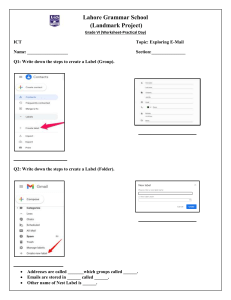
Subject Grade Date Block week ICT 7 16/11/2023 2 3 Student Name: Unit/Lesson/ Topic Revision sheet with answers ………………………………………………… ………………………………………………… …………………. classwork 1 out of 5 Class G7A/B 1 Define the following: 1) Target Audience: ………………………………………………………………………………… ………………………………………………………………………………… 2) E-safety ………………………………………………………………………………… ………………………………………………………………………………… 3) Spam ………………………………………………………………………………… ………………………………………………………………………………… 4) Phishing ………………………………………………………………………………… ………………………………………………………………………………… 5) Macro ………………………………………………………………………………… ………………………………………………………………………………… 6) Wiki ………………………………………………………………………………… ………………………………………………………………………………… 7) Blog 2 8) Diffrentiate between blogs & wiki Edited by the author 9) List 5 of the E-safety rules. Keep Personal Information Professional and Limited. Keep Your Privacy Settings On. Be Careful What You Download. Choose Strong Passwords. Make Online Purchases from Secure Sites. 3 19) What are the reasons of keeping your personal information private? (List 3 reasons). a) Prevent identity theft. b) Protect your financial information. c) Avoid being robbed. 11) How can you avoid phishing? 1) Don’t open any email from strangers. 2) Avoid logging in to any website you don’t trust. 3) Avoid clicking on any link you don’t trust. 12) A teacher set up a spreadsheet to compare ICT grades for six students over five years. (a) What is the formula used in cell H5 to find the average ICT grade for Ali? AVERAGE (B5:G5) (b) What is the formula used in cell I6 to find the highest ICT grade for Esraa? = MAX (B6:G6) (c) If the data in cell E4 was changed to 50, which cells would be automatically updated? H4, I4 (d) The teacher wants to extend the spreadsheet to include ICT grade for 2016 Describe how he could do this? Add column between G and H (e) How could the formula in H2 be used in H3 to H7 without writing it out another five times? Select/highlight H2 down to H7 select Auto/fill down 4 13)Choose the correct answer: 1)…………………….. is a series instructions that you group together as a single command to accomplish a task automatically. a) Macros b) Movie c) Creative common 2) After a system failure, data must be retrieved from a backup. This is the process of: a) Backup b) Restore c) Hack 16) You might receive an email claiming to be from your bank It is usually include a link to a fake website that looks identical to the real one. When you log in it sends your username and password to someone who will steal your money or your identity. This is the situation of: a) Spam b) Phishing c) Fishing 17) …………………. emails offer all kinds of things like money, prizes and very low prices for products that are normally very expensive. They can contain malware too. a) Phishing b) Spam c) Hack 18)What does CC stand for in an email? a) Closed Caption b) Carbon Copy c) Copy Carbon 19)Email etiquette is a) Behavior you should use when writing or answering an email message b) A French word for email writing c) Sending emails via the Post Office 5 20)What are the advantages and disadvantages of using email? Advantages Disadvantages ❖ Emails are delivered extremely fast when compared to traditional post. ❖ The recipient needs access to the internet to receive email. ❖ Emails can be sent 24 hours a day, 365 days a year. ❖ Viruses are easily spread via email attachments ❖ Emails can be sent and received from any computer, anywhere in the world, that has an internet connection. ❖ Emails can be sent to one person or several people. ❖ No guarantee the mail will be read until the user logs on and checks their email. ❖ Spam - unsolicited email, ie junk mail. 6 7