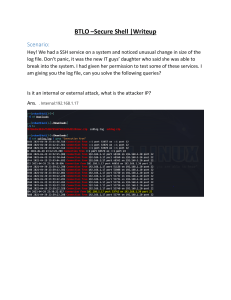
Scenario:In big industrial corporate can be accure and so many Network attack can be possible.In a one insider thread company employee,He made to this DOS flooding for cras entire servers & web base applications.Now Investigate to this case study.In Firewall all information & ip logs,pcap files captured all open ports.In a system establish all data and capture port name,port address and use to dump process and captured firewall traffic & pcap logs. QUESTIONS:I. What is the source ip address? II. What is the destination ip address? III. Which company’s router used by victim? IV. What is the MAC address of router? V. What is the IP adddress of router? VI. What is the destination port use for attack? VII. Which protocol use maximum packet request? VIII. How many methods used in this pcap file?give example. IX. What is the IP address of Attacker machine? X. What is the MAC address of Attacker machine? XI. Which type of DOS attack performed by attacker? XII. How many numbers of packet avilable in evidence file? XIII. How mant TCP request counts transmit by Attacker?