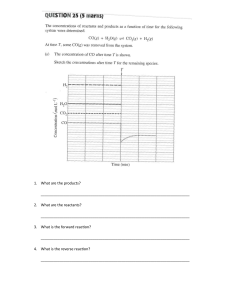
QUESTION Comparison of access techniques, random methods, error control scheme for link layer access. ACCESS TECHNIQUES….. are methods used to control how devices in a network gain access to a shared communication medium. The two commonly used access techniques are; Random access: in random access, multiple devices contend for access to the network without any predetermined order. Each device has an equal chance of accessing the medium. Random-access is commonly used in networks where the communication medium is shared, such as ethernet networks. Examples of random-access methods include carrier sense multiple access (CSMA) and CSMA/CD (carrier sense multiple access with collision detection). ❖ Controlled access: controlled access refers to access techniques where devices gain access to the network in a predetermined manner. These techniques are typically used in scenarios where devices are assigned specific time slots or priorities. Controlled access can provide guaranteed access and can be more efficient in managing network resources. Examples of controlled access techniques include Time Division Multiple Access (TDMA) and polling. ❖ RANDOM ACCESS METHODS. These are methods are a subset of access techniques that use randomization to handle conflicts and allow fair access to the medium. ALOHA: ALOHA is a random-access method where nodes can transmit data whenever they have it. without checking for channel availability. Collision may happen if multiple nodes transmit simultaneously, resulting in the loss of data. There are two variations of ALOHA: pure ALOHA and slotted ALOHA ❖ Carrier sense multiple access (CSMA): In CSMA, nodes listen to the channel before transmitting. If the channel is idle, they transmit simultaneously. ❖ Carrier sense multiple access with collision detection (CSMA/CD): CSMA/CD is used in ethernet networks. It improves upon CSMA by detecting collision occurs. It then waits for a random period before retrying. ❖ Carrier sense multiple access with collision avoidance (CSMA/CA): CSMA/CA is used in wireless networks like WIFI. It includes a handshake mechanism where nodes exchange control packets to reserve the channel before ❖ ERROR CONTROL SCHEME FOR LINK LAYER… These schemes in link layer aims to detect and correct errors that may occur during data transmission over a physical layer. ❖ Automatic repeat request (ARQ): ARQ is a common error control scheme that detects and corrects transmission errors by retransmitting lost or corrupted data. It uses acknowledgements and timeouts to identify and recover from errors, ARQ is divided into the following categories . Stop-and-wait ARQ Back-N ARQ Selective repeat ARQ Forward error correction (FCF): FCF adds redundant error-correcting codes to the transmitted data. the receiver can use these codes to detect and correct errors without requiring retransmissions. Common FEC codes include hamming codes and convolutional codes. ❖ Hybrid ARQ (HARQ): HARQ combines the techniques of ARQ and FEC. It uses error-detection codes to correct errors if possible, and if not, it requests retransmission through ARQ error detection and retransmission ❖ Checksums: checksums are simple error-detection techniques that involve calculating a checksum value from the data. The receiver recalculates the checksum and compares it with the received checksum to detect errors. Checksums are less reliable than ARQ or FEC but are computationally efficient. ❖ SIMILARITIES OF ACCESS TECHNIQUES, RANDOM ACCESS METHODS, ERROR CONTROL SCHEMES FOR LINK LAYER… ❖ Link Layer Scope: All three concepts—access techniques, random access methods, and error control schemes—operate at the link layer of the network protocol stack. They primarily deal with the communication between adjacent nodes or devices in a network. ❖ Enhance Efficiency: Access techniques, random access methods, and error control schemes aim to improve the efficiency of data transmission. They strive to maximize the utilization of the available bandwidth, minimize collisions or errors, and optimize the overall performance of the link. ❖ Impact on Data Transmission: All three mechanisms directly influence the process of transmitting data over a link. Access techniques determine how multiple devices or users’ access and share the medium. Random access methods control the timing and protocol for devices to transmit data. Error control schemes detect and handle errors to ensure reliable data delivery. SIMILARITIES OF ACCESS TECHNIQUES, RANDOM ACCESS METHODS, ERROR CONTROL SCHEMES FOR LINK LAYER… ❖ Protocol Implementation: Access techniques, random access methods, and error control schemes require specific protocols and algorithms to be implemented at the link layer. These protocols define the rules, procedures, and signaling mechanisms necessary for successful communication. ❖ Trade-offs and Performance: Each of these concepts involves trade-offs and considerations related to performance. Access techniques and random-access methods often trade off fairness, latency, and throughput to achieve optimal utilization of the medium. Similarly, error control schemes balance the overhead of error detection and correction against the reliability of data transmission. ❖ Interaction with Higher Layers: While primarily operating at the link layer, access techniques, random access methods, and error control schemes can also interact with higher layers of the network protocol stack. For example, they may influence flow control, congestion control, and packet retransmission strategies implemented at higher layers to ensure end-to-end reliability. DIFFERENCES OF ACCESS TECHNIQUES, RANDOM ACCESS METHODS, ERROR CONTROL SCHEMES FOR LINK LAYER RANDOM ACCESS METHOD … PROPERTIES ACCESS TECHNIQUES ERROR CONTROL SCHEME FOR LINK LAYER DEFINITION These are techniques Are a subset of access which determine how techniques. devices or users share communication medium. These scheme focuses on ensuring reliable data transmission over a link. EXAMPLES Examples include contention based access, controlled access, and polling. Examples include ALOHA, CSMA, and CSMA/CA. Examples include error detection techniques and error correction techniques (e.g. ARQ and FEC) CONTROL MECHANISM Employ a control mechanism to manage the shared medium. Do not rely on a central control mechanism. These use protocols and algorithms to manage error detection and correction DIFFERENCES OF ACCESS TECHNIQUES, RANDOM ACCESS METHODS, ERROR CONTROL SCHEMES FOR LINK LAYER PROPERTIES ACCESS TECHNIQUES RANDOM ACCESS METHODS ERROR CONTROL SCHEME FOR LINK LAYER MEDIUM SHARING Determine how multiple devices share the available bandwidth. Allow devices to contend for the medium and transmit when available Do not directly influence medium sharing but focus on data integrity during transmission. COLLISION HANDLING Access techniques such as CSMA/CD and CSMA/CA incorporate collision handling mechanism. Random access methods like ALOHA and CSMA, have collision detection and avoidance. Error control scheme particularly ARQ protocols, handle retransmission in case of collision or errors.