Q1+2:
+ Connection-oriented Acknowledged service: Before transmission can happen, a
dedicated path must be established between the sender and the receiver, often
using ‘call request’ and ‘call accept’ package. When this approach is used, the
transmission path is fixed throughout the transmission period. After the receiver
receives the datagram, it must send a acknowledement message to the sender. If
the sender doesn’t receive the acknowledgement, the datagram is considered
being lost and retransmitted. This method can protect the integrity of the data as
well as the stability of the network during transmission time. Widely used in TCP
protocol
+ Connectionless service: The sender and the receiver don’t need to establish a
dedicated path before transmission. Datagrams contain destination information
and the intermediate devices use this information to forward datagrams to the
right destination. When this approach is used, the transmission path is not fixed,
the datagram can travel through different route and doesn’t need to come to the
destination in order.
+ Connectionless acknowledged service: After the receiver received the datagram,
the receiver must send an acknowledge to the sender, this allow the sender to
know whether the datagram has reached the destination or not, if not, the sender
can retransmit the data. This approach is often seen in wifi network.
+ Connectionless unacknowledged service: The receiver doesn’t need to send
acknowledgement packet to the sender. This approach favour transmission speed
over the integrity of the data. Often seen wired LAN.
Q3:
HDLC – High-level Data Link Control
PPP – Point to Point
+ PPP là một giao thức Byte-oriented, HDLC là một giao thức Bit-oriented.
+ PPP sử dụng Flag byte và kỹ thuật nhồi byte (byte stuffing) để đánh dấu điểm
bắt đầu và kết thúc của frame, trong khi HDLC sử dụng Flag bit và kỹ thuật nhồi
bit(bit stuffing).
+PPP cung cấp các giao thức xác nhận bên gửi và bên nhận như PAP(Password
Authentication Protocol) hay CHAP(Challenge Handshake Authentication
Protocol). HDLC không hỗ trợ các giao thức xác nhận.
+HDLC được dùng trong truyền tin đa điểm-điểm(point-to-point) hoặc đa
điểm(multi-point). PPP chỉ cho phép truyền tin điểm-điểm.
+HDLC chỉ vận hành được trên các thiết bị của hãng Cisco còn PPP thì có thể làm
việc được với các thiết bị khác.
HDLC – High-level Data Link Control
PPP – Point to Point
+ PPP is a byte-orientd protocol, HDLC is a bit-oriented protocol
+ PPP uses flag-byte and byte stuffing technique to mark the beginning and
ending of a frame, meanwhile, HDLC uses flag-bit and bit stuffing technique.
+ PPP provides several authentication protocols like PAP (Password
Authentication Protocol) or CHAP (Challenge Handshake Authentication Protocol).
HDLC doesn’t support authentication.
+ HDLC is used for Point to Point as well as Multi-point transmission. PPP only
support Point to Point transmission.
+ HDLC can only be used in Cisco devices while PPP can be used for other network
devices brand.
Q4:
First, we need to calculate the propagation delay:
Tprop = 2*RTT(round trip time) = 2*(375*106 / 3*108) = 2.5 s
In order to continuously transmiting data to the moon, the transmission time
must equal the propagation delay
So: Ttransmission = TProp
Frame size / bandwidth = Tprop = 2.5 s
Frame size = 2.5 * bandwidth = 2.5 * 1.5Mbps = 3.75 Mbit
Because HDLC approach is used for transmission, so either Go-back-N is used or
Selective-repeat is used.
For Go-back-N, suppose the window size is 7 by default:
The smallest possible frame size is: 3.75Mbit/7 = 0.535714Mbit = 535714bit
For Selective-Repeat, suppose the window size is 4 by default:
The smallest possible frame size is: 3.75Mbit/4 = 0.9375Mbit = 937500bit
Q5:
Suppose: +Bandwidth = 1.5Mbps = 1.5*106bps
+Frame size = 250byte = 2000bit
+Distance between earth and satellite is approximate 36000km =
3.6*10 m
7
+ The speed of light is 3*108m/s
First, we need to calculate the propagation delay:
Tprop = 3.6*107 / 3*108 = 0.12s
The transmission time of one frame is:
tf = frame size / bandwidth = 2000/1.5*106= 0.00133s
Because HDLC approach is used for transmission, so either Go-back-N is used or
Selective-repeat is used.
+) For Go-back-N, suppose the window size is 7 by default:
Suppose N is the number of bit can be transmitted in one transmission:
N = window size = frame size * 7 = 2000 * 7 = 14000bit
Suppose Tcycle is the time to transfer one window:
Tcycle = transmission time + 2*Tprop = 0.00133 + 0.12*2 = 0.24133s
Suppose no error occur, the maximum transmission rate for Go-back-N with the
window size of 7 is:
Rmax = N/Tcycle= 14000/0.24133 = 58011bitps = 58kbps
+) For Selective-Repeat, suppose the window size is 4 by default:
Suppose N is the number of bit can be transmitted in one transmission:
N = window size = frame size * 4 = 2000 * 4 = 8000bit
Suppose Tcycle is the time to transfer one window:
Tcycle = transmission time + 2*Tprop = 0.00133 + 0.12*2 = 0.24133s
Suppose no error occur, the maximum transmission rate for Selective-repeat with
the window size of 4 is:
Rmax = N/Tcycle= 8000/0.24133 = 33149bitps = 33.15kbps
Q6: (Câu này chịu, chép)
Firstly, we find out the probability of the k packets that have reached the Tsecond. It can be computed with the help of binomial distribution that has
parameters as N=60 and shows the probability of p=0.1.
The average number for the arrivals of the packets can be given as Np=6. Now,
calculate the average number of packets received through the first line as below:
X= ∑8𝑘=0 𝑘 . 𝐶𝑘60 . (0,1)𝑘 . (0,9)60− 𝑘 = 4.59
Now, the average number of packets received is 4.59 that gets transmitted
through the first line. The remaining will get transmitted by the second line. Now,
the average number of packets transmitted through the second line per T second
can be obtained as below:
Y= Np – X = 6 – 4,59 = 1,41
Therefore, it will transmit 1.41 packets on average per T second from the second
line.
Q7:
a,
+ Message size is important because in real-time signals of voice it is necessary to
transfer a fixed packet size of that holds no more than 20 ms of the speech signal.
The handling of arbitrary message size is not as important as long as the desired
packet size for voice can be handled.
+ Sequencing is essential because each packet needs to arrive in the same
sequence that it was generated.
+ Reliability is moderately important since voice transmission can tolerate a
certain level of loss and error.
+ Pacing and flow control are not as important because the synchronous nature of
the voice signal implies that the end systems will be matched in speed.
+ Timing, for real-time voice transfer, is important because this adaptation
function helps to control the jitter in the delivered signal.
+ Addressing is only during the connection setup phase if we assume some form
of virtual circuit packet switching method
+ Privacy, integrity, and authentication have traditionally not been as important
as the other issues discussed above.
b)
+ If the underlying network is reliable then the end-to-end approach is better
because the probability of error is very low so processing at the edge suffices to
provide acceptable performance.
+ If the underlying network is unreliable then the hop-by-hop approach may be
required. For example, if the probability of error is very high, as in a wireless
channel, then error recovery at each hop may be necessary to make effective
communication possible.
Q8:
a)
The sender in the stop-and-wait protocol described in the chapter retransmits a
frame when an acknowledgment is not received in time. The modified protocol
says that the frame is retransmitted every time the sender or receiver sees an
error.
Therefore, the only difference is that frames are retransmitted sooner. So, the
protocol will work correctly.
b)
No. The state transition diagram doesn’t need to be modified.
c)
The error recovery process will be faster with this modified protocol.
Q9: (Đề như bị lỗi má rồi mà bao năm nay không ai nói gì)
Q10:
1Mbyte = 106 byte = 8 x 106 bits because1 byte = 8 bits
The file length n = 8 x 106 bits, the transmission rate R = 1 Mbps = 106 bps
and p = 10-6
a)
For n lagrge and p very small: (1 − 𝑝)𝑛 ≈ 𝑒 −𝑛𝑝
So the probability that the entire is transmitted without errors is:
P[no error in the entire file] = (1 − 𝑝)𝑛 ≈ 𝑒 −𝑛𝑝 = 𝑒 −8 = 3.35 x 10−4
b)
A subblock of length n/N is received without error with probability :
P[no error in subblock] = (1 − 𝑝)𝑛/𝑁
A block has no errors if all subblocks have no errors, so the probability that all
subblocks arrived without errors is:
𝑁
𝑃[no error in subblock]𝑁 = (1 − 𝑝)(𝑛/𝑁) = (1 − 𝑝 )𝑛 = (1 − 𝑝)𝑛 ≈
𝑒 −𝑛𝑝 = 𝑒 −8 = 3.35 x 10−4
Because P[no error in subblock] = 𝑃[no error in subblock]𝑁
So simply dividing the blocks does not help.
c)
In Stop-and-Wait ARQ protocol, the sender sends a packet and then wait for an
acknowledgment from the receiver. If the acknowledgement arrives before timeout, the transmission is successful. If the acknowledgement doesn’t arrive and the
time out expires, the sender retransmits the packet.
So by using Stop-and-Wait ARQ protocol, the file can always be delivered errorfree to the receiver.
In case the ARQ transmits the entire file each time, the probability that the file
will arrives successfully without error is :
P[no error in the entire file] = (1 − 𝑝)𝑛 ≈ 𝑒 −𝑛𝑝 = 𝑒 −8 = 3.35 x 10−4
So on average, the file must be transmitted 1/P = 1/(3.35 x 10−4 ) = 2981 times
before a successfull transmission occur.
Without propagation delay, the transmission time of the file each time is :
T1 time = 1Mbyte/1Mbps = (8*106)/ (1*106)= 8s
So the average time for the file to be transmitted successfully is:
T2981 times = 8s x 2981 = 23848s = 6.62h
Q11:
a)
Base on the topology, there are 4 LAN switches: S1, S2, S3, S4 and an interface
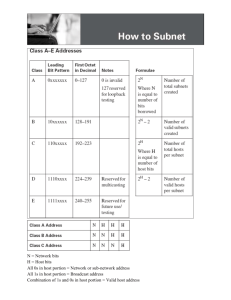
between two Routers R1, R2 that require IP address. So 5 subnets are needed.
b)
There are 5 subnets in the topology so we will divide the network address into
23=8 subnets. Therefore, the number of bits must be borrowed is 3 bits.
c)
We borrow 3 bits so the number of subnets can be created is 23 = 8 subnets.
d)
After borrow 3 bits for subnetting, the subnet mask will become /27. So the
number of bits for host address is : 32 – 27 = 5 bits
With 5 bits, the maximum number of usable hosts per subnet is 25 – 2 = 30 hosts
Q12:
Table for B1:
Step 1
Step 2
Step 3
Step 4
Step 5
S1 -> S5
S3 -> S2
S4 -> S3
S2 -> S1
S5 -> S4
Address
S1
S3
S4
S2
Port
1
2
2
1
Address
S1
S3
S4
Port
1
1
2
S5
2
Table for B2:
Step 1
Step 2
Step 3
Step 4
Step 5
Q13:
S1 -> S5
S3 -> S2
S4 -> S3
S2 -> S1
S5 -> S4
a)
Iteration
Initial
1
2
3
4
5
Node
D1
(5,D4)
(4,D2)
(4,D2)
(4,D2)
(4,D2)
--------
{D4}
{D4, D2}
{D4, D2, D3}
{D4, D2, D3, D5}
{D4, D2, D3, D5, D6}
{D4, D2, D3, D5, D6, D1}
D2
(1,D4)
------------------------------------
D3
(2,D4)
(2,D4)
-----------------------------
According to the table:
The shortest part from D4 to D1 is 4 and the path is D4 -> D2 -> D1
The shortest part from D4 to D2 is 1 and the path is D4 -> D2
The shortest part from D4 to D3 is 2 and the path is D4 -> D3
The shortest part from D4 to D5 is 3 and the path is D4 -> D5
The shortest part from D4 to D6 is 3 and the path is D4 -> D3 -> D6
b)
Destination
Cost
Next Hop
D1
4
D2
D2
1
D4
D3
2
D4
D5
3
D4
D6
3
D3
D5
(3,D4)
(3,D4)
(3,D4)
----------------------
D6
∞
∞
(3,D3)
(3,D3)
---------------
Q14:
a)
The largest required subnet is LAN-A with a minimum of 50 hosts.
b)
According to the question, two subnets are required for LAN-A and LAN-B, and
two additional unused subnets are needed for future network expansion. So the
minimum number of subnets required is 4.
c)
/24 means the length of the prefix is 24 bits:
So in binary form, it is:
11111111.11111111.11111111.00000000
d)
In the subnet mask, the ones represent the network portion of the IP address, the
zeros represent the host portion of the IP address.
e)
Subnet Address
Prefix
Subnet Mask
192.168.0.0
/26
255.255.255.192
192.168.0.64
/26
255.255.255.192
192.168.0.128
/26
255.255.255.192
192.168.0.192
/26
255.255.255.192
Q15:
a)
2 things are needed to be changed:
+ The frame header needs to be modified to recieve the list of frames and Since
the reciever explicitly indicates which frames are needed to be transmitted.
+ Change in transmitter operation is needed. If the recieved list contains m oldest
frames that are yet to be recieved , then it can be used to skip retransmission of
frames that have already been received.
b)
Performance will surely increase if the error rate is high or delay is high. A single
frame can ask for the retransmission of several frames.
The complexity of the protocol will surely increase relative to the unchanged
Selective repeat ARQ
Q16:
a)
The time it takes to download the file over a 32Kbit/s modem is:
File size / Bandwidth = 1Mbyte/32Kbit = (8*220)bit / (32*103)bit = 262.144 s
b)
The time it takes to download the file over a 1Mbit/s modem is:
File size / Bandwidth = 1Mbyte/1Mbit = (8*220)bit / (1*106)bit = 8.388 s
c)
Suppose the file size after compression is n Mbyte.
The download time in case of the 32Kbit/s modem is :
(n/original file size)*262.144 s
The download time in case of the 1Mbit/s modem is : (n/original file size)*8.388 s
Q17:
g(x) = x3+x+1 => the generate code is: 1011
Calculating the CRC code:
Step 1: the generate code is 4 bits so we add 000 to the data bits for caculation.
The data bits becomes: 1001000
Step 2: Perform binary division, data bits divides by the generate code
101
1011 | 1001000
1001
1011
001000
1011
00110
According to the caculation, the remaining is 110.
The codeword is : 1001110
Q18:
a)
When the router receives a packet with IP address 135.46.63.10, it will look into
it’s routing table to find the appropriate network to forward the packet, using
longest prefix first approach.
First it will look at IP address of Router 1: 192.53.40.0/23
From the subnet mask /23 of Router 1, it will caculate the network address of the
packet using binary AND operation between the subnet mask and the packet IP
address:
Packet IP address: 10000111.00101110.00111111.00001010 (135.46.63.10)
Subnet Mask:
11111111.11111111.11111110.00000000 (/23)
Binary AND =
10000111.00101110.00111110.00000000 = 135.46.62.0
The Router see that the result of the AND operation (135.46.62.0) doesn’t match
Router 1 IP address (192.53.40.0) so it continue to the next IP address in the
routing table.
Now it will look at the Interface 0 and 1, and uses the subnet mask /22 of two
Interfaces to caculate the network address of the packet:
Packet IP address: 10000111.00101110.00111111.00001010 (135.46.63.10)
Subnet Mask:
11111111.11111111.11111100.00000000 (/22)
Binary AND =
10000111.00101110.00111100.00000000 = 135.46.60.0
Now the Route sees that the result of the operation (135.46.60.0) matches the
network address of Interface 1 (135.46.60.0).
The router forward the packet to Interface 1.
b)
Using the same technique mentioned in question (a), the router first caculate the
network address of the packet using subnet mask /23 of Router 1:
Packet IP address: 10000111.00101110.00111001.00001110 (135.46.57.14)
Subnet Mask:
11111111.11111111.11111110.00000000 (/23)
Binary AND =
10000111.00101110.00111000.00000000 = 135.46.56.0
The Router see that the result of the AND operation (135.46.56.0) doesn’t match
Router 1 IP address (192.53.40.0) so it continue to the next IP address in the
routing table.
Now it will look at the Interface 0 and 1, and uses the subnet mask /22 of two
Interfaces to caculate the network address of the packet:
Packet IP address: 10000111.00101110.00111001.00001110 (135.46.57.14)
Subnet Mask:
11111111.11111111.11111100.00000000 (/22)
Binary AND =
10000111.00101110.00111000.00000000 = 135.46.56.0
Now the Route sees that the result of the operation (135.46.56.0) matches the
network address of Interface 0 (135.46.56.0).
The router forward the packet to Interface 0.
Q19:
Given IP address: 198.16.0.0
IP addresses will be allocated in blocks of power of 2. So the for organization A, B,
C, D will be allocated 4096, 2048, 4096, 8192 addresses respectively.
+ Organization A:
A will be allocated 212 = 4096 addresses so the host portion of A network will has
12 bits -> the network potion will have 20 bits
A first IP address : 198.16.0.0
A last IP address: 198.16.15.255
A network mask : 198.16.0.0/20
+ Organization B:
B will be allocated 211 = 2048 addresses so the host portion of B network will has
11 bits -> the network potion will have 21 bits
B first IP address : 198.16.16.0
B last IP address: 198.16.23.255
B network mask : 198.16.16.0/21
+ Organization C:
C will be allocated 212 = 4096 addresses so the host portion of C network will has
12 bits -> the network potion will have 20 bits
C first IP address : 198.16.24.0
C last IP address: 198.16.39.255
C network mask : 198.16.24.0/20
+ Organization D:
D will be allocated 213 = 8192 addresses so the host portion of D network will has
13 bits -> the network potion will have 19 bits
D first IP address : 198.16.40.0
D last IP address: 198.16.71.255
D network mask : 198.16.40.0/19
Q20:
The Host IP address is: 192.135.250.180
Number of subnet bits
Number of subnet created
Number of Host bits per
Subnet
Number of Hosts per Subnet
Network Address of this
Subnet
IPv4 Address of First Host on
this Subnet
IPv4 Address of Last Host on
this Subnet
IPv4 Broadcast Address on
Original Subnet Mask:
255.255.255.0
0 bit
1 subnet
New Subnet Mask:
255.255.255.248
5 bits
25 = 32 subnets
8 bits
3 bits
254 hosts
6 hosts
192.135.250.0
192.135.250.176
192.135.250.1
192.135.250.177
192.135.250.254
192.135.250.182
192.135.250.255
192.135.250.183
this Subnet
Q21:
The total overhead is:
H = TCP header + IP header + Ethernet header = 20 + 20 + 18 = 58 bytes
With L = 100 bytes, the percentage of data compare to the total frame size is:
P = L / (L + H) = 100 / (100+58) = 63.29%
With L = 500 bytes, the percentage of data compare to the total frame size is:
P = L / (L + H) = 500 / (500+58) = 89.61%
With L = 1000 bytes, the percentage of data compare to the total frame size is:
P = L / (L + H) = 1000 / (1000+58) = 94.52%
Q22:
a)
In a three-way handshake procedure, the generated value of the initial sequence
number is always unique. If station B receives an old SYN segment from A, B will
acknowledge the request based on the old sequence number. When A receives
the acknowledgment segment from B, A will find out that B received a wrong
sequence number base on the ACK field. A will discard the acknowledgment
packet and reset the connection.
b)
If an old SYN segment from A arrives at B, followed by an old ACK segment from A
to a SYN segment from B, the connection will also be rejected. Initially, when B
receives an old SYN segment, B will send a SYN segment with its own distinct
sequence number set by itself. If B receives the old ACK from A, B will notify A
that the connection is invalid since the old ACK sequence number does not match
the sequence number previously defined by B. Therefore, the connection is
rejected.
Q23:
The checksum is calculated as follow:
Step 1: Perform binary addition on all of the words, the remaining is also added to
the result.
Word 1:
1111111111111111
Word 2:
1111111100000000
Word 3:
1111000011110000
Word 4:
1100000011000000
--------------------------------------
Result:
1011000010101111
Remainder:
11
--------------------------------------
Result:
1011000010110010
Step 2: Perform one’s complement on the result, we obtain the checksum
0100111101001101
Q24:
G = 10011
D = 1001010101
To calculate the remainder R, we perform the following steps:
Step 1: The Generator G is 5 bits so we add 4 zero bits 0000 to the data D
The data D becomes: 10010101010000
Step 2: Perform the binary division D divides by G
10011|10010101010000
10011
00011010
10011
010011
10011
000000000
According to the calculation, the remainder R is 0000.
Q25:
a)
The Bandwidth is: R = 2Mbps = 2*106 bps
The distance between two hosts A and B is: 20000km = 2*107 m
The propagation delay between A and B is:
distance/propagation speed = (2*107)/(2.5*108) = 0.08s
The Bandwidth-delay product is the multiplication of the Bandwidth and the
propagation delay:
Rdprop = 2*106*0.08 = 16000 bits
b)
The Bandwidth-delay product is the maximum amount of data that can reside in
the transmission link at any given time.
Because the bandwidth-delay product between A and B is 16000 bits, which is
smaller than the file size = 800000 bits
So the maximum number of bits that will be in the link at any given time is 16000
bits.