RAM. _______CU_______: A component in the CPU that controls all the operations in the CPU. ______instruction set______: A set of commands that can be processed by a certain CPU. _______virtual memory_______: A type of memory that can be used as an extension to the RAM. Q2: In which way the data and instructions are given to the computer? By an input device Q3: Explain the role of the arithmetic logic unit (ALU). Component in the CPU that performs all the mathematical and logical operations when processing data and instructions Q4: What are the wires used for the transmission of control signals between components in a computer? Control bus Q5: Give 3 examples of: Input devices: Scanner, microphone and keyboard Output devices: Printer, screen projector and speakers Q6: Choose (True or False) for the following statements. 1- Output device is a device that can be used to obtain the results of data that has been processed. (True - False) 2- Input device is a device that allows data to be entered into a computer system. (True - False) 3- Automated system is a system that is designed to operate with the need for human intervention. (True - False) 4- Sensor is a type of input device that is used in an automated system. (True - False) 5- Primary storage is a type of storage that is designed to store data permanently until it is deleted by the user. (True - False) 6- Primary storage is a type of storage that is directly accessed by the CPU. (True - False) 7- ROM stands for read only memory. (True - False) 8- RAM stands for random access machine. (True - False) 9- RAM is a volatile storage. (True - False) 10- ROM is non-volatile storage. (True - False) 11- ROM is a type of primary storage that stores the start up instructions for the computer. (True - False) 12- If the power is turned off, the contents of RAM are retained. (True - False) 13- Magnetic storage is a type of storage that uses the properties of magnetism to store data. (True - False) Q7: What are the three main types of secondary storage? Magnetic, optical, and solid state storage Q8: Fill the spaces with one of these words: Cloud storage- Server- Network- Transmission Media- Static IP- Data packet- Hardware _______server______: A component that acts as a central resource for the storage of data and applications or for providing a service. ______network_______: Computers and devices that are joined together using cables or wireless technology. _______cloud storage_______: Data storage that is owned by a third party and accessed by the user, using the internet. ______transmission media________: The cables that are used to transfer data in a network. ______data packet_______: A unit of data that is used to transmit data across a network. ______static IP_______: An IP address that does not change each time the device connects to a network. ______hardware_______: All the physical components that you can see in a computer system. Q9: What are the benefits of storing data in the cloud? - Its storage can be increased or decreased as needed by the user - Can be accessed from any device - No need to pay for any hardware to store it Q10: Explain the role of programming languages. Allow developers to create software, applications and programs Q11: Write the types of programming languages: High and low level Q12: What is the meaning of translator? Software that converts a written code in a programming language to another Q13: Who is responsible of organizing interrupts into an order based upon priorities? Interrupt handler Q14: Who is responsible of converting code written in one programming language into another? complier Q15: Circle the correct answer. - An interrupt has a: -Multitasking unit -Priority Level -special processor - Unit number - When you write computer programs you will make specific software that allows you to: -Write and edit the programs you write - Test the programs you write - Run the programs you write - All of the above -The creation of files by the user needs to use: -Multitasking -Interrupts -Bootstrap - Application software -The interrupt sent to the processor to tell it that something needs its attention is considered as: -Signal -Interface -Command line -Natural Language Q16: Write the roles of Operating System: - Provides an interface and platform to run applications - Manages files, drivers, peripherals, memory, multitasking, interrupts, and user accounts Q17: What is the difference between high-level language and low-level language? High level language uses English-like commands (friendlier with user), while lowlevel language uses the computer’s language (binary code of 0s and 1s – more difficult for the user to understand). Q18: What is the meaning of interrupt handler (IH)? A program that organizes interrupts into an order bases upon priorities. Q19: Choose (True or False) for the following statements. -The operating system can't allow the user to move files. (True - False) - The operating system allows the creation of directories that the files can be stored within. (True - False) High-level language is easier for users to understand, read, and write. (True False) -Low-level language is easier for users to debug code. (True - False) Most computers need a user to set up an account. (True - False) -The software could be written by anyone in any language. (True - False) Q20: Write the different types of interface: GUI, natural, and command line Q21: Compare between the types of interfaces according to the functionality. GUI: uses windows, icons, pointers, and menus. Natural: user types or speaks commands Command line: user types commands Q22: What does System software manage? A computer’s software and hardware Q23: How is application software different from system software? Application software is a software the allows the user to perform a certain useful task, while system software manages it alongside hardware. Q24: What is the meaning of interrupt service routine (ISR)? Program the receives an interrupt and performs the required action(s). Q25: Choose (True or False) for the following statements? 1-Digital currency is a currency that exists electronically rather than physically. (True - False) 2-The internet is the infrastructure that is used to access the World Wide Web. (True - False) 3-Packet interception is a unit of data that is used to transmit data across a network. (True - False) 4-Blockchaine is a method that is used to track all the transactions made with a cryptocurrency. (True - False) 5- Domain name server is a network component where the web pages for a website are stored. (True - False) 6- HTTP is a secure version of HTTPS protocol. (True - False) Q26: Give the suitable word for the following definitions --------website---------: A collection of web pages, normally about a related topic or purpose. -------network--------: Computers and devices that are joined together using cables or wireless technology. ---------web browser---------: A piece of software that retrieves and displays web pages. ------------URL--------------: Another name for the text-based address for a website. -------------DNS--------------: A special server that contains a database of domain names and their corresponding IP address. ---------bookmark------------: A link that can be created to allow you to quickly find a web page again. --------cookie-------- Small text file that is used to store personal data, by a web browser. ----------------two-step verification-----------------: A process that involves inputting two different kinds of data to enter an account or device. ----------------biometric password----------------: A type of password that uses a person’s biological data, such as their fingerprint. Q27: What are the main types of viruses? Worm, trojan horse, spyware, adware, and ransomware Q28: What is the difference between of biometric password and biometric device? A biometric password that uses a person’s biological data like his fingerprint or face ID, while a biometric device allows the user to record and input it. Q29: What are the security solutions that can be used against hackers? Anti-virus, anti-malware, 2-step verification, firewall, and a strong password. Q29: Give three reasons that make hackers try to hack. Get unauthorized data to steal or corrupt them. Q30: Give an example for web browser. Google chrome. Safari, Microsoft edge… Q31: Give an example for search engine. Google, Bing, Yahoo… Q32: How is a web browser different from a search engine? A web browser receives and displays webpages, while a search engine helps find the websites. Q33: What are the types of cookies? Session and persistent Q34: What do we mean by digital currency? A currency that’s electronic instead of physical. Q35: What is the purpose of a web browser? Receives the user’s input information to fetch websites and display them. Q36: What are the main functions of a web browser? Receives and displays web pages. Q37: What is the difference between Pharming and Phishing? Pharming is downloading a dangerous (malicious) software in a user’s hard drive to direct him to a fake website that looks genuine to encourage him to enter their personal data, leading it to get stolen, while phishing is sending a user a fake email that looks genuine to encourage him to also enter his personal data by clicking on a fake link or website or responding to the email. Q38: What do we mean by access level? Access level is a set of rules or permissions that defines what a user can perform in a system. Q39: What is the meaning of software? Series of instructions written in a specific programming language that performs a certain task. Q40: Why do we use databases? To helps us store and control data Q41: Do we consider peripheral as a hardware device or software device? Explain your result. Hardware; used to input, store, or output data from a computer that isn’t directly a part of it. Q42: The machine code is considered as an example of low-level language. Explain why? Uses binary code (0s and 1s) which is difficult for the user to understand. Q43: Choose three roles of operating system and explain their importance. Manage multitasking: allows the user to perform multiple tasks at once by deciding which process should be executed next and how long it needs to get processed before switching to another process. Manage memory: manages how data moves into and out of hardware like RAM, as well as checks the process carried out and ensures there’s enough RAM to perform it only. Provide a platform to run an application: allows the application software to run on the computer by fetching instructions from it then execute them.